Roger Clarke's Web-Site
© Xamax Consultancy Pty Ltd, 1995-2024

Infrastructure
& Privacy
Matilda
Roger Clarke's Web-Site© Xamax Consultancy Pty Ltd, 1995-2024 |

|
|||||
| HOME | eBusiness |
Information Infrastructure |
Dataveillance & Privacy |
Identity Matters | Other Topics | |
| What's New |
Waltzing Matilda | Advanced Site-Search | ||||
Emergent Working Paper of 30 January 2019
Roger Clarke, <co-author>, and <co-author> **
© Xamax Consultancy Pty Ltd, 2018-19
Available under an AEShareNet ![]() licence or a Creative
Commons
licence or a Creative
Commons  licence.
licence.
This document is at http://www.rogerclarke.com/DV/RPP.html
Privacy has been an active topic within the IS discipline for three decades. Commonly, individuals' privacy concerns are perceived as an impediment to the processes of business and government, and means are sought whereby those barriers can be overcome. The question arises as to whether the interests of individuals are adequately addressed.
Theory relating to the perspectives adopted by IS researchers was applied to the topic-area of privacy. A substantial set of papers was selected and assessed. This used a multi-partite sampling technique in order to include both works in influential venues and articles that may provide alternative views or herald changes in direction.
[[SPECULATIVE:
Despite the importance of privacy to individuals, it was
found that a large proportion of papers adopt the perspective of the system
sponsor, and treat that organisation's interests as objectives and those of
individuals as constraints on the achievement of the organisation's objectives.
A small proportion of published IS research is dual-perspective in nature, and
even fewer multi-perspective studies, and their impact is limited.
The consequences of this dominance of the interests of organisations over the interests of individuals gives rise to concern about the extent to which the IS discipline is conducting consultancy assignments for corporations rather than functioning as an academic discipline. In addition, the lack of dual-perspective research casts doubt on the quality of IS research, even from the viewpoint of corporate clients. Opportunities are identified for greater diversity in researcher perspectives, for higher-quality research, and for multi-perspective research that can address the needs of policy-makers.]]
The first-named author has published many refereed articles on a wide variety of aspects of privacy. However, only a few have appeared in venues directly associated with his own profession and discipline of information systems (IS). Those few have quite specifically addressed the needs of business and government, in such areas as human identification and geo-location. Two further articles, on dataveillance and the need for US data protection laws, appeared in Communications of the ACM. Many other papers, however, have been published in law and policy venues, because - although their subject-matter was relevant to IS - they were concerned with the needs of individuals or were addressed to policy-makers. Such papers did not find a fit with the statements of intent of IS journals, and, when submitted to such venues, failed to stimulate much interest, and met at least incomprehension and even hostility.
With his consultancy commitments declining, the first-named author recently found himself in a position to consider the reasons for this substantial gap between his conception of the IS discipline and that evidenced by the accumulating literature. Is he really a mis-fit? Is his perception justified that has IS has narrowed its scope in ways that are not appropriate for an academic discipline? Is it reasonable for him to regard a great deal of business school IS as thinly-disguised consultancy services to business enterprises?
During the period since 2015, he, variously alone and working with colleagues, has conducted a series of investigations that lay a foundation for empirical work that may throw some light onto those questions. The articles arising from those investigations present a theoretical analysis of the notion of 'researcher perspective'. This posits that each research project prioritises the interests of one or more stakeholders in the circumstances that IS researchers subject to study. The theory identifies the key characteristics of the concept, distinguishing single-perspective from dual- and multi-perspective approaches, and postulating that the IS literature is dominated by single-perspective work that favours the interests of the system sponsor. Techniques have been developed that enable assessment of the researcher perspectives adopted in published works. Applying that theory and research protocol, a series of exploratory studies have been undertaken of works published in a range of IS venues. This has provided considerable evidence in support of the key postulates of the theory.
The present paper reports on the application of the theory of researcher perspective to the following general research question:
To what extent does IS research on privacy topics reflect the interests of system sponsors in comparison with those of the individuals whose privacy is impacted by the relevant information system?
The paper commences by outlining the theory of researcher perspective, and then examines the privacy concept as it relates to IS. Consideration is given to ways in which suitable samples of privacy-related IS research might be identified, in order to assess the researcher perspectives adopted in those works. The findings of the study are then presented and discussed.
This section provides an overview of theory relating to researcher perspective, as developed progressively in Clarke (2015, 2016b and 2017), Clarke & Davidson (2019) and Jia et al. (2019).
The adoption of interpretivism as a viable research approach within the discipline brought with it the recognition that phenomena can be viewed from multiple perspectives. Observation by a disengaged person may be casual or dispassionate. Some observers, however, are involved in the phenomena, stand to gain or lose from natural developments or interventions, and hence have interests that they wish to protect or advance. The term 'stakeholder' has been commonly defined in IS research along the lines of "any group or individual who can affect or is affected by the achievement of the organization's objectives" (Freeman 1984). The definition adopted for the present purpose differs a little from that formulation, in that it encompasses both legal and natural persons, but omits entities that are not affected by the path that events take:
A Stakeholder is an entity that perceives itself to be at least potentially affected by an activity.
Donaldson and Preston (1995) argue that there are descriptive, instrumental and normative aspects of stakeholder theory, and that "managers should acknowledge the validity of diverse stakeholder interests and should attempt to respond to them within a mutually supportive framework because that is a moral requirement for the legitimacy of the management function" (p.87). Introna & Pouloudi (1999) apply this idea specifically in the context of privacy, identifying: "who the stakeholders are and what their perspectives concerning privacy issues are (descriptive element), what interests underlie these perspectives (instrumental element) and what values affect their attitudes (normative element)" (p.28, emphases in original). The following definition is adopted:
A Stakeholder Perspective is the viewpoint adopted by a stakeholder in a particular activity, reflecting that stakeholder's perception of phenomena within the relevant context, the stakeholder's value-set, and the interests that the stakeholder seeks to protect and advance
The central proposition of researcher perspective theory is that research is seldom conducted in a universalist manner, reflecting the interests of all stakeholders at once. It is very challenging for a researcher to convincingly adopt a pose of omni-cognisance, and hence it is much more common to adopt the perspectives of one or a few of the parties involved in or affected by the events. The key term is accordingly defined as:
A Researcher Perspective is a particular stakeholder perspective that is adopted by a researcher as the, or a, viewpoint from which to observe phenomena during the conduct of a research project
The simplest approach is to adopt a single perspective. This may be done consciously, or by default, for example when working within a genre or tradition, or replicating the application of a particular research technique in a particular context. In principle, single-perspective research may reflect the interests of any of the stakeholders. In practice, however, it appears that one particular category of stakeholder is very prominent in IS research. This is an organisation, or perhaps a partnership among organisations, or a particular organisational role. In order to encompass a range of contexts, the term is defined as follows:
The System Sponsor is the entity that develops, implements or adapts a system, process or intervention, or causes it to be developed or implemented, or for whose benefit the initiative is undertaken
Many IS studies have adopted as the unit of study a dyad, such as manufacturer-and-retailer, or supervisor-and-supervisee. However, many such projects are single-perspective in nature, in that their focus is on the interests of just one of the entities. Most commonly, the favoured entity is the more powerful of the two, with the interests of the less powerful entity treated as constraints on the achievement of the other entity's objectives. Historically, for example, upstream car-manufacturers have tended to dominate car-retailers, whereas downstream supermarket-chains have tended to dominate small foodstuff-manufacturers and vegetable-growers.
A corollary of the interpretivist position is that a comprehensive understanding of phenomena requires triangulation, that is to say that the different points-of-view of key actors need to at least acknowledged, and preferably taken into account. Introna & Pouloudi (1999) argued that "the situation at hand can be considered from multiple perspectives, without privileging a priori any of the viewpoints" (p.32). We suggest, however, that, when studying dyads, both perspectives can be 'privileged', in the sense of being treated as embodying desirable outcomes. For dual-perspective research, the interests of both sides of the dyad need to be treated by the researcher as objectives. By adopting this approach, the tensions between the two sets of interests are defined as being within-scope of the research, rather than being confounding variables.
A further consideration is that stakeholders' perspectives may not lie on the same dimension. Where B2B participants are negotiating on the price of a tradable item and the allocation of the costs of delivery, the perspectives of both parties lie on the economic dimension. On the other hand, whereas an organisation's interests in relation to its staff may focus on the cost and productivity of labour, employees are concerned about not only economic factors (in particular, pay and allowances) but also social factors (such as impositions on their free time, work-induced stress, and intrusions into their physical space such as the enforced extraction of biometrics for identity authentication and body fluids for drug-testing). In short, the conflicts among stakeholders' interests may straddle the economic and social dimensions.
