Roger Clarke’s Dataveillance and Information Privacy Home-Page
© Xamax Consultancy Pty Ltd, 1995-2024

Infrastructure
& Privacy
Matilda
Roger Clarke’s Dataveillance and Information Privacy Home-Page© Xamax Consultancy Pty Ltd, 1995-2024 |

|
|||||
| HOME | eBusiness |
Information Infrastructure |
Dataveillance & Privacy |
Identity Matters | Other Topics | |
| What's New |
Waltzing Matilda | Advanced Site-Search | ||||
This segment of the site provides access to papers that I've published in the broad area of privacy and dataveillance, since the 1970s. Dataveillance is the systematic use of personal data systems in the investigation or monitoring of the actions or communications of one or more persons. I coined the term in 1986, as a contraction of 'data surveillance', and published an analysis of the concept in Clarke (1988).
The word has come into increasingly wide use, both in the academic community, and more generally, and made it into the 2009 edition of Webster's New Millennium™ Dictionary of English, and the Oxford in March 2012. The OED entry identifies two earlier uses, which I was not aware of at the time. (Neither was anyone else, and they have no citations, whereas my 1988 article reached 1,000 in mid-2019; so I feel justified in claiming the credit).
A substantial set of resources on dataveillance and privacy topics has been available on this site since 1995, attracting over 25 million hits to the end of 2023.
The resources in this segment of the site can be accessed in the following ways, most useful first. The indexes are up-to-date as at 31 December 2023:
This page is the Topic-Based Index of my papers on dataveillance and privacy themes
The What's New Page (because the indexes are never fully up-to-date) is here
The Chronological Index of my papers on dataveillance and privacy themes is here
There is also a chronological index of Presentations here
There is a Search Facility, at the top-right-hand side of this and other index-pages
|
1. Theory:
|
2. Organisational Strategy, Policy, Practice:
3. Public Policy:
4. Australia:
|
Introductory and Overview sources are available, as follows:
See also the following recent papers:
The first cluster of papers establishes the theory of dataveillance. In part, these papers recapitulate knowledge developed by other people, but they also contain a lot of original contributions.
My early work, from the mid-1980s, was specifically in the then new field of Dataveillance (a term that I coined). I later extended my work into surveillance more generally, and into specific, new forms that have become rampant and that lacked (and still lack) adequate controls.
Surveillance inevitably threatens the human value of privacy. Privacy is a
complex notion that is still poorly understood, so it's been necessary to publish
a number of papers on the concept. A useful way to define privacy is as the
interest that individuals have in sustaining 'personal space', free from interference
by other people and organisations.
It's vital to get the focus beyond the narrow notion of 'data privacy' – which
is all that 'data protection laws' address. The
five dimensions that I use
to explain the diversity of privacy concerns are as follows:
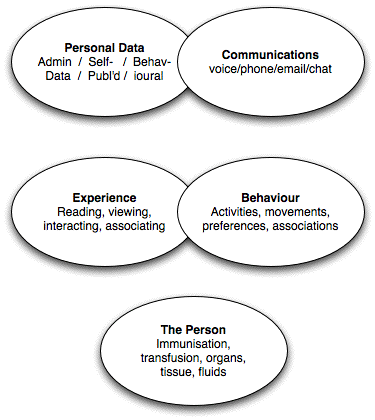
Details are in the following papers:
An aspect of particular concern that is far too little-discussed is the significance of privacy as an enabler of political expression and acts, and hence of democracy and freedoms more generally. See:
Surveillance is the systematic investigation or monitoring of the actions or communications of one or more persons.
Overviews of the field are provided here:
As regards the concept generally, see also:
Specific forms of Surveillance are addressed in the following sub-sections.
