Roger Clarke's Web-Site
© Xamax Consultancy Pty Ltd, 1995-2024

Infrastructure
& Privacy
Matilda
Roger Clarke's Web-Site© Xamax Consultancy Pty Ltd, 1995-2024 |

|
|||||
| HOME | eBusiness |
Information Infrastructure |
Dataveillance & Privacy |
Identity Matters | Other Topics | |
| What's New |
Waltzing Matilda | Advanced Site-Search | ||||
Version of 16 May 2009
Presented at IDIS 2009 - The 2nd Multidisciplinary Workshop on Identity in the Information Society, London School of Economics, 5 June 2009
© Xamax Consultancy Pty Ltd, 2008-09
Available under an AEShareNet ![]() licence or a Creative
Commons
licence or a Creative
Commons  licence.
licence.
This document is at http://www.rogerclarke.com/ID/IdModel-090605.html
The accompanying Glossary is at http://www.rogerclarke.com/ID/IdModelGloss.html
The accompanying slide-set is at http://www.rogerclarke.com/ID/IdModel-090605.ppt
During the last 20 years, the practice of identification and identity authentication has been highly unsatisfactory. One important reason for this has been that the theory underpinning the practice has been seriously deficient.
A model is presented that is argued to be sufficiently comprehensive and rich to reflect the relevant complexities, and hence to guide organisations in devising architectures and business processes for such activities as user registration, 'sign-on' and 'identity management'. The sufficiency of the model is evaluated by means of brief analyses of its application to relevant categories of entity and identity.
Organisations are confronted by many risks, and seek ways to understand and manage those risks. The most effective form of risk management is proactive, based on foreknowledge of key information. In particular, organisations want to have confidence in assurances given to them by others on which their success depends. This paper focusses on one particular cluser of assurances - that the entity or identity the organisation is dealing with is who or what it purports to be. Relevant categories of entity include people, organisations, goods, containers, vehicles, devices of various kinds, and software packages.
Achieving an appropriate level of confidence in assertions about entities and identities, and doing so without undue cost and effort, has always been challenging. For an extended period, the contexts were mostly physical, and involved assurances in relation to such things as physical goods, and the entrance of goods and people into physical locations, and the behaviour of those people once they were on the premises. Particularly since the widespread application of online computing to business processes from the 1970s onwards, however, digital goods, virtual locations and disembodied actions have become much more commonplace. That has given rise to new forms of uncertainty and risk. As a result, during the last 20 years a great deal of attention has been paid to various aspects of identification and authentication, and many schemes have been implemented, particularly in relation to goods, containers, vehicles, devices, animals and people.
A great deal of the investment has delivered unsatisfactory outcomes, most of all in relation to people. Fraud continues to be perpetrated in great volumes, particularly in the context of credit-card payments. Identity fraud has become widespread. Individuals are issued with and required to use large numbers of identifiers and credentials, and they continually forget, lose and compromise them. Despite many initiatives, 'single sign-on' remains wishful thinking, and even 'simplified sign-on' remains uncommon. Digital signatures, which once appeared to be a highly promising invention, have remained little-used, and their effectiveness in most real-world contexts is in serious doubt (Clarke 2001b). 'Identity management' initiatives continue to promise more than they deliver (Clarke 2004c).
This author has been active in the domain for two decades, variously as researcher and consulltant. I have observed first-hand widespread, inadequate understanding of the2009a identity authentication, particularly in eBusiness and eGovernment contexts. The mistaken appreciation shown by many business analysts, executives and managers and technology providers alike has reflected naiveté in the models used by academics, and the theories that they put forward. Simplistic assumptions continue to be made about entities, about the various identities that entities adopt, about the processes by which confidence in assertions is achieved, and about the authenticators used in those processes.
Based on a combination of consultancy practice and research, I have progressively developed a model which I believe to be sufficiently comprehensive and rich to enable effective analysis of identification and authentication needs to be undertaken. Further, based on this model, architectures, credentials and business processes can be devised that are appropriate to the wide variety of circumstances that arise in busineess and government. Yet further, I believe that the use of any model less complete than this one is doomed to perpetuate the inadequacies and outright failures experienced in this domain during the last two decades.
The purpose of this paper is to provide an exposition of theory intended to address the inadequacies of existing theory, and underpin more satisfactory practice in the area. The paper does not provide conventional references to the literature. It does, however, refer to a long series of papers in which the model was developed, which are listed under Sources below. Fifteen of those papers appeared in the refereed literature and cite many references.
The paper comprises two sections. In the first, the model is presented. The model comprises a set of concepts for which definitions are provided, and whose inter-relationships are displayed. In the second section, the model is applied to a number of different categories of entity. The purposes of doing this are to provide an adequate sample of the considerable richness and diversity of requirements, and to demonstrate that the model is sufficient to enable description and analysis of important real-world problems.
This section presents a set of working definitions of key terms that underpin studies of identity in the information society. The definitions are instrumentalist in their origins and purpose. They adopt the conventional ontological presumptions: that there is a real world of things; and that there is an abstract world of data that is created, stored, transmitted, used and disclosed by means of combinations of manual procedures and automated processes that utilise various kinds of information technology.
A small number of meta-comments are provided in italics. These relate to the origins of the less commonly-used terms, and alternatives to them.
The model comprises two segments. The first, presented in diagrammatic form in Figure 1, has a form akin to an entity-attribute-relationship (EAR) model. It depicts most of the key concepts, and the following sub-sections provide definitions of each of them. The second segment of the model addresses the processes involved in authentication and authorisation, and is presented in the final sub-section.
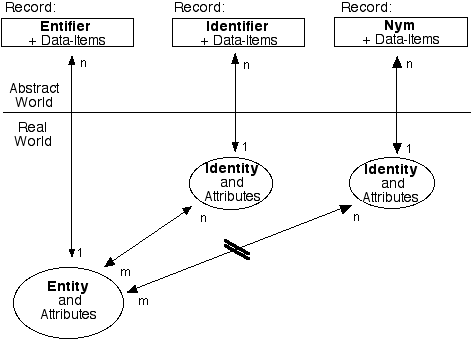
First published in Clarke (2001d)
Entity. An entity is a real-world thing. The notion encompasses pallets piled with cartons, the cartons, and each item that they contain, plus artefacts such as computers and mobile phones, and animals and human beings.
Identity. An identity is also a real-world thing, but is of virtual rather than physical form. Some kinds of entity may present many identities. For example, identities may correspond to the multiple processes that are running in a computing device, or the particular SIM-card currently inserted into a particular mobile phone. A person (whether human or legal) may also present many identities, to different people and organisations, and in different contexts. Each identity is commonly a presentation or role of an underlying entity. Examples important in eCommerce and eGovernment include customer/client, supplier, employee and contractor.
During recent decades, organisations have co-opted the term 'identity' to refer to something that they create and that exists in machine-readable storage. Better terms exist to describe that notion (such as 'digital persona', discussed below). The term 'identity' has widespread usage among normal people to refer to a real-world phenomenon evidenced by human beings, and it is important that observers respect that usage rather than co-opting the term for other purposes.