Shifting beyond dual- to multi-perspective research involves considerably greater challenges. This is because the interests of multiple entities are inevitably in more substantial conflict than arises with only two stakeholders. Moreover, the conflict is more likely to extend across both economic and social dimensions rather than being merely a zero-sum game centred on the price of goods or services. Despite the difficulties, this challenge needs to be taken up if the discipline is to deliver substantial value to the economy and society by contributing to the determination of public policy questions.
The privacy field, broadly speaking, involves conflict between the interests of two categories of stakeholder - organisations that handle personal data, on the one hand, and the individuals to whom the data relates, on the other. In the following three contexts, for example, the key stakeholders are:
In all of these mainstream cases, the entities involved are participants. A further class needs to be distinguished, however, where one of the entities is not a participant, but is nonetheless impinged upon by the circumstances. Examples arise in the contexts of criminal intelligence databases, of pooled records of payments by debtors and tenants, and of claims by insurees. The term 'usee' has been coined to refer to entities that lack the power to affect a process, but are nonetheless affected by it (Clarke 1992, Fischer-Hübner & Lindskog 2001, Baumer 2015). Hence a fourth example of stakeholder-pairing is:
A further aspect of the privacy field is that the interests of the organisation are almost entirely economic in nature, whereas individuals' privacy interests are almost entirely on the social dimension. Hence the resolution of conflicts involves trade-offs across quite distinct dimensions.
Given the significant interests that at least two entities have in situations that involve privacy research, it might reasonably be expected that IS research would in some cases adopt the perspective of user organisations, in some cases that of the affected individuals, and in yet others the perspectives of both. Meanwhile, a few ambitious projects would presumably be multi-perspective in nature, taking into account also the concerns of other categories of organisation involved in the business of gathering, storing, trafficking in and analysing personal data, but also advocacy organisations for the stakeholders, and policy and regulatory agencies.
The following section considers the concept and dimensions of privacy and its treatment within the IS discipline, at a sufficient depth to enable the design of an empirical study.
This section first considers the multi-faceted meanings of the word 'privacy', then outlines the frameworks within which legal protections have emerged. This is followed by an outline of the nature of prior research into privacy-related topics within the IS discipline.
Most discussions of privacy trace its emergence to a US judgement at the end of the nineteenth century, which stated that "the right to be let alone ... secures the exercise of extensive civil privileges" (Warren & Brandeis 1890). Accessible historical and philosophical discussions are in Packard (1964), Cowen (1969), Flaherty (1984), Schoeman (1984), Rubenfeld (1989), Whitman (2004), Lindsay (2005) and Cohen (2013).
Privacy is widely acknowledged as being a complex and contested notion that defies unequivocal definition. The word can be applied in many contexts, admits of many interpretations, and is bound up with value-sets, both personal and cultural. People regard privacy as being important, and for many different reasons. At lower Maslowian levels, there are needs relating to physical safety, psychological wellbeing and self-esteem. There are also important economic, social, cultural and political concerns. In some contexts, concepts such as human dignity, individual autonomy, self-determination and self-actualisation come into play. Crucially, individuals' privacy concerns have very little to do with the economic dimension.
Because of the importance of these values, privacy inherently involves value conflicts. Each individual's privacy interests are often in conflict with other interests of the same individual, and with interests of other individuals, groups, societies, organisations and economies. As a result, privacy protection is an exercise in balancing interests. The balance-points that exist in any particular context, at any particular point in time, inevitably reflect the far greater political and economic power of governments and corporations in comparison with individuals.
A further complication in discussions about privacy is that most endeavours to explain privacy refer to it as a 'right'; yet writers seldom make clear whether they mean a moral or a legal right, and seldom give sufficiently deep consideration to the implications and constraints that arise from their definitions.
Because the intention here is to achieve progress in a particular field, i.e. for instrumentalist rather philosophical purposes, this article follows Morison (1973) and adopts the following as the working definition of the word:
Privacy is the interest that individuals have in sustaining 'personal space', free from interference by other people and organisations
In order to impose some structure on the field, authors have distinguished a variety of 'dimensions' or 'types'. In particular, Finn et al. (2013) identified seven types and Koops et al. (2016) identified nine. See also Solove (2006). This article applies the five dimensions proposed in (Clarke 1997), and adopted in the first-named author's works and by a variety of other researchers as well. They are depicted in Figure 1. The first four of those dimensions are:
The aspects of these dimensions that involve or give rise to data are particularly central to the IS discipline, and hence it is appropriate to adopt a working definition that reflects theory and practice in the field, as follows:
Data Privacy is the interest that individuals have in sustaining 'personal space' by being aware of and controlling, or at least significantly influencing, the handling of data about themselves
There is a tendency for people to conflate 'data' and 'privacy'. In this article, the more useful convention is adopted whereby 'data' refers to inert symbols, signs or measures, whereas 'information' implies the use of data by humans, in a particular context, in order to extract or impose meaning.
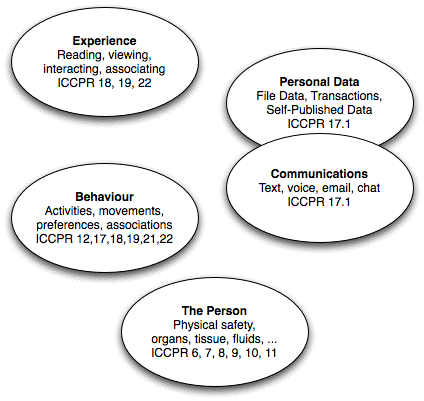
From
(Clarke
1997), incl. cross-references to the
International Covenant on Civil
and Political Rights
Whereas the first four dimensions are highly familiar, the most recently-emerged dimension is perhaps less so. Individuals have long consumed printed books, newspapers, plays, public addresses and private meetings without giving rise to recorded data that represents evidence of the ideas that they have been exposed to and that may have influenced them. Privacy of Personal Experience emerged as a serious concern only during the first decade of the 21st century (Cohen 1996, Greenleaf 2003, Clarke 2014). (The term 'experiential privacy' has subsequently been applied by marketers to indicate actual or imagined privacy-protective features as "a positive part of the [brand] experience [that] further delights the customer" - Bergman 2018. That is not the sense in which the term is used in this paper).
Reading and viewing activities have migrated to computer-based display-screens. They are performed under the control of corporations, and are recorded. Most conversations have become 'stored electronic communications', with each event recorded and both 'call records' and content retained. Events tickets are paid for using identified payment instruments. Many individuals' locations are tracked, in particular through cellular phone identifiers and mass-surveillance applications of automated number plate recognition, and geo-spatial correlations may be performed in order to find out who is co-located with whom and how often. This massive consolidation of individuals' personal experience is available for exploitation, and is exploited. This harbours threats to privacy that strike yet deeper than previous forms of intrusion: "The privacy of personal thought may not yet be directly under assault, but the privacy of personal experience is a dangerously close proxy for it" (Clarke 2016). This represents a particularly serious threat to the social, cultural and political aspects of privacy interests.
The working definition of privacy provided above is intentionally couched in terms of the interest that people have in private space. However, laws do create some privacy rights. Most countries have at least nominally acceded to the International Covenant on Civil and Political Rights (ICCPR 1996), although many have failed to comply with the resulting obligations, and some countries simply ignore them. Privacy is express in only one ICCPR Article, no.17; but as indicated in Figure 1, it is implicit in many parts of the document. Even where human rights are entrenched in a country's Constitution, however, it is commonly the case that a great many qualifications to the rights exist, reflecting both the conflicts among interests noted above, and the power exercised by various interests groups.
Data privacy and communications privacy are directly relevant to IS. However, behavioural privacy and experiential privacy are also greatly affected by data flows and associated IS. Considerable intensity of concern may arise in relation to organisational practices that curb individuals' activities, such as the denial of access to credit, health insurance and transport services. Individuals' concerns about such practices and systems can be expected to affect their adoption and acceptance behaviours, and their preparedness to continue to respect the requirements of such systems. Physical privacy is also relevant, for example where IS involve physical impositions on individuals, such as the gathering of biometric data for identity authentication, and virtual imprisonment by means of electronic monitoring anklets.
Privacy can be studied in multiple ways. In an article of this nature, it would normally be most appropriate to present an intellectual history of the concept. In practice, however, a major driving force in relation to privacy in the IS discipline has been legal developments. The approach adopted here is therefore to briefly outline the distinctly different forms that privacy regulation takes in the USA, on the one hand, and most of the rest of the world, driven by Europe, on the other.
