Roger Clarke's Web-Site
© Xamax Consultancy Pty Ltd, 1995-2024

Infrastructure
& Privacy
Matilda
Roger Clarke's Web-Site© Xamax Consultancy Pty Ltd, 1995-2024 |

|
|||||
| HOME | eBusiness |
Information Infrastructure |
Dataveillance & Privacy |
Identity Matters | Other Topics | |
| What's New |
Waltzing Matilda | Advanced Site-Search | ||||
Version of 31 January 2010
Accepted for 2nd International Symposium on Cloud Computing, Melbourne, May 2010
Published in Parashar M. & Buyya R. (2010) Proc. 10th IEEE/ACM International Conference on Cluster, Cloud and Grid Computing, Melbourne, Australia, 17-20 May 2010, pp. 625-630
© Xamax Consultancy Pty Ltd, 2009-10
Available under an AEShareNet ![]() licence or a Creative
Commons
licence or a Creative
Commons  licence.
licence.
This document is at http://www.rogerclarke.com/II/CCSA.html
The accompanying slide-set is at http://www.rogerclarke.com/II/CCSA.ppt
To date, the literature on software architecture for cloud computing is focussed largely on the service-provider, and fails to reflect the fact that cloud computing is a form of client-server relationship. Architectures must also encompass both the software and devices that users utilise in order to invoke functions in the cloud, and intermediary functions. A further problem with analyses to date is inadequate reflection of the risks that users are subject to when they use cloud services. This paper proposes a comprehensive model that reflects user needs, and identifies implications of the model for computer scientists working in the area.
The phenomenon of cloud computing has been driven largely from the supply side. Computer scientists have created technological possibilities and have proposed solutions to categories of problems, and corporations have offered services incorporating those ideas. Analyses of cloud computing have generally been undertaken from the perspective of service-providers (e.g. Armbrust et al. 2009).
There is an urgent need for the optimism of the first three years of the movement's existence to be tempered by realism about the needs of potential users of cloud computing and the constraints within which they work. This paper investigates multiple aspects of the user perspective of cloud computing, in order to provide a counter-balance against the technocentric view and to temper enthusiasm about the breadth of its applicability.
Many interpretations of the concept of cloud computing have been put forward (Vaquero et al. 2009). This paper adopts the following broad working definition.
Cloud computing refers to a service that satisfies all of the following conditions:
The paper commences by considering the scope of cloud computing architectures, and proposes a comprehensive framework. It then presents a brisk risk analysis from the viewpoint of users. This gives rise to the definition of three kinds of use-profile, for which cloud computing respectively is not, may be, and is, a potential solution. Building on these ideas, a brief statement of user requirements is presented. Together, these representations of the user perspective give rise to significant implications for designers of cloud computing architectures and components.
Architecture diagrams have to date focussed primarily on the server-side of the cloud. For example, Youssef et al. (2008) proposed what they referred to as an 'ontology', comprising layers for infrastructure, for the software environment or platform, and for applications. Other architectural depictions are in Anderson (2008) and CSA (2009).
A first step in developing a user-driven conception of cloud computing is to assert a comprehensive framework that encompasses not only server-side, but also client-side and intermediary infrastructure. Exhibit 1 provides an overview of such a framework.
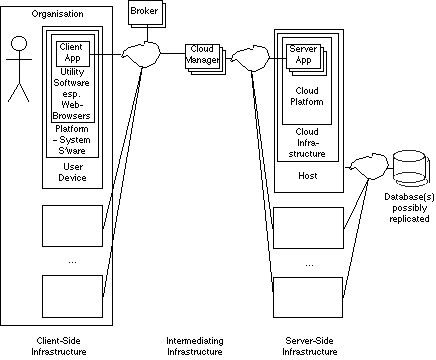
According to this conception, a user utilises one or more user devices, and may do so within the context of an organisation. The software in each device comprises a client application (which may be substantial, or merely, say, a few lines of Javascript), which may run within utility software. The presumption is generally made that Web-browsers will be the primary or even sole vehicle, but other possibilities exist. The upper-layer software on the client-side depends, of course, on underlying systems software and hardware.
