Roger Clarke's Web-Site
© Xamax Consultancy Pty Ltd, 1995-2024

Infrastructure
& Privacy
Matilda
Roger Clarke's Web-Site© Xamax Consultancy Pty Ltd, 1995-2024 |

|
|||||
| HOME | eBusiness |
Information Infrastructure |
Dataveillance & Privacy |
Identity Matters | Other Topics | |
| What's New |
Waltzing Matilda | Advanced Site-Search | ||||
Version of 13 August 2015
Computer Law & Security Review 32, 3 (May-June 2016) 403-418
Used as a basis for a segment on ABC Lateline, 24 August 2015
© Xamax Consultancy Pty Ltd, 2015
Available under an AEShareNet ![]() licence or a Creative
Commons
licence or a Creative
Commons  licence.
licence.
This document is at http://www.rogerclarke.com/DV/IANS.html
Democracy in Australia is gravely threatened by a flood of measures harmful to human rights that have been introduced since 2001, a large proportion of which are unjustified and not subject to effective controls. The passage of these measures through the Parliament has been achieved on the basis of their proponents' assertions and without appropriate scrutiny. Parliament had available to it various forms of impact assessment techniques, but failed to require that such methods be applied. The study reported here found that one particular form of evaluation, Privacy Impact Assessment (PIA), should have been performed, but was seldom applied, and where it was applied the process and report were in almost all cases seriously deficient. Survival of democracy is dependent on the Parliament standing up to the national security extremism that has taken hold of the Attorney-General's Department. Ministers and Parliamentary Committees must demand prior evaluation of proposals that restrict civil freedoms, must ensure transparency in relation to the proposals and their justification, and must require effective controls over, and mitigation features within, those measures that survive the evaluation process.
The last 15 years have seen the passage through Australian Parliaments of scores of statutes containing hundreds of provisions that embody unprecedented threats to human rights and freedoms. The national security extremists who have grasped power within the public service since 2001 have successfully sustained an ongoing scare campaign, aided and abetted by a credulous media. Parliament has become dominated by the Executive, and in particular by the Attorney-Generals' Department (AGD). The vast majority of MPs and Senators have been, and remain, cowed by a combination of party staff, departmental briefings and opinion polls driven by the media. As and when a genuine emergency arises in Australia, the increased numbers of law enforcement agencies, with their vastly increased resources and their increasingly para-military organisational arrangements, are in a strong position to exercise the wide-ranging powers and curtail democratic processes.
The human rights that are under threat are highly diverse. Appendix 1 contains a list of widely-recognised rights, extracted from AHRC (2015). Rights that have been compromised by national security measures since 2001 include freedom from arbitrary detention (ICCPR Art. 9), freedom of movement (Art. 12), right to a fair trial (Art. 14.1), minimum guarantees in criminal proceedings (Art.14.2-14-7), privacy (Art.17), freedom of information, opinion and expression (Art. 19) and freedom of association (Art. 22), and possibly also rights to equality and non-discrimination (Arts. 2.1, 26, 27), freedom from torture (ICCPR Art. 7), retrospective criminal laws (Art.15), freedom of assembly (Art. 21) and right to nationality (Art.24). It is conventional to define human rights within the context of the International Covenant (ICCPR 1966). However, it is arguably inappropriate to do so in Australia, because, almost alone among its reference group, it does not have human rights entrenched in its Constitution. Moreover, the federal Parliament has steadfastly refused to comply with its obligations under international law, which nominally compel it to implement human rights by means of legislative provisions.
This paper's purpose is to document the last 15 years' incursions into human rights using the excuse of 'the terrorist threat'. It is necessary that such analyses be undertaken now, before the increasing constraints on access to information and publication of information render them illegal, and unsafe for the individual conducting them. In order to keep the scale of the challenge within bounds, a narrow lens has been used. Firstly, the focus is on the cluster of human rights associated with privacy. Secondly, the analysis is framed in terms of the impacts on privacy of measures that have been identified as national security and/or counter-terrorism initiatives. Thirdly, the specific question asked is to what extent the privacy impacts have been subjected to assessment prior to being put before the Parliament and enacted.
The paper commences by providing working definitions of key terms. This is followed by a brief overview of the statutes and measures imposed during the period 2001-15. It then reports on a study undertaken of the extent to which the technique of Privacy Impact Assessment (PIA) has been applied to those proposals.
This section provides brief reviews of several matters than underlie the analysis that follows. It first describes privacy as a cluster of aspects of human rights, and then outlines the protections for privacy in Australia. Working definitions of the terms 'national security' and 'counter-terrorism' are provided. The various forms of impact assessment are surveyed, with a particular focus on those most relevant to privacy. Finally, relevant government policies are identified relating to the conduct of PIAs.
This section draws very heavily on a summary previously published in Clarke (2014c). Privacy is expressed as a human right in the Universal Declaration (UDHR 1948, particularly Art. 12) and the International Covenant (ICCPR 1966, particularly Art. 17). When conducting policy analysis, however, it has proven to be much more convenient to define it as "the interest that individuals have in sustaining a 'personal space' free from interference by other people and organisations" (Morison 1973). This underlines the fact that privacy is one interest among many. Hence all privacy protections are an exercise in balance among multiple considerations. Contrary to the organisation-serving precepts popularised by Westin (Harris & Westin 1995), there are no 'privacy fundamentalists' who adopt an absolutist position on privacy rights; almost all rights are universally acknowledged as being to some degree relative, including privacy.
The human need for privacy has multiple dimensions (Clarke 1997, 2006), summarised in Figure 1. Despite privacy's allegedly recent origin as a preoccupation of well-off societies, all of these dimensions are readily recognisable in the Universal Declaration and the International Covenant.
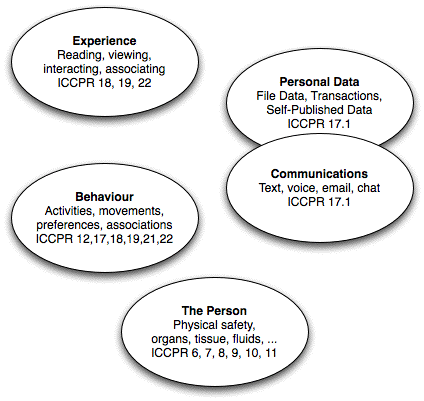
The deepest-seated need is for privacy of the physical person, which is addressed by a large number of Articles in ICCPR. It's useful to distinguish four further dimensions. Surveillance, whether it is conducted in a physical manner (using the eyes and ears of humans), aided by technologies (such as directional microphones and recording apparatus), or entirely automatically, threatens the privacy of personal behaviour and thereby constrains how people act. Covert surveillance causes many people to have a generalised fear of the 'pan-optic', which has an even more substantial impact on their freedom of behaviour. This 'chilling effect' ranges from being highly desirable (where it creates a disincentive for criminal, psychopathic and sociopathic behaviour) to highly undesirable (where it reduces artistic creativity, scientific and engineering inventiveness, economic innovation or political speech, or dehumanises individuals and thereby increases criminal, psychopathic and sociopathic behaviour).
Since at least the early days of the telegraph in the 1840s, messages have been subject to electronic interception, which is much easier to conduct covertly than most earlier forms of surveillance. Recent decades have seen invasions of the privacy of human communications reach epidemic proportions. Since the application of computing technologies to administrative data in the 1960s, the privacy of personal data has also been subject to a rapidly-rising crescendo of threats (Clarke 1988). During the 1970s, business and government moved to dissipate public concerns by creating a smokescreen rather than a shield, in the form of the 'fair information practices' movement (OECD 1980, Clarke 2000). The real function of 'data protection' laws is to authorise privacy-invasive behaviours by organisations while offering the appearance of a regulatory framework.
The early years of the current century have seen technological change that embodies serious threats to a further dimension of human concerns. What an individual reads and views, and the ideas that they gain access to through meetings and other events, have been converted from unrecorded ephemera to stored data. That data is under the control of and exploitable by for-profit corporations, and available to government agencies. The privacy of personal thought may not yet be directly under assault, but the privacy of personal experience is a dangerously close proxy for it.
In 1986, the four higher-level dimensions of privacy were referred to by Health Minister Neal Blewett, while he was championing the Australia Card, as 'a bourgeois right' (Clarke 1987). It is certainly the case that a person who is in danger, wet and cold, or seriously hungry, does not have the luxury of worrying about needs higher up the Maslowian hierarchy. On the other hand, people in many societies enjoy pleasant living conditions, and place considerable value on these dimensions of their privacy, for psychological, social, economic and political reasons.
This paper is particularly concerned about the scope for a privacy-invasive surveillance society to constrain political freedoms to the extent that democracy is undermined. Aspects of this were investigated in Clarke (2008).
The most direct reference to privacy in ICCPR (1966) is in Art. 17.1 - "No one shall be subjected to arbitrary or unlawful interference with his privacy, family, home or correspondence". This is subject to an explicit and specific requirement in Art. 17.2: "Everyone has the right to the protection of the law against such interference and attacks". The Australian Constitution embodies no such protections, and the Parliament has failed to enact effective legislative provisions. Only one Territory (ACT in 2004) and one State (Victoria in 2006) have human rights legislation. In both cases, however, they include only the Art. 17.1 wording, and omit 17.2, thereby rendering the two statutes nugatory.
Data protection measures of the FIP kind, heavily influenced by OECD (1980), were enacted in 1988 in respect of Australian government agencies and in 2000 in respect of some of the private sector. However, these long and very complex provisions contain a vast array of designed-in exemptions and exceptions, and they were greatly weakened by amendments in 2012. The law is in any case infinitely malleable and subject to continual depradations through amendments slid into other legislation. The three largest States and the two small Territories have weak data protection laws, while the remaining three States have no meaningful data protection laws in place. The five Privacy Commissioners are under-resourced, weak oversight agencies, not strong regulators, let alone watchdogs.
In relation to the other dimensions of privacy, there are scatters of incoherent and inadequate laws. An indication of their patchwork-quilt nature is provided by analyses of the laws relating to visual surveillance in Clarke (2013 and 2014b). The Privacy Commissioners' have limitations outside the data privacy area, and in any case rarely exercise such powers as they have in relation to other dimensions.
A theoretical definition of national security, from a US legal dictionary, is "The protection of a nation from attack or other danger by holding adequate armed forces and guarding state secrets. Encompasses economic security, monetary security, energy security, environmental security, military security, political security and security of energy and natural resources". In practice, a great deal of the public discussion about national security falls into the following areas:
Since 2001, the sale to the Australian public that national security is the most important thing that they should be worried about has been almost entirely based on public safety aspects, using the term 'counter-terrorism', and with a very strong emphasis on the threats to it arising from Islamic fundamentalism. Frequent reminders are given of the major strikes in New York and Washington in 2001, Bali in 2002 and 2005, Jakarta in 2003, 2004 and 2009, Madrid in 2004, London in 2005 and Mumbai in 2008. Among the 202 who were killed in the Bali attack in 2002 were 88 Australians. In addition, a handful of Australians have died in other attacks around the world.
In Australia, meanwhile, the terrorist threat has been very limited. Since 2001, despite periodic large-scale raids, law enforcement agencies have successfully prosecuted a total of only 15 individuals in relation to 6 instances of preparation to commit an act of terrorism-related violence in Australia (AGD 2013, pp. 102-111. See also Lynch et al. 2014, pp. 94-97). During the 15 years since the World Trade Center attacks, there have been well over 20,000 deaths from vehicle accidents, whereas terrorism has given rise to zero deaths and injuries on Australian soil, and no harm to property. The rhetoric used by and on behalf of national security extremists vastly exaggerates the reality.