Where appropriate, the expression 'entity and/or (id)entity' is abbreviated to '(id)entity', in order to enable statements that apply to both to be written once rather than twice. The expressions '(id)entifier' and '(id)entification' are used in similar manner.
Nymity. The term nymity usefully encompasses both anonymity and pseudonymity. The term anonymity refers to a characteristic of an identity, whereby it cannot be associated with any particular entity, whether from the data itself, or by combining it with other data. The term pseudonymity refers to a similar but materially different characteristic of an identity. In this case, the identity may be able to be associated with a particular entity, but only if legal, organisational and technical constraints are overcome. In the diagram, nymity is signified by the interference with the arrow linking the entity with the nymous identity.
Attributes. Both entities and identities have attributes, or characteristics. For example, human entities have physiological characteristics such as hair colour and psychological traits such as expertise; whereas an identity such as a particular eConsumer may have a profile containing attributes such as demographics, user-interface preferences, and the default credit-card details and default delivery-address to be used for purchases. Attributes, like the things they are associated with, exist in the real world.
Entity-to-Identity Relationship. In Figure 1, entities and identities are shown as having an m:n relationship. Firstly, each entity may have multiple identities (e.g. a person may play multiple roles, and a mobile-phone may contain multiple SIM-cards, at least at different times and in some cases even at the same time). In the diagram, that is represented by the 'n' at the end of the arrow.
In addition, each of the identities may be used by multiple entities, and hence the other end of the arrow is marked with an 'm'. For example, the identity 'associate editor of a particular journal' is adopted by multiple people, both in parallel and in succession. Similarly, email client-software may send messages on behalf of the device's normal user; but if malware is installed such that the device is a 'zombie', then the device may also send messages on behalf of the botnet manager, or the botnet manager's clients.
The ambiguity in the relationship between entities and identities may be intended and well-known. Alternatively, a person (or any other sentient entity) might want to be the only user of a particular identity, or an organisation may want a particular identity to be used only by a specific entity. It is challenging, however, to prevent use of identities by other parties. Such activities are described by such terms as impersonation, masquerade, spoofing, identity fraud and identity theft.
All of the concepts introduced in the previous sub-section exist in the real world. This sub-section introduces their correlates in the abstract world of information systems.
Records. Each entity and each identity may be represented by a record that contains data. Each record relates to a particular instance of the general category of entity (e.g. computers, organisations or human beings) or of identity (e.g. processes running in a computer, business divisions of an organisation, or roles played by a human being).
Data-Items. The attributes of the real-world entity or identity are represented by the content of data-items stored in the relevant record. A record associated with an entity or identity may also contain data representing transactions conducted between the (id)entity and the organisation, and data generated by the record-keeper. An important example of data generated by the record-keeper is authorisations (also referred to as permissions or privileges). These are addressed in a later sub-section.
(Id)entity-to-Record Relationship. Each (id)entity may give rise to an associated record in each of multiple data collections, but each record is intended to relate to just one (id)entity. Hence the cardinality is shown in Figure 1 as a 1:n relationship, by which is meant that each (id)entity is associated with 'n' (i.e. zero, one or more) records.
Digital Persona. The collection of data stored in a record is designed to be rich enough to provide the record-holder with an adequate image of the represented entity or identity. The term 'digital persona' is usefully descriptive of the phenomenon. It was my own coinage, first presented at the Computers, Freedom & Privacy Conference in San Francisco (Clarke 1993), and published in Clarke (1994a, and 1994b). But it is in any case an intuitive term and has gained some degree of currency. It is quite common to see the term 'identity' used to refer to what is called here a digital persona; but 'identity' has many meanings, and to avoid ambiguity it is far preferable that some other term be used. Another candidate term is e-persona. The term 'partial' (which originated in the sci-fi genre) is also a contender, because it underlines the inherent incompleteness of a digital persona in comparison with the real-world entity or identity it represents.
Data Silo. As indicated by the cardinality markers in Figure 1, a real-world (id)entity may have multiple records associated with it. Each set of records may be a 'data silo', separate from the others. In particular, records about an individual that are held by different government agencies, by different divisions of the same agency, by different corporations, and by different divisions of the same corporation, are maintained separately from one another, in many cases as a legal requirement. During recent years, this phenomenon has tended to be regarded as an impediment to quality of service, and even more so to efficiency in business and government. These justifications have been used for the breaking down of data silos through the correlation, matching, consolidation or merger of multiple sets of records. This has undermined a longstanding side-effect of data silos - privacy protection.
Identifier. An identity can be distinguished from others in the same category by means of some sub-set of its attributes. A data-item or items that represent such attributes is called an identifier.
One example of an identifier is the particular name or name-variant that a person commonly uses in a particular context (such as with family, with a particular group of friends, or when working in a customer-facing role such as a telephone help-desk). Names are highly variable and error-prone, and do not represent convenient identifiers for operators of information systems. More effective and efficient business processes can be achieved by means of an organisation-imposed alphanumeric code (Clarke 1994d). Examples include a customer-code or a username (for a human identity); an International Mobile Subscriber Identity or IMSI (in the case of the identity of the SIM-card currently in a particular GSM mobile phone); and a process-id (e.g. for a software agent).
Entifier. An identifier is associated with an identity, and not directly with the underlying entity, e.g. not directly with a person, a mobile-phone, or a computer. In order to distinguish an entity from others of the same category, a separate term is needed to refer to a suitable sub-set of the entity's attributes. An appropriate term is entifier. The term entifier has been used consistently in my works since Clarke (2001D), but is not yet widely adopted. It has the advantages of being obvious and being otherwise unused. Contemporary approaches to 'identity management' suffer important deficiencies (Clarke 2004c) that will not be overcome until the concept is better-appreciated, and a commonly-used name arises for it.
Examples of entifiers that distinguish an artefact from others of the same category include the serial-number of white goods such as a refrigerator, a computer's processor-id (or a suitable proxy such as the identifier of its network interface card / NICId) and the International Mobile Equipment Identity (IMEI) which distinguishes each mobile-phone - as distinct from the IMSI, which distinguishes the subscriber module such as a SIM-card which is currently inserted in it (Clarke 2008b).
In the case of human beings, distinguishing one entity from another can be achieved by means of biometrics. A biometric is a measure of some aspect of the physical person that is unique (or is claimed, or assumed, to be so). A further possible entifier for a human is what is usefully referred to as an 'imposed biometric' such as a brand, an RFID tag fastened to the person, or an implanted chip (Clarke 1994d, 1997, 2001a, 2002a).
Identification. Identification refers to the process whereby data is associated with a particular identity. This is achieved by acquiring an identifier for it, such as a person's name, or a cargo container's unique number. This application of the term is consistent with dictionary definitions, and has been used in this manner in my works since Clarke (1994b). The term has many other, loose usages, however, particularly as a synonym for 'identifier' (discussed above) or for 'token' (discussed below). It is incumbent on analysts and authors of formal works to avoid such ambiguities.