Physical Surveillance depends on a human watcher and/or listener, perhaps using aural and/or visual aids such as cameras to transmit images to a remote location or directional microphones. See:
Visual Surveillance goes beyond Physical Surveillance in that it involves the projection and/or capture of images and video, perhaps with synchronised audio. See:
By Electronic Surveillance is meant the monitoring of people's interactions, behaviour and social networks through their communications over electronic networks, with other individuals, devices and databases. See:
I coined 'dataveillance' in the mid-1980s. The purpose was to draw attention to the substantial shift that was occurring from (expensive) physical and electronic surveillance of individuals to (cheap) surveillance of people's behaviour through the increasingly intensive data trails that their behaviour was generating. I've created a dozen or so neologisms, but dataveillance is far and away the most successful of them, making it into dictionaries by 2009. See also Wordspy, 2001.
For introductory and summary material, see these papers:
The base for my extensive work in this area was laid in a paper entitled 'Information Technology and Dataveillance' (1988, published in a major US journal). Physical and electronically enhanced monitoring of individuals and groups is expensive. The paper shows how information technology is enabling those old techniques to be replaced by highly automated, and therefore much cheaper, systematic observation of data about people. This new form of monitoring, whose descriptor I abbreviated to 'dataveillance', is potentially highly privacy-invasive. I later reviewed progress, in .
A second paper, 'Human Identification in Information Systems: Management Challenges and Public Policy Issues' (1994, published in a leading international journal), further develops a vital aspect of the argument: the nature of human identification as it is applied within information systems. Remarkably, there are very few works in any academic literature which address the question of such uses of human identity, and for this reason the paper had a long gestation period (from 1985 until 1994).
The paper 'The Digital Persona and Its Application to Data Surveillance' (1994, published in a leading international journal) introduced a new concept, the 'digital persona', as a tool in the analysis of behaviour on the 'net. It applies the tool, together with data surveillance theory, to predict the monitoring of the 'real-life' behaviour of individuals and groups through their net behaviour. The concept of 'nym' is related to (but not identical to) what I mean by 'digital persona'. Nyms are addressed in the following section.
Another important development in the ideas was in Person-Location and Person-Tracking: Technologies, Risks and Policy Implications (1999-2001).
I've reviewed Progress with the Concepts a few times, here:
The following two are less pretentious than the above papers, but they contain some important ideas:
The many articles on Identity and Authentication are also relevant to dataveillance.
The following papers further develop various aspects of the notion:
A separate segment of this site lists c. 50 papers from 1996 to 2001 on ePrivacy topics.
I've published several score more since then, including:
Search here using terms that describe the specific topic you're interested in (e.g. <"social networking">,< Google privacy>, <P2P>, <Web 2.0>, <mobile privacy>, <crypto>, <"deep packet inspection">, <ENUM>, <Gen-Y>, <"social networking">, <"social media">).
This theme was introduced in Person-Location and Person-Tracking Technologies, initially presented at the 1999 conference of Privacy and Data Protection Commissioners, and reported on in The Melbourne Age in August 1999. The final version was published in a leading international journal in 2001.
An important analysis was provided as an Addendum: Relevant Characteristics of Person-Location and Person-Tracking Technologies.
Further forays into this area included 'Mobile Technologies' and 'Privacy on the Move: The Impacts of Mobile Technologies on Consumers and Citizens' (May 2003), followed by 'Wireless Transmission and Mobile Technologies' (October 2003)
The ideas were pursued further in 2008, with a pair of papers on 'You Are Where You've Been: Location Technologies' Deep Privacy Impact' – YAWYB, Sydney and YAWYB, Canberra.
Other contributions have been:
In 2016, I coined the term 'Digital Surveillance Economy' to
refer to a new form of business model that has emerged since the beginning
of the 21st century. This model is predicated on the acquisition, expropriation
and consolidation of very large volumes of personal data, and its exploitation
in order to target advertisements, manipulate consumer behaviour,
and price goods and services at the highest level that each individual is
willing to bear. A key feature of it is dependence of organisations on management
of the digital persona rather than the person.
The exposition is in Risks Inherent in the
Digital Surveillance Economy: A Research Agenda (2019, in A* journal JIT).