Impact assessment in the environmental space has a long history. In the name of 'red tape reduction' and Budget considerations, the Australian Parliament has instituted Regulatory Impact Assessment and Financial Impact Assessment in relation to Bills placed before it. On the other hand, the Parliament has signally failed to do the same in relation to impacts on society. A wide variety of impact assessment techniques exist, as evidenced by Table 1.
Extract from Clarke (2014a)
The study reported on in this paper adopted as its focus neither the broader forms early in the Table, nor the narrower forms in the later parts of the Table, but rather the PIA technique, which is concerned specifically with privacy, but which extends to all of the dimensions of privacy outlined in s.2.1 above. After a slow start in the 1990s, Privacy Impact Assessment techniques are now the subject of an expanding literature. See, in particular, Clarke (2009) and Wright & De Hert (eds) (2012). Practices around the world were documented in ICO (2007). For an evaluation of the guidance issued by government agencies around the world, see Clarke (2011).
In order to establish a comprehensive framework for privacy protection, the Australian Privacy Foundation declared a set of 'meta-principles', which are reproduced in Table 2. These consolidate a set of well-known requirements that together represent a benchmark against which the quality of a PIA can be measured.
Extract from APF (2013)
All proposals that have the potential to harm privacy must be subjected to prior evaluation against appropriate privacy principles.
All evaluation processes must feature consultation processes with the affected public and their representative and advocacy organisations.
Sufficient information must be disclosed in advance to enable meaningful and consultative evaluation processes to take place.
All privacy-intrusive aspects must be demonstrated to be necessary pre-conditions for the achievement of specific positive outcomes.
The benefits arising from all privacy-intrusive aspects must be demonstrated to be commensurate with their financial and other costs, and the risks that they give rise to.
Where privacy-intrusiveness cannot be avoided, mitigation measures must be conceived, implemented and sustained, in order to minimise the harm caused.
All privacy-intrusive aspects must be subject to controls, to ensure that practices reflect policies and procedures. Breaches must be subject to sanctions, and the sanctions must be applied.
All privacy-intrusive aspects and their associated justification, proportionality, transparency, mitigation measures and controls must be subject to review, periodically and when warranted.
This section examines the basis on which it is contended firstly that a public policy imperative exists in Australia to conduct PIAs in relation to Bills, government programs and new and amended applications of technology.
The immediate ancestor of PIAs was the 'program protocol' imposed from 1990 onwards on one particular program by the Data-Matching Program (Assistance and Tax) Act. The 'Guidelines for the Conduct of the Data-Matching Program' of 31 October 1994 remain in force, but with a sunset clause of 1 October 2019. Generic 'Guidelines on Data Matching in Australian Government Administration', which also had a program protocol at their core, were published in 1992 (current version of June 2014).
Following a lengthy development and consultation period, the Australian Privacy Commissioner published guidance in relation to the conduct of PIAs in 2006. This was lightly revised in 2010 and more substantially in 2014 (OAPC 2014). This Guide, since its revision in 2014, is among the best of the various Guides published by privacy oversight agencies around the world (Clarke 2011).
The orientation of the two Australian Privacy Commissioners who have held office since 2004 has been strongly toward the protection of the interests of government agencies and corporations, rather than of privacy. However, the Commissioners' attitudes to PIAs have been a very positive aspect of their performance. The message has been consistently given to agencies that PIAs are beneficial to organisations, and should be regarded as being part of normal government business.
There were early signs that the Guide would become mainstream. For example, " ... agencies should carry out a privacy impact assessment (PIA) before choosing and implementing an e-authentication mechanism in accordance with the PIA privacy guidelines released by the Office of the Privacy Commissioner in August 2006" (AGD 2007); and "[smart card] authorities shall undertake a privacy impact assessment" (DoF 2008). Moreover, on at least one occasion, the Privacy Commissioner directly conveyed the message in respect of major national security initiatives: "the OAIC strongly recommends that the [COAG Review of Counter-Terrorism Legislation] further recommend that Privacy Impact Assessments (PIA) be conducted in relation to these changes" (OAIC 2012).
The question arises as to whether agencies are free to conduct PIAs quietly, and avoid exposure of the proposal to the public generally and to advocacy organisations in particular. The Privacy Commissioner's original Guide in 2006 was excessively organisation-friendly and inadequate in its consideration of the interests of the public. There was little sense of transparency, and none of community input to policy development, of the inclusion of the affected public as a stakeholder, or of the achievement of a design that balances the interests of all stakeholders. Submissions were made to successive Commissioners to the effect that these aspects were inadequate. Improvements in the 2010 edition were very marginal. However the 2014 (and current) edition of the Guide states that "Affected individuals are likely to be key stakeholders, so public consultation is important ... [Stakeholders include] clients, advocacy organisations ... It is important that some form of targeted consultation is undertaken, ... such as with groups representing relevant sectors of the population, or advocacy groups with expertise in privacy" (pp.11, 12). So a PIA process that is conducted in secret, or that omits public consultation, is non-compliant with the Privacy Commissioner's Guide.
A further question is whether agencies can avoid publishing PIA Reports. The Privacy Commissioner's 2014 Guide states that: "The OAIC strongly encourages the publication of PIA reports. This contributes to the transparency of the project's development and intent, and demonstrates to stakeholders and the community that the project has undergone critical privacy analysis, potentially reducing community concerns about privacy. However, the OAIC acknowledges that there may be circumstances when the full release of a PIA report may not be appropriate; for example, if the project is still in its very early stages, or if there are security or commercial reasons for not releasing the full report. Where there are difficulties making the full PIA available, the OAIC encourages the release of a summary or edited version" (p. 32).
Moreover, all agencies are subject to 'proactive disclosure' obligations under ss.8-8E of the Freedom of Information Act, which were driven by Open Public Access Principle 1: "If there is no legal need to protect the information it should be open to public access". Although some occasions will arise when some content such as security-sensitive details may need to be put in closed Appendices, PIA Reports clearly fall into the category of documents to which a positive obligation to publish applies. The suppression of PIA Reports is accordingly at the very least contrary to government policy, and arguably in breach of the FoI Act.
Do organisations merely need to give people the opportunity to communicate their views, or do organisations need to reflect the views communicated to them by and on behalf of the affected public? The Privacy Commissioner's Guide is rather weak on this aspect, although it does say that "Potential benefits of undertaking a PIA include ... reflecting community values around privacy and personal information in the project design" (p. 2), "analysis should include any stakeholder or public consultation results that may assist you to work out how to improve the project's privacy outcomes" (p.18) , and the PIA Report is to include "privacy risks that have been identified, ... strategies already in place to protect privacy [and] recommendations to avoid or mitigate privacy risk" (p.30).
With effect from 12 March 2014, the Australian Privacy Commissioner gained the power to direct an agency to conduct a PIA. Recommendations 47-4 and 47-5 of the ALRC's 2008 Report on Privacy were based on the rationale that "encouragement and education [to agencies and organisations to conduct PIAs] should be supported by a power vested in the Privacy Commissioner to direct agencies to prepare a PIA in relation to projects that may have a significant impact on the handling of personal information, and for the Commissioner to report to the Minister on non-compliance with such a direction" (para. 47.72). The Recommendations were implemented by the creation of s.33D. The Second Reading Speech made clear that "It is expected that agencies will continue to voluntarily conduct privacy impact assessments as appropriate when developing policies which will impact on privacy, as part of their compliance with their obligations under the Privacy Act".
The issuance of a direction in respect of a project that was already well under way in March 2014 could, on the one hand, be seen as a draconian use of the power. On the other hand, where the privacy impacts of an initiative are substantial, it can be readily argued that the will of the Parliament was that it be applied to precisely such projects. In any case, there are already current initiatives that post-date the creation of the power. Fully 15 months after the section came into force, in June 2015, the Privacy Commissioner published a 'Guide to privacy regulatory action', dealing with, among other things, the s.33D power. It appears to be largely superfluous, and in effect a substitute for action. No evidence has been found of the Privacy Commissioner as yet exercising the s.33D power of direction.
During 2014, the Government deliberately emasculated the Privacy Commissioner's host organisation, the Office of the Australian Information Commissioner (OAIC), and at the end of the Privacy Commissioner's term in July 2015, he was appointed on a short-term basis to the vacant Information Commissioner's post, forcing him to perform the functions of all three Commissioners. It is entirely possible for a very part-time Privacy Commissioner on a very short term contract to issue a direction to an agency to perform a PIA. However, AGD and successive Attorneys-General have demonstrated themselves to have no respect whatsoever for democratic conventions, so such an action could be seen to fall into the category of 'courageous'.
This section commences by outlining the method adopted in conducting the study. An overview is then provided of the very substantial numbers of measures enacted since September 2001. Based on detailed documentation provided in an Appendix, it identifies the extent to which PIAs have been performed, and to which those that have been undertaken fulfilled a number of key requirements.
The objective of the study was to provide understanding of the extent to which Privacy Impact Assessments can and have acted as a control mechanism over excessive measures associated with the national security and counter-terrorism memes. The study identified projects directly or indirectly associated with national security, and examined the extent to which PIAs have been undertaken, and their effectiveness.
In each case, the following five-factor test was applied:
There are strong policy and in some cases legal presumptions that the answers to these questions should generally be 'Yes', for all instances of proposals that are within the scope of this analysis. However, it was known in advance of the analysis that there was a low incidence of published Reports. So a sixth factor was included:
The data-gathering process exploited the author's personal archives and prior research, and those of the specialist advocacy organisation the Australian Privacy Foundation (APF). The APF is the world's longest-serving such organisation, having been formed in 1987. Its electronic archives of submissions and media reports are comprehensive throughout the period covered by this research. These sources were complemented by a review of literature relating to national security legislation in Australia, and by searches on the websites of the Australian Parliament and the relevant government agencies.
The meaning of the word 'terrorism' is subject to debate. It generally refers to acts of violence, or threats of acts of violence, whose intention is to strike fear into the general public or some segment of the public. The motivation is commonly the advancement of a political, religious or ideological cause. Acts are commonly not classed as terrorism where they are a thrill-seeking, psychopathic or sociopathic nature, or are targeted at an individual.
Acts of terrorism occur spasmodically in Australia. During the 1970-2001 period, there were about 10 events that might be classified as terrorism, i.e. about 1 every 3 years. These were associated with unrest in then-Jugoslavia, opposition to a visiting Indian Prime Minister and to the Turkish and French Governments, anti-Semitism and abortion. The situation in Australia in 2001 was that few of the perpetrators of terrorist acts had ever been brought to justice, but existing criminal law was regarded as being adequate to address the risk. Pre-existing laws criminalise attempts, conspiracy and incitement to commit an act of violence, and these are complemented by offences relating to weapons and explosives.
The justification for new criminal laws in Australia was provided by a hasty UN Security Council Resolution following the attacks on the New York Trade Center and the Pentagon. "Adopted on 28 September 2001, Resolution 1373 called upon states to ensure that `terrorist acts are established as serious criminal offences in domestic laws and regulations and that the punishment duly reflects the seriousness of such terrorist acts'" (Williams 2011, p.1140). The ambiguity of the words "are established as ... offences" was such that governments around the world were easily panicked into 'establishing' new offences rather than assessing 'already-established' offences to see whether any adaptation was necessary.
In Australia, "The [first four] Bills were introduced into the House of Representatives on 12 March 2002, and were passed by that House the next day" (Williams 2011, p.1164). The Bills were delayed in the Senate, but passed without significant changes in June 2002. This established a pattern that has been sustained for the intervening 13 years: "Those sponsoring the new measures sought to see them passed by Parliament as quickly and with as little scrutiny as possible". This was easier during the period 2004-07, when the government of the day had a majority in the Senate and "rode roughshod over parliamentary process and normal parliamentary timelines" (Williams 2012, p.1164).