Entification. The association of data with a particular entity depends on the acquisition of an entifier such as a processor-id or a human biometric. This process is usefully described as entification. This term has been used consistently in my work since Clarke (2001d), but to date neither it nor any equivalent has become mainstream. The emergence of some such term is important, because there are material differences between identification and entification, firstly conceptually, secondly in terms of the data involved, and thirdly in relation to their impacts and implications.
Token. (Id)entification procedures need to be reliable and inexpensive. Achieving that aim can be facilitated by pre-recording an (id)entifier on a token from which it can be conveniently captured. One common form of token is a card, with the data stored in a physical form such as embossing, or on, or in, a recording-medium such as a magnetic stripe or a silicon chip.
Nym. Several categories of identifiers can be distinguished, depending on whether or not they can be associated with the underlying entifier. The term pseudonym refers to a circumstance in which the association between the identifier and the underlying entity is not known, but in principle at least could be known, e.g. if access could be gained to data that is normally protected (such as an index linking a client-code to the name and address of the AIDS-sufferer to whom the record relates). If an identifier cannot be linked to an entity at all, then it is appropriately described as an anonym. The term nym usefully encompasses both pseudonyms and anonyms.
The term 'pseudonym' is widely used, and has a large number of synonyms (including aka, 'also-known-as', alias, avatar, character, handle, nickname, nick, nom de guerre, nom de plume, manifestation, moniker, persona, personality, profile, pseudonym, pseudo-identifier, sobriquet and stage-name). In contrast, only a small number of authors have used the term 'nym', although it is readily traceable back prior to 1997. Even fewer have used the term 'anonym', but it is far from unknown and I have used it consistently in my work since Clarke (2002b). It is important to have a term such as 'anonym' available, because it is entirely feasible to conduct persistent communication with an identity whose underlying entity or entities is, and will remain, unknown. A celebrated example is the whistleblower who brought US President Nixon undone. 'Deep Throat' remained an anonym from 1974 until 2005. 'Publius', which was used for contributions to debates about the U.S. Constitution, has remained a nym since 1787.
Identity Silo. When data silos are destroyed, the correlation, matching, consolidation or merger of separate records is undertaken on the basis of one or more identifiers, such as name and date of birth, or commonly occurring identifying codes. The term 'identity silo' is usefully descriptive of a context in which an identity and its associated identifier(s) are used for a restricted purpose. The term 'identity silo' is my own coinage, in consistent use since Clarke (2006). It is a natural extension of the established data silo notion, but has not at this stage come into common usage. The term was unfortunately adopted by some other writers at about the same time, as a (misleading) way to refer to Google's endeavours to establish a Google-controlled single sign-on service.
A multi-purpose identifier is expressly intended to enable the conflation of identities. A common example is national registration numbers assigned to residents in many European countries, which are used within some cluster of related functions such as taxation, health insurance and self-funded pensions (known in some countries as superannuation or national insurance). A general-purpose identifier, such as the national identity number that is imposed on the residents of countries such as Denmark and Malaysia, is intended to enable the merger of all 'partials', deny the right to nymity, and thereby provide the State, or organisations more generally, with much greater power over people (Clarke 1994d, 2006).
Authentication. The term authentication refers to a process that establishes a level of confidence in an assertion. The term 'verification' is sometimes used as a synonym for authentication. It is much less appropriate because 'verity' = 'truth' and 'verify' = 'prove to be true', and hence 'verification' implies that a very high level of confidence is necessary, and is attainable. The term 'validation' is also sometimes used.
Authentication Strength. The degree of confidence achieved in the assertion is determined by the quality or strength of the authentication process. This depends on a range of factors including the nature, quality and number of authenticators (discussed below).
Assertion. There are many different categories of assertion that may be important in particular contexts. They include an assertion of fact, an assertion of data quality, an assertion relating to value, an attribute assertion (i.e. that a particular (id)entity has a particular attribute), a location assertion (i.e. that an entity is in a particular location), and an agency assertion (i.e. that an (id)entity has the capacity to represent, or act as an agent for, a principal).
A particular form of assertion that has been focussed upon by many analysts to the virtual exclusion of all others can be usefully referred to as an identity assertion. This is an assertion that an identifier is being appropriately used, or that the identity in question is who or what it purports or is inferred to be.
A further form of assertion is entity assertion. This is an assertion that an entifier is being appropriately used, or that the entity in question is who or what it purports or is inferred to be. Many analysts fail to distinguish entity assertion from identity assertion, and thereby create fundamental flaws in their designs.
Authenticator. Authentication is performed by cross-checking the assertion against one or more authenticators, or items of evidence. For example, an assertion of value may be checked by examining the characteristics of the banknote that is being offered, or by comparing a newly-executed written signature with one previously executed by the presenter of the cheque or card, or by checking the validity of a card-identifier (which identifies a card not a person) and a PIN (which tests whether the person presenting the card knows something that they should know and others should not know, generically referred to as a 'shared secret').
In the case of an attribute assertion, e.g. that a person qualifies for a trade discount at a retail outlet, an appropriate authenticator may be evidence of a trade qualification, or a company letterhead. Attributes such as age and pension-status may be attested to by a token issued by a relevant authority.
Credential. This is a general term for an authenticator that has physical or digital existence. In particular, a document or a token may contain evidence of value to the process of authentication. For example, a document may attest to an attribute, and a token with a chip may be able to provide evidence that a person is an appointed agent for a particular organisation.
Identity Authentication. For an identity assertion, the appropriate term to describe the process whereby a level of confidence is achieved in the assertion is identity authentication. Identity authentication is quite distinct from identification, which was described above as the process whereby data is associated with a particular identity, by acquiring an identifier for it.
It is common for the unqualified term 'authentication' to be used for what is referred to here as 'identity authentication'. This is highly inadvisable, because it leads organisations to overlook the many other relevant assertions that may be as important or more important to authenticate.
The alternative term identity verification (often just 'verification') is much-used in business and government discussions and even in the academic literature. Strong authentication of identity is very challenging and expensive for whoever is doing the authentication, and onerous on, and even demeaning of, the person on whom it is imposed. The term 'identity authentication' avoids the implication of very high accuracy and is hence much to be preferred.
Evidence of Identity (EOI). The authenticators used in the context of identity authentication are commonly referred to as evidence of identity (EOI). All other things being equal, two-factor authentication is regarded as being stronger than single-factor authentication, and three-factor as stronger again, provided that the factors are independent from one another.
An alternative term that is in common use is proof of identity (POI). The term is misleading, because, like 'verification', it implies a level of reliability that is generally unattainable. In addition to being unrealistic, the idea is inconsistent with a risk-managed approach to the conduct of business.
In the case of human identities, several forms of EOI are used. They include 'what the person knows' (such as a password or PIN) and 'what the person has' (such as documents and tokens).
Entity Authentication. Entity authentication is the process of achieving a level of confidence in an entity assertion.