On the other side, the cloud application services layer comprises such offerings as computational and data-analytical services, all forms of webmail, and business applications such as Google Docs and Microsoft Office Live. Application-servers are dependent on underlying software and hosts. The literature currently distinguishes between 'cloud platforms' (such as Google's App Engine and the SalesForce Apex language), and deeper-nested 'cloud infrastructure' (such as Amazon's Elastic Compute Cloud). A host may run multiple instances of server applications (and conceivably also of platforms or infrastructure). Server applications generally need access to background databases. These may be remote, and hence accessed over the Internet, and may be replicated.
Intermediation is needed between the client and server applications. Communications over the Internet must be facilitated. A function, referred to here as a 'Cloud Manager', must be available, to at least assign the request to a server. In practice, a range of additional functions must be performed at the gateway to the cloud, including monitoring of the available capacity of the various hosts, load-balancing, and usage accounting. The tariff may be variable, in which case the Cloud Manager needs to administer it, and make it available to clients. If cloud computing matures into a competitive market, brokers are likely to emerge, to intercede between vast numbers of clients, on the one hand, and multiple service-providers' cloud managers, on the other.
A comprehensive framework such as this is essential, because otherwise designs will reflect service-providers' interests to the detriment of users' interests.
Users may benefit from cloud computing, in such areas as enhanced service accessibility, other technical advantages, and reduced up-front and/or operational costs. The purpose of this section is to consider the downsides of cloud computing, from the user perspective.
In any form of outsourcing, risks arise (Loh & Venkatraman 1995, Kremic 2006). User organisations cede a degree of control, because the resources are no longer under hierarchical or command control. Instead, information about the resources, and influence over them, is mediated by employees of at least one, and often more than one, outside organisation, and by the terms of the relevant contract(s). This may be advantageous to the user organisation in several ways. The potential benefits are not automatic outcomes, however. They depend on appropriate choice of contractor, appropriate terms of contract, monitoring, effective actions when problems are detected, and ongoing, constructive relationships among the parties.
Cloud computing is a particular form of outsourcing, characterised by increases in the extent to which resource-management is delegated. This is beneficial in that it enables both parties to focus on their special competencies. On the other hand, the greater opacity is problematical when things go wrong. Cloud computing therefore exacerbates many of the risks arising from outsourcing, and creates some new ones. The following sub-sections provide outlines of key operational, contingent, security and business risks. The categories adopted reflect Avizienis et al. (2004), but have been adapted somewhat to better support analysis of risks from the user's perspective.
Problems may arise during the day-to-day operation and use of a cloud service, which affect its dependability.
Availability. By this is meant the service's readiness and reachability.
Reliability. The continuity of availability of hosts, servers and databases is dependent upon the cloud operators' performance, and upon the performance of the sub-nets that user devices and hosts are connected to, and of the relevant parts of the backbone.
All facilities are subject to unplanned outages, occasioned by 'Acts of God' and of mankind. Even at this early stage of market maturation, cloud service-providers have suffered unscheduled downtime.
Facilities are also subject to planned outages, unless they are fully supported by hot-sites, and their switchover arrangements are proven and reliable and are transparent to the user.
Integrity. By this is meant sustained correctness of the service, in conformance with the users' reasonable expectations. The elements whose integrity are at risk include:
Loss of integrity is potentially very harmful to the user, and to the user's customers. The user organisation has limited control, and limited access, and is entirely dependent on the service-provider for investigation, information about the cause of the problem, corrective actions, and the prioritisation of efforts to achieve corrective actions.
Fit. The available services may not match the user's needs. This may give rise to additional user costs, delays and duplication of effort.
Maintanability. Deficiencies in the service need to be fixed, and minor modifications undertaken, without undue impact on the service's availability, reliability, integrity and fit.
This sub-section considers problems that may be of low likelihood but are potentially highly significant.
Survival. Two distinct areas of risk exist:
Major Service Interruptions. Some outages have already been for periods of time that could have a serious negative impact on organisations that become dependent on cloud computing, in such areas as staff costs and the quality of customer service. For most organisations, survival is threatened if a service outage exceeds some period of time; and, for many, that period may be measured not in months or even weeks, but days.
Frequency of Interruption, and Resilience. Even short outages and response delays have an impact on usability. Rapid resumption after interruptions may be dependent on replicated databases whose synchronisation is maintained in real-time.
Compatibility. The service-provider may use software, software versions, protocols or data formats that are not convenient to the user. Worse, the service-provider may switch from one software supplier or data format to another, or upgrade to a new software version or data format, without the user being able to accommodate the change in a prompt, convenient or cost-effective manner.