During the Howard period 2001-07, 48 counter-terrorism statutes were passed (c. 7 p.a.). During the Rudd-Gillard period 2007-13, a little more circumspection was evident, but a further 13 statutes were enacted (c. 2 p.a.). The first 18 months of the Abbott period since late 2013 has already seen 4 further statutes (c. 3 p.a.), embodying some very substantial and highly intrusive measures, with more on the parliamentary table. The 65 statutes are listed in Appendix 2. Almost all of them involved multiple measures, and hence a list of measures rather than statutes would run into hundreds of line-items. Williams' set of categories for counter-terrorism measures is reproduced in Appendix 3.
Key instances of the 65 statutes' compromises to human rights are identified in Appendix 4. The powers have been matched with resources. ASIO's staff-count increased by a factor of 3 between 2001 and 2015, and its funding by a factor of 9 (Lynch et al. 2014, p.155). There have been a number of instances of abuse of various of the powers, those most well-publicised being in the Haneef case (Clarke J. 2008, Lynch et al. 2014, pp. 141-143) and the Ul-Haque case (Lynch et al. 2014, pp. 107-108, 157-158). Given that the compromises to human rights include multiple circumstances in which information disclosure and publication may be suppressed, there may have been further, unpublicised abuses. The most serious concern, however, is about the extent to which abuse will occur in the future, and to which it will not come to public knowledge, particularly if and when genuine emergencies arise and law enforcement agencies feel confident that they can exercise their powers with little likelihood of retribution.
Generally, later statutes have refined existing powers, and created many new powers, but "have not brought about any significant winding back of the anti-terror regimes" (Williams 2011, p.1145). There have been some instances of measures being delayed, and a variety of minor amendments have been made, but the proponents have rarely been required to demonstrate justification - as distinct from assert it, supported by undocumented anecdotes. In addition, a great many of the 65 Acts feature seriously inadequate controls and mitigation measures. Where reviews have been undertaken, the government has tended to implement the recommendations for further or enhanced measures, but to omit safeguards proposed as part of the package, and to take no action in regard to recommendations to rescind measures, to adjust them to reduce their scope, or to enhance controls over agencies' powers. (Two exceptions among the hundreds of measures enacted are "the 'dead-time' provisions in Pt IC of the Crimes Act 1914 (Cth) and sedition offences in pt 5.1 of the Criminal Code" - Hardy & Williams 2014).
Despite Australia facing vastly lower threat levels than other countries, the volume, the pace and the feigned necessity and urgency of measures have been much greater than those in other countries - much greater than in the USA and Canada, and greater even than those in the UK. Many of the measures have been copied from the UK. However, whereas UK legislation in some cases contains safeguards, and in all cases is subject to constitutional safeguards, the powers that the Australian Parliament has granted are subject to exceedingly weak controls, and to no entrenched human rights protections whatsoever. Furthermore, "while these laws were often cast as a transient response to an exceptional set of events, it is now clear that the greater body of this law will remain on the Australian statute book for the foreseeable future" (Williams 2011, p.1171).
This section presents information arising from the review of national security measures and of such PIAs as appear to have been performed in relation to them. Tables 3-5 list measures introduced during the period 2001-15 that were of such a nature that a PIA was clearly needed. Table 3 presents 36 measures brought forward by the lead agency on most national security matters, the AGD. Table 4 contains 19 measures brought forward by other agencies. Table 5 identifies 17 further measures which, while introduced for broader purposes, have relevance to counter-terrorism. Further detail on all of these measures is provided in Appendix 5.
[INSERT NatSec-PIAs-Table-AGD.xls]
[INSERT NatSec-PIAs-Table-Other.xls]
[INSERT NatSec-PIAs-Table-Related.xls]
The 17 ancillary projects in Table 5 evidence very poor compliance by a wide range of agencies with public expectations, government policy, and effective governance principles. Only 1/17 satisfied the 5-factor test described in section 3.1 above. The other 16 failed on almost all counts.
National security projects in agencies other than AGD, listed in Table 4, also score very badly, with none of them satisfying more than 3 of the 5 factors. A PIA Report was published for just 1/19 projects - and that process avoided any engagement with advocacy organisations. In the mere 4/19 in which advocacy organisations were engaged, none of the PIA Reports were published and only 1 of them seems to have eventually become accessible.
The most important exhibit, Table 3, shows that the behaviour of the AGD, throughout the 15 years, has been simply scandalous, and the failure of the Parliament to represent a control over national security extremism has been nothing less than abject. At best, only 2/36 projects satisfy the 5-factor test. Engagement with advocacy organisations occurred in only 3/36 cases, and to the extent that it can be judged, their views were largely ignored. In 10/36 cases (but possibly 4 more), a PIA process was held in secret. Of these, only 1 Report was published, although 7 further documents have later come to light, in many cases because of FoI requests and the inapplicability of any of the nine exemption and eight conditional exemption categories in the Act.
Case studies of 4 of the 72 measures are presented below. Their purpose is to provide deeper insight than is possible with counts and percentages. In each case, some public light was thrown on the matter; but the proponents succeeded in convincing the Parliament that justification, care, prudence and balance should be abandoned, and that special-case pleading should win the day.
The Document Verification System (DVS) is a hub-system that enables enquiring organisations to provide data about a government-issued document related to personal identity. The organisations then receive confirmation or denial by the relevant agency as to whether the details provided match those on file. The scheme falls within the AGD's responsibility. The DVS has become so pivotal, initially in government and recently in the private sector, that a search on the OAIC website finds 45 documents mentioning it. It has been subject to continual function-creep, and to continual attempts to outsource the hub-system to the private sector. Both the scheme and the processes whereby its privacy impact have been assessed have been of the utmost concern to the lead advocacy organisation, with a search on the APF's website finding 26 documents mentioning it.
The first public knowledge of the scheme arose from an aside by the Attorney-General during an interview with a reporter from The Australian in January 2005. From the context, it was clear that the project had been under way for some time, and a pilot commenced later that year. Only 4 days after the emergence of the scheme, the APF wrote to the Attorney-General, expressing its concern at the absence of transparency and consultative processes, and laying out its initial questions. That resulted in a dismissive response. An indication of the scheme's deep privacy-intrusiveness was that the NSW Privacy Commissioner had to exempt that State's Roads & Traffic Authority (RTA) from the NSW data protection legislation in order to enable the agency to participate. (The exemption appears to have been later extended indefinitely, rendering the Act nugatory).
An additional $28 million in funding was provided in the 2006 Budget. In late 2006, advocacy organisations continued to be excluded from the pilot, and no PIA appears to have been performed during the foundation stages, 2004-06. A PIA was subsequently performed, resulting in a PIA Report dated June 2007. However, the process did not include engagement with advocacy organisations, and no evidence exists that the document was published, in any meaningful sense of that term. Indeed, the existence of the document was unknown to advocacy organisations for almost 3 years, when it came to light during work on another matter, in April 2010.
By at least the 3rd quarter of 2011, AGD had a project under way to greatly extend access to the DVS. The changes eventually included access for the first time by the private sector - some 17,000 corporations - and permission for corporations to act as agents for government agencies. Further, the Medicare registry was added to the scheme. Early in the 4th quarter of 2011, it appears that AGD commissioned a consultancy to perform a PIA. Consultations were conducted with both industry and State governments, but not with advocacy organisations. The consultancy completed the PIA Report by July 2012. The Report recommended engagement with civil society, but AGD continued to avoid doing so.
AGD successfully hid the project's existence from advocacy organisations for over a year, until October 2012. Moreover, its exposure was indirect and accidental. Several advocates had participated in a separate consultation process relating to a National Trusted Identity Framework (NTIF), which was conducted by the Department of Prime Minister & Cabinet (PM&C), commencing in December 2011. During a meeting in mid-October 2012, it was apparent that industry representatives in the meeting were aware of the existence of a project being run by AGD to extend the DVS. They clearly saw it as being no longer necessary to keep the new arrangements secret, because they considered it 'a done deal', and in any case the PIA Report was now in the hands of the media, following an FoI request. This meeting was the first occasion on which any advocacy organisation appears to have heard of the project. At the end of October, following repeated requests, PM&C's consultant gained permission from AGD to provide APF with the PIA Report completed on 20 July 2012.
Correspondence with the AGD in November-December 2012 gave strong indications that the project was proceeding, and that involvement of advocacy organisations was not desired. However, a revised AGD invitation indicated a "genuine offer to consult with [APF]", and APF made a Submission in February 2013. This identified a wide range of substantive issues with the seriously inadequate PIA Report, and with the design. These criticisms would have been available to AGD at least a year earlier had it engaged with advocacy organisations. The identified deficiencies included multiple materially misleading statements in the background information about the proposals; a substantial lack of transparency - whose effect was likely to mask the real nature of the scheme, and which was in arguable breach of government information policy; the inclusion of State and Territory registry data, which in at least two cases needed to be the subject of a PIA but had not been; failure to manage the risk of function creep and to ensure that PIAs are conducted for each such extension; and an absence of key protections for individuals' interests, and in particular a pretence that the data trail at the DVS hub is anonymous.
A further PIA process was then conducted by a different consultancy. It provided a (very sketchy) background document, dated 22 January 2014, and invited a submission, to be "followed by discussions ... in the week of 10 February". The APF provided initial comments on 7 February 2014, with its previous submission as a constituent part. The meeting was never called, and in early March 2014, the APF discovered that the AGD had already let the contract for construction of the system in mid-February, without any consideration of, or response to, the APF's two substantial submissions. The APF's letter to the Attorney-General of 7 March 2014 was similarly ignored. It appears that the consultancy presented a PIA Report on 15 May 2014, but this was not brought to the attention of APF, and no copy of it has come to light. A further PIA Report dated 31 March 2015, prepared by the same consultancy as for the 2014 report, was discovered during the preparation of this case study, together with the AGD's disagreement with some of the Report's Recommendations. The 2015 PIA Report falsely states that advocacy groups "were consulted" in relation to the 2015 process - whereas no engagement took place, and the content of the Report completely ignores the submissions made to AGD and to the consultants during 2013-14. (It is noteworthy that Schedule 2 'Documents considered in the course of the PIA' includes no documents from advocacy groups).
The depth of the dishonesty with which the AGD has behaved throughout the period 2004-15 is so great that the conventional presumption of incompetence rather than venality cannot be sustained. The AGD actively denied the legitimacy of the notion of consultation. They actively sought to conduct the process without the public knowing that it was under way. When the project became known, they actively suppressed documents, and they actively misled advocacy organisations about the nature of the process. They subsequently offered "a briefing", and did so in a context in which no notice whatsoever would or indeed could be taken of the submissions made by the advocacy organisation, because the design was already a fait accompli. This is not in any sense engagement, but just 'public education' by an authority, of the kind that is derided in Australia when it is done by government agencies in other countries.
In short, throughout the life of the DVS, the AGD has consistently had complete disregard for transparency and engagement, involving serious breaches of government policy in relation to openness generally and PIAs in particular, and resulting in demonstrable deficiencies in the scheme and in privacy protections for the country's entire population.
Crimtrac is an Australian government agency that develops and operates shared data management services for law enforcement agencies of the Commonwealth and the 6 States and 2 Territories. During 2007, Crimtrac conducted a 'Scoping Study' of Automated Number Plate Recognition (ANPR). According to the Privacy Commissioner's 2007-08 Annual Report, the Commissioner recommended to Crimtrac that it conduct a PIA on the project. During 2007, Crimtrac contracted the author's company to conduct a preliminary Privacy Issues Analysis of the technology's use. In 2008, Crimtrac commissioned another consultancy to conduct a PIA.
APF was invited to meet with Crimtrac, and a Background Paper was provided. Two APF Board members attended the meeting in mid-June, with travel funded by Crimtrac. Crimtrac had APF's Policy Statement on ANPR of March 2008 available to them. The discussions included a commitment by Crimtrac to provide a copy of the PIA Report to APF. To this point, the relationship was cordial, and the process was appropriate.