In the case of a cargo container, the process of entification involves collection of the container's serial-number. The process of entity authentication involves the collection of additional data (such as the container-type code, and its length, height and other size characteristics) followed by computation of the check-digit and comparison against data held in records in order to detect any material inconsistencies.
To conduct entity authentication for an active device such as a computer or mobile phone, a test needs to be conducted of the claim that the device is properly distinguished by means of a relevant entifier (such as the processor-id or mobile-phone-id). For example, if an entifier presents at the same time in two local networks or cells, or in a new cell very shortly after being in a cell a considerable distance from the previous cell, it would appear that at least one of the devices is conducting masquerade.
To conduct entity authentication for a human, it is necessary to collect a measure of 'what the person does' (such as the act of providing a written signature or the micro-actions involved in the keying of a password), 'what the person is' (a biometric), or 'what the person is now' (i.e. an imposed biometric), and then compare the measure against some previously collected and stored measure of the same thing. All such mechanisms involve significant challenges in terms of quality and security.
It is common among analysts to discuss 'what the person does' and 'what the person is' as though they were forms of identity authenticator rather than entity authenticator. This is not only erroneous, but also harmful. It was noted above that authentication of human identities is challenging, expensive, onerous and even demeaning. Authentication of human entities is substantially more so. It is undermined by a whole litany of difficulties in achieving adequate measurement and comparison quality. It suffers serious security vulnerabilities. And it is highly personally intrusive and degrading (Clarke 2002a).
(Id)entity Credential. A token was referred to above as a facility that supports the identification process by providing a convenient means for capturing an identifier. In addition, or instead, a token may assist in the authentication process. For example, it may carry a copy of a secret (or, better, a hash of the secret), or a set of one-time passwords, or a digital signing key and the ability to generate a digital signature, or a biometric (or, much less dangerously, a hash of a biometric).
Authorisation. An (id)entity, once it has been (id)entified - i.e. an (id)entifier has been collected - and after (id)entity authentication has been performed, may be permitted to perform particular acts. The process whereby it is determined what a particular Entity or Identity is permitted to do is referred to as authorisation.
A permission or privilege is a capability that an (id)entity is permitted to perform. In a physical context, the capability may be access to particular premises, or to particular parts of premises. In a virtual context, an identity is provided with access to system resources, and in particular authorised to run particular software, use particular functions performed by that software, access particular data collections and/or access particular data within those data collections.
Permissions may be associated with entities, or with identities. Association with entities is fraught with difficulties because entity authentication is confronted by many quality problems, it is highly intrusive and it is insecure. In any case, a person's access to computer applications and databases commonly depends on the identity or role that they are performing. For example, an employee will generally not be authorised to approve his or her workmates' sick leave forms but may be in the event that their usual manager is absent and the person is 'acting up' as his or her workmates' supervisor; and a person has different authorisations when they are acting as a selection committee member, or as a fire warden.
The relationship between authentication and authorisation is the subject of considerable confusion in the literature and in practice. A process description is therefore included within the model presented in this paper. A process model that encompassed physical as well as virtual contexts would have to be highly abstract and of limited value as a communication and analytical tool. The depiction in Figure 2 is accordingly limited to virtual contexts, i.e. the enabling of users to gain access to system resources.
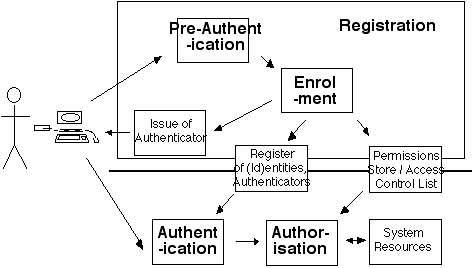
Figure 2 depicts the user operating from a desktop computer. It also serves quite satisfactorily if the device is instead a portable, handheld or mobile phone. In current and emerging contexts, however, several other variants need to be taken into account. In particular:
The lower part of Figure 2 shows the process flow from Authentication on to Authorisation, which occurs on each occasion that a user seeks access to services. Those concepts have already been introdcued. The upper part of the Figure, on the other hand, introduces further concepts. It distinguishes the establishment-phase Registration activities, comprising Pre-Authentication and Enrolment.
User. This term refers to an entity that seeks access to system resources. The scope may be limited to humans, or may extend to organisations and/or devices.
Loginid, Userid or Username. These terms are commonly used for the identifier that distinguishes a particular user from other users and non-users. The identifier may be weakly or strongly associated with a real-world identity; and the identity may be weakly or strongly associated with one or more real-world entities behind the identity. Alternatively, the identifier may be a nym, because the link back to the entity has not been established.
A loginid is commonly associated with an account (discussed immediately below). If so, and if the identifier is a nym, then it is a persistent nym that can be utilised for as long as the service-provider makes system resources available to it, and hence may come to be a more or less trusted identity even if the entity or entities behind it remain unknown.
Account. This term refers to the facilities that a loginid or username provides access to. From the service-provider's perspective, an account comprises one or more linked records containing a set of data-items, which together define and describe a real-world identity recognised by the service-provider and provided with specified services. From the model as a whole, it is clear that a person, an organisation or a device may have multiple accounts with any one organisation, to reflect the various identities that they adopt; and that an account may be used by any entity that can satisfy the authentication tests.
Access Control. A primary purpose of establishing accounts and performing authentication and authorisation activities is the protection of system resources against unauthorised access, use and abuse. From the perspective of the service-provider, the term 'access control' is usefully descriptive of the complete set of processes depicted in Figure 2.
Registration. This usefully refers to the comprehensive process, of the nature of a 'rite of passage', whereby future acts of (id)entity authentication are facilitated.
Pre-Authentication. This is a convenient term to describe that part of the Registration process whereby the assertion is tested that the (id)entity is an appropriate one to have an identifier, identity authenticator(s) and authorisations created for it or assigned to it. Examples of techniques used to achieve relatively strong authentication include the presentation of documents (in some countries referred to as 'the 100-point check'), cross-checking of data supplied by the applicant with entries in databases, call-back to nominated contact-points, and contact with the entity through other channels such as phone-books or previously-recorded email-addresses. Another approach to pre-authentication is reputation-based, with known identities attesting to the appropriateness of the applicant to be provided with an account. A further possibility is evaluation of the applicant's performance or behaviour (e.g. what the user has done in other fora or while using a trial account, or what the user knows).
There are many circumstances in which strong authentication is unnecessary, impractical, too expensive, or unacceptable to the entities involved. For example, the creation of accounts at Passport/Hotmail, Yahoo and Google involves little or no authentication. The identity is just 'an identity', and any reliance that any remote computer, person or organisation places on it depends on subsequent authentication activities. One reason for this is that unauthenticated identities are entirely adequate for a great many purposes, and they are inexpensive and quick for both parties. In addition, nymity is positively beneficial in some circumstances, such as obligation-free advice, online counselling and whistle-blowing.
