Roger Clarke's Web-Site
© Xamax Consultancy Pty Ltd, 1995-2024

Infrastructure
& Privacy
Matilda
Roger Clarke's Web-Site© Xamax Consultancy Pty Ltd, 1995-2024 |

|
|||||
| HOME | eBusiness |
Information Infrastructure |
Dataveillance & Privacy |
Identity Matters | Other Topics | |
| What's New |
Waltzing Matilda | Advanced Site-Search | ||||
Emergent Draft of 23 November 2009
© Xamax Consultancy Pty Ltd, 2009
Available under an AEShareNet ![]() licence or a Creative
Commons
licence or a Creative
Commons  licence.
licence.
This document is at http://www.rogerclarke.com/II/CCI-0911.html
The term 'cloud computing' has shot into prominence recently, driven, as most buzz-phrases are, by marketing interests. The term encompasses multiple, pre-existing services, but an analysis of the phenomenon's key features shows that it includes some new developments. Those developments have potential user benefits. They also embody risks, which are largely borne by users, and whose impacts could be considerable. Risk assessment and risk management are therefore essential, for organisational and individual users alike.
The image of a cloud has long been used as a means of depicting the means whereby the Internet somehow provides connectivity between distant devices. The term 'cloud computing' is commonly ascribed to Google's CEO in a conference presentation in 2006, although it was quickly applied to announcements by Amazon and IBM of intentions to release services claimed to be rather different from anything currently on offer, and soon after was retro-fitted to the SaleForce service (Fowler & Worthen 2009). The first articles using the term that are visible in Google Scholar were published during 2008.
Broadly speaking, cloud computing promises to shift customer data and processing from customers' own devices to hosts run by service-providers. Microsoft refers to it as "Internet-based storage and services ... enabling users to access software applications and data that are stored at off-site datacenters rather than on the user's own device or PC or at an organization's on-site datacenter" (Microsoft 2009, p. 1). It is claimed to enable customers to pay for usage rather than invest in their own technology, resulting in enhanced affordability and convenience.
The term was created by marketers, and is intended to convey a sense of excitement and difference, even revolution. On the other hand, it can be regarded as an evolution from several previous threads of development, and even as an attempt to recover from previous failed attempts. A balanced interpretation might be that it represents a further step in the commoditisation of IT services.
The services currently on offer exhibit somewhat varying characteristics. Some represent underlying infrastructure or platforms, such as Google Code, Amazon's Elastic Compute Cloud (EC2), Microsoft Azure and Sun Grid. Others are applications such as SalesForce, Clarizen (project management), gmail, and Google Apps, most visibly Google Docs for Business and Google Docs for Consumers.
As is the case with all new, marketing-motivated terms, questions arise as to what the term means, what benefits such services confer, to whom, and under what circumstances; what negative impacts and implications they entail, and for whom; and what risks arise, and who bears them. Analyses have been undertaken from the perspective of service-providers (e.g. Armbrust et al. 2009). The need exists for analyses from the viewpoints of prospective organisational users and individual users.
The approach adopted in this research has been a comprehensive review of academic, commercial and popular literatures, complemented by the application of prior bodies of theory and practice to the subject-matter, and the assessment of terms of contract and privacy policies against previously-published normative templates. Google Scholar disclosed in November 2009 a few dozen articles that had attracted citations. All of these were evaluated. The AIS eLibrary disclosed at that stage no articles of relevance. This research accordingly represents an initial foray into the research-domain within the information systems discipline.
The article commences by considering the meaning of the term, culminating in a working definition, statement of scope, and architectural model. The potential benefits to users are identified. Disbenefits and risks are then considered. Although specific elements have been discussed in various prior publications, few sources were unearthed that attempted a comprehensive review of the issues that arise. It was accordingly necessary for that section to present an original analysis. Implications are drawn for organisational and individual users, and opportunities for researchers are identified.
This section reviews the origins of the term, and key features that provide candidates for a definition, in order to establish a working definition, a statement of scope, and an architectural model.
Since the term 'cloud computing' was coined, apparently in 2006, a great many definitions have been offered. The review below shows that some commonalities exist, but that no authoritative definition has yet been enunciated.