However, a planned second meeting was re-scheduled twice from early to mid-July, and the APF Board members were unable to travel on the final date that was set. Despite completion of the PIA Report in mid-July 2008, by September it was still unavailable to APF. Following the release of a Report on ANPR by a Queensland Parliamentary Committee, APF issued a Media Release, which made clear that Crimtrac's proposal relating to ANPR was not merely for traffic management, but quite clearly for mass surveillance of vehicle movements. Crimtrac made no further contact with APF, and enquiries about the PIA Report elicited no response.
In November 2009, at a periodic event run by the APF, the Big Brother Award for 'Most Invasive Technology' was given to ANPR and "the Australian Police Forces in combination with CrimTrac". Some time later, APF was informally advised that Crimtrac staff were bemused by the Award, because, after the Scoping Study was completed, the government had not provided the funds requested, and hence the project had stalled. APF and the general public were unaware of this at the time, and no public announcement has been found of the cancellation of the project.
In August 2013, the APF became aware that, in mid-2011, an FoI request from a reporter - Sean Parnell, of The Australian - had been successful in prising a copy of the 568-page Scoping Study Report from Crimtrac's unwilling grasp. The files (sections 1, 2, 3 and 4) are mere scans, denying copiable access to the text. The document included on pp. 183-198 a summary of, and responses to, the PIA Report, with the PIA Report itself on pp. 309-352. It may have been posted on the Crimtrac website at some stage in 2011, but was not evident in 2013. These copies came to light, 5 years late, purely because of the persistence of a reporter and a subsequent mention in a newspaper article.
The PIA process for Crimtrac's 2007-08 project was seriously deficient. In addition, it appears that, throughout the period 2009 to 2013, it ignored its declared commitment to conduct PIAs, and that it withdrew that commitment in 2014. (In its 2006-07 Annual Report, Crimtrac stated that it had "committed the agency to undertake a Privacy Impact Assessment on each of our new developments and initiatives" (p.3). Statements such as "Crimtrac conducts Privacy Impact Assessments (PIAs) on all new projects " appear in its Annual Report in each of the following 6 years, to 2012-13. However, APF has not been aware of any PIAs being undertaken by Crimtrac since 2008, no PIA Reports appear on Crimtrac's website (although a document title in a 2012 list includes the term 'PIA'), and no mentions of Crimtrac PIAs appear on the Privacy Commissioner's website or Annual Reports. In Crimtrac's 2013-14 Annual Report, no mention is made of the longstanding "commitment" to PIAs. Presumably the agency considers it is no longer necessary to make a hollow statement that it had safely ignored for 6 years.
The notion of a national database of vehicle sightings clearly remains on the agenda of law enforcement agencies. In 2011, the Australian Federal Police (AFP) succeeded in inveigling a naive ACT Assembly into authorising mass surveillance ANPR in that Territory. A pool of data is being accumulated by several police forces that will be available to be funnelled into any such national database, as and when the national security extremist community utilises an opportunity to enlist a Minister's support for the measure. Despite the strong public policy imperative for PIAs to be performed, Crimtrac clearly has no intention of conducting one on such a scheme, least of all one worthy of the name.
In April 2013, it became apparent that the Australian Securities and Investment Commission (ASIC) had used a little-known provision of the Telecommunications Act to block web-sites. The matter attracted attention because, although the agency's purpose was to block a scammer's web-page, it had demonstrated remarkable technical incompetence by blocking at IP-address level rather than web-page (or perhaps domain-name) level, and had thereby unintentionally blocked 1200 websites of which 1199 were not targets (EFF 2013).
The provision that the agency used is Telecommunications Act s.313. Its multiple sub-sections enable government agencies to 'request' assistance from a telco or an ISP, but impose a positive obligation on the company to assist the agency (Libertus 2013). The powers can be used by almost any agency, for almost any purpose, require no warrant, and are not subject to any other meaningful control. It transpires that many agencies have been utilising the impenetrable text of the section as legal justification for a range of purposes.
Many business and civil society organisations expressed serious concerns about these revelations, and there was considerable media coverage. Beyond the question of uncontrolled censorship powers, many agencies were found to be treating s.313 as carte blanche to demand actions by telcos and ISPs, including the provision of personal data, for a great many purposes. Given the sensitivity of personal communications and of personal electronic experiences, and because s.313 lacks any vestige of controls or mitigation measures, this represents an important privacy issue.
In July 2014, it was announced that the House of Representatives Infrastructure and Communications Committee would conduct an Inquiry into s.313. No substantive documents were made available as a basis for discussion. No formal demands for information were made by the Committee to the proponents of the s.313 powers, and in particular the Committee did not require the AGD, the Department of Communications, or any other agency, to conduct a PIA. The few submissions from agencies arrived late, and were not available to advocacy organisations when they prepared their submissions. This is fairly indicative of the very low standards of Parliamentary Committee proceedings, which have been subverted, or have willingly transformed themselves, into auto-approval processes for submissions made by government agencies. (The most recent honourable exception of which the author is aware was the Report of the Senate Committee Inquiry into the Access Card, nearly a decade ago, in March 2007).
Multiple advocacy organisations made submissions, including the APF, initially in August 2014, and again as verbal evidence at the long-delayed hearing in 4 March 2015, supported by Clarke (2015a). Civil society emphatically recommended rescission of s.313, failing which a whole raft of provisions were essential in order to achieve a suitable mechanism.
When the Parliamentary Committee filed its Report in June 2015, it completely ignored all submissions from advocacy organisations, without bothering to counter the arguments put to it. The Committee recommended that the unjustified and uncontrolled mechanisms remain in place, subject to 'whole-of-government guidelines'. This is a completely ineffective mechanism, and was clearly intended as nothing more than a smokescreen for the Committee's abject failure to protect the public's interests. The Committee's response to ASIC's incompetence was to make the vacuous recommendation that agencies should "have the requisite level of technical expertise". The complete indifference of the Committee to the views of the public was underlined by the utterly misleading report title: 'Balancing Freedom and Protection'.
Around the world, national security agencies have prompted governments to establish so-called 'data retention schemes', forcing telcos and ISPs to store vast volumes of data about all traffic passing through them. Many of these schemes have subsequently been struck down or withdrawn. In Australia, there have been repeated attempts by national security extremists to achieve a scheme, culminating in 'success' in March 2015. An outline of the history in Australia and overseas is in Clarke (2015b). This identifies attempts by AGD as early as 2003 and again in 2008. Much the same proposal was run through three successive Labor Attorneys-General 2008-2013, but was not met with much enthusiasm.
In July 2012, the AGD launched a major assault, publishing a Discussion Paper in which it sought a wide array of additional powers, including data retention. The proposition was extraordinarily sketchy. From September 2012, the Parliamentary Joint Committee on Intelligence and Security (PJCIS) undertook an Inquiry into 'potential reforms of National Security Legislation' (which was a misleading representation of the AGD's ambit claims). In its Report in June 2013, the Committee noted the massed chorus of criticism from advocacy organisations, but ignored it, and supported data retention, subject to a few thoroughly inadequate controls and mitigation measures.
In late 2013, the staunchly conservative Abbott Government won office. In August 2014, AGD provided to an unknown list of corporations a 'Confidential industry consultation paper' on data retention. A copy was leaked within 24 hours. Unusually, it appears that no attempt has been made by the Government to pursue the miscreant. The new Coalition Government duly tabled the Bill that AGD wanted Parliament to pass, and between November 2014 and February 2015, it was considered by the PJCIS.
Among the 200 submissions were about 30 from advocacy organisations, including one of 35 pp. from APF. Those submissions provided a great deal of evidence, and all savaged the proposal. Meanwhile, ample evidence was provided by both industry and advocacy organisations that the proposition was extremely vague, and would be extremely difficult and extremely expensive to interpret and implement. The Attorney-General and the Prime Minister both gave media interviews during this period which drew widespread derision because of their very apparent inability to understand what 'meta-data' was, and what the proposed scheme entailed (Keane 2014).
However, the hearings of the PJCIS on 30 January 2015 were indicative of the extent to which that Committee, and with it the Parliament, has been as comprehensively captured as the Government has, by the very organisations over which it nominally exercises oversight. A phalanx of senior executives from AGD, the Australian Security Intelligence Organisation (ASIO) and the Australian Federal Police (AFP) gave evidence to the Committee. The chair (a Government member) fawningly thanked the head of ASIO for inviting the Committee to visit ASIO's (vast, new) building by the Lake; and the lead Opposition member expressed honest admiration for the skilful evasiveness of the answers given by the AGD executive.
The appearance of the APF's representatives, including one who had travelled from interstate, was deferred for four hours - something that the author had never previously experienced in over 50 appearances before Parliamentary Committees. The few parliamentarians remaining in the room showed no interest in the APF's evidence, and asked no questions. APF provided a Supplementary Submission on 31 Jan 2015, helpfully answering the questions that it had reasonably anticipated that the Committee would ask. The PJCIS's Report of February 2015 dismissed the flood of evidence against the scheme, and recommended passage of the Bill with amendments that made some marginal improvements. The proposal remained unjustified, grossly invasive and technically incompetent.
The data retention proposal was also considered by the Senate Legal and Constitutional Affairs References Committee (SLACAR) within the context of a comprehensive review of the TIAA. Copious submissions were made by advocacy organisation to this Committee as well, including three by APF, on 14 October 2014, and 1 February and 2 February 2015. SLACAR's Report in March 2015 (pp.42-95) was indicative of the political realities in contemporary Australia. The Government members of the Committee backed the national security extremist / AGD / PJCIS view of the world, and ignored the massive weight of contrary evidence presented by advocacy organisations. The Opposition members continued Labor's position of bipartisanship on any matter labelled as 'national security', which conveniently excuses them from applying any rational thought to the matter. Only the Greens Senator, Scott Ludlum, Chair of the Inquiry, actually considered the evidence. He concluded that he was "opposed to the introduction of a mandatory data retention regime and draws attention to the failed pursuit of such regimes internationally. ... The regime being proposed equates to mass surveillance. It should not proceed" (p.72).
Subsequently, it has been gradually penetrating the consciousness of the Parliament that, among the many ways in which the data retention scheme as enacted on 26 March 2015 is seriously defective is in its destruction of shield laws for journalists' sources, legal privilege and a variety of other longstanding protections (Taylor 2015).
It appears that, at no stage between 2003 and 2015 has any form of impact analysis been performed by AGD, and that none of the five Attorneys-General have instructed that one be done, and that the PJCIS did not do so either, despite opportunities in both 2014 and 2015. It is noteworthy that the first of those five Attorneys-General launched the Privacy Commissioner's PIA Guide in August 2006, stating that: "By conducting a Privacy Impact Assessment, government agencies will be able to take into account the community's expectations about privacy protection, and reflect those in a project. This is something we should strive for". But neither he nor his successors have taken his advice, to the serious detriment of human rights.
A deeper comparison of the process relating to the data retention proposals against the APF's Meta-Principles is in Clarke (2015b).
Given the very substantial privacy-invasiveness inherent in national security measures, and taking into account the public policy and legal framework that surrounds PIAs, it would have been reasonable to expect that government agencies would have scored very high on the five-factor test. An examination of the tables presented in section 3.3 above discloses that 57 of the 72 projects (79%) failed on every test, and that the total score for projects did not even remotely approach pass-level, viz. an overall 11%, comprising AGD 9%, agencies other than AGD 16%, and related projects 8%. For the last decade, agencies generally, and AGD most especially, have been in reckless breach of public expectations, public policy and in many cases the law; but they have escaped publicity, and escaped sanctions.