The model can be seen as a more grounded cousin of Shoshanna Zuboff's
'Surveillance Capitalism', published in the same journal 4 years earlier
The following papers are some of the predecessors> to this theme:
The following papers present the development of the theme:
The term überveillance / ueberveillance / uberveillance was coined by Michael & Michael in 2006. It can be used to refer to:
See:
See the separate segment of this site on 'Identity Matters', including Biometrics.
See the separate segment of this site on Authentication.
See the separate segment of this site on national id schemes in Australia. This section contains only those papers that have general relevance to the topic:
I coined the term 'PIT' in late 1998. An explanation is in Introducing PITs and PETs: Technologies Affecting Privacy (March 2001). See also my PITs and PETs Resources Site (February 2001). The remainder of this section provides references to papers on particular technologies that adversely affect privacy.
An early paper, 'Database Retrieval Technology and Subject Access Principles'(1984; with Graham Greenleaf, published in the Australian Computer Journal), is concerned with data retrieval technology. It examines the scope for a particular form of database technology to render impractical an established privacy-protective mechanism, the so-called 'subject access principle'. This case study exemplifies the way in which developments in information technology undermine privacy protection laws. It provides a basis for understanding the impact of other developments, such as 'reverse access' to telephone directories, monitoring of energy usage, textual analysis, 'data mining', and the discovery of individual characteristics through the analysis of seemingly anonymous, statistical collections.
An invitation to a Symposium in Bielefeld provided the opportunity to revisit the general topic 30 years later, in Freedom and Privacy: Positive and Negative Effects of Mobile and Internet Applications (2015) and A Framework for Analysing Technology's Negative and Positive Impacts on Freedom and Privacy (2016).
Field work, undertaken in both the United States and Australia between 1987 and 1992, resulted in a series of papers on Computer Matching:
Since I undertook that work in the period 1987-92, an enormous range of blunders have been committed by practitioners of the black art of data matching.
A project popularly referred to as 'Robo-Debt' was a particularly vicious assault on the lower socio-economic strata of Australian society. It was perpetrated by Scott Morrison, with active enablement by a flotilla of senior executives in several federal government agencies, during the period 2014-23. A detailed case study is in 'Robodebt: An Exemplary Case Study of a Failed Transformative IT Project in the Public Sector' (2020-24).
The paper 'Trails in the Sand' (1996) highlights the wide range of transaction trails that people leave behind them.
Another technique, Profiling, was examined in 'Profiling: A Hidden Challenge to the Regulation of Data Surveillance' (1993). A later paper examines 'Customer Profiling and Privacy: Implications for the Finance Industry' (1997).
A comprehensive paper examines Direct Marketing (February 1998), including mail, fax, outbound tele(phone)-marketing, and Internet marketing. Related topics that have been addressed include spam, cookies and emailing lists.
Another area of importance has been public key infrastructure (PKI) to support digital signatures. A long series of papers published in that area is indexed here.
This theme was evident in a number of my papers from 1986 onwards. The first time that I wrote a paper on the topic itself, however, was in 2017, for the APF. The following list includes several other items that relate to the issue:
I've addressed AI tangentially many times. Listed here are the results of more specifically targeted works:
For papers on IoT, eObjects, Pervasive/Ubiquitous Computing, etc., see this index.
This concept dates to 1995. My key papers in this area are:
An early series of papers addresses security aspects:
updated from 2012:
A series of papers has considered technologies whose purpose is to directly support privacy. This work is primarily in:
I was active in the original W3C Working Group on P3P (Platform for Privacy Preferences). Unfortunately, the initiative fell so far short of its aspirations that it is not worthy of the name 'PET'. All of the following appeared in Privacy Law & Policy Reporter:
In the 1970s, government agencies and corporations resisted calls for privacy protections. During the intervening decades, many of them have come to recognise privacy as a factor that can harm their business, and that therefore needs to be addressed in a positive manner.