Many publications refer to the Gartner 'hype-cycle', a model first published in 1995 (Fenn 1995, Linden & Fenn 2003). Articles published during 2009 generally place cloud computing in the early 'Inflated Expectations' phase. However, the Gartner hype-cycle is itself a part of the 'hype economy', in that it reinforces the continual, marketing-driven creation of new buzz-words. The 'hype-cycle' notion embodies the presumptions that each new term reflects a meaningful phenomenon, that each new phenomenon is usefully differentiated from predecessors, and that each new phenomenon will survive rather than fail. A degree of scepticism is advisable, to allow for the possibility of failure, and for the possibility of absorption by some subsequent and perhaps better-conceived notion.
One of the difficulties in defining cloud computing is that the descriptions provided encompass a great many pre-existing categories of service, some of which are of very recent coinage, and others of which date as far back as the 1960s. Exhibit 1 identifies key predecessor terms.
A wide range of definitions is available, e.g. CCJ (2009). A commercial provider offers this: "[cloud computing is] the notion of providing easily accessible compute and storage resources on a pay-as-you-go, on-demand basis, from a virtually infinite infrastructure managed by someone else" (Crandell 2008).
A tighter definition from the computer science literature is "a large-scale distributed computing paradigm that is driven by economies of scale, in which a pool of abstracted, virtualized, dynamically-scalable, managed computing power, storage, platforms, and services are delivered on demand to external customers over the Internet" (Foster et al. 2008).
In Armbrust et al. (2009), the distinguishing features are argued to be "the illusion of infinite computing resources available on demand ..., the elimination of an up-front commitment, ... [and] the ability to pay for use of computing resources on a short-term basis as needed".
Five 'essential characteristics' were nominated in Mell & Grant (2009). See also ISACA (2009, p. 6). These were:
Several authors have attempted to sift the literature for an emergent, authoritative definition. An analysis by Vaquero et al. (2009) found no common features, but the authors suggested that the key aspects were virtualized resources that can be dynamically re-configured to the scale needed by the user at the time.
In Buyya et al. (2009), it is asserted that it is inherent to cloud computing that services are subject to a Service Level Agreement (SLA). Arbrust et al. (2009) take the opposite view, lauding the emergence of "pay-as-you-go computing with no contract" (p. 7). The analysis that follows needs to take into account the extent to which the cloud computing service-provider offers warranties and indemnities, and abides by them, or operates on an 'all-care, no-responsibility' basis.
In order to support a coherent analysis of benefits, downsides and risks, a working definition is essential. In this paper, the term 'cloud computing' encompasses any arrangement in which:
Several circumstances are expressly declared to be out-of-scope. The term, as used in this paper, does not relate to access to, or processing of, data that is not under the user's control. Hence a user is not using cloud computing if they are accessing someone else's web-site, or using an outsourced analytical service that processes census data. For clarity, the organisation that outsourced that web-site or those analytical services may be dependent on a cloud computing services provider.
In addition, if the organisation retains control over the primary copy of its data, and has the capability of processing it, then it is not dependent on cloud computing, but is only using it as an adjunct to its operations, e.g. for peak processing power, or backup.
On the other hand, a wide range of circumstances are defined to be within-scope for the purposes of the analysis that follows. Applications may offer computational resources, data storage or communications. As regards the form of data-storage, all of the following are within-scope:
As regards the format of the data, the scope extends to email, web-pages managed by the user, and data-formats typical of 'business applications', including textual ('word-processed') documents, spreadsheets, images and databases.
As regards the version of the data, cloud computing applications encompass circumstances in which:
Further, a cloud computing service may be openly accessible, (a 'public cloud'), or limited to particular users, as in an Intranet or an Extranet (a 'private cloud'). It may be depended upon by an organisation (in which case the relationship with the service-provider is 'B2B') or by an individual (in a 'B2C' relationship).
Beyond a mere textual definition, clarity is needed concerning the elements involved and the inter-relationships among them. Architecture diagrams in the literature to date have focussed exclusively on the server-side of the cloud. For example, Youssef et al. (2008) proposed what they referred to as an 'ontology', comprising layers for infrastructure, for software environment or platform, and for applications. Other architectural depictions are in Anderson (2008) and CAS (2009).