The five dimensions of privacy are subject to scatters of laws rather than to coherent frameworks. In the case of data privacy, protections arise indirectly, not through measures to protect people's human rights, nor to protect their data privacy, but rather to protect data about them. The form of data that is subject to such protection is referred to by various terms, including personal data, personal information, and 'personally identiable information' (PII).
Data protection laws emerged in Europe from the beginning of the 1970s (Flaherty 1984, Bennett 1992, Bygrave 2014). Business concern about the risk of inconsistencies among national laws resulted in the formation of an OECD Expert Group, which published an influential set of Principles whose primary purpose was to facilitate international trade in personal data (OECD 1980). In the USA, the following four decades have seen continual efforts to ratchet back those modest protections, whereas Europe has seen increases in the effectiveness of existing protections and the introduction of additional measures.
The US approach is commonly referred to as Fair Information Practices (FIPs). This originated in the work of Columbia University economist, Alan Westin (Westin 1967, 1971; Westin & Baker 1974). For a review of the origins, see Bennett (1992, pp.95-152). Another influential work was the heavily economic interpretation of privacy advocated by Posner (1977). FIPs are encapsulated in the narrow sub-set of data privacy protections embodied in FTC (2000). A recent expression of FIPs is in the Privacy Shield arrangements to protect US corporations from EU law (DoC 2016). For a comprehensive history, see Gellman (2017).
The FIPs approach has been described as an 'official response' which legitimated dataveillance measures in return for some limited procedural protections (Rule 1974, Rule et al. 1980). It is highly permissive of corporate exploitation of personal data, and enforcement is very light-handed (Cate 2006). The failure of the US Congress to meet public expectations in relation to data protection has resulted in an extraordinary number and variety of statutes, drafted and passed as knee-jerk reactions to sudden flurries of concern (Smith 1974-). It is popularly considered that the category of personal data that enjoys the most stringent protections is video rental records - as a result of public disclosure of a conservative judge's (family's) taste in movies, during the period when Senate confirmation hearings into his appointments were in progress.
In about 2000, it appeared that Internet-era encroachments might lead to the USA enacting comprehensive protections (Clarke 1999). However, the explosion in government intrusiveness following the terrorist attacks of 2001 interrupted the process, and the power of Internet corporations has since been sufficient to hold meaningful regulation at bay.
One major thread of the ongoing efforts by US corporations to wind back privacy protections has been the endeavour to achieve reduction of privacy from a human right to an economic right. The Westin/Posner lines of thought were combined and further articulated by Laudon (1993), which proposed "market-based mechanisms based upon individual ownership of personal information and National Information Markets ... where individuals can receive fair compensation for information about themselves" (p. 2). Laudon's notion of 'fair compensation' overlooked the fundamental point that individuals' interests in privacy are primarily on the social dimension, and financial compensation is not commensurate with the harm wrought by privacy-invasions.
For the Internet era, Shapiro & Varian (1999) provided the intellectual underpinnings of consumer-manipulative economics, re-defining 'loyalty' as a one-way relationship from consumer to provider, achieved through lock-in techniques based on deep knowledge of customers. Despite the deep intrusions into personal interests inherent in the proposals, the book does not even include the word 'privacy' in its 1000-entry index. For reviews of the resulting state of affairs two decades later, see Zuboff (2015) on surveillance capitalism and Clarke (2019) on the digital surveillance economy.
Europe's path has been very different from that in the USA. The pioneering legislation of the early 1970s was progressively built upon, and protections have migrated progressively through the Council of Europe Convention 108 (CoE 1981), the EU Directive (EU 1995), and the CoE Addendum (CoE 2001), to the General Data Protection Regulation (GDPR 2016), which came into force in May 2018, and a 'modernised and improved' 'CoE 108+' (CoE 2018). Authoritative reviews such as Bennett (1992) and Bygrave (2014) indicate that data protection in European countries is comprehensive and robust, and offers consistent coverage across almost all of the continent. The GDPR applies consistently across the EU, is enforceable and appears very likely to be enforced, at least within Europe. Further, it appears that it may significantly affect practices of international Internet corporations, including the powerful ones that are based in the data haven of the USA (de Hert & Czerniawski 2016, EDPB 2018).
Despite US endeavours through various international fora, the rest of the world has been much more strongly influenced by the European than the US approach. In addition the extra-territorial reach of the GDPR, 'CoE 108+' is in the process of being adopted far beyond the boundaries of Europe (Greenleaf 2012, 2014, 2017).
An examination of privacy-related research in the IS discipline suggests that the approaches adopted reflect a number of inter-connected factors. One is the dominance of a particularly narrow interpretation of the function of a business school discipline, whereby the interests of corporations are treated as primary and the interests of other stakeholders in information systems are at best secondary. Associated with that idea is dominance of a conception of privacy that derives from the economics discipline. The third factor is the US-centricity of IS research, which extends across the affiliations of highly-cited authors, the subjects of empirical research, and the jurisdictional contexts within which research is conducted. This section draws on three systematic literature reviews, each of which was published in 2011, and each of which has a significant number of citations. It commences, however, by considering the 'economics of privacy' thread underlying IS research into privacy-related topics.
The Westin/Posner/Laudon/Varian line of economic analysis is evident in a number of IS research genres. An important example is commonly referred to as 'the privacy calculus'. Within the IS discipline, the term first appeared in Culnan & Armstrong (1999, p. 108), whose Figure 1 contained an entry: "Privacy Calculus: Customer Discloses if Benefits of Disclosure Exceed Risks". The supporting discussion is "Customers will continue to participate in this social contract [i.e. exchanging personal information for intangible benefits] as long as the perceived benefits exceed the risks" (p. 106).
This notion embodies a raft of assumptions commonly adopted in economic analyses: a rational consumer maximises rather than satisficing, has access to sufficient and accurate information, is capable of concentrating sufficiently hard and long to enable them to make a decision in their own best interests, has choices available that are not dictated by superior institutional or market power, and is unaffected by appeals of a hedonic nature. Dinev and Hart (2006), in applying the notion in the Internet Commerce context, expressly adopted the naive economic assumption-set: "Internet users' behavioral intentions should be consistent with expectancy theory, which holds that individuals will behave in ways that maximize positive outcomes and minimize negative outcomes" (p.62). This is consistent with the position that "Implicit in most of the neoclassical economics literature on privacy is the assumption that consumers are rationally informed agents with stable privacy preferences (see, for instance, Posner 1978; Stigler 1980)" (Acquisti et al. 2013, p. 253). On the other hand, such assumptions are very much at odds with IS practitioners' knowledge of human behaviour when using information systems.
In a recent analysis of 'the economics of privacy', Acquisti et al. (2016, p.464) reached the conclusion that " ... the economic consequences of less privacy and more information sharing for the parties involved (the data subject and the actual or potential data holder) can in some cases be welfare enhancing, while, in others, welfare diminishing". This author's inference is that there is little evidence that economic analysis of privacy has delivered much economic value, while at the same time either omitting the primary, social concerns of the individuals whose data is handled, or adopting clumsy proxies for social values. It is difficult to see how economic analysis based on such unworldly assumptions about human behaviour could ever provide a firm basis for understanding circumstances in which privacy plays a major role.
The first of the systematic literature reviews, Smith et al. (2011), presents the results of "an interdisciplinary review of privacy-related research", comprising "320 privacy articles and 128 books and book sections" (p.989). Because the authors were undertaking an expressly multidisciplinary review, only 82 of the works are in core IS publishing venues. The article is addressed to "IS scholars interested in empirical information privacy research" (p.990), and hence does not focus on the needs of stakeholders in the contexts that researchers subject to study.
The authors do not declare their intended scope. The pool of works is, however, limited to B2C marketing by corporations to consumers. No consideration is given to privacy issues arising from other economic roles that individuals play when dealing with organisations (such as employee, investor and usee), nor to the use of personal data by other individuals (as arises, for example, in C2C eCommerce), nor to individuals' social interests (which are the most important aspects of privacy), nor to service-provider abuses of data arising in the context of social media, nor even to the use of personal data by government agencies. Several mentions are made of the very different approach adopted in Europe (e.g. p. 1006); but the USA is not noted as being an outlier on the world stage. A large majority of the authors who are cited in the article are affiliated with North American, and overwhelmingly US, institutions. This even applies to the brief discussions about European approaches to privacy regulation.