A further alternative is to pre-authenticate not the entity, but rather an attribute of the entity. In this case, assurance may be achieved that the account is associated with an (unknown) entity that has a particular characteristic, such as being a registered medical practitioner, or a qualified online counsellor. For this to be achieved, the applicant needs to provide a credential that the service-provider trusts. For example, a medical registration board can provide a digitally-signed message, which omits the applicant's identifier, but is cryptographically assured to refer to the applicant.
An important category of attribute is agency. Pre-authentication of an agent's authority is very important in a range of circumstances, such as the capacity and limitations of an individual to act on behalf of an organisation, e.g. to access data, to provide data, and to bind the organisation in contract. To date, however, authentication processes for agency relationships are extremely poorly developed.
Enrolment. This refers to that part of the Registration process which establishes the means for effective and efficient authentication on each subsequent occasion that the user seeks access. It comprises the creation or adoption of an authenticator (or perhaps more than one), possibly issue of the authenticator to the user, recording of means of checking the authenticator (which may be a copy of the authenticator, or some more secure alternative such as a 'one-way hashed' copy of the authenticator), and recording of the capabilities that the user is to be provided with.
Single Sign-On. The number of service-providers has exploded during the last 20 years, and the number of service-providers that any one person may have accounts with is large. This brings with it many practical problems. Some arise from lost and forgotten authenticators, and other from lost and forgotten accounts. Security issues arise, because people record their many authenticators in ways that become accessible to other people, they prefer a small number of easily-remembered passwords to a unique and strong password for each account, and they resist the requirement to frequently change their passwords. The term 'single sign-on' refers to the notion of each using having a single master-account that enables access to all accounts with all service-providers, or all service-providers within some domain such such as that provided by their employer. In addition to being challenging to implement, the notion creates additional security problems. As a consequence of all these difficulties, single sign-on is a theoretical construct rather than a tenable design.
Simplified Sign-On. This refers to a less ambitious and less insecure approach than single sign-on, whereby a master-account provides access to a number of accounts rather than to all accounts within a domain.
Identity Management. A generic term for architectures, infrastructure and processes that support the authentication of assertions relating to identity. Standards and services has been the subject of a great deal of competitive activity since the late 1990s. Most products and most standard-sets are seriously deficient when evaluated against the model described in this paper (Clarke 2004c).
The model presented in this section has encompassed a set of related concepts, has carefully distinguished them, has segregated real-world from information-systems concepts, and has described the relationships among them. The following section tests the model's efficacy by applying it in a range of contexts.
The model presented in the previous section is asserted to be sufficiently comprehensive and rich to enable effective representation of (id)entity, (id)entity authentication and authorisation processes relating to a wide range of (id)entities that exist in real-world contexts. This section applies the model to a range of entity-categories, in order to provide a test of that assertion.
The range of entities includes the vitally important category of humans, but extends well beyond them. The following sub-sections consider in turn goods, packaging, devices, software, animals, organisations and finally humans. This represents a substantial proportion of the categories of entity that are relevant to information systems in business, government and community organisations, but is of course not a complete set. The consideration of each entity-category is necessarily superficial because of space-constraints. Examples are presented in such a way as to exercise a substantial sub-set of the wide array of concepts and relationships in the model.
By 'goods' is meant here physical items that are produced, traded between parties, delivered from one location to another, and transformed or consumed. Two different senses of the word 'goods' need to be distinguished: a specific item, and a category of identical or near-identical items. For example, a particular motorised vehicle (car, fork-lift truck, diesel engine, NASA rocket) is an item, but also an instance of a category. The expressions used in this sub-section are 'item' and 'product' respectively.
In applying the model, an item is an entity, and so is a product an entity. An appropriate entifier for a product may be a product code such as the UPC for supermarket products, which uniquely defines that product and distinguishes it from other, similar products. For an item, an appropriate entifier may be a serial number, or a serial number within a batch number, perhaps even within a date (if the batch numbers are not unique). Both product-numbers and item serial-numbers are important for such purposes as maintenance, warranty and product recall.
Some items and products may be used for multiple purposes, and hence may need to be treated as having multiple identities. One example is an item that is out-of-warranty, or has been traded on from its original owner. Another is an item that has been co-opted for a purpose different from its original purpose, e.g. a motor designed for static use on land being installed on a vessel in a salt-water environment, a fire extinguisher used on a fire of the wrong type (which could be reasonably expected to void any applicable warranty, and raise liability issues), and a 'spare part', which may have different characteristics depending on what it is substituted into (and which may cause its host to have different characteristics).
Entification processes commonly involve the capture of the product-number (for a product) or serial-number (for an item). Authentication processes commonly involve checking the product-number or serial-number against previously stored information. Nymity is seldom a quality of any great consequence; but it exists at item-level, if the items are not readily distinguished by any identifier. At the extreme, commodities such as a grade of iron ore or coffee are undifferentiated and anonymous. Authorisation is often irrelevant to products or items, bu exceptions occur, such as regulations about the permitted locations of explosives, hazardous chemicals, fissile materials and biologically active materials.
By 'packaging' is meant here materials used to protect goods during transit. It includes boxes, crates and cargo containers, pallets, and insulation against such threats as impact, heat and cold.
Most packaging is insufficiently important to warrant the investment involved in (id)entification. There are exceptions, however. For example, packaging that carries the risk of contamination by chemicals or nuclear material is subject to regulatory controls, and requires identification and management throughout its life and journeys.
Another special case is cargo containers, which are expensive, and intended for multiple, successive uses. They are carefully (id)entified, the (id)entifiers are subject to authentication (e.g. through double-recording of the (id)entifier and the code that indicates the container-type, and checking against available databases), and they are tracked through physical space. They may also have different identities, as occurs when a 'refrigerated container' (reefer) is empty, or is used for goods that do not need cooling. In those circumstances, many of the conditions applicable to them in their primary mode of use do not apply during that period. As is the case with goods, nymity and authorisation are seldom important, but may arise.
In the case of animals, the correlates to 'item' and 'product' in the previous sub-sections are the individual beast, and the species and any race or breed to which it belongs. Entifiers for a species or breed may be names or possibly a DNA profiles. Entifiers that can be used for individual animals include biometrics and imposed biometrics such as a embedded chip - typically in the neck for domestic animals and in an ear-tag for stock such as cattle.
Animals may have different identities at times. For example, in a slaughter-line, the animal may be identified by a sequence-number that is then associated with its body-parts through the meat-inspection stages; and a guide-dog generally has that identity only when accompanying a blind person.
For breeding-stock, both for domestic and commercial animals, relevant attributes include the animal's blood-lines, and hence the design of the records associated with the animal's identifier(s) may be highly specialised.
(Id)entification of an animal comprises collection of the relevant (id)entifier. (Id)entity authentication may comprise a check of key attributes recorded against the (id)entifier, such as dog-breed or coat-colour. Authorisation may be relevant in the case of animals that have particular capabilities, such as blind people's guide dogs and Customs 'sniffer' dogs, which need access to locations in which animals are normally not permitted.