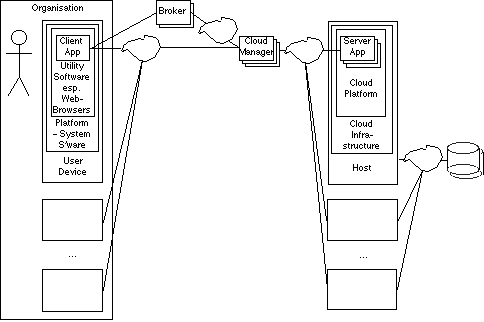
To support an analysis of benefits and risks for users, it is essential that the architectural model encompass not only the service-provider side, but also the user side and the intermediating elements. Exhibit 2 reflects all three segments of a comprehensive cloud computing model.
A user utilises one or more user devices, and may do so within the context of an organisation. The software in each device comprises a client application (which may be substantial, or merely, say, a few lines of Javascript), which may run within utility software. The presumption is generally made that Web-browsers will be the primary or even sole vehicle, but other possibilities exist. The upper-layer software on the client-side depends, of course, on underlying systems software and hardware.
On the other side, the cloud application services layer comprises such offerings as all forms of webmail, Google Docs and Microsoft Office Live. Application-servers are dependent on underlying software and hosts. The literature currently distinguishes between 'cloud platforms' (such as Google's App Engine and the SalesForce Apex language), and deeper-nested 'cloud infrastructure' (such as Amazon's Elastic Compute Cloud). A host may run multiple instances of server applications (and conceivably also of platforms or infrastructure). Server applications generally need access to background databases. These may be remote, and hence accessed over the Internet, or replicated locally.
Intermediation is needed between the client and server applications. Communications over the Internet must be facilitated. A function, referred to here as a 'Cloud Manager', must be available, to at least assign the request to a server. In practice, a range of additional functions must be performed at the gateway to the cloud, including monitoring of the available capacity of the various hosts, load-balancing, and usage accounting. The tariff may be variable, in which case the Cloud Manager needs to administer it, and make it available to clients. If cloud computing matures into a competitive market, brokers are likely to emerge, to intercede between vast numbers of clients, on the one hand, and service-providers' cloud managers, on the other.
Earlier versions of outsourced service provision have already offered a range of potential benefits to both organisational and individual users. Cloud computing offers upgraded promises. The catalogue in Exhibit 3 reflects the selling-points identified in the recent commercial and academic literatures. It is divided into enhanced service accessibility, other technical benefits, and financial benefits.
Few of the potential benefits arise solely from the incremental difference between cloud computing and its predecessors, and hence rational users need to consider whether cloud computing or some more conventional form of outsourcing is appropriate to their needs. Moreover, none of the benefits arise automatically, but rather are contingent on correspondence between the user's needs, on the one hand, and the service-provider's capabilities, terms of service and pricing, on the other.
Despite the technical benefits, it appears that service-providers perceive the main driver for adoption as being cost-savings combined with the convenience to business divisions arising from the ability to by-pass internal IT departments and contract directly for services. If this transpires to be the case, the cautious risk assessment conventionally undertaken by IT departments will also be by-passed. It is therefore particularly important for senior executives to appreciate the downsides of cloud computing that are analysed in the following sections. Technical factors are identified first, then business risks.
[THE REMAINDER OF THE DRAFT IS HIGHLY PROVISIONAL AT THIS STAGE!]
This section focusses on technical factors, relating to service operation, contingent risks, and security.
This sub-section considers the normal operation of services that are outsourced under cloud computing arrangements.
[LOOK FOR A THEORETICAL BASIS FOR THIS SEGMENT. IS THERE A RELEVANT ISO OR AS/NZS?]
Relevant standards include AS ISO/IEC 20000-2007 (Information technology - Service management). Process guidance is provided by the Information Technology Infrastructure Library (ITIL), but ITIL lacks clear statements of the qualities that the processes are intended to assure.