The word 'consumer' occurs 33 times within the text of the article. Although there are also 70 occurrences of 'individual' and 6 of 'person', those of relevance to this analysis sustain the focus on people's economic role as consumers. There were very few indications that the needs of individuals outside the economic setting are of relevance to the IS discipline. The authors - either in their own right, or reflecting the content that they examined - appeared to strongly prefer the 'economic right' notion espoused by the Westin/Posner/Laudon/Varian school of thought over the recognition of privacy as a human right. The article adopts the common but misleading term 'commodity', to convey that business wants personal data to be a tradable item (p.984), and it prioritises business interests over individual interests. Given the overwhelming stress on corporate interests, it is unsurprising that regulation is deprecated: "Assigning fundamental rights to personal information would result largely in an opt-in market for information sharing, whereby firms would have access to the information only of those consumers who chose to make it available ... The commodity societies [i.e. the USA] largely see opt-in [i.e. consent-based handling of personal data] as an undue burden" (p.1001).
The article contains only one mention of the stakeholder notion, plus two of stakeholder theory, each made in passing. Where individuals' interests are mentioned, they are framed by business needs, not by individual needs. For example: "privacy awareness reflects the extent to which an individual is informed about organizational privacy practices" (p.998). If the individual's perspective were adopted, it would be reasonable to expect that further factors would be considered, such as the individual's educational background, the context in which the individual is situated, the extent to which the individual is inherently concerned about various dimensions and aspects of privacy, and the extent to which the individual is aware of risk factors arising from (ab)use of their personal data. The driver for privacy research appears to be the extraction of personal data for use by corporations: "compensating consumers through financial rewards can foster their information disclosure" (p.1001), "the value of personalization ... can override privacy concerns ... " (p.1001), and "users are more likely to provide personal information when they receive personalization benefits" (p.1002). Similarly, where a beneficiary of research is apparent, it is almost exclusively the system sponsor. For example, "privacy concerns had a significant impact on online purchase intent ... Firms that are positioned as 'safer' or 'trustworthy' on the privacy dimension will likely have a competitive advantage ... consumers who trust the firm are less concerned about their privacy and more willing to provide personal information ... building trust is more effective than trying to reduce consumer concern" (p.1000).
The authors note the 'privacy paradox', by which is meant the widespread inconsistency between individuals' stated intentions to disclose personal information and their actual personal information disclosure behaviours. One plausible explanation is offered for it - consumers' bounded rationality (p.1000). No consideration is given to the possibility that corporations might induce individuals into data disclosure through misinformation or obfuscation, or might exercise market power so as to effectively force individuals to disclose data, or might exploit the tendency of individuals to let the hedonic over-rule the rational.
The authors recognise corporate misbehavour, but not as a prevalent, systemic or inevitable pattern, and instead as "opportunistic behavior", providing as examples "insider disclosure or unauthorized access and theft ..., and selling personal data to, or sharing information with, third parties, financial institutions ..., or government agencies" (p.1001, emphasis added). There is no mention of corporations misinforming consumers, or obfuscating detail that would risk giving rise to misgivings on the part of individuals, or using market power to impose terms on individuals that involve the provision of personal data and the ceding of rights in relation to that data. Similarly, it is not corporate misbehaviour that is depicted as the culprit in undermining consumer trust, but instead "skepticism about the effectiveness of industry self-regulation in protecting consumer privacy ... has resulted in privacy advocates and consumers clamoring for strong and effective legislation to curtail rampant abuses of information by firms" (p.1001, emphasis added).
In categorising the relevant environmental variables that represent "context matter in the relationships between privacy and other constructs", the authors of the article (and/or the authors of the works that were evaluated) considered "the types of information collected", "the industry sector", "the political context" and "technological applications". Yet the authors omitted from their notion of 'context' any consideration of the perceptions, needs and interests of the particular individual. Young people have fewer, and different, things to hide compared with the mature and the middle-aged; rich people have different needs from the less well-off; families differ greatly in their privacy values depending on such factors as family structure, intra-family relationships, activities, cultural heritage, lingual background, and religious beliefs and affiliations; and there are well-documented gender differences in the nature of privacy concerns which are nowhere acknowledged. Yet, to Smith et al., none of this appears to be relevant to IS research.
[[THIS GENRE AND/OR MY UNDERSTANDING OF IT MAY BE TOO MUCH OF A PICKLE TO INCLUDE IN THE ARTICLE:
Another research genre of relevance is usefully described as addressing 'the consumer valuation of privacy'. This can be traced at least to Hann et al. (2003). Papers in the area also cite Cvrcek et al. (2006) and Acquisti & Gross (2006). The contexts vary, e.g. across various forms of eCommerce and social media). Longstanding consumer behaviour notions have been applied - 'willingness to accept' (WTA) money in order to grant access to personal data, and 'willingness to pay' (WTP) in order to protect it.
Some of the papers in the area read as though a competition is in train to find effective ways in which consumers can be enveigled into gifting their data for the least possible cost to corporations, with little sense of achieving an equitable balance between two competing sets of interests (QUOTE NEEDED). On the other hand, some contributions are dual-perspective in nature (e.g. Krasnova et al. 2009). In others, they may even be oriented towards the interests of individuals rather than marketers or social media service-providers. However, extraordinary care appears to be necessary in adopting such an approach: " ... revealed-preferences arguments should not, alone, justify the uncritical conclusion that privacy-conscious consumers will never pay for privacy. If individual privacy decisions are so malleable to endowment and order effects, such arguments lose their normative standing" (Acquisti et al. 2009, p.270). There is, as always in research in the economics field, a marked absence of recognition of social factors.
]]
One important research genre comprises studies of individuals' online behaviour in contexts in which privacy concerns arise. Li (2011) reports on a systematic literature survey of this genre. It assessed peer-reviewed academic research that reports empirical studies of individuals' online information privacy and its impact on their online behavior, constrained to the e-commerce domain, and to those studies that contain "a privacy or privacy concern related construct".
Li builds on two prior frameworks. The first is that of Smith et al. (1996), which explored the underlying structure of privacy concerns and developed a latent construct called Concerns for Information Privacy (CFIP), consisting of four dimensions: collection, errors, unauthorized secondary use, and improper access. The second framework is that proposed by Malhotra et al. (2004), which developed a scale of privacy concerns called Internet Users' Information Privacy Concerns (IUIPC). It is a higher-order construct with three dimensions: control, awareness, and collection. Based on the meta-study he performed, Li proposes "an integrative framework for the study on online information privacy [including] the distinction between two types of information privacy concerns: General Concerns for Information Privacy (or General CFIP) and Specific Concerns for Information Privacy (or Specific CFIP)" (p. 465).
The motivation for work in this genre is that " ... individuals' concerns for online information privacy play critical roles in determining their intention to use the Internet to provide personal information for services and transactions" (p. 453). The satisfaction of users' needs is not in focus, and the implications for practice drawn from Li's study are almost entirely addressed to businesses.
A remarkable aspect of the literature as evidenced by these studies is the very limited recognition and study of information asymmetry between marketing corporations and consumer, of power assymetry between them, and of the ease with which corporations can and do depend firstly on pseudo-consents to acquire and deal in personal data, secondly on at best marginally-legal spyware to acquire and deal in even more personal data, and thirdly on breaches of the undertakings embodied in the terms of services that they advertise to users. Acquisti et al. (2016), for example, in their recent and comprehensive summary of 'the economics of privacy', makes only a single reference to "information asymmetries regarding the usage and subsequent consequences of shared information" (p.449), makes no reference at all to 'power asymmetries' [REF NEEDED], and seems to avoid acknowledging the variously immoral and illegal behaviour indulged in by marketing corporations [REF NEEDED].
Another feature of the IS literature is widespread avoidance by authors with US affiliations, and more broadly by authors seeking to publish in US-dominated IS journals, of direct suggestions that formal regulation is necessary in order to address rampant abuse of personal data by marketers. The following appears to be indicative of the strength of expression that authors appear confident to use: "doubts are being expressed about the ability of self-regulatory 'notice and consent' and transparency and control mechanisms to adequately protect consumers' privacy (Acquisti et al., 2013; Solove, 2013)" (Acquisti et al. 2016, p. 483).
A third systematic literature review is that by Belanger & Crossland (2011), which examined 142 journal articles, 57 of them in core IS publishing venues. It evidences considerable commonality with that in Smith et al. (2011). It reflects the existing literature in overlooking the primarily social nature of privacy concerns. It accepts unquestioningly the prevalent, usually implicit assumption that economics is what matters, and that the human's economic role (as consumer) is all that needs to be researched. It also adopts uncritically the attitude prevalent in the IS literature that most research should follow-the-leader and apply existing tools, rather than being instrumentalist and problem-driven, striving for problem-solutions. (It does, however, call for more 'design and action' research). It also reflects the IS literature in that the term 'market power', and the concepts of asymmetry and power asymmetry between marketers and consumers, were not evident in the article.