I have performed many consultancy assignments in this area during the last two decades. This section identifies published papers that are addressed specifically to business enterprises and government agencies, firstly in matters of general strategic significance, and secondly in the specific area of privacy impact assessments (PIAs).
The primary papers I've published on privacy as a strategic factor for corporations and government agencies are as follows:
Here's a catalogue of disasters that arose because the above advice was ignored:
Guidance on specific matters of a strategic nature is provided in:
See Security on the eBusiness index-page.
I've performed a considerable number of consultancies in this area (see client list). Important among them have been the preparation of guidelines for the performance of PIAs (1998), the review of guidelines prepared by government agencies (1999, 2006), research reports on PIA laws, policies and practices in the Asia-Pacific (2007), lead-authorship in the drafting of the UK Information Commissioner's PIA Handbook (2007), and training materials for the Hong Kong Privacy Commissioner's staff (2010).
My published papers in the area are:
Clarke R. (1998) 'Privacy Impact Assessment Guidelines' Xamax Consultancy Pty Ltd, February 1998, at http://www.xamax.com.au/DV/PIA.html (long form), http://www.rogerclarke.com/DV/PIA.html (short form)
Clarke R. (2004) 'A History of Privacy Impact Assessments' Xamax Consultancy Pty Ltd, February 2004
Clarke R. (2004) 'The Search for Balance: The Past, Present and Future of Privacy Impact Assessments' Presentation, Queens University, Kingston ON, 9 June 2004
Clarke R. (2004) 'Identity Management; and PIAs' Presentation, Office of the Privacy Commissioner of Canada, 11 June 2004
Clarke R. (2005) Submission
re the Commonwealth Privacy Commissioner's PIA Guidelines Australian
Privacy Foundation,
February 2005
Clarke R. (2005) Submission re the Victorian Privacy Commissioner's PIA Guidelines Australian Privacy Foundation, February 2005
Clarke R. (2008) 'Privacy Impact Assessment in Australian Contexts' Murdoch eLaw Journal 15, 1 (June 2008), Preprint at http://www.rogerclarke.com/DV/PIAAust.html
Clarke R. (2009) 'Privacy Impact Assessment: Its Origins and Development' Computer Law & Security Review 25, 2 (April 2009) 123-135, PrePrint at http://www.rogerclarke.com/DV/PIAHist-08.html
Warren A., Bayley R., Bennett C., Charlesworth A.J., Clarke R. & Oppenheim C. (2008) 'Privacy Impact Assessments: International experience as a basis for UK Guidance' Computer Law & Security Report 24, 3 (April-June 2008) 233-242
Warren A., Bayley R., Bennett C., Charlesworth A.J., Clarke R. & Oppenheim C. (2009) 'Privacy Impact Assessments: The UK Experience' Proc. 31st Int'l Conf. of Data Protection and Privacy Commissioners, Madrid, September 2009
Clarke R. (2010) 'PIAs in Australia - A Work-in-Progress Report' Review Draft of a chapter for Wright D. (ed.) (2011) 'Privacy Impact Assessments: Engaging stakeholders in protecting privacy' 30 September 2010, Xamax Consultancy Pty Ltd, PrePrint at http://www.rogerclarke.com/DV/PIAsAust-11.html
Clarke R. (2011) 'An Evaluation of Privacy Impact Assessment Guidance Documents' International Data Privacy Law 1, 2 (March 2011), PrePrint at http://www.rogerclarke.com/DV/PIAG-Eval.html
APF (2013) Meta-Principles for Privacy Protection', Australian Privacy Foundation, April 2013
APF (2013) 'Privacy Impact Assessments', Australian Privacy Foundation, April 2013
Clarke R. (2014) 'Approaches to Impact Assessment' Notes for a Panel Presentation at CPDP'14, Brussels, 22 January 2014
Clarke R. (2016) 'Privacy Impact Assessments as a Control Mechanism for Australian National Security Initiatives' Computer Law & Security Review (March 2016), used as a basis for a segment on ABC Lateline
Clarke R. (2017) 'The Distinction between a PIA and a Data Protection Impact Assessment (DPIA) under the EU GDPR' CPDP, Brussels, January 2017
Clarke R. & Taylor K. (2018) 'Towards Responsible Data Analytics: A Process Approach' Proc. Bled eConf., June 2018, plus slide-set
Clarke R. (2018) 'The Responsible Application of Data Analytics' Presentation to D2D CRC, Adelaide, and slide-set