By a 'device' is meant here an artefact that has the characteristic of being able to perform computations and in some manner act on its environment, perhaps in a physical manner (e.g. an automated teller machine or a computer-controlled sluice-gate or heating-device) or by displaying or transmitting data to another device (e.g. a desktop, portable or handheld computer, or a mobile phone).
Each such entity has particular attributes. Each typically has an entifier for the product (e.g. manufacturer's name and model-number) and for the item (e.g. a device serial-number). In addition, many such devices have, or have the potential for, multiple identities, each with its own identifiers. For example, mobile phones have an IMEI or similar as an entifier and an IMSI or similar as the identifiers for each of the separate SIM-cards that they may contain. Some mobile phones only contain one slot for a SIM-card and hence their identities are adopted serially, by switching SIM-cards; whereas other mobile phones contain slots for two or more SIM-cards and hence may have two or more identities simultaneously.
(Id)entification typically comprises collection of the IMEI and/or IMSI or its equivalent. Some of the other attributes of a device may, however, be used as a less reliable and possibly temporary (id)entifier under a variety of circumstances. In particular, the serial-number of a component may be used (e.g. the NICId of its network interface card), and so can the device's network address at a particular time, such its IP-address. Alternatively, its location in physical space may be a sufficient (id)entifier, e.g. for a payment-card on a tollway.
(Id)entity authentication may comprise a check of the (id)entifier and perhaps some key attributes against data stored about the (id)entity in one or more registers, and/or against locations in which it was recently detected (to detect likely data collection errors). Alternatively, much stronger forms of authentication are possible, such as digital signatures by means of private signing keys securely embedded in a chip in the device and/or SIM-card at the time of manufacture.
Where needed, nymity may be programmed by means of the device exercising control over the device-identifier that is transmitted. Nymity may be challenging to achieve with respect to the local network infrastructure, but it is much more readily implemented with respect to distant devices, in particular through the use of proxy-servers.
Conventional computing hardware designed to be used variously as hosts, workstations, portables and handhelds is intended to support a wide range of loadable systems and applications software, serially and concurrently. In addition, mobile-phones need not be restricted to phone-calls and text-messaging and may be fully programmable devices capable of performing whatever functions are provided by loadable software. This may be client software (to support the device's user), server software (to support remote users) or intermediary software (to support other network users). Intermediary functions are moving far beyond routers, proxy-servers and network-caches, as peer-to-peer (P2P) architectures proliferate.
Software needs to be distinguished at two levels, in much the same manner as products and items were in an earlier sub-section. The entifier for the category of software is typically a product-name and version-number. For an instance of software, one candidate entifier is the file-name or path-name in which it is stored. A dynamic rather than static candidate entifier is the process-id allocated by the device's operating system. A possible proxy entifier is the port-number or the socket-id (IP-address plus port-number), which are the addresses (as distinct from names) used by the local systems software and the network respectively.
The concepts of identity and identifier are also applicable to software. Re-entrant or multi-threaded code, whether running in interleaved fashion on a single processor or concurrently on multi-processor configurations, enables a single instance of software running in a machine to support multiple users as though there were multiple instances of the program running. It expressly has multiple identities at once. Another example is a web-server (using that term in its correct sense as software, not hardware). A single web-server may manage many web-sites with different domain-names and even IP-addresses, and respond to requests from browsers sent to its many different identities and addresses.
Entity authentication may be important. For example, web-servers customise the HTML streams that they send to web-browsers, depending on which product each declares itself to be. Identity authentication may be important, for example where cross-pollution among identities such as threads gives rise to unacceptable security or quality risks, and as software agents become more common.
On the other hand, risk assessment may lead to the conclusion that it is the identity of the device in which the software is running that needs to be authenticated, or even more so the organisation or person on whose behalf the device purports to be performing its functions. This is at the heart of the challenge to overcome 'phishing' attacks. In some circumstances, the authentication process may need to take into account the combination of person, device-type, device, software product and version, process, network location and even apparent physical location.
Anonymity and pseudonymity are readily available, e.g. through self-manipulation of (id)entifiers, and through proxy-servers. These capabilities have been increasingly applied in recent years, and their use is, for various reasons in various contexts, likely to continue and increase.
An organisation is an entity whose existence arises through acknowledgement by humans. Organisations are non-corporeal, i.e. they have no physical existence or form, and are (for all their importance and scale in the modern world), like cyberspace, 'shared hallucinations'. Acts may be performed under law (such as incorporation) and entries may be placed in registers, but these are adjuncts to and evidence of the shared hallucination that the organisation exists, and do not make the mirage any more physically real.
Organisations commonly have names, although the names may be designed to obfuscate rather than inform, and may change frequently, particularly where the individuals concerned are actively trying to avoid detection (e.g. 'organised crime', and underground political opposition). Private sector corporations generally also have registration numbers, and in many jurisdictions so do unincorporated business enterprises. Registration codes are less common in the cases of government agencies, incorporated associations (even those with primarily economic functions) and unincorporated associations (many of which have primarily social or community functions).
Each organisation is an entity, and may have multiple identities and associated identifiers, such as business divisions, 'business names', brands and logos.
(Id)entification comprises the collection of an (id)entifier. (Id)entity authentication comprises measures taken to establish that the organisation or a component of it is what it purports to be. This is seriously challenging, because of the organisation's incorporeal nature. Common techniques used to achieve some degree of confidence include searches in multiple informal registers such as phone-books and industry directories, physical visits to advertised corporate 'footprints', and phone-calls to apparent places of business.
All actions taken by an organisation are, of necessity, taken by humans, and perhaps devices or software processes, that purport to be agents for and acting on behalf of the organisation. Authentication of an action by a corporation (such as entering into contract) therefore involves not only (id)entity authentication but also attribute authentication, in order to achieve confidence in the legal capacity of the particular human(s) and/or device(s) to perform that action and thereby bind that organisation.
Humans represent the most complex and challenging category of entity to which organisations seek to apply (id)entification and (id)entity authentication.
A human entity has entifiers in the form of biometrics. Each human entity has many identities, arising within the many contexts within which the person acts, including workplaces, home(s), and social and community settings. Those identities have associated with them various identifiers.
Some identifiers are variants of a commonly-used name (e.g. a surname with different given names, initials and nicknames). Others are successive names (e.g. changed as a result of adoption, marriage, separation or divorce, ambiguity, personal taste or physical danger). Others are alternate names. For example, a woman's maiden name may not be used socially after marriage, but may continue to be used in professional contexts. Another source is multiple transliterations of diacritics (such as diphthongs, including umlauts) and between incompatible alphabets and from logographic languages such as Chinese into an alphabet.
Many additional situations arise in which multiple distinct names may be used concurrently by the same human entity, in some cases for positive reasons (such as a nom de plume for an author, for physical safety because the individual has a hazardous occupation, and for other categories of persons-at-risk - Clarke 1999b), and in others for negative purposes (such as criminal aliases/akas). In addition to names, many organisations assign codes as identifiers (such as employee numbers and customer numbers) (Clarke 1994d).