TEXT
The conventional approach to managing such operational risks is through Service Level Agreements (SLAs). There appear to be no standards for SLAs, although some guides and checklists exist. The design, negotiation and administration of SLAs are fraught with difficulties in any IT outsourcing activity, but especially so where the nature of the service involves considerable delegation to the service-provider in relation to the location of hosts.
The reliability of outsourced services might compare favourably with equivalent internal services. On the other hand, control and fine-tuning of internal services is much more readily achieved than negotiations with an incumbent supplier.
This sub-section considers the contingencies that may arise, and that would have an adverse impact on the organisational or individual user that is depending on a cloud computing service-provider.
[LOOK FOR A THEORETICAL BASIS FOR THIS SEGMENT. IS THERE A RELEVANT ISO OR AS/NZS?]
Standards relevant to these risks include ISO/IEC 24762:2008 (Disaster Recovery Services), BS 25999:2006/07 (Business continuity), and BS 25777:2008 (Information and communications technology continuity management - Code of practice).
TEXT
The following major issues arise:
Many businesses face a business survival risk, in the sense that, after some period of unavailability of Internet-based services, the company would lose revenue to such an extent that it would not survive. In all such circumstances, fallback mechanisms are essential. Where an organisation depends on internal IT resources, its survival depends on its own actions. Outsourcing without contingency plans, especially to a cloud of virtual servers, passes control over the organisation's future into the hands of unknown others, with limited legal recourse against malfunction. Investment in fallback mechanisms, and hence in local replication of key data and processing capabilities, appears to be an absolutely essential element of all significant corporate uses of cloud computing.
Addressing these contingencies in a satisfactory manner depends on the existence of appropriate terms of contract and an SLA. Business continuity for the user organisation depends on the replication of data and software, on either multiple contracts or the proven ability to quickly convert to another provider that can deliver the required services at short notice.
This sub-section considers the security aspects of cloud computing services. An early analysis was reviewed in Brodkin (2008a). CAS (2009) provides a preliminary analysis by an association of vendors. See also Mather at al. (2009).
[LOOK FOR A THEORETICAL BASIS FOR THIS SEGMENT. IS THERE A RELEVANT ISO OR AS/NZS?]
Relevant standards include ISO/IEC 27002:2005 - previously 17799:2005 (Information technology - Security techniques - Code of practice for information security management)
Consider MS (2009a).
[Can SLAs really help? Isn't third-party certification essential, given the opaqueness of the services and conditions, and the user organisation's probable lack of security expertise?]
The previous section identified the various technical factors that may result in harm to the organisational or individual user. This section focusses on business factors, relating to acquisition of the service, and the consumer terms, privacy and more general compliance aspects.
This sub-section considers the factors that arise when an organisational or individual user is considering adopting a cloud computing service. It draws on relevant parts of a normative template previously developed and applied by the author/s (Clarke 2006, Clarke 2008, Svantesson & Clarke 2010).
[PROVIDE A BRIEF OVERVIEW OF THE Normative Template for Marketer-Prosumer Communications]
KEY ELEMENTS TO TALK ABOUT:
This sub-section considers the factors that arise from the use of a cloud computing service. It draws on relevant parts of the normative template previously developed and applied by the author/s (Clarke 2006, Clarke 2008, Svantesson & Clarke 2010).
KEY ELEMENTS TO TALK ABOUT:
Do SLAs help, given the likely disparity in organisational size and market power, and the likely jurisdictional distance between the parties??
[COMPARISON OF ONE PROVIDER'S TERMS AGAINST THE TEMPLATE:
[?GOOGLE DOCS?
This sub-section considers privacy impacts of cloud computing. It extends beyond mere compliance with data protection laws to encompass public expectations and policy issues that are not, or not yet, reflected in the law.
Several early privacy analyses have been published variously by a Privacy Commissioner (Cavoukian 2009), an industry association (Gellman 2009), a news service (Harris 2009), an IT provider (MS 2009b), and a commercial publisher (Mather et al. 2009). At least one privacy advocacy organisation maintains a resource-page (EPIC 2009), and at least one has issued a policy statement on the matter (APF 2009).