The pool of papers appears to have been strongly oriented towards the system sponsor perspective. Moreover, the papers appear to have evidenced little understanding of stakeholder theory, because the authors found it necessary to say that "researchers should explore whether organizations have different stakes in information privacy than the consumers they serve" (p. 1029). It is difficult for an IS practitioner, a consumer or a policy observer to comprehend that IS researchers may be so ignorant of marketplace realities that they might permit themselves the implicit assumption that the interests of marketers and consumers coincide.
Belanger & Crossland identified five groups of "topics in IS information privacy research", four of which evidence strong orientation towards system sponsor interests. 'Concerns about organisational practices' are of interest to IS researchers not because they fail to fulfil human needs, or harm human interests, but because they "influence individuals' attitudes ... [and] individuals' acceptance of technology" (p. 1020),. In 'E-Business Impacts' research, "individuals' views of privacy affect their intention to participate in e-commerce or e-government interactions, or their willingness to share information with e-commerce merchants or e-government agencies ... In this research, the outcome variable overwhelmingly used is intentions to use an electronic service" (pp. 1020, 1021). In 'Attitudes' research, "the majority of studies look at privacy attitudes as an independent variable that influences behaviors such as creative performance, use and acceptance of invasive technologies, and online information disclosure" (p. 1021). 'Research on organizational practices' "is abundant, and mostly focused on analyses of privacy policies of websites and frameworks for organizational practices. Researchers typically discuss the fair information practices (FIP) compliance in privacy policies or provide assessments or metrics to investigate the policies" (p. 1022). Those findings strongly suggest that the reflection of consumers' needs is at best incidental to the primary purpose of IS research.
On the other hand, the authors made several specific suggestions that are cognisant of the interests of consumers, and of the significant differences between their interests and those of marketing corporations:
Moreover, Belanger & Crossland evidences several key departure points that are highly relevant to the analysis and argument pursued in the present paper.
Firstly, in relation to the perspectives of individuals in their social roles, nothing appears to have been found in the pool of 142 works, and almost nothing was evident in the authors' text either. But Belanger & Crossland made the suggestion that: "One possible avenue to extend [privacy policy statement] research would be to look at other types of organizations beyond commercial websites, for example, studying privacy policies for government agencies" (p. 1029, emphasis added). It appears remarkable that no such study was found in the IS literature. On the positive side, the authors noted that this is a deficiency.
Secondly, although the pool of 142 works appears to have contained no dual-perspective research, Belanger & Crossland made the following suggestion: " ... understanding the desires and interactions of both [companies and the consumer] provides practical insight that can be used to further enhance the online experience for both ... Research could also take the form of an analysis of the dual perspective of the consumer and the web merchant, investigating the impacts of match or mismatch between the privacy preferences of the consumer and the merchant" (pp. 1030, 1031, emphases added). This is a rare instance of prior publication of even the concept of dual-perspective research, let alone use of the same term to describe it.
A third insight in the piece, which seems obvious to IS practitioners, but appears to be necessary to communicate to IS researchers, is that "individuals from different countries can be expected to have different cultures, values, and laws, which may result in differences in [individuals'] perceptions of information privacy and its impacts" (p. 1026).
A final contribution by Belanger & Crossland to the argument pursued in this paper is their fifth topic-area, 'Tools and Technologies'. They note that "[the call for research into privacy enhancing technologies (PETs)] has been mostly answered by computer scientists as opposed to IS researchers ... there are many opportunities for IS researchers to be more involved in research on information privacy tools and technologies ... IS researchers need to identify the features of privacy protection tools that are the most important for consumers" (p. 1022). Further, "of great interest would also be studies of information privacy tools and technologies at the societal level, specifically focusing on potential national bias in design. Is the design of information privacy tools and technologies focused on the American understanding of information privacy, and is that understanding applicable to the rest of the world?" (p. 1030).
[[IS THERE BENEFIT IN EXPANDING THE PREVIOUS EXPLANATION OF MOTIVATION, ALONG THE LINES OF THE FOLLOWING TWO PARAS.?]]
The first-named author has been an active researcher in privacy topics for over four decades. His impression has been that the IS discipline's gatekeepers consider that corporate interests are the primary concern. The adoption of alternative and even balanced approaches appear to be unwelcome. As a result, fewer than one-quarter of his 75 refereed publications in the privacy arena have been in IS venues. For example, has has published studies of the privacy impacts of a range of information technologies (including profiling, data matching, identity authentication, location and tracking, data analytics, social media, data retention by ISPs, and drones). But he found it pointless to try to get them into IS venues, and instead they have appeared in journals and conference proceedings whose scope includes 'IT and policy' topics. Similarly, his works on data protection regulation and privacy impact assessment have been generally unwelcome within IS. Multi-perspective research has been acceptable, although it was safest to smuggle the policy issues in after the primary implications had been drawn for business enterprises. Moreover, 4 of his 7 articles in this category were published in a single journal, Information Techology & People. On the other hand, many of his c. 5,000 Google-citations to privacy works appear in IS venues - which suggests that, when conducting literature reviews, IS researchers have to look outside their mainstream journals in order to identify relevant material.
This section has made observations about the single-perspective and system-sponsor orientation of IS research, and the lack of interest by IS venues in studies that adopt other perspectives, dual perspectives and multiple perspectives. The evidence presented in support of the contentions has comprised personal experience and anecdote reinforced by re-interpretation of other researchers' works. In order to provide stronger evidence and greater depth, the remainder of this article presents an empirical assessment of the relevant IS literature.
This section describes the design of the research that was undertaken in order to gain insight into researcher perspectives adopted in privacy research within the IS discipline. It commences by articulating the general research question. The key term 'IS research' is then operationalised, and an appropriate sample of the IS literature defined and selected. A customised version of the previously established assessment and coding process is then described.
The introductory section included a general research question that was sufficient to provide orientation to the literature reviews presented above. Applying the theory of researcher perspective outlined above to the treatment of privacy in the IS literature, the following, more specific research questions can now be enunciated:
[[Questions that do not deliver interesting results may of course be omitted from the resulting article]]
The process of examining papers for researcher perspective, and coding and documenting them, is exacting and resource-intensive. It was accordingly untenable to examine a population as large as all articles in the IS discipline that have privacy as their core concern. If a high degree of external validity were to be sought, it would be necessary to select a sufficiently large random sample from a defined population, and to demonstrate that key attributes of the sample were comparable with those of the population as a whole. Hence, if random sampling is adopted, the identification of key attributes is crucial to the design. In this case (as in many others), this is a quite challenging undertaking. For one thing, the approach being adopted here is somewhat exploratory, and hence there is a limited body of theory available to assist in defining what aspects of the population of articles are likely to have significant effects on the results.
[[THE ABOVE SEEMS OBVIOUS ENOUGH, BUT PERHAPS A CITATION OR TWO IS NEEDED?
[[ONE REASON FOR THE PARA. IS TO SUPPORT SUBSEQUENT COMMENTS MADE ABOUT THE TWO 2011 ARTICLES - WHICH GOT AWAY WITH SOMEWHAT UNCLEAR EXPLANATIONS OF THEIR SURVEY METHODS]]
The resource-limitation problem has been approached in various ways by previous teams that have sought to understand some aspect of prior IS research practice in relation to privacy. For example, the examination of empirical information privacy research in Smith et al. (2011, pp.1017-18) began by searching several publishers' catalogues, individual journal databases and Web of Science (p.A1), using a small set of keywords to establish a set of contender publications, then filtered the super-set based on examinations of the title and abstract, and citation-counts, and finally adding in further publications that had been cited by, or had cited, documents in the first-round set. The authors refer to the resulting set as being "a sample of 320 privacy articles and 128 books and book sections" (p.989).
Belanger & Crossler (2011) began with "papers on information privacy in the ABI/Informs database" (p.1019). The resulting 340 articles were then screened, in particular for articles on "information privacy research in IS ... that we could code for theoretical foundations, sample characteristics, and level of analysis". Within the remaining pool of 70 articles, citations were then considered, and the secondary pool of over 100 further papers screened to 72, resulting in a "sample of 142".
In Li (2011), the catchment was limited to studies that were in the e-commerce domain, that reported empirical studies of an individual's behaviour, that used a qualified construct, and that were published in a peer-reviewed journal or ICIS Proceedings, and thate were published since 1996. Titles, abstracts and keywords in a wide array of catalogues were scoured for keywords, resulting in close to 5,000 titles, screened down to a pool of 88.