A great many initiatives have been undertaken in the national security space, and a number in adjacent areas. Yet only a very small proportion of national security measures have been subjected to meaningful evaluation processes. In particular, transparency and engagement with civil society has been highly deficient, and even where advocacy organisations have made submissions, their arguments have been almost entirely ignored in the final analysis rather than being reflected in withdrawal or defeat of, or adaptations to, the proposals.
The arrogance of the lead agency on national security matters, the Attorney-General's Department, is plain to see. In many cases, PIAs have been avoided. In almost all cases in which they've been conducted, advocacy organisations have been excluded, and the PIA Report suppressed unless and until forced out by FoI applications. The behaviour of the AGD has been so seriously unreasonable and so seriously in breach of government policy, that seven advocacy organisations wrote to the Attorney-General in September 2011, complaining that his Department "appears to have no process in place to ensure consultation with civil society organisations about many of the initiatives that arise in your portfolio", with specific proposals for change. The Attorney-General, like almost all appointees to that position since 2001, was under the thrall of and/or cowed by the Department, and failed to even reply.
It is especially concerning to see the complete failure of the Parliamentary Commitee system to demand that agencies generally, and the Attorney-General's Department in particular, observe proper process and bring forward PIAs with their proposals, including clear justification, and clear responses to the questions and criticisms put by civil society. The Parliamentary Joint Committee on Intelligence and Security (PJCIS) is a body of hand-selected MPs and Senators all of whom are closely aligned with the intelligence community. Very little critical thought can be expected from such a captive group, and very little is forthcoming. It should be demanded of other Committees, however, that they give much more careful consideration to proposals that seriously constrain civil rights. At the other end of the spectrum, the Parliamentary Joint Committee on Human Rights is young, and has very little influence; but it too has failed to speak with the authority and depth that should be expected of it. The two Senate Standing Committees on Legal and Constitutional Affairs (SLAC) have been particularly cowardly, because they have some degree of influence, but have chosen not to use it. As is evident from the Data Retention Case Study, this cowardice arises from the dominance of party politics over public policy.
There are few mechanisms whereby the 'eternal vigilance' necessary to protect freedoms can give rise to effective controls over the power of national security extremism that has become embedded in the Australian government bureaucracy since 2001.
The early 21st century has seen the collapse of the business models used by newspapers. Among the impacts of this has been very substantial reductions in the extent to which the media acts as a check on excesses in government and a bulwark against totalitarianism. The Murdoch media is dominant. Most of its outlets are oriented towards entertainment rather than news, and its only broadsheet is opinion-driven and unbalanced. The ABC is under permanent assault from conservative politicians and the corporations, institutions and opinion(ated) commentators that support them. The fourth estate is becoming limited to a few venues such as The Guardian, Crikey and The Conversation, all of which are easily marginalised, and all of which have fragile business models.
Lynch et al. (2014, p. 198) noted that "Poor process leads to inferior laws". The Meta-Principles presented in s.2.4 above summarise the characteristics of good process. The conduct of PIAs, in accordance with existing public policy imperatives, has the benefits of forcing a degree of transparency, enabling informed decision-making and the filtering out of unjustified measures, and leading to the imposition of appropriate controls and mitigation measures on those proposals that are found to be justified.
The Parliament has recently empowered the privacy oversight agency to direct an agency to conduct a PIA. However, the consistent lack of interest shown by the Privacy Commissioner in exercising available powers, and the emasculation of the Office by the Government and the AGD, render the power all-but irrelevant. Parliament, through its Committees, could directly enforce appropriate evaluation of proposals before they are placed on the table. Despite APF submissions that Committees should do so, the author is not aware of any instance in which any Committee has made such a demand. On the contrary, advocacy organisations' submissions are routinely ignored by Parliamentary Committees. National security proposals are routinely passed through the Parliament with unseemly haste, and generally with a supine Opposition voting with the Government rather than joining with the cross-benches to force proper process, and amendments to or defeat of the proposals.
Australian democracy is now extremely fragile. It will be in dire straits as soon as a genuine national emergency arises, or national security extremists contrive the appearance of one, by leveraging off minor incidents, overseas incidents, or imaginary circumstances, in order to manipulate public opinion. To date, compromises of human rights in Australia have primarily afflicted only Aboriginals and a small minority of Muslims and converts to Islam. The scope exists for much broader abuse of human rights. The Parliament shows no sign of protecting privacy, and with it democracy. So the holding back of the tide is likely to be dependent on the activities of fringe groups and the unofficial media, and over-reach by law enforcement agencies.
Extract from AHRC (2015), emphases added
As listed in Williams (2011), p. 1144
1. Criminal Code Amendment (Anti-Hoax and Other Measures) Act 2002
(Cth);
2. Security Legislation Amendment (Terrorism) Act 2002 (Cth);
3.
Suppression of the Financing of Terrorism Act 2002 (Cth);
4. Criminal Code
Amendment (Suppression of Terrorist Bombings) Act 2002 (Cth);
5. Border
Security Legislation Amendment Act 2002 (Cth);
6. Telecommunications
Interception Legislation Amendment Act 2002 (Cth);
7. Proceeds of Crime Act
2002 (Cth);
8. Proceeds of Crime (Consequential Amendments and Transitional
Provisions) Act 2002 (Cth);
9. Crimes Amendment Act 2002 (Cth);
10.
Criminal Code Amendment (Terrorist Organisations) Act 2002 (Cth);
11.
Criminal Code Amendment (Offences against Australians) Act 2002 (Cth);
12.
Charter of the United Nations Amendment Act 2002 (Cth);
13. Australian
Protective Service Amendment Act 2002 (Cth);
14. Australian Crime Commission
Establishment Act 2002 (Cth);
15. Australian Protective Service Amendment Act 2003 (Cth);
16. Criminal
Code Amendment (Terrorism) Act 2003 (Cth);
17. Criminal Code Amendment
(Hizballah) Act 2003 (Cth);
18. Terrorism Insurance Act 2003 (Cth);
19.
Criminal Code Amendment (Hamas and Lashkar-e-Tayyiba) Act 2003 (Cth);
20.
Maritime Transport Security Act 2003 (Cth);
21. Australian Security
Intelligence Organisation Legislation Amendment (Terrorism) Act 2003
(Cth);
22. ASIO Legislation Amendment Act 2003 (Cth);
23. Australian Federal Police and Other Legislation Amendment Act 2004
(Cth);
24. Australian Security Intelligence Organisation Amendment Act 2004
(Cth);
25. Aviation Transport Security Act 2004 (Cth);
26. Aviation
Transport Security (Consequential Amendments and Transitional Provisions) Act
2004 (Cth);
27. Criminal Code Amendment (Terrorist Organisations) Act 2004
(Cth);
28. Telecommunications (Interception) Amendment Act 2004
(Cth);
29. Surveillance Devices Act 2004 (Cth);
30. Anti-Terrorism Act
2004 (Cth);
31. Anti-Terrorism Act (No 2) 2004 (Cth);
32. Anti-Terrorism
Act (No 3) 2004 (Cth);
33. National Security Information (Criminal
Proceedings) Act 2004 (Cth);
34. National Security Information (Criminal
Proceedings) (Consequential Amendments) Act 2004 (Cth);
35. National Security Information (Criminal Proceedings) Amendment
(Application) Act 2005 (Cth);
36. National Security Information Legislation
Amendment Act 2005 (Cth);
37. Maritime Transport Security Amendment Act 2005
(Cth);
38. Law and Justice Legislation Amendment (Video Link Evidence and
Other Measures) Act 2005 (Cth);
39. Anti-Terrorism Act 2005 (Cth);
40.
Anti-Terrorism Act (No 2) 2005 (Cth);
41. ASIO Legislation Amendment Act 2006 (Cth);
42. Anti-Money Laundering and
Counter-Terrorism Financing Act 2006 (Cth);
43. Anti-Money Laundering and
Counter-Terrorism Financing (Transitional Provisions and Consequential
Amendments) Act 2006 (Cth);
44. Telecommunications (Interception) Amendment
Act 2006 (Cth);
45. Law and Justice Legislation Amendment (Marking of Plastic Explosives) Act
2007 (Cth);
46. Aviation Transport Security Amendment (Additional Screening
Measures) Act 2007 (Cth);
47. Anti-Money Laundering and Counter-Terrorism
Financing Amendment Act 2007 (Cth);
48. Classification (Publications, Films
and Computer Games) Amendment (Terrorist Material) Act 2007 (Cth);
49. Customs Amendment (Enhanced Border Controls and Other Measures) Act 2009 (Cth);
50. Crimes Legislation Amendment (Serious and Organised Crime) Act 2010
(Cth);
51. Independent National Security Legislation Monitor Act 2010
(Cth);
52. National Security Legislation Amendment Act 2010 (Cth);
53.
Telecommunications Interception and Intelligence Services Legislation Amendment
Act 2011 (Cth); and
54. Defence Legislation Amendment (Security of Defence
Premises) Act 2011 (Cth).
From Williams (2013), p.7, fn.9
55. Combating the Financing of People Smuggling and Other Measures Act 2011
(Cth)
56. Aviation Transport Security Amendment (Air Cargo) Act 2011 (Cth)
57. Nuclear Terrorism Legislation Amendment Act 2012 (Cth)
58. Social
Security Amendment (Supporting Australian Victims of Terrorism Overseas) Act
2012 (Cth)
59. Aviation Transport Security Amendment (Screening) Act 2012
(Cth)
60. Customs Amendment (Military End-Use) Act 2012 (Cth)
61. Aviation Transport Security Amendment (Inbound Cargo Security Enhancement) Act 2013 (Cth)
From searches of Australian Parliamentary and AustLII Databases
62. Counter-Terrorism Legislation Amendment (Foreign Fighters) Act
2014
63. National Security Legislation Amendment Act (No. 1) 2014
64. Telecommunications (Interception and Access) Amendment (Data Retention) Act
2015
65. Customs and Other Legislation Amendment (Australian Border Force)
Act 2015
As listed in Williams (2011)
Extracted from AHRC (2008), Williams (2011), HRLC (2011, 2012) LCA (2012), Lynch et al. (2014)
Legislation swept away many well-established common law protections that had grown up to deal with the excesses of the old statute, and gave DFAT and its allies elsewhere in the national security apparatus an array of new powers, not least in relation to biometrics, which are free of Parliamentary oversight.
The Passports Office did not conduct a PIA, and refused to conduct any meaningful discussions with APF.
The APF's communications with them are indexed here: http://www.privacy.org.au/Papers/indexPolicies.html#Pass
There is no evidence that a PIA was performed.
The APF's submissions are at https://www.privacy.org.au/Papers/AGTI0406.doc and https://www.privacy.org.au/Papers/SubmnSenateTISC0406.html
There is no evidence that a PIA was performed. Current information about the scheme is at http://www.bdm.nsw.gov.au/Pages/apply-for-certificates/certvalid.aspx
OIAC Annual Reports refer to PIAs conducted by both Immigration and DFAT.
No evidence exists of any engagement with advocacy organisations, nor of
publication.
There is no evidence that a PIA was performed
The APF's submission is at https://www.privacy.org.au/Papers/SubmTelecomIntercept050520.pdf
The Draft Bill was suppressed by the Clth Govt, but released by the ACT Chief Minister. It contained a raft of proposed measures, most highly prejudicial to the privacy interests of the population as a whole. OAIC's Submission urged the conduct of a PIA. No evidence has been found of a PIA ever being performed
The APF's submissions are at https://www.privacy.org.au/Papers/BriefAntiTerrBill2005.rtf, https://www.privacy.org.au/Papers/AGSecLawsRevSupp0602.rtf, https://www.privacy.org.au/Papers/SenLCCTerror-sub165.pdf
A series of PIAs was conducted 2005-07, by the author's company, including active engagement with advocacy organisations.
There is no evidence that a PIA was conducted.