(Id)entification comprises the collection of an (id)entifier. (Id)entity authentication comprises measures to establish a degree of confidence that the (id)entity is accurate and is being appropriately used. This may involve demonstration that the individual is capable of the performance of an act (e.g. the production of a signature or enunciation of spoken language) or the divulging of a 'shared secret' that only the relevant individual is expected to be a able to perform or know (such as a password, the appropriate answer to a previously-agreed test-question, or some aspect of the most recent transaction conducted with the organisation).
In some circumstances, it may be more convenient to collect and authenticate proxies for human (id)entities rather than human (id)entifiers themselves. One possibility is the registration plates of a person's commonly-used vehicle. Similarly, a person's commonly-used handsets enable identification of them, and location and tracking of their movements (Clarke 1999b). Authentication may be feasible based on the usage style, or the content of intercepted voice or text messages. In static situations, the IP-address used by the device may be an effective a proxy not only for the device and software, but also for the individual.
Many different authenticators are used, but their use gives rise to considerable security risks. For example, sets of personal (id)entification and authentication data represent highly attractive opportunities for (id)entity fraud and even theft. This needs to be seen in the light of the vasts volume of evidence that organisations throughout the public and private sectors and throughout the world are incapable of exercising adequate control over inappropriate uses and disclosures of data.
Some forms of biometric measure (primarily DNA and iris-scans) may be capable of being sufficiently reliably matched against a single record in a large database, in which case they are, in principle at least, capable of supporting human entification and entity authentication in a single action. For most biometrics, however, the collection process results in highly variable measures, and the measures from different people overlap. As a result, most forms of biometrics are capable of being used only as a human authenticator, and not as a human entifier.
The capture of most forms of biometric is in principle intrusive into the individual's physical person, and hence into their personal / psychological space; and some forms of collection are significantly intrusive. The ability to require the act to be performed signifies power by the organisation over the individual, and has a substantial chilling effect.
In addition, the acquisition of biometric measures of all kinds is fraught with quality and security risks, and their capture into recorded form generates even more security and privacy issues, because it gives rise to a 'honey-pot' of valuable data. The data is attractive to organisations and individuals seeking to exercise control over individuals, groups and societies, including not only national security and law enforcement agencies but also service agencies and corporations. It is also attractive to organisations and individuals intending criminal acts such as fraud. Beyond that, the scope for planting biometric evidence creates opportunities for extortion, and for deflection of the target's energies through unjustified investigations and court-cases, and in extreme cases for the miscarriage of justice.
The authentication of human entities gives rise to major issues for people at philosophical, political, social and psychological levels. It also leads to substantial risks for organisations. Because of these factors, biometric schemes demand a great deal more care in the analysis of requirements for entification and authentication, in the preparation of business cases, in the conduct of risk assessments, and in the design of systems, than has been evident during the last two decades.
A great deal of human behaviour has in the past gone unrecorded, and a great deal of what was recorded was anonymous, or was pseudonymous but with inbuilt protections against the breaking of the pseudonymity. The undisciplined and largely unregulated application of information technologies during the last 50 years has seen the recording of transaction data rise dramatically, and the collection and association of (id)entifiers with that data increase enormously as well.
Many individuals, in many different circumstances, have strong interests in the avoidance of data-recording and especially in the association of (id)entifiers with that data. Government agencies and corporations have ridden rough-shod over those strong human interests. Security and privacy concerns have continually arisen, and there has been increasing incidence of public resistance to and rejection of features of information systems and even of entire systems.
There are a great many circumstances in which the cost and intrusiveness of (id)entification and (id)entity authentication are unwarranted, and instead risk management can and should be achieved through the authentication of assertions relating to aspects other than (id)entity, such as value and attributes, including the individual's capacity to act as an agent for another individual or for an organisation.
The actions that an individual human is permitted in particular contexts is determined through the authorisation decisions taken on the basis of authentication, whether of (id)entity of of some other aspect. Where an individual is unable to achieve authentication, the consequences vary. For example, people with memory deficiencies have difficulty using ATMs and debit-cards and increasingly now credit-cards, because they cannot readily recall their PIN. Employees who cannot reliably produce a biometric (and 2-5% of the population share this characteristic in relation to fingerprints) may be continually calling for assistance from their employer's technical support team in order to be able to log into the systems they need access to in order to perform their functions.
Beyond those functional problems lie much more serious potentials. One is intentional service denial (such as the preclusion of use of scheduled airline services, public transport and toll-roads). The sci-fi genre many years ago envisaged a highly-networked world in which the scope exists for public-private partnerships to extend the service-denial concept to outright identity denial.
This paper presented a contribution to theory, in the form of a model of (id)entity, authentication and authorisation. The model defines the following concepts and the relationships among them:
The model was asserted to be sufficiently comprehensive and rich to enable effective representation of real-world phenomena and designs for systems intended to perform (id)entification, authentication and authorisation functions. The series of test-applications demonstrated that the model is effective in reflecting the realities of multiple categories of entity, which together have a wide array of different attributes and attribute-values, and exist and are used in widely varying contexts. On this basis, it is argued that the model satisfies the requirements of comprehensiveness and sufficiency.
Further, it is asserted that systems designed on the basis of this model will avoid a wide range of deficiencies that have afflicted and continue to afflict practice in this area.