In all three studies, the pool is referred to as a sample, but without a clear definition of sampling frame and population, and hence it is unclear whether the sample characteristics correspond with the population distribution. The three pools may therefore be better interpreted as the populations of publications judged by the authors to be relevant to each study.
Random sampling, whether within a population, or within a sampling frame used as a proxy for a population, implicitly assumes that 'all articles are equal'. In terms of influence, however, it is patently not the case that all articles are equal. The vast majority of articles that are published achieve very few citations, limited readership and even more limited influence, either on practice or on subsequent research. This pattern may be in the process of becoming even more pronounced, as a result of the flood of publications arising from the influx of researchers and authors, and the demands of their employers for quantity of publications. For the present purpose, a more appropriate approach to sample selection is a form of stratified random sampling, with an intentional and strong bias favouring papers with significant influence, but with a second stratum defined in terms of originality or disruptive potential.
As an operational definition for 'influence', consideration could be given to citation-count. If so, it is necessary to moderate for time-since-publication, in order to avoid overlooking papers that have not yet had time to accumulate many citations but may be influential in current research projects whose results have not yet been published. Alternative approaches might take into account the venue in which the paper appears and/or the reputation of the author(s).
Relying on influence alone would create the risk of failing to detect alternative, minority-view or outlier papers that may offer insights missed by mainstream work, or may be harbingers of change. Hence a complementary strategy is needed, in order to detect original contributions that have disruptive potential.
The population "IS research" might reasonably be defined as being all papers published in refereed journals and conference proceedings whose title and description include 'information systems' used in a manner consistent with the (somewhat contested) sense(s) common among IS academics. This might be operationally defined as the set of journals included in John Lamp's Index of IS Journals (which number in the range 600-900), together with the 16 conferences that are included in the AIS eLibrary's Collections of AIS, Affiliated and Other Conferences. The temporal scope of the study was defined as extending from the emergence of the discipline c.1965 (Clarke 2008, Hirschheim & Klein 2012) to the end of 2018.
An approach to sample selection was devised that reflects the above discussion. Consideration was given to 'standing on the shoulders of giants' and contributing to a 'cumulative tradition' within the discipline (Keen 1980), by adopting and extending the works in the literature reviews of Smith et al. (2011) and Belanger & Crossland (2011). However, testing would have had to be performed of the comprehensiveness or representativeness of those pools, and a broad search would still have been necessary, in order to identify further works, in order to complement the prior-reviews list by:
Given these factors, it appeared to be more appropriate and more practical to instead conduct a series of searches, using a variety of facilities, but to then check the results against the pools in Smith et al., Belanger & Crossland and Li.
For a work to be relevant to the study, the qualifying conditions were defined as being that the work had to:
Free-text search languages of the 1960s, such as Status and STAIRS supported such capabilities. The quality of search facilities currently available, however, is far inferior to those standards. Google's is not metadata-based, the language is limited, and the algorithms are intentionally obfuscated. The bepress system on which the AIS eLibrary runs also has significant limitations. The various commercial publishers offer facilities, but none of them have the power of the earlier products, and most are very weak and error-prone. In all cases, it is therefore necessary to apply such techniques as are available in order to approximate or sub-set the preferred selection criteria defined above.
Firstly, a pool of works was sought that satisfied the test of influence, and then works were sought in other venues that appeared likely to contain works of originality.
As proxies for influence, the following were adopted:
As proxies for originality, the following approach was adopted:
Searches of the available archives of Basket of 8 articles delivered 118 works, and the 2 conferences 37. The very large collections of ICIS papers were pseudo-randomly sampled to provide a similar number of contenders to the journals. The 8 'originality' journals provided 97 and the 2 conferences 28. Google Scholar searches identified a further 11 works. The resultant pool of 291 was then checked against those of the three previously-cited literature reviews. Smith et al. (2011)'s 82 items and Belanger & Crossland (2011)'s 57 had only a small intersection of 22 works. The 88 from Li (2011) were also considered. As a result, a further 32 works were added to the pool for consideration in this research, resulting in a total of 323 works.
In Appendix 2, a detailed report is presented on the rationale and mechanics of the sample selection process.
The researcher perspectives adopted in published research have been assessed in multiple prevkous projects (Clarke (2015, 2016b and 2017) and Jia et al. (2019). The established coding protocol has been adapted to the specific context of privacy research, and is provided at Appendix 1.
[[SUBJECT TO FURTHER CONSIDERATION OF THE PROCESS:
The
articles were first coded by one team-member, then reviewed and if necessary
re-coded by another, then further reviewed by the third. Where discrepancies
arose, they were discussed and resolved. Sufficient was recorded about each
article to show the basis on which codes were assigned, and to support review,
audit, and replication. Agreement was achieved on all codings, thereby
satisfying the requirement for inter-rater reliability.
To enable encoding of each article, preliminary steps were necessary. A sufficiently deep understanding of an article depends on first appreciating the author's purpose. Depending on the type of research, this may be expressed in the form of a Research Question (for empirical work, both positivist and interpretivist), or an Objective (particularly for design science research), or a Topic-Area (in the case of theoretical discussions). The first two steps were accordingly to categorise the type of research, and to then isolate the purpose. Wherever possible this was done by extracting the author's own words, but where necessary the purpose was inferred from the text as a whole.
The central concern of the assessment was the identification of researcher perspective. This was achieved by isolating passages that indicate the interests that are being represented and/or the audience to which the outcomes are addressed. Explicit statements of the perspective adopted by the researcher were sought, [[CHECK: but were seldom found]]. Even where found, however, they were evaluated within the context of the whole text. Key passages were noted. A cardinality measure was recorded, to identify respectively single-, dual- and multi-perspective research. Sufficient data was recorded to support deeper analyses where required.
Indicatively, a single-perspective article would, if favouring the system sponsor, contain statements of such forms as 'we examined the extent to which <an intervention> delivers benefits to the organisation' and 'the research shows that the organisation benefits from ...'. Mentions of the individuals whose privacy is affected would likely be used in negative senses, as having interests that compete with those of the organisation, or as actors whose behaviour acts as a constraint on the achievement of the organisation's objectives.
On the other hand, a single-perspective article that adopts the perspective of the affected individuals would contain statements such as 'we examined the impact on consumers of <an intervention>', or 'employees are likely to find it advantageous to ...'. The system sponsor would be likely to be considered as an entity whose actions are competing with and even hostile to the individual's interests.
A dual-perspective article could be expected to contain such statements as 'we sampled the opinions of both managers and their staff', or 'the final section identifies implications for both marketing organisations and consumers'. A paper may be dual-perspective even if the two perspectives are unevenly weighted. The threshold test is whether material attention is paid to each of two perspectives, not whether the two are equally-weighted. However, if the weighting is pronouncedly uneven, it may be appropriate to distinguish primary and secondary perspectives.
A multi-perspective article may refer to more than two specific categories of stakeholder, in which case the text may contain more complex forms of the examples provided above for dual-perspective research. Alternatively, the paper may be phrased in more general terms, e.g. by using abstract notions ('for the general good of society', 'benefits to the economy as a whole'). Again, the threshold test is whether serious attention is paid to more than two perspectives, rather than whether the attention is in some sense equally-weighted.
The dimension was encoded as Economic, Social or Both, based on the presence, frequency and apparent importance of key concepts. The economic dimension is indicated by terms such as revenue, costs, profit, market-share, growth and competitive advantage; whereas terms such as wellbeing, fairness and equity are associated with the social dimension. The threshold test was not equality of emphasis but rather material attention to values on the particular dimension.
The process of detailed research design, followed by trial application of the coding protocol, suggested two further research questions.
The sample selection process involves 16 journals and 4 conference series, in two distinct venue clusters. Patterns within venues and within clusters might be expected to evidence differences. This gives rise to the question:
A number of recurring approaches to privacy research in IS were detected. They are referred to in this article as 'research genres'. One that has been particularly prominent involves empirical research into the 'privacy calculus' postulate. This gives rise to the following further question:
[[PRESUMABLY THESE WILL BE PRESENTED IN SEQUENCE OF THE RQs]]
[[SOME SUB-SETS NEED TO BE CONSIDERED:
[[IN THE CASE OF PATTERNS OVER TIME (RQ6):
[[TESTING OF THE INFLUENCE / ORIGINALITY DISTINCTION MAY BE APPROPRIATE, e.g. sort by citation-count and extract some measure of the dominance (or otherwise) of 'influence' over 'originality' venues. An initial calculation suggests less dominance than might have been expected - c.70% of the Top-20% works were from 'influence' venues; but below the Top-20% works the distribution is not greatly different. The Top-20% of works accounted for a little over 80% of the total citation-count, and the influence venues had almost 2/3rds of those citations; but for the remaining 80% of works the total citation-counts for 'influence' and 'originality' were almost identical.