The APF's submission is at https://www.privacy.org.au/Papers/SenTIAmendmentBill2006.rtf
This partial review of national security legislation appears not to have included any PIA, nor consideration of whether individual items of legislation had been the subject of PIAs.
The APF's submissions are at https://www.privacy.org.au/Papers/AGSecLawsRev0601.rtf and https://www.privacy.org.au/Papers/ACTTerrorBill-0602.rtf
Background information is at http://www.austrac.gov.au/businesses/legislation/amlctf-act. The documents at the time referred to a PIA performed within AGD, and to an 'extensive consultation process'. But the groups consulted with were overwhelmingly, if not exclusively, finance industry and law enforcement. Consumer interest groups were largely excluded. The PIA Report appears to have been suppressed for a time, but at some stage was published: http://www.ag.gov.au/www/agd/rwpattach.nsf/VAP/(CFD7369FCAE9B8F32F341DBE097801FF)~88Privacy+impact+assessment+aml-06.pdf/$file/88Privacy+impact+assessment+aml-06.pdf
The APF's submission are at https://www.privacy.org.au/Papers/Sen-AML-CTF-0603-v2.rtf, https://www.privacy.org.au/Papers/AGs-AUSTRAC-AML-CTF-0604.rtf, https://www.privacy.org.au/Papers/AGs-AUSTRACreAML-CTFBill.pdf, https://www.privacy.org.au/Papers/AML-CTFBill2006.rtf, https://www.privacy.org.au/Papers/AML-CTFBill2006-Supp.rtf and https://www.privacy.org.au/Papers/AML-CTFBill2006-Supp2.rtf
No evidence has been seen to suggest that the 2nd Tranche was subject to a PIA.
The APF's submission are at https://www.privacy.org.au/Papers/AMLCTF-Tranche2-AGs-0708.pdf, https://www.privacy.org.au/Papers/Ludwig-AMLCTF-070913.pdf and https://www.privacy.org.au/Papers/AML-CTF-Tanner-071213.pdf
A PIA was conducted behind closed doors, but the Report was suppressed. Had it been appropriately performed, and public, and heeded, it would have saved both taxpayers and the private sector hundreds of millions of dollars expended before it was abandoned 18 months later.
The APF's primary submission, to the Senate Committee, is at https://www.privacy.org.au/Campaigns/ID_cards/HSAC.html
A PIA may have been conducted in relation to a common login-point for multiple client-facing agencies. If so, it was conducted in secret, and the PIA Report suppressed.
A PIA was performed by Salinger, with APF input: https://www.privacy.org.au/Papers/Sen-AusCheckBilll-070228.pdf
The PIA Report may have been published at the time, but the APF appears not to have been aware of it until some time later: http://www.ag.gov.au/www/agd/rwpattach.nsf/VAP/(756EDFD270AD704EF00C15CF396D6111)~Privacy+Impact+Assessment+-+Auscheck.pdf/$file/Privacy+Impact+Assessment+-+Auscheck.pdf
This involved substantial changes to the Act. No evidence has been found of any PIA being performed.
APF's submissions are at https://www.privacy.org.au/Papers/AGs-DraftTIAABill-070228.pdf, https://www.privacy.org.au/Papers/TIAAAmdtBill-Senate-0707.pdf, https://www.privacy.org.au/Papers/Senate-TIA0804.pdf, https://www.privacy.org.au/Papers/Senate-TIA0804-Supp.pdf, https://www.privacy.org.au/Papers/TIA-SenSub-0904.pdf and https://www.privacy.org.au/Papers/TIA-SenSubSupp-0904.pdf
AGD performed a PIA, with a Report completed in June 2007: http://www.oaic.gov.au/privacy/applying-privacy-law/list-of-privacy-assessments/documentation-verification-service-department-of-human-services-assessment-report
No evidence has been found of any consultation, or even stakeholder analysis, let alone engagement with advocates, who were unaware the process had occurred until late 2012.
The document was released quietly only 5 years later, in late 2012, apparently forced out by an FoI request during a subsequent round of the DVS extensions, which proceeded behind the smokescreen of the NTIF: http://www.ag.gov.au/RightsAndProtections/IdentitySecurity/Documents/FINAL%20PIA%20for%20publication%20on%20webpage%20June%202007%20%5BDOC%204835KB%5D.doc
Crimtrac commissioned a PIA, APF was provided with a Background Paper, and APF participated in one meeting.
The PIA Report was suppressed. Some years later, it was forced into the open by a reporter's FoI request, and later still it came to the APF's notice. The PIA Report was published in facsimile form only.
AGD conducted this review. The OAIC drew attention to the need for PIAs: http://www.oaic.gov.au/images/documents/migrated/migrated/sub0808.pdf. There is no evidence of any PIAs being performed.
A PIA was performed, but in secret, and excluding consultation with advocates. The PIA Report was tabled in the House of Representatives in March 2009, but was not notified to civil society and the APF did not become aware of it until June: http://www.ag.gov.au/www/agd/agd.nsf/Page/OrganisationalStructure_NationalSecurityandCriminalJustice_AusCheck_PrivacyImpactAssessmentandCommentary
In the meantime, the scheme had been subject to a great deal of function creep
The APF's submission is at https://www.privacy.org.au/Papers/AusCheckBill-090604.pdf
No evidence has been seen to suggest that a PIA was performed.
The APF's submissions are at https://www.privacy.org.au/Papers/TIAA-AG-09814.pdf and https://www.privacy.org.au/Papers/CAC-100506.rtf
A PIA was performed, but the process was deficient.
APF's submission is at https://www.privacy.org.au/Papers/AML-CTF-eVerifn-0908.pdf
No evidence has been seen of the PIA Report being published.
APF was heavy involvement in several intensive consultation sessions during 2011 - which were subsequently aborted in bad faith by the Department.
Four years later, as part of the current research, a reference to a 2010 document was unearthed by a Google search on the Department of Immigration site, at http://www.border.gov.au/ReportsandPublications/Documents/acbpsfilelisting01-01-13to30-06-13.pdf#search=%22privacy%20impact%22:
'2010/031074-03 Personal Search - Internal Concealment Improvement Strategy 2010 - Body Scanner - Privacy Impact Assessment, Travel Facilitation & Compliance - Enforcement - Search (Internal Body)'
The document appears to be a PIA Report, which was at no stage brought to the attention of advocacy organisations.
A PIA appears to have been performed on one aspect of a Bill that contained multiple privacy-intrusive measures.
No evidence has been seen that the PIA Report was published.
APF's submissions are at https://www.privacy.org.au/Papers/AMLCTF-CFPSBill-1012.pdf and https://www.privacy.org.au/Papers/SenLAC-Austrac-110309.pdf
A project was apparent from a newspaper article: http://www.canberratimes.com.au/news/local/news/general/speed-camera-also-spy-lens/2228819.aspx?storypage=0
The APF's submissions are at http://www.privacy.org.au/Papers/ACT-Pt-to-Pt-101021.pdf and http://www.privacy.org.au/Papers/ACT-PttoPt-Reply-101111.pdf
No evidence has been found of any PIA having been conducted. At that stage, the proposal appears to have not been for any mass surveillance application of ANPR.
There is mention of this project in a Crimtrac Annual Report.
Despite an annually-reiterated agency commitment to undertake PIAs, no evidence has been found that a PIA was undertaken.
This involved an extremely serious set of extensions, but no evidence has been found that a PIA was performed.
The APF's submission is at https://www.privacy.org.au/Papers/Sen-TIISL-101028.pdf
Mention of this project was made in a newspaper article: http://www.themercury.com.au/article/2011/02/17/207911_road-toll.html
No evidence has been seen of any PIA being performed.
Invasive provisions were included in the Customs Amendment (Serious Drugs Detection) Bill 2011.
No evidence has been found of any PIA being performed.
The statements in the Media Release included that "body scanning technology will not be used on all travellers or used randomly". That particular politician's promise appears to have had an extremely short period of validity: http://www.ministerhomeaffairs.gov.au/www/ministers/oconnor.nsf/Page/MediaReleases_2011_FirstQuarter_23February2011-Usingtechnologytostopdrugcouriersatourairports
This was a quite gross initiative, going far beyond what was required to comply with the relevant treaty, and misrepresented to the public.
There is no evidence that a PIA was performed.
The APF's submissions are at https://www.privacy.org.au/Papers/SenLAC-Austrac-110309.pdf, https://www.privacy.org.au/Papers/JSC-Cybercrime-Transcript-110801.pdf, https://www.privacy.org.au/Papers/JSC-Cybercr-Supp-110805.pdf and https://www.privacy.org.au/Papers/Cybercrime-PS-110904.html
This was a widely-publicised measure, combining agencies that hold a vast treasure-trove of data about the entire population, e.g. http://www.theaustralian.com.au/australian-it/privacy-fear-over-agencies-mega-merger-medicare-centrelink-data-plan/story-e6frgakx-1226025592629
No evidence has been seen that a PIA was performed on any aspect of the matter.
AGD was urged by OAIC to conduct a PIA on this Draft Bill: http://www.oaic.gov.au/news-and-events/submissions/privacy-submissions/proposed-extradition-and-mutual-assistance-reforms. No evidence has been found of any PIA being performed.
There is mention that a PIA was performed on this matter, in https://www.comlaw.gov.au/Details/C2011B00002/5c3cda59-7319-473b-ab11-6de888cd74f5
This emerged only as a result of the research undertaken for this paper.
A PIA Report was commissioned on this matter by AGD: http://www.ag.gov.au/RightsAndProtections/FOI/Documents/Privacy%20Impact%20Assessment%20Preliminary%20Report%20Telecommunications%20(Interception%20and%20Access)%20ACT%201979%20Reform.pdf
The process completely excluded advocacy organisations.
According to OAIC documents of 2013 and 2014, ATO conducted a PIA in June 2011: http://www.oaic.gov.au/privacy/applying-privacy-law/list-of-privacy-assessments/dvs-ato-audit-report and http://www.oaic.gov.au/privacy/applying-privacy-law/list-of-privacy-assessments/documentation-verification-service-department-of-human-services-assessment-report
No other evidence in relation to this PIA has been found
APF and other NGOs argued that the latest round of body scanners were ineffective, back when the Labor government bowed down before a US Under-Secretary and committed to installing them.
APF's many submissions are indexed at http://www.privacy.org.au/Papers/indexPolicies.html#BS. See, in particular, http://www.privacy.org.au/Papers/BodyScans-1002.html and http://www.privacy.org.au/Papers/BS-PIA-Response-1109030.pdf
A process was pursued for some time by the Department, but then aborted, using the excuse that the Privacy Commissioner accepted that the data was not personal data. This enabled the submissions made by advocates to be ignored.
The existence of an unpublished PIA is attested to in this OAIC document:
http://www.oaic.gov.au/news-and-events/submissions/privacy-submissions/consultation-draft-implementation-of-body-scanners-privacy-impact-assessment
Roundtable discussions were held, which may or may not have proceeded far enough to justify a PIA. No evidence has been found of a PIA being undertaken.
Crimtrac was reported in the media, on the basis of an AGD Media Release, as being funded to deliver a national database.
No evidence has been found that a PIA was ever performed.
It appears that a PIA may have been conducted in effective secrecy, without consultation with advocates, and and with the report suppressed.
The PIA Report came to light under media pressure in October 2012.