Flexibility. The service-provider may not support the customisation necessary to fit the service to a particular user's needs.
The service-provider may not support forward-compatibility of software, protocols and data formats (to enable migration to new levels of service), backward compatibility (to protect legacy systems), or lateral compatibility (to ensure operational freedom of escape to another provider).
A familiar litany of security risks exists, on the server side, on the client side and on the communications links among them. The categories include:
Service Security. Harm may arise from environmental, second-party and third-party threats to any aspect of reliability or integrity.
Data Security. Harm may arise from environmental, second-party and third-party threats to content, both in remote storage and in transit.
Authentication and Authorisation. There are enormous challenges in providing clients with convenient access to data and processes in the cloud, while denying access to imposters (Hogben 2009).
Susceptibility to Denial of Service Attacks. In principle, this risk should be reduced in a cloud computing environment, because of the existence of multiple, separate servers. In practice, economics dictates that choke-points will exist, particularly on the client side, but perhaps also in cloud managers and in data servers.
The previous sub-sections have considered technical issues. This sub-section identifies risks to the outsourcer's business operations.
Cost. Outsourcing commonly results in the user organisation losing corporate knowledge about the application, about IT services, and about the reasonable costs involved in delivering them. As a result, there is a risk of cost blow-outs within the agreed tariff.
Further, commitment to the use of any service-provider gives rise to an inherent lock-in effect, because of the switching costs that the user will incur if they move to an alternative provider or shift the function back in-house. The user is therefore exposed to price-increases or tariff-shifts by the service-provider.
In addition, cloud computing may involve high-volume and expensive data transfers. This may be because of the size of the data-sets being handled, or because of the need for frequent, medium-sized data transfers as part of replication and synchronisation processes.
Customer Service. If applications are affected that reduce service to the outsourcer's own customers, direct business harm arises.
Privacy Breach. If applications involve personal data, then a range of potentially serious impacts can arise from low-quality service from the cloud. Categories of harm include:
Legal Compliance. Organisations in many countries have formal obligations in such areas as data protection law, the law of confidence, financial services regulations, and evidence discovery law. Company Directors have additional obligations in relation to asset protection, due diligence, business continuity and risk management. All of these are threatened by low-quality service from the cloud.
The rich catalogue of risks identified above could be seen as throwing serious doubt on the applicability of cloud computing. As the first sub-section below indicates, however, organisations have varying needs for computing support, and in some contexts even highly risk-prone cloud computing services have a role to play. The second sub-section presents a consolidated statement of user requirements of cloud computing architecture.
All users of cloud computing would appear to require the following:
Assurance depends on a legal relationship being created and sustained that obligates the service-provider to the user, and practical means whereby the user can enforce those obligations. It is conventional for the terms to be defined in a contract, terms of service, and a service level agreement (SLA, e.g. Buyya et al. 2009). (Although, remarkably, Armbrust et al. (2009) regard SLAs as superfluous).
Further, the discovery of shortfalls in the service-provider's performance depends on the auditability of the services, and on the effective and timely performance of audits.
Apart from the three essential features identified in the previous sub-section, the many other risk factors identified above are of varying significance to users. In order to appreciate the implications of the risk analysis conducted above, three categories of use-profile are usefully distinguished.
At one extremity, cloud computing is (at least in its current, emergent form) completely inappropriate. One possible depiction of this category is 'mission-critical systems'. This is meaningful in military applications, and some other kinds of operational contexts; but it fits very poorly with most applications in business and government. Alternative depictions include systems that embody the organisation's 'core competencies', and applications whose failure or even extended malperformance would threaten the organisation's health and even survival. In these circumstances, cloud computing's opacity, uncertain reliability, and the various contingent risks make it a very bad fit to the use-profile.
At the other extremity, cloud computing may be very well-suited to some kinds of activities. Some uses of computing are highly price-sensitive. Others are adjuncts to analysis and decision-making rather than essential elements. (For example, some data analysis is undertaken on a 'just in case' basis, in much the same way as trawls of publications and patents databases are conducted). In such circumstances, loss of control, uncertain reliability and contingent risks can be traded-off against the cost-advantages and convenience factors. Even service quality and data survival may be able to be sacrificed.