[[USE QUOTATIONS FROM WORKS TO SUPPORT POINTS BEING MADE
[[PROVIDE BRIEF DESCRIPTIONS OF EXEMPLAR WORKS WITHIN EACH RELEVANT CATEGORY
[[PROVISIONAL OF COURSE, SUBJECT TO WHAT THE DATA SHOWS!!
[[Show ways in which IS research can address the needs of stakeholders
[[Show ways in which more dual- and multi-perspective research can improve IS research quality, and serve the needs of various clienteles rather than only system sponsors
[[Note Gimpel et al. (2018) in EM. This refers to 'delighting customers', but with "data-driven business models" as the objective, and privacy measures as a means of addressing the constraint of "customers' concerns". The authors seek to shift the business view from the negativeness of the "necessary evil" of "compliance and risk management", towards the positive "potential to create a competitive advantage", but it remains a single-perspective / system sponsor approach. In any case, the proposition is anything but new (e.g. Clarke 1996, 2006).
TEXT
Acquisti A., John L.K. & Loewenstein G. (2013) 'What Is Privacy Worth?' Journal of Legal Studies 42, 2 (June 2013) 249-274
Baumer E.P.S. (2015) 'Usees. Proceedings of the 33rd Annual ACM Conference on Human Factors in Computing Systems (CHI'15), April 2015
Belanger & Crossler (2011) 'Privacy in the Digital Age: A Review of Information Privacy Research in Information Systems' MIS Quarterly Vol. 35 No. 4 pp. 1017-1041/December 2011, at https://vtechworks.lib.vt.edu/bitstream/handle/10919/81984/BelangerPrivacy2011.pdf?sequence=1
Belanger, F., Hiller, J. S., and Smith, W. J. 2002. 'Trustworthiness in Electronic Commerce: The Role of Privacy, Security, and Site Attributes' Journal of Strategic Information Systems (11:3/4), pp. 245-270.
Bennett C.J. (1992) 'Regulating Privacy: Data Protection and Public Policy in Europe and the United States' Cornell University Press, New York, 1992
Bergman A. (2018) 'Celebrate Data Privacy Day with a Website Check Up!' Adobe Blog, 29 January 2018, at https://theblog.adobe.com/celebrate-data-privacy-day-website-check/
Bygrave L.A. (2014) 'Data Privacy Law: An International Perspective' Oxford University Press, 2014
Cate F.H. (2006) 'The Failure of Fair Information Practice Principles' in Consumer Protection in the Age of the Information Economy, 2006, at https://papers.ssrn.com/sol3/papers.cfm?abstract_id=1156972
Clarke R. (1992) 'Extra-Organisational Systems: A Challenge to the Software Engineering Paradigm' Proc. IFIP World Congress, Madrid, September 1992, PrePrint at http://www.rogerclarke.com/SOS/PaperExtraOrgSys.html
Clarke R. (1997) 'Introduction to Dataveillance and Information Privacy, and Definitions of Terms' Xamax Consultancy Pty Ltd, 15 August 1997, at http://www.rogerclarke.com/DV/Intro.html
Clarke R. (1999) 'Internet Privacy Concerns Confirm the Case for Intervention' Communications of the ACM 42, 2 (February 1999) 60-67, PrePrint at http://www.rogerclarke.com/DV/CACM99.html
Clarke R. (2001) 'Person Location and Person Tracking: Technologies, Risks and Policy Implications' Information Technology & People 14:2 (2001) 206-231, at http://www.rogerclarke.com/DV/PLT.html
Clarke R. (2008) ' A Retrospective on the Information Systems Discipline in Australia' Chapter 2 of Gable G.G. et al. (2008) 'The Information Systems Discipline in Australia' ANU e-Press, 2008, pp. 47-107, at http://epress.anu.edu.au/info_systems_aus/pdf_instructions.html, PrePrint at http://www.rogerclarke.com/SOS/AISHist.html
Clarke R. (2014) 'Privacy and Social Media: An Analytical Framework' Journal of Law, Information and Science 23,1 (April 2014) 1-23, PrePrint at http://www.rogerclarke.com/DV/SMTD.html
Clarke, R. (2015). Not Only Horses Wear Blinkers: The Missing Perspectives in IS Research, Proc. ACIS'15, Adelaide, December 2015, at http://www.rogerclarke.com/SOS/ACIS15.html
Clarke R. (2016a) 'A Framework for Analysing Technology's Negative and Positive Impacts on Freedom and Privacy' Datenschutz und Datensicherheit 40, 2 (February 2016) 79-83, http://www.rogerclarke.com/DV/Biel15-DuD.html
Clarke, R. (2016b). An Empirical Assessment of Researcher Perspectives, Proc. 29th Bled eConf., Slovenia, June 2016, PrePrint at http://www.rogerclarke.com/SOS/BledP.html
Clarke, R. (2017). Content Analysis in Support of Critical Theory Research: How to Deliver an Unwelcome Message Without Being Shot' Proc. 30th Bled eConference, June 2017, PrePrint at http://www.rogerclarke.com/SOS/CACT.html
Clarke R. (2019) 'Risks Inherent in the Digital Surveillance Economy: A Research Agenda' Forthcoming, Journal of Information Technology 34,1 (Mar 2019), PrePrint at http://www.rogerclarke.com/EC/DSE.html
Clarke R. & Davison R.M. (2019) 'Through Whose Eyes? The Critical Concept of Researcher Perspective' Working Paper, Xamax Consultancy Pty Ltd, 10 December 2018, at http://www.rogerclarke.com/SOS/RP.html
Clarke R. & Pucihar A. (2012) 'The Web of Science Revisited: Is it a Tenable Source for the Information Systems Discipline or for eCommerce Researchers? Working Paper, 29 August 2012, Xamax Consultancy Pty Ltd, at ://www.rogerclarke.com/SOS/WoSRev.html
CoE (1981) 'Convention for the Protection of Individuals with regard to Automatic Processing of Personal Data' COETS 1 (28 January 1981), at http://www.worldlii.org/int/other/COETS/1981/1.html
CoE (2001) 'Additional Protocol to the Convention for the Protection of Individuals with regard to Automatic Processing of Personal Data, regarding supervisory authorities and transborder data flows' COETS 4 (8 November 2001), at http://www.worldlii.org/int/other/COETS/2001/4.html
CoE (2018) 'Protocol amending the Convention for the Protection of Individuals with regard to Automatic Processing of Personal Data' CETS No.223, 10/10/2018, at https://www.coe.int/en/web/conventions/full-list/-/conventions/treaty/223
Cohen J.E. (1996) 'A Right to Read Anonymously: A Closer Look at 'Copyright Management' In Cyberspace' 28 Conn. L. Rev 981 (1996) , at 17990http://papers.ssrn.com/sol3/papers.cfm?abstract_id=17990
Cohen J.E. (2013) 'What Privacy is for' Harvard Law Review 126 (2013) 1904-1907
Cowen Z. (1969) 'The Private Man' The Boyer Lectures, Australian Broadcasting Commission, Sydney, 1969
de Hert P. & Czerniawski M. (2016) 'Expanding the European data protection scope beyond territory: Article 3 of the General Data Protection Regulation in its wider context' International Data Privacy Law 6, 3 (2016) 230-243
Donaldson T. & Preston L. E. (1995) 'The Stakeholder Theory of the Corporation: Concepts, Evidence, and Implications' Academy of Management Review 20, 1 1995) 65-91
EDPB (2018) 'Guidelines 3/2018 on the territorial scope of the GDPR (Article 3) - Version for public consultation' European Data Protection Board, 16 November 2018, at https://edpb.europa.eu/sites/edpb/files/files/file1/edpb_guidelines_3_2018_territorial_scope_en.pdf
EU (1995) 'The Directive on the protection of individuals with regard to the processing of personal data and on the free movement of such data', Directive 95/46/EC of the European Parliament and of the Council of 24 October 1995, at https://eur-lex.europa.eu/LexUriServ/LexUriServ.do?uri=CELEX:31995L0046:en:HTML
Fernandez-Aleman J.L., Senor I.C., Lozoya P.A.O. & Toval A. (2013) 'Security and privacy in electronic health records: A systematic literature review' Journal of Biomedical Informatics, Volume 46, Issue 3, June 2013, Pages 541-562, at https://www.sciencedirect.com/science/article/pii/S1532046412001864