_____
The following documents were contributed to as part of a consultancy assignment:
ICO (2007a) 'Privacy Impact Assessment Handbook' UK Information Commissioner's Office, version 1, November 2007 – for which I was lead-author
ICO (2007b) 'Privacy Impact Assessments: International Study of their Application and Effects' UK Information Commissioner's Office, 2007 – Report mirrored, and Appendices mirrored. I was a contributing author for the Report, and sole author of the following Appendices:
Note that the 2007 Handbook was the substantive version for only 18 months, after which it was replaced successively by:
ICO (2009) 'Privacy Impact Assessment Handbook' UK Information Commissioner's Office, version 2, June 2009
ICO (2014) 'Conducting privacy impact assessments code of practice' UK Information Commissioner's Office, February 2014
A Privacy Policy Statement (PPS) is a web-page that makes statements about the web-site owner's privacy policies. The device is talked about by business and government as if the concept mattered, even though its significance is very low. Nonetheless, some guidance is provided in:
It is widely claimed that information technology is becoming pervasive, and is giving rise to an 'information economy' and an 'information society'. If that is the case, then its impacts will be substantial, and must be managed. This part of my collection of papers is concerned with public policy regarding dataveillance.
This section identifies clusters of papers on specific issues not elsewhere addressed in this index.
I identified what I then saw as the Five Most Vital Privacy Issues, (July 1997), for the Montreal Daily, Le Devoir, prior to the International Conference on Privacy, Montreal. A resource-page was maintained for a few years, 1996-2006, citing surveys of public attitudes to privacy issues.
A paper published in a major U.S. journal argued that Internet Privacy Concerns Confirm the Case for Intervention (1999), and that that last renegade among advanced western nations would find it necessary to establish a statutory framework for privacy protections in the private sector. This paper also specified the requirements of a genuinely 'co-regulatory' approach.
The serious inadequacies in the 'Fair Information Practices' model of privacy protection were stated in Beyond the OECD Guidelines: Privacy Protection for the 21st Century (Jan 2000), which identified the many additional steps urgently necessary if a collapse in consumer and citizen confidence were to be avoided.
The apparent progress during the post-Cold War 1990s came to a shuddering halt on 11 Sep 2001 ("9/11" in IS parlance). Shaven-headed national security extremists grasped the opportunity with both hands, regaining dominance over desperately timid parliamentarians.
SO, two decades later, it was necessary to come forward with a reviewed proposal for A Comprehensive Framework for Regulatory Regimes as a Basis for Effective Privacy Protection (for CPDP, Brussels, 2021).
Many of my papers pursue positive arguments about what specific policy measures should look like. The most important of these are:
Others include:
Resources (March, 2017, major revision):
A paper on the OECD's Data Protection Guidelines (1989) provides a template for evaluating laws, and proposals for laws, and has been applied in a number of countries.
Many of my papers examine the inadequacies of the 'official response' by Parliaments and Governments, which involves providing mere 'fair information practices' protections. The intellectual basis underlying thse arguments is in 'Beyond the OECD Guidelines: Privacy Protection for the 21st Century' (January 2000).
The following comments were made on the dreadful Privacy Amendment (Private Sector) Act 2000. It passed into law in December 2000, and became [in]effective on 21 December 2001:
A specific matter of concern is public key infrastructure (PKI), and the use of digital signatures for identity authentication. A long list of papers is indexed above. Two that are particularly oriented towards the policy aspects are 'eAuthentication: Where's the Public Interest?' (2003), and Identity Management; and PIAs (2004).