[PROVIDE A BRIEF OVERVIEW OF THE Privacy Statement Template]
KEY ELEMENTS TO TALK ABOUT:
Privacy laws?
Privacy policy statements?
[COMPARISON OF ONE PROVIDER'S TERMS AGAINST THE TEMPLATE:
[?GOOGLE DOCS?
Joint et al. (2009) considered legal aspects of the adoption of cloud computing, and concluded that there were serious compliance difficulties, particularly for European companies. They drew attention to problems in such areas as data protection law, the law of confidence, and financial services regulation including auditability. CSA (2009) offered a similar list, but added evidence discovery. In addition to express obligations, corporations may need to demonstrate adequate performance against various business and technical standards.
More broadly, Company Directors have obligations in relation to asset protection, due diligence, business continuity and risk management. Various of the technical and business risks discussed in this section may be sufficiently significant to demand attention not only from business managers and senior executives, but also from the Board room.
In widely-reported comments made in September 2008, the Free Software Foundation's Richard Stallman said that cloud computing forces people to hand over control of their information to a third party. "One reason you should not use Web applications to do your computing is that you lose control. It's just as bad as using a proprietary program. Do your own computing on your own computer with your copy of a freedom-respecting program. If you use a proprietary program or somebody else's Web server, you're defenseless. You're putty in the hands of whoever developed that software" ( Johnson 2008).
The analysis reported on in this paper puts flesh to those claims. It has provided some clarity about the term's meaning, and about the benefits that may be available to user organisations and individual users. Most crucially, it has clarified the very substantial downsides and risks involved in using cloud computing. It lays a foundation for guidance to user organisations in determining the circumstances in which cloud computing is an appropriate approach to adopt.
User organisations need to appreciate the nature, benefits, disadvantages and risks, and carefully consider the extent to which the services may be applicable to their needs. Where cloud computing is adopted, risk management strategies need to be devised and carefully implemented. Because services are unlikely to be subject to clear law, policy and standards, fallback positions and disaster plans are essential. For many organisations, and many business functions within them, it is essential that key data be mirrored within the organisation, and that internal processing capabilities and capacity must be sufficient to enable interim operation and subsequent resumption of normal business.
Individual users may use cloud computing, provided that they place no great value on the ongoing availability of the data or the services. They need to assume that the terms of service will be opaque, that they will be advantageous to the provider rather than the user, and that the user will have little or no capability to enforce such limited rights as they may appear to have.
Research is needed in a variety of areas. The generic analysis reported on in this paper needs to be applied to specific categories of cloud computing services. The terms offered by particular providers need to be evaluated against these risks, and against the templates used in this paper, or other checklists of a similar nature. Also of considerable value would be case studies of various successful, and especially unsuccessful, applications.
In Armbrust et al. (2008), it was noted that "past efforts at utility computing failed, and we note that in each case one or two ... critical characteristics were missing" (p. 5). If cloud computing is to be more than just another marketing buzz-phrase that leaves corporate wreckage in its wake, service-providers need to invest a great deal in many aspects of their infrastructure, platforms, applications, and terms of service.