Finn R. L., Wright D. & Friedewald M. (2013) 'Seven types of privacy' in Gutwirth S. et al. (eds) 'European Data Protection: Coming of Age' , Springer, 2013, pp. 3-32, at http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.827.5418&rep=rep1&type=pdf
Fischer-Hübner S. & Lindskog H. (2001) 'Teaching Privacy-Enhancing Technologies' Proceedings of the IFIP WG 11.8 2nd World Conference on Information Security Education, Perth, Australia
Flaherty D.H. (1984) 'Privacy and Data Protection: An International Bibliography' Mansell, 1984
FTC (2000) 'Privacy Online: Fair Information Practices in the Electronic Marketplace: A Federal Trade Commission Report to Congress' Federal Trade Commission, May 2000, at http://www.ftc.gov/reports/privacy2000/privacy2000.pdf
Freeman, R.E. (1984). Strategic Management: A Stakeholder Approach. Cambridge: Ballinger
GDPR (2016) 'EU General Data Protection Regulation', April 2016, at http://www.privacy-regulation.eu/en/index.htm
Gellman R. (2017) 'Fair Information Practices: A Basic History' SSRN, Version 2.18, April 2017, at http://www.bobgellman.com/rg-docs/rg-FIPShistory.pdf
Greenleaf G.W. (2003) 'IP, Phone Home: Privacy as Part of Copyright's Digital Commons in Hong Kong and Australian Law' in Lessig L. (ed.) 'Hochelaga Lectures 2002: The Innovation Commons' Sweet & Maxwell Asia, Hong Kong, 2003, at http://papers.ssrn.com/sol3/papers.cfm?abstract_id=2356079
Greenleaf G.W. (2012) 'The Influence of European Data Privacy Standards Outside Europe: Implications for Globalisation of Convention 108' International Data Privacy Law 2, 2 (2012) 68-92, at http://papers.ssrn.com/ abstract_id=1960299
Greenleaf G.W. (2014) 'Asian Data Privacy Laws - Trade and Human Rights Perspectives' Oxford University Press, 2014
Greenleaf G.W. (2017) ''European' Data Privacy Standards Implemented in Laws Outside Europe' Privacy Laws & Business International Report 149 (September 2017) 21-23, PrePrint at https://ssrn.com/abstract=3096314
Hirschheim R. & Klein H.K. (2012) 'A Glorious and Not-So-Short History of the Information Systems Field' Commun. AIS 13, 4, (2012) 188-235
ICCPR (1996) 'International Covenant on Civil and Political Rights' United Nations, 1966, at http://treaties.un.org/doc/Publication/UNTS/Volume%20999/volume-999-I-14668-English.pdf
Introna L.D. & Pouloudi A. (1999) 'Privacy in the Information Age: Stakeholders, Interests and Values' Journal of Business Ethics 22, 1 (October 1999) 27-38
DoC (2016) 'Privacy Shield: Requirements of Participation' U.S. Department of Commerce, July 2016, at https://www.privacyshield.gov/article?id=Requirements-of-Participation
Jia W., Davison R.M. & Clarke R. (2019) 'Researcher Perspective in the IS Discipline: An Empirical Study of Articles in the Basket of 8 Journals' Manuscript under review, December 2018, at http://www.rogerclarke.com/SOS/RPBo8.html
Keen P.G.W. (1980) 'MIS Research: Reference Disciplines and a Cumulative Tradition' Proc. ICIS 1980, 9
Koops B.J., Newell B.C., Timan T., Korvanek I., Chokrevski T. & Gali M. (2016) 'A Typology of Privacy' University of Pennsylvania Journal of International Law 38, 2 (2016), at https://papers.ssrn.com/sol3/papers.cfm?abstract_id=2754043
Laudon K.C. (1993) 'Markets and Privacy' Stern School of Business, Workinq Paper Series IS-93-21, July 1993, at http://archive.nyu.edu/bitstream/2451/14257/1/IS-93-21.pdf. Revised version published in Communications of the ACM 39, 9 (September 1996) 92-104
Li Y. (2011) 'Empirical Studies on Online Information Privacy Concerns: Literature Review and an Integrative Framework' Communications of the Association for Information Systems: Vol. 28 , Article 28.
Li Y. (2012) 'Theories in online information privacy research: A critical review and an integrated framework' Decision Support Systems Volume 54, Issue 1, December 2012, Pages 471-481
Lindsay D. (2005) 'An Exploration of the Conceptual Basis of Privacy and the Implications for the Future of Australian Privacy Law' Melb. Uni. L. Rev. 29, 1 (2005) 131-178
Mason R.O (1986) ' Four Ethical Issues of the Information Age' MIS Quarterly 10, 1 (March 1986) 4-12
Morison W.L. (1973) 'Report on the Law of Privacy' Government Printer, Sydney, 1973
OECD (1980) 'Guidelines on the Protection of Privacy and Transborder Flows of Personal Data', Organisation for Economic Cooperation and Development, Paris, 1980, at http://www.oecd.org/document/18/0,2340,en_2649_201185_1815186_1_1_1_1,00.html
Packard V. (1964) 'The Naked Society' McKay, New York, 1964
Posner R.A. (1977) 'The Right of Privacy' 12 Georgia Law Review 393, at http://chicagounbound.uchicago.edu/cgi/viewcontent.cgi?article=2803&context=journal_articles
Rubenfeld J. (1989) 'The Right of Privacy' Harvard Law Review 102 (1989) 737-784, at https://digitalcommons.law.yale.edu/cgi/viewcontent.cgi?referer=&httpsredir=1&article=2568&context=fss_papers
Rule J.B. (1974) 'Private Lives and Public Surveillance: Social Control in the Computer Age' Schocken Books, 1974
Rule J.B., McAdam D., Stearns L. & Uglow D. (1980) 'The Politics of Privacy' New American Library 1980
Schoeman F.D. (1984) 'Philosophical Dimensions of Privacy: An Anthology' Cambridge University Press, 1984, 2009
Shapiro C. & Varian H.R. (1999) 'Information Rules: A Strategic Guide to the Network Economy' Harvard Business School Press, 1999
Smith H.J., Dinev T. & Xu H. (2011) 'Information Privacy Research: An Interdisciplinary Review' MIS Quarterly 35, 4 (December 2011)
Smith R.E. (ed.) (1974-) Privacy Journal, Providence RI, monthly since November 1974
Solove D.J. (2006) 'A Taxonomy of Privacy' 154 U. Pa. L. Rev. 477 (2006), at http://scholarship.law.gwu.edu/cgi/viewcontent.cgi?article=2074&context=faculty_publications
Warren S. & Brandeis L.D. (1890) 'The Right to Privacy' 4 Harvard Law Review (1890) 193-220, at http://athena.louisville.edu/library/law/brandeis/privacy.html
Westin A.F. (1967) 'Privacy and Freedom' Atheneum 1967
Westin, A.F., Ed. (1971) 'Information Technology in a Democracy', Harvard University Press, Cambridge, Mass., 1971
Westin A.F. & Baker M.A. (1974) 'Databanks in a Free Society: Computers, Record-Keeping and Privacy' Quadrangle 1974
Whitman J.Q. (2004) 'The Two Western Cultures of Privacy: Dignity Versus Liberty' Yale L.J. 113 (2004) 1151-60
Zuboff, S. (2015). Big other: Surveillance capitalism and the prospects of an information civilization. Journal of Information Technology, 30, 75-89, at https://cryptome.org/2015/07/big-other.pdf
TEXT
Roger Clarke is Principal of Xamax Consultancy Pty Ltd, Canberra. He is also a Visiting Professor in Cyberspace Law & Policy at the University of N.S.W., and a Visiting Professor in the Computer Science at the Australian National University.
| Personalia |
Photographs Presentations Videos |
Access Statistics |
 |
The content and infrastructure for these community service pages are provided by Roger Clarke through his consultancy company, Xamax. From the site's beginnings in August 1994 until February 2009, the infrastructure was provided by the Australian National University. During that time, the site accumulated close to 30 million hits. It passed 65 million in early 2021. Sponsored by the Gallery, Bunhybee Grasslands, the extended Clarke Family, Knights of the Spatchcock and their drummer |
Xamax Consultancy Pty Ltd ACN: 002 360 456 78 Sidaway St, Chapman ACT 2611 AUSTRALIA Tel: +61 2 6288 6916 |
Created: 16 December 2018 - Last Amended: 30 January 2019 by Roger Clarke - Site Last Verified: 15 February 2009
This document is at www.rogerclarke.com/DV/RPP.html
Mail to Webmaster - © Xamax Consultancy Pty Ltd, 1995-2022 - Privacy Policy