Another concern is 'ENUM' (March 2003).
Yet another is the mindless enthusiasm for biometrics that has arisen as a result of the dominance of 'national security' over both civil liberties and logic, aided and abetted by fraudulent representations by technology providers. A specific critique is at:
Another criticism was of the fatuous 'data breach notification' laws, a placebo that was still being discussed in Australia a full decade after such a law might have been of some value:
A paper on an of European law from 2018 is 'The Distinction between a PIA and a Data Protection Impact Assessment (DPIA) under the EU GDPR' (2017)
We opened up a new stream of research in 2016-17:
The Ethics and Law of Privacy in the Digital Age, Notes for National Science Week Event, Adelaide, August 2018, and slide-set
A submission to a pseudo-review of the Privacy Act (Cth) was used as an opportunity to hammer a few points, in Bringing Australia's Privacy Act up to international standards (2020, with Greenleaf et al.)
Papers between 1996 and 1999 were:
Older papers that are now of primarily historical interest are as follows:
Organisational self-regulation without a layer of statutory regulation underpinning it is not a form of privacy protection, but a mere pretence. This is addressed in a number of places, including:
A major paper provides guidance to corporations and government agencies concerning 'Privacy and Dataveillance; and Organisational Strategy' (1996, a keynote presentation at an Australian Conference).
Observations concerning a particular industry code are provided in 'Smart move by the smart card industry: The Smart Card Industry's Code of Conduct - Part I' (1996) and Part II (1997). Both were published in the Privacy Law & Policy Reporter.
See also:
A paper entitled 'Economic, Legal and Social Implications of Information Technology' (1988, published as an 'Issues and Opinions' piece in a leading US journal) provides a discussion of the ethics of academic endeavour in the information systems discipline. It argues that information technology's impacts are so great that detached observation is an inadequate stance for an information systems academic.
Information systems researchers must engage themselves in their subject-matter, and extend themselves beyond mere description and explanation, and even beyond the prediction of the outcomes of artefact design and interventions in organisations and society. Information systems researchers are irretrievably involved in the process of engineering organisations and society, and cannot meaningfully sustain the pretext that they are entirely uninterested in, and unaffected by, the processes around them. These issues are examined in 'Data Surveillance: Theory, Practice and Policy' (July 1997). That paper argues that policy issues in general, and information privacy in particular, are not only an appropriate area of focus for information systems researchers, but that they are also capable being approached in a sufficiently disciplined manner.
Here is the Australian Computer Society's ELSIC Committee, which I chaired 1984-95, and of which I continue to be an active member.
An outline is provided of 'Information Systems Audit & Information Privacy' (1997), and resources are provided for Privacy Impact Assessments (1998) and (2004).
Other papers on this topic include:
Self-regulation by research professional in the I.S. discipline is considered in considered in 'Information Privacy in a Globally Networked Society: Implications for Research', plus slide-set (December 2002). The contributions to the panel session were later published as 'Information Privacy in a Globally Networked Society: Implications for IS Research' (October 2003).
A further paper comments on the social responsibility of engineers, plus PowerPoint slides (2002).
(Ir)responsibility among IS researchers is considered in 'Whose Data is it Anyway? The Researcher Perspectives Evident in IS Privacy Research', (Preliminary Draft, January 2019)
Here's a lecture on IT and Data Ethics (ANU, 2020)
Like other technologies, computing and telecommunications are capable of being applied to the benefit of humanity as a whole, or of particular interest groups within society. Use of information technology by the politically powerful as a means of exercising control over the thoughts and actions of members of the public, is a matter of especial concern to those living in democracies.
A paper entitled 'Information Technology: Weapon of Authoritarianism or Tool of Democracy?' (1994; presented at the World Congress of computing academics) identifies critical implications of information technology for democracies. It represented a response to a paper submitted to the conference by a senior government executive of a country that had previously been dominated by the U.S.S.R., and that has no tradition of democracy as it is known in 'western' countries.