For the third category of use-profile, in between the two extremes, the applicability of cloud computing will depend firstly on the threshhold tests of whether the risks can be adequately understood and adequately managed, and secondly on the nature of the trade-offs between potential benefits and uncontrollable risks.
In order to reflect the above analyses, broad user requirements of cloud computing architecture are summarised in Exhibit 2.
This section draws some implications from the analyses reported in the preceding sections.
The fact that the client side is intrinsic to cloud computing leads to the implication that security risk assessments and solutions must be end-to-end rather than limited to the server side.
Features of cloud computing architectures must enable the assurance of data transmission security from clients, via brokers and cloud managers, across to process-servers, and out to data-servers. The data that is stored and processed within the cloud must have assured data integrity and data access security, and that depends on special-purpose components and features being specified within cloud computing infrastructure.
Further, client-side infrastructure embodies a vast array of vulnerabilities, particularly in the case of consumer-oriented devices and software, and even more so in the case of devices that support user mobility (Clarke & Maurushat 2007). Of particular relevance is the designed-in vulnerability of browsers. For example, ActiveX 'controls' provide uncontrolled (and uncontrollable) access to devices running Microsoft systems software. In addition, Javascript has become fare more intrusive with the rise of AJAX techniques. Hence the infrastructure must encompass features that enable the designers of platforms and services to address the risks arising from communications with vulnerable user devices and vulnerable clients.
Other aspects of users' requirements depend on end-to-end, cooperative actions. In particular, satisfactory levels of client authentication need to be achieved, through identity authentication components or APIs, and by accepting externally-managed identities such as those arriving through Shibboleth (Morgan et al. 2004) and OpenID.
For applications that support any form of personally identifiable data, components and features are necessary to support privacy protections. Many privacy-enhancing technologies (PETs) have been proposed and prototyped, but remarkably few have been deployed, despite the scope for positive business cases (Clarke 2008).
The 'privacy through policy' movement was still-born when Platform for Privacy Preferences (P3P) was limited to the server side. Multiple attempts to resuscitate it have borne little fruit. An alternative 'privacy by architecture' notion is proposed in Spiekermann & Cranor (2009). An example of an architectural feature that addresses the problem of privacy risk is the proposal for 'sticky privacy policies', in (Creese et al. (2009).
For users to be able to demonstrate compliance with data protection laws, cloud managers must have the capability to exercise control over the jurisdictional locations of hosts in which servers are used. This will only be possible if cloud computing architectures extend to intermediary nodes, and encompass components or APIs that deliver that functionality.
The need has been identified for cloud computing architecture to be comprehensive, in the sense of encompassing not only the server side, but also the client side and intermediating functions. Risks have been identified that confront users. The differential attitudes to those risks have been shown to depend on the use-profile, and user requirements have been proposed that need to be blended with the technical requirements identified in the relevant computer science literature.
Cloud computing faces impediments to adoption similar to those that dogged both B2C and B2B eCommerce for long periods, and that resulted in a great deal of lost time and lost investment. Many potential applications of cloud computing are 'accidents waiting to happen'. Publicity arising from those accidents will greatly harm cloud computing's reputation. If the initiative is to fulfil its promise, it is essential that investment be made in public awareness, education and training. For those efforts to be credible, however, it is essential that the architectures of cloud computing reflect the user perspectives presented in this paper.