Anderson R.W. (2008) 'The Cloud Services Stack -- Infrastructure', rwandering.net, July 2008, at http://rwandering.net/2008/07/28/the-cloud-services-stack-infrastructure/
APF (2009) 'Policy Statement re Cloud Computing' Australian Privacy Foundation, November 2009, at http://www.privacy.org.au/Papers/CloudComp-0911.html
Armbrust M., Fox A., Griffith R., Joseph A.D., Katz R., Konwinski A., Lee H., Patterson D., Rabkin A., Stoica I. & Zaharia M. (2009) 'Above the Clouds: A Berkeley View of Cloud Computing' Technical Report No. UCB/EECS-2009-28, UC Berkeley Reliable Adaptive Distributed Systems Laboratory, February, 2009, at http://www.eecs.berkeley.edu/Pubs/TechRpts/2009/EECS-2009-28.pdf
Brodkin J. (2008a) 'Gartner: Seven cloud-computing security risks' InfoWorld, July 2008, at http://www.infoworld.com/print/36853
Brodkin J. (2008b) 'Loss of customer data spurs closure of online storage service 'The Linkup' Network World, August 2008 , at http://www.networkworld.com/news/2008/081108-linkup-failure.html
Brodkin J. (2009) 'Rackspace apologizes for cloud outage, prepares to issue service credits' Network World, 5 November 2009, at http://www.networkworld.com/news/2009/110509-rackspace-outage-apology.html?fsrc=netflash-rss
Buyya R., Yeo C.S., Venugopal S., Broberg J. & Brandic I. (2009) 'Cloud computing and emerging IT platforms: Vision, hype, and reality for delivering computing as the 5th utility' (2009) Future Generation Computer Systems 25 (January 2009) 599-616, at http://www.buyya.com/gridbus/papers/Cloud-FGCS2009.pdf
Cavoukian A. (2009) 'Privacy in the clouds: A white paper on privacy and digital identity' Information and Privacy Commissioner of Ontario, 2009, at http://www.ipc.on.ca/images/Resources/privacyintheclouds.pdf
CCJ (2009) 'Twenty-One Experts Define Cloud Computing' Cloud Computing Journal, January 2009, at http://cloudcomputing.sys-con.com/read/612375_p.htm
Clarke R. (2006) 'A Major Impediment to B2C Success is ... the Concept 'B2C' Proc. ICEC'06, Fredericton NB, Canada, 14-16 August 2006, at http://www.rogerclarke.com/EC/ICEC06.html
Clarke R. (2008) 'B2C Distrust Factors in the Prosumer Era' Proc. CollECTeR Iberoamerica, Madrid, 25-28 June 2008, pp. 1-12, at http://www.rogerclarke.com/EC/Collecter08.html
Crandell B. (2008) 'Defogging Cloud Computing: A Taxonomy' gigaom.com, June 2008, at http://gigaom.com/2008/06/16/defogging-cloud-computing-a-taxonomy/
CSA (2009) 'Security Guidance for Critical Areas of Focus in Cloud Computing' Cloud Security Alliance, April 2009, at http://www.cloudsecurityalliance.org/csaguide.pdf
EPIC (2009) 'Resources on Cloud Computing' Electronic Privacy Information Center, Washington DC, 2009, at http://epic.org/privacy/cloudcomputing/
Fenn J. (1995) 'When to Leap on the Hype Cycle' Gartner Group, January, 1995
Foster I., Zhao Y., Raicu I. & Lu S. (2008) 'Cloud Computing and Grid Computing 360-Degree Compared' Proc. Grid Computing Environments Workshop, 12-16 Nov. 2008
Fowler G.A. & Worthen B. (2009) 'The Internet Industry Is on a Cloud -- Whatever That May Mean' Wall Street Journal, 26 March 2009, at http://online.wsj.com/article/SB123802623665542725.html#printMode
Fried I. (2009) 'Major outage hits T-Mobile Sidekick users' C-Net News, 6 October 6 2009, at http://news.cnet.com/8301-13860_3-10368709-56.html
Gellman R. (2009) 'Cloud Computing and Privacy' World Privacy Forum, 2009, at http://www.worldprivacyforum.org/pdf/WPF_Cloud_Privacy_Report.pdf
Harris L. (2009) 'Perils in the Privacy Cloud' ABC News, 15 Sep 2009, at http://abcnews.go.com/Technology/AheadoftheCurve/privacy-evaporates-computing-cloud/Story?id=8573715&page=1
Hogben G. (2009) 'Privacy, Security and Identity in the Cloud' European Network and Information Security Agency (ENISA), June 2009, at http://www.enisa.europa.eu/act/res/other-areas/cloud-computing/Cloud_Identity_Hogben.pdf