Clarke R. (1987) ''Just Another Piece of Plastic for Your Wallet': The Australia Card' Prometheus 5,1 (June 1987), at http://www.rogerclarke.com/DV/OzCard.html
Clarke R. (1988) 'Information Technology and Dataveillance' Commun. ACM 31,5 (May 1988) 498-512, at http://www.rogerclarke.com/DV/CACM88.html
Clarke R. (1992) 'The Resistible Rise of the Australian National Personal Data System' Software L. J. 5,1 (January 1992), at http://www.rogerclarke.com/DV/SLJ.html
Clarke R. (1993) 'Computer Matching and Digital Identity' Presentation at Computers, Freedom & Privacy (CFP'93) in San Francisco, Xamax Consultancy Pty Ltd, February 1993, at http://www.rogerclarke.com/DV/CFP93.html
Clarke R. (1994a) 'The Digital Persona and its Application to Data Surveillance' The Information Society 10,2 (June 1994), at http://www.rogerclarke.com/DV/DigPersona.html
Clarke R. (1994b) 'Dataveillance: Delivering '1984' Chapter 4 in Green L. & Guinery R. (Eds.) 'Framing Technology: Society, Choice and Change' Allen & Unwin, Sydney, 1994, at http://www.rogerclarke.com/DV/PaperPopular.html
Clarke R. (1994c) 'Dataveillance by Governments: The Technique of Computer Matching' Information Technology & People 7,2 (June 1994) 46-84, at http://www.rogerclarke.com/DV/MatchIntro.html
Clarke R. (1994d) 'Human Identification in Information Systems: Management Challenges and Public Policy Issues' Info. Technology & People 7,4 (December 1994), at http://www.rogerclarke.com/DV/HumanID.html
Clarke R. (1997) 'Chip-Based ID: Promise and Peril' Proc. Int'l Conf. on Privacy, Montreal September 1997, at http://www.rogerclarke.com/DV/IDCards97.html
Clarke R. (1999a) 'Anonymous, Pseudonymous and Identified Transactions: The Spectrum of Choice', Proc. IFIP User Identification & Privacy Protection Conference, Stockholm, June 1999, at http://www.rogerclarke.com/DV/UIPP99.html
Clarke R. (1999b) 'Person-Location and Person-Tracking: Technologies, Risks and Policy Implications' Proc. 21st International Conf. Privacy and Personal Data Protection, Hong Kong, September 1999. Revised version published in Info. Techno. & People 14, 1 (2001) 206-231, at http://www.rogerclarke.com/DV/PLT.html
Clarke R. (2001a) 'Biometrics and Privacy' Xamax Consultancy Pty Ltd, April 2001, at http://www.rogerclarke.com/DV/Biometrics.html
Clarke R. (2001b) 'The Fundamental Inadequacies of Conventional Public Key Infrastructure' Proc. Conf. ECIS'2001, Bled, Slovenia, 27-29 June 2001, at http://www.rogerclarke.com/II/ECIS2001.html
Clarke R. (2001c) 'Certainty of Identity: A Fundamental Misconception, and a Fundamental Threat to Security' Privacy Law & Policy Reporter 8, 3 (September 2001) 63-65, 68, at http://www.rogerclarke.com/DV/IdCertainty.html
Clarke R. (2001d) 'Authentication: A Sufficiently Rich Model to Enable e-Business' Xamax Consultancy Pty Ltd, December 2001, at http://www.rogerclarke.com/EC/AuthModel.html
Clarke R. (2002a) 'Biometrics' Inadequacies and Threats, and the Need for Regulation' Xamax Consultancy Pty Ltd, April 2002, at http://www.rogerclarke.com/DV/BiomThreats.html
Clarke R. (2002b) 'The Mythology of Consumer Identity Authentication', Statement for a Panel Session on 'Understanding e-Business: Can we remain anonymous in the marketplace?' Proc. 24th Int'l Conf. of Data Protection & Privacy Commissioners, Cardiff UK, 9-11 September 2002, at http://www.rogerclarke.com/DV/AnonDPPC02.html
Clarke R. (2003a) 'Authentication Re-visited: How Public Key Infrastructure Could Yet Prosper' Proc. 16th Int'l eCommerce Conf., at Bled, Slovenia, 9-11 June 2003, at http://www.rogerclarke.com/EC/Bled03.html
Clarke R. (2003b) 'eAuthentication Realities: You want to authenticate what???' Presentation in 11 cities across Australia, July-October 2003, for the Australian Computer Society Professional Development Board, Xamax Consultancy Pty Ltd, August 2003, at http://www.rogerclarke.com/EC/ACSeAuth.html
Clarke R. (2004a) 'Identification and Authentication Glossary' Xamax Consultancy Pty Ltd, extract from pp. 57-65 of 'Identity Management: The Technologies, Their Business Value, Their Problems, and Their Prospects' Xamax Consultancy Pty Ltd, March 2004, at http://www.rogerclarke.com/EC/IdAuthGloss.html
Clarke R. (2004b) 'Identification and Authentication Fundamentals' Xamax Consultancy Pty Ltd, May 2004, at http://www.rogerclarke.com/DV/IdAuthFundas.html
Clarke R. (2004c) 'Identity Management: The Technologies, Their Business Value, Their Problems, Their Prospects' Xamax Consultancy Pty Ltd, March 2004, at http://www.xamax.com.au/EC/IdMngt.html
Clarke R. (2005) 'Human-Artefact Hybridisation: Forms and Consequences' Proc. Ars Electronica 2005 Symposium on Hybrid - Living in Paradox, Linz, Austria, 2-3 September 2005, at http://www.rogerclarke.com/SOS/HAH0505.html
Clarke R. (2006) 'National Identity Schemes - The Elements' Xamax Consultancy Pty Ltd, February 2006, at http://www.rogerclarke.com/DV/NatIDSchemeElms.html
Clarke R. (2008a) '(Id)Entities (Mis)Management The Mythologies underlying the Business Failures' Xamax Consultancy Pty Ltd, Prepared for an Invited Keynote at 'Managing Identity in New Zealand', Wellington NZ, 29-30 April 2008, at http://www.rogerclarke.com/EC/IdMngt-0804.html
Clarke R. (2008b) 'You Are Where You've Been Location Technologies' Deep Privacy Impact' Invited Keynote at a Seminar on 'Location Privacy' at the University of N.S.W. on 23 July 2008, Xamax Consultancy Pty Ltd, at http://www.rogerclarke.com/DV/YAWYB-CWP.html
Clarke R. & Wigan M. (2008) 'You Are Where You've Been Location Technologies' Deep Privacy Impact' Proc. Third Workshop on Social Implications of National Security, Canberra, 23-24 July 2008, in Michael K. & Michael M.G. (2008) 'Australia and the New Technologies: Evidence Based Policy in Public Administration' Research Network Secure Australia, July 2008, pp. 100-114, at http://www.rogerclarke.com/DV/YAWYB-CW.html
The successive versions of this model since the early 1990s have benefited greatly from many interactions with my colleagues at ETC, now Convergence eBusiness Solutions Pty Ltd - particularly David Jonas, Ian Christofis, Ross Oakley and Kevin Jeffery. Valuable feedback was also provided by many clients for whom aspects of the model were presented in workshops and reports, and by participants in the many seminars at which the definitions and related models and analyses have been presented. Comments on advanced drafts by reviewers, David Vaile and Jill Matthews were valuable in clarifying the presentation. Responsibility of course lies with the author alone.
Roger Clarke is Principal of Xamax Consultancy Pty Ltd, Canberra. He is also a Visiting Professor in the Cyberspace Law & Policy Centre at the University of N.S.W., a Visiting Professor in the E-Commerce Programme at the University of Hong Kong, and a Visiting Professor in the Department of Computer Science at the Australian National University.
| Personalia |
Photographs Presentations Videos |
Access Statistics |
 |
The content and infrastructure for these community service pages are provided by Roger Clarke through his consultancy company, Xamax. From the site's beginnings in August 1994 until February 2009, the infrastructure was provided by the Australian National University. During that time, the site accumulated close to 30 million hits. It passed 65 million in early 2021. Sponsored by the Gallery, Bunhybee Grasslands, the extended Clarke Family, Knights of the Spatchcock and their drummer |
Xamax Consultancy Pty Ltd ACN: 002 360 456 78 Sidaway St, Chapman ACT 2611 AUSTRALIA Tel: +61 2 6288 6916 |
Created: 30 March 2008 - Last Amended: 16 May 2009 by Roger Clarke - Site Last Verified: 15 February 2009
This document is at www.rogerclarke.com/ID/IdModel-090605.html
Mail to Webmaster - © Xamax Consultancy Pty Ltd, 1995-2022 - Privacy Policy