There are rumours that an earlier PIA may also have been conducted: http://www.itnews.com.au/News/318539,attorney-general-told-to-keep-data-retention-to-six-months.aspx and http://www.ag.gov.au/Freedomofinformation/Documents/Privacy%20Impact%20Assessment%20Preliminary%20Report%20Telecommunications%20(Interception%20and%20Access)%20ACT%201979%20Reform.pdf
An Inquiry was performed into 'potential reforms of National Security Legislation' - actually a log of claims by the AGD for yet more powers: http://www.aph.gov.au/Parliamentary_Business/Committees/House_of_Representatives_Committees?url=pjcis/nsl2012/index.htm, including a Discussion Paper (60 pp.): http://www.aph.gov.au/Parliamentary_Business/Committees/House_of_Representatives_Committees?url=pjcis/nsl2012/additional/discussion%20paper.pdf
No evidence has been found that a PIA was performed on any element (with the possible, but dubious, exception of the data retention proposal).
A PIA was undertaken by AGD. No consultation appears to have taken place with advocacy organisations, and it is unclear when and under what circumstances the PIA Report was published. The Project and the PIA were not known to APF until they were discovered during searches undertaken for this project in July 2015: http://www.ag.gov.au/Publications/Documents/ExchangeofcriminalhistoryinformationwithNZforvettingpurposes/PIAonthesixmonthtrialwithNZfortheexchangeofcriminalhistoryinformationforvettingpurposes.pdf
There is a reference to a PIA, apparently dated 23 Oct 2012, at: http://www.ag.gov.au/CrimeAndCorruption/AusCheck/Pages/AccesstoAuscheckdatabase.aspx
The APF was unaware of it until the document emerged during the research undertaken for this article in July 2015.
Industry consultations were held. But community associations were expressly excluded from that process, the PIA Report was suppressed for a further 3 months while a nominally separate (NTIF) process was in train, and the advocacy community only became aware of the DVS initiative and the existence of a PIA Report at the end of October - apparently after its publication was forced by a media FoI request: http://www.itnews.com.au/News/322040,the-australian-governments-identity-catch-all.aspx, http://www.ag.gov.au/Freedomofinformation/Pages/Freedomofinformationdisclosurelog.aspx, http://www.ag.gov.au/Documents/FINAL%20PIA%20for%20publication%20on%20webpage%20-%20June%202007.pdf, http://www.ag.gov.au/RightsAndProtections/FOI/Documents/Privacy%20Impact%20Assessment%20-%20DVS%20Private%20Sector%20Access%20-%2020%20July%202012.pdf, http://www.ag.gov.au/RightsAndProtections/IdentitySecurity/Documents/Privacy%20Impact%20Assessment%20DVS%20Private%20Sector%20Access%2020%20July%202012%20%5BPDF%20860KB%5D.pdf and http://www.ag.gov.au/RightsAndProtections/IdentitySecurity/Documents/Privacy%20Impact%20Assessment%20National%20Document%20Verification%20Service%20%5BPDF%20230KB%5D.pdf
APF wrote to AustPost when this was announced in April 2012: http://www.privacy.org.au/Papers/AP-DigMbox-120422.pdf
AustPost's partial reply, 6 weeks later, is here: http://www.privacy.org.au/Papers/AP-DigMBox-Reply-120608.pdf
" ... we have not undertaken any public consultation processes in relation to the privacy aspects of the initiative. However, over the course of the development of the APDM, we have engaged two companies - Lockstep and most recently Information Integrity Solutions Pty Ltd - to undertake the necessary Privacy Impact Assessments".
The PIA Report was not published.
See also http://www.itnews.com.au/News/318779,auspost-to-launch-digital-mailbox-this-month.aspx and http://www.governmentnews.com.au/2013/05/28/article/Digital-Mailbox-or-Digital-Australia-Card-Australia-Posts-big-gamble/PVXIATWGAN.html
There is mention in Legislative Instrument Explanatory Statement that a PIA was performed on this project: https://www.comlaw.gov.au/Details/F2012L02374/e239b359-9fb6-4000-9b1d-1976111a50af
This only came to light as a result of the research undertaken in July 2015 in support of this paper.
No evidence has been found that a PIA was ever conducted
(The project was subsequently folded, and DHS's parallel internal project extended).
This was an ambit claim by AGD to the Parliament for a wide range of yet more intrusive extensions to existing legislation: https://www.privacy.org.au/Papers/JPCIS-NatSec-120820.pdf
In the context of the COAG review and in a Submission to the PJCIS, the OAIC urged that PIAs be undertaken: http://www.oaic.gov.au/news-and-events/submissions/privacy-submissions/review-of-counter-terrorism-legislation and http://www.oaic.gov.au/news-and-events/submissions/privacy-submissions/inquiry-into-potential-reforms-of-national-security-legislation
There is no evidence that any of the many elements were subject to PIAs.
Media articles abounded, e.g. http://www.itnews.com.au/News/318539,attorney-general-told-to-keep-data-retention-to-six-months.aspx
A PIA was apparently conducted in secret, and the Report suppressed.
A PIA Report was released in August 2012 as a result of a media FoI request. An unreadable copy is at: http://www.ag.gov.au/Freedomofinformation/Documents/Privacy%20Impact%20Assessment%20Preliminary%20Report%20Telecommunications%20(Interception%20and%20Access)%20ACT%201979%20Reform.pdf
A NSW Registry of Births, Deaths and Marriages, tightly linked to national security systems: http://www.itnews.com.au/News/365534,nsw-govt-to-finally-finish-lifelink.aspx
No evidence has been seen of any PIA ever being performed
OAIC recommended that a PIA be performed: http://www.oaic.gov.au/news-and-events/submissions/privacy-submissions/new-streamlined-identity-checking-requirements-for-prepaid-mobile-carriage-services-consultation-on-the-draft-2013-determination
No evidence has been seen of a PIA being performed.
This was reported in the media: http://www.itnews.com.au/News/359874,australia-post-spends-71m-on-new-tracking-service.aspx
No evidence has been seen of a PIA being performed
Australian Customs Service (ACS), since renamed ACBPS, operates a system to handle details concerning inbound airline passengers.
An OAIC report mentions the existence of a PIA: http://www.oaic.gov.au/privacy/applying-privacy-law/list-of-privacy-assessments/passenger-name-records-implementation-of-recommendations-audit-report
No evidence has been seen of any engagement with advocacy organisations, or of publication of the PIA Report.
No evidence has been seen of any PIA being conducted
PIAs are mentioned in the strategy documented, but they are not mandated.
No evidence has been seen of any being performed, by any agency.
Complaints were made by Privacy International to the HRC and IGIS, who amply demonstrated the absence of controls over intelligence agencies by excusing themselves from taking any action: https://www.privacy.org.au/Papers/PI-Ct-IGIS-131202.pdf, https://www.privacy.org.au/Papers/PI-Ct-AHRC-131202.pdf, https://www.privacy.org.au/Papers/NatSec-131204.pdf, https://www.privacy.org.au/Papers/PS-SS.html and https://www.privacy.org.au/Papers/UNHRC-Surv-150323.pdf
Mention is made in the OAIC's 2012-13 Annual Report that DHS had prepared a draft PIA Report. No evidence has been found of any engagement with advocacy organisations, nor or publication of the PIA Report. APF had no knowledge of this at the time.
The system's insecurity caused headlines in May 2014: http://www.theage.com.au/it-pro/government-it/opposition-urges-government-to-take-security-of-citizens-data-seriously-20140429-zr12y.html
A (seriously inadequate) PIA Report was subsequently found during research for this paper, in July 2015: http://www.humanservices.gov.au/spw/corporate/publications-and-resources/resources/mygov-inbox-privacy-impact-assessment.pdf
Austrac commissioned a PIA. It appears not to have included consultation with civil society. It published a PIA Report that indicated that the process was deficient.
APF's submission is at https://www.privacy.org.au/Papers/Austrac-CDDRules-140128.pdf
This was a broad-ranging review, which failed to achieve the depth required of a PIA.
APF's submission is at https://www.privacy.org.au/Papers/AGD-AML-CTF-140330.pdf
This was a broad-ranging review which failed to achieve the depth required of a PIA.
APF's submissions are at https://www.privacy.org.au/Papers/Sen-TIAA-140317.pdf, https://www.privacy.org.au/Papers/SLCA-TIAA-141014.pdf, https://www.privacy.org.au/Papers/SLAC-TIA-150201.pdf and https://www.privacy.org.au/Papers/SLCA-TIAA-Notes-150202.pdf
Yet more changes were proposed, with yet more serious impacts.
There was yet more strong evidence of AGD subversion of democratic process
APF's submission is at https://www.privacy.org.au/Papers/SLAC-TIAA-140729.pdf, including:
"When I was preparing for this hearing yesterday I stumbled across a privacy impact assessment report on the telecommunications interception act regime ... The report was presented to the government in December 2011. I understand it was made public on the Attorney-General's website in August 2012. ... I think it is extraordinary that the Attorney-General's Department has apparently not drawn the committee's attention to that piece of work, which would I think have been extremely valuable to you" (Hansard, SLACC, 29 Jul 2014, p.30)
This matter related to a section that was exposed as having been contrived to be sufficiently obscure that its meaning was not publicly apparent, and that was being seriously abused by agencies
No evidence has been found of any PIA being conducted.
APF's submissions are at https://www.privacy.org.au/Papers/SCIC-TA313-140824.pdf, https://www.privacy.org.au/Papers/SLCA-TIAA-Notes-150202.pdf, http://www.rogerclarke.com/DV/TA313.html and https://www.privacy.org.au/Papers/SCIC-TA313-150304.pdf
This contained significant and highly intrusive measures.
No evidence has been found of any PIA being conducted.
APF's submisson is at https://www.privacy.org.au/Papers/JPCIS-ASIO-140818.pdf
Mention exists of a PIA in a departmental document.
Mention is made in an OAIC document that a PIA was conducted, including a
recommendation that the PIA be published:
http://www.oaic.gov.au/images/documents/news-and-events/submissions/privacy-submissions/submission-by-the-australian-privacy-commissioner-on-the-migration-amendment-strengthening-biometrics-integrity-bill-2015.pdf
No evidence has been found of engagement with advocacy organisations, nor of the PIA being published.
No evidence has been found of any PIA being conducted.
The APF's submission is at https://www.privacy.org.au/Papers/PJCIS-CTLA-141002.pdf
No evidence has been found of any PIA being conducted.
The APF's submission is at https://www.privacy.org.au/Papers/PJCIS-CTLA-141110.pdf
This was a longrunning initiative, rebuffed by the Parliament several times, but eventually the national security apparatus headquartered in the AGD succeeded in bludgeoning a Bill through the Parliament in 2014-15.
The OAIC urged that PIAs be undertaken: http://www.oaic.gov.au/news-and-events/submissions/privacy-submissions/submission-on-the-inquiry-into-the-telecommunications-interception-and-access-amendment-data-retention-bill-2014
There is no evidence of any PIAs being undertaken.
APF's submissions are at https://www.privacy.org.au/Papers/PJCIS-DataRetention-150119.pdf, https://www.privacy.org.au/Papers/PJCIS-DataRet-Supp-150131.pdf and https://www.privacy.org.au/Papers/SLCA-TIAA-Notes-150202.pdf
This was the subject of media articles: https://www.ato.gov.au/About-ATO/About-us/Contact-us/Phone-us/Voiceprint/
No evidence has been found of any PIA being conducted.
A highly unsatisfactory process was conducted. A misleading statement was included in the PIA Report - whose existence only came to light while undertaking research in support of this paper: http://www.ag.gov.au/RightsAndProtections/IdentitySecurity/Documents/PIAReportAExpandedPrivateSector.pdf
See also AGD's response to that PIA: http://www.ag.gov.au/RightsAndProtections/IdentitySecurity/Documents/AGDresponsetoPIA.doc
An RFQ was issued for a PIA on this Project, by AGD's Cyber & Identity Security Policy Branch, in mid-2015, with a report to AGD due by the end of July. It is not apparent that any engagement was undertaken by the AGD or by the successful consultant.
No PIA Report was evident as at 30 Jul 2015.