This paper's importance is that it lifts the application of the theory of dataveillance from the individual and social levels to the political level, and is a first, tentative step toward the building of a bridge between the theory of dataveillance (developed, as it has been, largely from within the information systems discipline), towards broader theories arising in anthropology, sociology and political science.
Other papers that consider broader issues related to dataveillance include:
This section identifies papers that deal with matters specific to Australia.
Many years ago, I hoped to use this sub-section to maintain a list of current issues. But because privacy-invasive technologies and applications are so rampant, it's extremely difficult to keep up ...
I drafted a summary paper – a history of privacy in Australia (December 1998). And I started what was intended to be a living document on current developments, with this update.
Some time later, I made these notes on the history of the Australian Privacy Foundation, 1987-2017 (2017)
But the most effective way to follow current issues is to subscribe to the privacy list.
Papers on National Identification schemes generally are in a separate section, above. This section addresses the specifics of the ongoing attempts by executives in Australian government agencies and Australian politicians to implement extremist social control mechanisms in this country.
During the period 1985-87, the Commonwealth Government developed a proposal to implement a central database of the Australian population, whose purpose, expressed in terms of the theory developed in this body of work, was the facilitation of dataveillance of all residents of this country. 'Just Another Piece of Plastic for Your Wallet: The Australia Card' (1987, published in an international technology policy journal) provides a carefully documented description and analysis of the proposal, a distillation of the issues, and a political history of the proposal's development and ultimate fate.
Another paper on the topic was 'National Identification Scheme - Costs and Benefits' (1986, published in an Australian journal).
Although the Australia Card proposal was withdrawn in the face of dramatically negative public opinion, the momentum that dataveillance applications of information technology had attained within the Commonwealth public sector was scarcely affected. 'The Resistible Rise of the National Personal Data System' (1992, published in an American journal of computers and law) documents a number of developments during the following three years. It is primarily a political history, expressed within the context set by the theory of dataveillance.
The untrustworthiness of a mere Prime Minister's assurances are underlined in 'The Tax File Number Scheme: A Case Study of Political Assurances and Function Creep' (1991, published in an Australian journal).
An attempt by law enforcement interests to create a highly privacy-intrusive scheme is documented in 'LEAN Times Ahead: The Proposed Law Enforcement Access Network' (1992).
The reasons for public concerns about government agencies are summarised in 'Why the Public Is Scared of the Public Sector' (1993, presented at an Australian conference).
The justification for a major computer matching scheme is shown to be incompetent or fraudulent, in 'Matches Played Under Rafferty's Rules: The Parallel Data Matching Program Is Not Only Privacy-Invasive But Economically Unjustifiable As Well' (1993, published in Privacy Law & Policy Reporter).
Echoes recur continually. In April 1999, the Commonwealth Auditor-General, Pat Barrett, sought to revive the process of extending the Tax File Number, this time into the Medicare arena (ANAO 1999). His proposal was then considered by the House of Representatives Standing Committee on Economics, Finance and Public Administration (EFPA). Too pressed for time to provide yet another time-wasting submission to yet another government committee, I submitted a brief letter (November 1999).
During the 1990s, bureaucrats achieved merger of all government benefits schemes, and correlation of identifiers, by means of Centrelink. Despite resistance going back 15 years, they eventually succeeded in combining the health insurance and pharmaceutical benefits schemes in to a single agency. Then in the early 2000s, the centralist's dream of a 'super-ministry' was achieved, euphemistically called Human Services, which enable the benefit schemes, health systems and child support agency to be drawn even closer together.
Meanwhile, a succession of attempts were made to upgrade drivers' licences into a much broader social control scheme. See Submission to Queensland Transport in relation to the Proposed Smartcard-Based Driver's Licence (2003).