ISACA (2009) ' Cloud Computing: Business Benefits With Security, Governance and Assurance Perspectives' ISACA, October 2009, at http://www.isaca.org/AMTemplate.cfm?Section=Deliverables&Template=/ContentManagement/ContentDisplay.cfm&ContentID=53044
Johnson B. (2008) 'Cloud computing is a trap, warns GNU founder Richard Stallman' The Guardian, 29 September 2008, at http://www.guardian.co.uk/technology/2008/sep/29/cloud.computing.richard.stallman
Joint A., Baker E. & Eccles E. (2009) 'Hey, you, get off of that cloud?' Computer Law & Security Review 25, 2 (2009) 270-274
Linden A. & Fenn J. (2003) 'Understanding Gartner's Hype Cycles' Gartner, Strategic Analysis Report R-20-1971, May 2003, at http://carbon.cudenver.edu/~jgerlach/emergingtechnologyOL/FirstReadings/HypeCycleIntro.pdf
Marshall R. (2008) 'Experts urge caution on cloud computing' Secure Computing Magazine, 14 October 2008, at http://www.securecomputing.net.au/News/125405,experts-urge-caution-on-cloud-computing.aspx
Mather T., Kumaraswamy S. & Latif S. (2009) 'Cloud Security and Privacy: An Enterprise Perspective on Risks and Compliance' O'Reilly Media, 2009
Mell P. & Grance T. (2009) 'The NIST Definition of Cloud Computing' National Institute of Standards and Technology, Information Technology Laboratory, Version 15, October 2009 at http://csrc.nist.gov/groups/SNS/cloud-computing/cloud-def-v15.doc
Metz C. (2008) 'Engineer accidentally deletes cloud' The Register, 9 October 2008, at http://www.theregister.co.uk/2008/08/28/flexiscale_outage/
MS (2009a) 'Securing Microsoft's Cloud' Microsoft, May 2009, at http://www.globalfoundationservices.com/security/documents/SecuringtheMSCloudMay09.pdf
MS (2009b) 'Privacy in the Cloud Computing Era - A Microsoft Perspective' Microsoft, November 2009
Raphael J.R. (2009) 'Gmail Outage Marks Sixth Downtime in Eight Months' PC World, 25 February 2009, at http://www.pcworld.com/article/160153/gmail_outage_marks_sixth_downtime_in_eight_months.html
Svantesson D. & Clarke R. (2010) 'A Best Practice Model for eConsumer Protection' Computer Law & Security Review 27, 1 (January 2010)
Vaquero L.M., Rodero-Merino L., Caceres J. & Lindner M. (2009) 'A Break in the Clouds: Towards a Cloud Definition' ACM SIGCOMM Computer Communication Review 39, 1 (January 2009) 50-55, at http://ccr.sigcomm.org/online/files/p50-v39n1l-vaqueroA.pdf
Woloski M. (2008) 'SaaS Taxonomy Map' M. Woloski, July 2008, at http://blogs.southworks.net/mwoloski/2008/07/10/saas-taxonomy-map/
Youseff L., Butrico M. & Da Silva D. (2008) 'Toward a Unified Ontology of Cloud Computing' Proc. Grid Computing Environments Workshop, 2008, at http://www.cs.ucsb.edu/~lyouseff/CCOntology/CloudOntology.pdf
TEXT
Roger Clarke is Principal of Xamax Consultancy Pty Ltd, Canberra. He is also a Visiting Professor in the Cyberspace Law & Policy Centre at the University of N.S.W., and a Visiting Professor in the Department of Computer Science at the Australian National University.
| Personalia |
Photographs Presentations Videos |
Access Statistics |
 |
The content and infrastructure for these community service pages are provided by Roger Clarke through his consultancy company, Xamax. From the site's beginnings in August 1994 until February 2009, the infrastructure was provided by the Australian National University. During that time, the site accumulated close to 30 million hits. It passed 65 million in early 2021. Sponsored by the Gallery, Bunhybee Grasslands, the extended Clarke Family, Knights of the Spatchcock and their drummer |
Xamax Consultancy Pty Ltd ACN: 002 360 456 78 Sidaway St, Chapman ACT 2611 AUSTRALIA Tel: +61 2 6288 6916 |
Created: 19 November 2009 - Last Amended: 23 November 2009 by Roger Clarke - Site Last Verified: 15 February 2009
This document is at www.rogerclarke.com/II/CCI-0911.html
Mail to Webmaster - © Xamax Consultancy Pty Ltd, 1995-2022 - Privacy Policy