The Department of Immigration was reported in the media to have conducted a PIA: http://www.itnews.com.au/News/404972,committee-rubberstamps-plans-to-collect-more-biometric-data-on-aussies.aspx
If so, it would appear that no engagement occurred with advocacy organisations.
A Roundtable discussion was held. However, it was apparent that background work was well-advanced, such that a PIA should have already been conducted. No evidence has been found of any such process, nor of any engagement with advocacy organisations.
AGD (2007) 'Report to the Council of Australian Governments on the elements of the National Identity Security Strategy' Attorney-General's Department, April 2007, at http://www.ag.gov.au/RightsAndProtections/IdentitySecurity/Documents/Report%20to%20the%20Council%20of%20Australian%20Governments%20on%20the%20elements%20of%20the%20National%20Identity%20Security%20Strategy%20%5B346%20KB%20PDF%5D.pdf
AGD (2013) 'Council of Australian Governments Review of Counter-Terrorism Legislation' Attorney-General's Department, 2013, at http://www.ag.gov.au/Consultations/Documents/COAGCTReview/Final%20Report.PDF
AHRC (2008) 'A Human Rights Guide to Australia's Counter-Terrorism Laws' Australian Human Rights Commission, 2008, at https://www.humanrights.gov.au/human-rights-guide-australias-counter-terrorism-laws
AHRC (2015) 'Rights and freedoms: right by right' Australian Human Rights Commission, 2015, at http://www.humanrights.gov.au/rights-and-freedoms-right-right-0
APF (2013) 'Meta-Principles for Privacy Protection' Australian Privacy Foundation, March 2013, at https://www.privacy.org.au/Papers/PS-MetaP.html
APL (2010) 'Terrorism Laws - Chronology of legislative developments - 2001-10' Australian Parliamentary Library, 2010, at http://www.aph.gov.au/About_Parliament/Parliamentary_Departments/Parliamentary_Library/Browse_by_Topic/TerrorismLaw/legislativedev
Clarke J. (2008) 'The Report of the Clarke Inquiry into the case of Dr Mohamed Haneef' Commonwealth of Australia, at http://pandora.nla.gov.au/pan/84427/20090121-0022/www.haneefcaseinquiry.gov.au/www/inquiry/rwpattach.nsf/VAP/(3A6790B96C927794AF1031D9395C5C20)_Volume+1+FINAL.pdf/$file/Volume+1+FINAL.pdf
Clarke R. (2000) 'Beyond the OECD Guidelines: Privacy Protection for the 21st Century' Xamax Consultancy Pty Ltd, January 2000, at http://www.rogerclarke.com/DV/PP21C.html
Clarke R. (2006) 'What's 'Privacy?' Presentation to a Workshop at the Australian Law Reform Commission, Xamax Consultancy Pty Ltd, July 2006, at http://www.rogerclarke.com/DV/Privacy.html
Clarke R. (2008) 'Dissidentity: The Political Dimension of Identity and Privacy' Identity in the Information Society 1, 1 (December, 2008) 221-228, at DOI 10.1007/s12394-009-0013-7, PrePrint at http://www.rogerclarke.com/DV/Dissidentity.html
Clarke R. (2009) 'Privacy Impact Assessment: Its Origins and Development' Computer Law & Security Review 25, 2 (April 2009) 123-135, at http://www.rogerclarke.com/DV/PIAHist-08.html
Clarke R. (2011) 'An Evaluation of Privacy Impact Assessment Guidance Documents' International Data Privacy Law 1, 2 (March 2011), PrePrint at http://www.rogerclarke.com/DV/PIAG-Eval.html
Clarke R. (2013) 'Surveillance by the Australian Media, and Its Regulation' Surveillance & Society 12, 1(Mar 2014) 89-107, at http://library.queensu.ca/ojs/index.php/surveillance-and-society/article/view/aus_media, PrePrint at http://www.rogerclarke.com/DV/MSR.html
Clarke R. (2014a) 'Approaches to Impact Assessment' Notes for a Panel Presentation at CPDP'14, Brussels, 22 January 2014, Xamax Consultancy Pty Ltd, at http://www.rogerclarke.com/SOS/IA-1401.html
Clarke R. (2014b) 'The Regulation of Point of View Surveillance: A Review of Australian Law' IEEE Technology & Society 33, 2 (Jun 2014), PrePrint at http://www.rogerclarke.com/DV/POVSRA.html
Clarke R. (2014c) 'Privacy and Free Speech' Invited Presentation at the Australian Human Rights Commission Symposium on Free Speech, Xamax Consultancy Pty Ltd, August 2014, at http://www.rogerclarke.com/DV/PFS-1408.html
Clarke R. (2015a) 'Telecommunications Act s.313' Notes provided to the Standing Committee on Infrastructure and Communications' Xamax Consultancy Pty Ltd, March 2015, at http://www.rogerclarke.com/DV/TA313.html
Clarke R. (2015b) 'Data Retention as Mass Surveillance: The Need for an Evaluative Framework' International Data Privacy Law 5, 2 (May 2015) 121-132, at http://idpl.oxfordjournals.org/content/early/2015/01/23/idpl.ipu036.full.pdf, PrePrint at http://www.rogerclarke.com/DV/DRPS.html
DoF (2008) 'National Smartcard Framework', Department of Finance, December 2008, at http://www.finance.gov.au/files/2012/04/national-smartcard-framework.pdf
EFF (2013) 'Australian Networks Censor Community Education Website' Electronic Frontier Foundation, 11 April 2013, at https://www.eff.org/deeplinks/2013/04/australian-networks-censor-community-education-site
Hardy K. & Williams G. (2014) 'Terrorist, Traitor, or Whistleblower? Offences and Protections in Australia for Disclosing National Security Information' UNSW Law Journal Volume 37, 2 (2014) 784-819, at http://www.unswlawjournal.unsw.edu.au/sites/default/files/t5_hardy_and_williams.pdf
Harris L. & Westin A.F. (1995) 'The Equifax-Harris Mid-Decade Survey on Consumer Privacy' Louis Harris & Associates, 1995
HRLC (2011) 'Submission to the Independent National Security Legislation Monitor re Review of Australia's Counter-Terrorism and National Security Legislation' Human Rights Law Centre, 26 October 2011, at http://www.hrlc.org.au/files/HRLC-Submission-to-National-Security-Legislation-Monitor.pdf
HRLC (2012) 'Submission to COAG: Necessity and proportionality must guide assessment as to whether counter-terrorism powers remain appropriate' Human Rights Law Centre, 19 October 2012, at http://www.hrlc.org.au/wp-content/uploads/2012/10/HRLC-Submission-COAG-Review-of-Counter-Terrorism-Laws.pdf
ICCPR (1996) 'International Covenant on Civil and Political Rights' United Nations, 1966, at http://treaties.un.org/doc/Publication/UNTS/Volume%20999/volume-999-I-14668-English.pdf
ICO (2007) 'Privacy Impact Assessments: International Study of their Application and Effects' UK Information Commissioner's Office, 2007, mirrored at http://www.rogerclarke.com/DV/ICOStudy-2007.pdf
Keane B. (2014) 'Brandis' disastrous data definition reflects a confused government' Crikey, 7 August 2014, at http://www.crikey.com.au/2014/08/07/brandis-disastrous-data-definition-reflects-a-confused-government/
LCA (2012) 'Anti-Terrorism Reform Project: A consolidation of the Law Council of Australia's advocacy in relation to Australia's anti-terrorism measures' Law Council of Australia, June 2012 , at http://www.lawcouncil.asn.au/lawcouncil/images/LCA-PDF/a-z-docs/Anti-TerrorismReformProjectUpdate.pdf
Libertus (2013) 'What are ISPs' obligations under s313 Telecommunications Act 1997?' Libertus, version of 23 March 2013, at http://libertus.net/censor/isp-blocking/au-ispfiltering-voluntary.html#s313
Lynch A., McGarrity N. & Williams G. (2015) 'Inside Australia's Anti-Terrorism Laws and Trials' NewSouth Publishing, 2015
Morison W.L. (1973) 'Report on the Law of Privacy' Government Printer, Sydney, 1973
OAIC (2012) 'Review of counter-terrorism legislation: Submission to the Council of Australian Governments' Office of the Australian Information Commissioner, September 2012, at http://www.ag.gov.au/Consultations/Documents/COAGCTReview/OfficeoftheAustralianInformationCommissioner.PDF
OAPC (2014) 'Guide to undertaking Privacy Impact Assessments' Office of the Australian Privacy Commissioner, August 2006, mirrored at http://www.rogerclarke.com/DV/OAPC-2006.pdf, rev. May 2010, mirrored at http://www.rogerclarke.com/DV/OAPC-2010.pdf, rev. May 2014, at http://www.oaic.gov.au/privacy/privacy-resources/privacy-guides/guide-to-undertaking-privacy-impact-assessments, mirrored at http://www.rogerclarke.com/DV/OAPC-2014.pdf
OECD (1980) 'OECD Guidelines on the Protection of Privacy and Transborder Flows of Personal Data' Organisation for Economic Cooperation and Development, at http://www.oecd.org/sti/ieconomy/2013-oecd-privacy-guidelines.pdf
Taylor J. (2015) 'Trust us: Telcos told they can't verify journalist metadata warrants' ZDnet, 8 July 2015, at http://www.zdnet.com/article/trust-us-telcos-told-they-cant-verify-journalist-metadata-warrants/
UDHR (1948) 'Universal Declaration of Human Rights' United Nations, 10 December 1948, at http://www.un.org/en/documents/udhr/index.shtml
Williams G. (2011) 'A Decade Of Australian Anti-Terror Laws' Melb. U. L. Rev. 35, 3 (2011) 1136-1176, at http://www.law.unimelb.edu.au/files/dmfile/35_3_13.pdf and http://www5.austlii.edu.au/au/journals/MelbULawRw/2011/38.html
Williams G. (2013) 'The Legal Legacy of the 'War On Terror'' Macquarie Law Journal 12, 3 (2013) 11-24, at http://www.austlii.edu.au/au/journals/MqLawJl/2013/11.html
Wright D. & De Hert P. (eds) (2012) 'Privacy Impact Assessments' Springer, 2012
The author acknowledges the assistance of colleagues in the Australian Privacy Foundation in locating sources and checking the appropriateness of statements, and of Margot O'Neill for asking the hard question that motivated the study.
Declaration: Of the 3/72 PIAs that arguably satisfied the 5-factor test, one was performed by the author's consultancy company and the other two by the consultancy run by the author's predecessor as Chair of the APF.
Roger Clarke is Principal of Xamax Consultancy Pty Ltd, Canberra. He is also a Visiting Professor in Cyberspace Law & Policy at the University of N.S.W., and a Visiting Professor in the Research School of Computer Science at the Australian National University. He has been a Board member of the Australian Privacy Foundation since 1987, and was its Chair 2006-14.
| Personalia |
Photographs Presentations Videos |
Access Statistics |
 |
The content and infrastructure for these community service pages are provided by Roger Clarke through his consultancy company, Xamax. From the site's beginnings in August 1994 until February 2009, the infrastructure was provided by the Australian National University. During that time, the site accumulated close to 30 million hits. It passed 65 million in early 2021. Sponsored by the Gallery, Bunhybee Grasslands, the extended Clarke Family, Knights of the Spatchcock and their drummer |
Xamax Consultancy Pty Ltd ACN: 002 360 456 78 Sidaway St, Chapman ACT 2611 AUSTRALIA Tel: +61 2 6288 6916 |
Created: 31 July 2015 - Last Amended: 13 August 2015 by Roger Clarke - Site Last Verified: 15 February 2009
This document is at www.rogerclarke.com/DV/IANS.html
Mail to Webmaster - © Xamax Consultancy Pty Ltd, 1995-2022 - Privacy Policy