Then in mid-2005, the Queensland Premier Beattie, in an endeavour to shift media attention away from serious problems in his State, suggested that an Australia Card was needed. The Prime Minister ran with it. A cluster of identity schemes was progressively drawn into one being developed by the 'Human Services' Minister dubbed the Access Card.
Advocacy groups and the media have caused a great deal of pertrubation in the statements made by politicians and bureaucrats about the scheme. The resolve with which it is being pursued by the Government appears set to bring down another Minister in due course.
Documentation about the schemes, the continual changes in Government pronouncements, and the privacy advocacy campaigns, is at:
Papers on the topic during this period include the following:
This series of attempts by the bureaucracy supported by extremist elements behind and within the Liberal Party, failed. (Even the reactionary Attorney-General Phillip Ruddock, didn't have the stomach for it). An opportunist Minister, Joe Hockey, offered to dress the proposal up differently, leading to ...
The story is told in this page on the Dept of Human Services' So-Called 'Access Card' (2006-07).
It collapsed. The APF had ensured that the media were well-informed. But, significantly, the proximate cause of the collapse was that rarity, a Senate Committee Chair (i.e. a Government member, not yet a Minister, but on the rise), whose Report comprehensively debunked it. (The Chair was Queensland Liberal Senator Brett Mason, whose PhD thesis and book had been highly uncomplimentary about privacy advocates).
Parallel State Government schemes included:
Presentations on the topic during this period include:
The Privacy Act, passed in December 1988, was carefully analysed in the following papers, which were distributed among a small community of interested researchers and government agencies:
A paper on 'Consumer Credit Reporting and Information Privacy Regulation', summarised the situation in the lead-up to the 1989 extensions to the Privacy Act (1989). The resultant legislation was described in 'Privacy Regulation of Consumer Credit Reporting' (June 1989, published in an Australian journal, not available on the web).
The disastrously bad amendment Bill of 2000 was analysed and severely criticised:
It came into force on 21 December 2001, exacerbating rather than solving problems. For subsequent analyses, see:
This section is provided primarily as a matter of record, most recent first.
During 1989-90, a series of papers was prepared under consultancy assignments for the Commonwealth Privacy Commissioner, on:
During the period 1985-1990, several Policy Papers were prepared for the Australian Computer Society, on:
The situation in health care is discussed in 'Current Health Care Information Privacy Issues' (1990, invited paper at an Australian conference).
A series of assessments of earlier proposals for privacy regulation was published:
During 1978-80, a series of papers were prepared for Michael Kirby(later a High Court judge), in relation to the design of the OECD Guidelines.
During 1976-77, a series of papers was prepared while I was a Research Officer the N.S.W. Privacy Committee. This included:
During 1972-75, several papers were prepared on behalf of the N.S.W. Branch of the Australian Computer Society. At that time, it appeared that the N.S.W. Government might push through privacy protection legislation that could have been harmful to the then immature computer industry. I led the professional association's lobbying against unreasonable regulation. I was too successful: N.S.W. passed no substantive law until 1998, and then came up with what was until December 2000 the world's worst privacy protection legislation ...
| Personalia |
Photographs Presentations Videos |
Access Statistics |
 |
The content and infrastructure for these community service pages are provided by Roger Clarke through his consultancy company, Xamax. From the site's beginnings in August 1994 until February 2009, the infrastructure was provided by the Australian National University. During that time, the site accumulated close to 30 million hits. It passed 65 million in early 2021. Sponsored by the Gallery, Bunhybee Grasslands, the extended Clarke Family, Knights of the Spatchcock and their drummer |
Xamax Consultancy Pty Ltd ACN: 002 360 456 78 Sidaway St, Chapman ACT 2611 AUSTRALIA Tel: +61 2 6288 6916 |
Created: 15 February 1995 - Last Amended: 31 December 2023 by Roger Clarke - Site Last Verified: 15 February 2009
This document is at www.rogerclarke.com/DV/index.html
Mail to Webmaster - © Xamax Consultancy Pty Ltd, 1995-2022 - Privacy Policy