Anderson R.W. (2008) 'The Cloud Services Stack -- Infrastructure', rwandering.net, July 2008, at http://rwandering.net/2008/07/28/the-cloud-services-stack-infrastructure/
Armbrust M., Fox A., Griffith R., Joseph A.D., Katz R., Konwinski A., Lee H., Patterson D., Rabkin A., Stoica I. & Zaharia M. (2009) 'Above the Clouds: A Berkeley View of Cloud Computing' Technical Report No. UCB/EECS-2009-28, UC Berkeley Reliable Adaptive Distributed Systems Laboratory, February, 2009, at http://www.eecs.berkeley.edu/Pubs/TechRpts/2009/EECS-2009-28.pdf
Avizienis A., Laprie J.C., Randell B. & Landwehr C. (2004) 'Basic Concepts and Taxonomy of Dependable and Secure Computing' IEEE Trans. Dependable and Secure Computing 1,1 (2004) 11- 33
Buyya R., Pandey S. & Vecchiola C. (2009) 'Cloudbus Toolkit for Market-Oriented Cloud Computing' Proc. 1st Int'l Conf. on Cloud Computing, Beijing, 1-4 December 2009, at http://arxiv.org/pdf/0910.1974
CSA (2009) 'Security Guidance for Critical Areas of Focus in Cloud Computing' Cloud Security Alliance, April 2009, at http://www.cloudsecurityalliance.org/csaguide.pdf
Clarke R. (2008) 'Business Cases for Privacy-Enhancing Technologies' Chapter 7 in Subramanian R. (Ed.) 'Computer Security, Privacy and Politics: Current Issues, Challenges and Solutions' IDEA Group, 2008, pp. 135-155, at http://www.rogerclarke.com/EC/PETsBusCase.html
Clarke R. & Maurushat A. (2007) 'The Feasibility of Consumer Device Security' J. of Law, Information and Science 18 (2007), at http://www.rogerclarke.com/II/ConsDevSecy.html
Creese S., Hopkins P., Pearson S. & Shen Y. (2009) 'Data Protection-Aware Design for Cloud Computing' Proc. CloudCom 2009, Beijing, Springer LNCS, December 2009, at http://www.hpl.hp.com/techreports/2009/HPL-2009-192.pdf
Hogben G. (2009) 'Privacy, Security and Identity in the Cloud' European Network and Information Security Agency (ENISA), June 2009, at http://www.enisa.europa.eu/act/res/other-areas/cloud-computing/Cloud_Identity_Hogben.pdf
Kremic T., Tukel O. & Rom W.O. (2006) 'Outsourcing decision support: a survey of benefits, risks, and decision factors' Supply Chain Management 11, 6 (2006) 467 - 482
Loh L. & Venkatraman N. (1995) 'An Empirical Study of Information Technology Outsourcing: Benefits, Risks, and Performance Implications' Proc. ICIS 1995, Paper 25, at http://aisel.aisnet.org/icis1995/25
Morgan R. L., Cantor S., Carmody S., Hoehn W. & Klingenstein K. (2004) 'Federated Security: The Shibboleth Approach' Educause Quarterly 27, 4 (2004), at http://www.educause.edu/EDUCAUSE+Quarterly/EDUCAUSEQuarterlyMagazineVolum/FederatedSecurityTheShibboleth/157315
Spiekermann S. & Cranor L.F. (2009) 'Engineering Privacy' IEEE Transactions on Software Engineering 35, 1 (Jan/Feb 2009) 67, at http://papers.ssrn.com/sol3/Delivery.cfm/SSRN_ID1330103_code421272.pdf?abstractid=1085333&mirid=1
Vaquero L.M., Rodero-Merino L., Caceres J. & Lindner M. (2009) 'A Break in the Clouds: Towards a Cloud Definition' ACM SIGCOMM Computer Communication Review 39, 1 (January 2009) 50-55, at http://ccr.sigcomm.org/online/files/p50-v39n1l-vaqueroA.pdf
Youseff L., Butrico M. & Da Silva D. (2008) 'Toward a Unified Ontology of Cloud Computing' Proc. Grid Computing Environments Workshop, 2008, at http://www.cs.ucsb.edu/~lyouseff/CCOntology/CloudOntology.pdf
Roger Clarke is Principal of Xamax Consultancy Pty Ltd, Canberra. He is also a Visiting Professor in the Cyberspace Law & Policy Centre at the University of N.S.W., and a Visiting Professor in the Department of Computer Science at the Australian National University.
| Personalia |
Photographs Presentations Videos |
Access Statistics |
 |
The content and infrastructure for these community service pages are provided by Roger Clarke through his consultancy company, Xamax. From the site's beginnings in August 1994 until February 2009, the infrastructure was provided by the Australian National University. During that time, the site accumulated close to 30 million hits. It passed 65 million in early 2021. Sponsored by the Gallery, Bunhybee Grasslands, the extended Clarke Family, Knights of the Spatchcock and their drummer |
Xamax Consultancy Pty Ltd ACN: 002 360 456 78 Sidaway St, Chapman ACT 2611 AUSTRALIA Tel: +61 2 6288 6916 |
Created: 26 November 2009 - Last Amended: 31 January 2010 by Roger Clarke - Site Last Verified: 15 February 2009
This document is at www.rogerclarke.com/II/CCSA.html
Mail to Webmaster - © Xamax Consultancy Pty Ltd, 1995-2022 - Privacy Policy