Roger Clarke's Web-Site
© Xamax Consultancy Pty Ltd, 1995-2024

Infrastructure
& Privacy
Matilda
Roger Clarke's Web-Site© Xamax Consultancy Pty Ltd, 1995-2024 |

|
|||||
| HOME | eBusiness |
Information Infrastructure |
Dataveillance & Privacy |
Identity Matters | Other Topics | |
| What's New |
Waltzing Matilda | Advanced Site-Search | ||||
Working Paper - Version of 6 August 2017
Prepared for presentation at the
10th
Workshop on the Social Implications of National Security
(SINS17)
Sydney, 9 August 2017
© Xamax Consultancy Pty Ltd, 2017
Available under an AEShareNet ![]() licence or a Creative
Commons
licence or a Creative
Commons  licence.
licence.
This document is at http://www.rogerclarke.com/ID/BiomReg.html
The supporting slide-set is at http://www.rogerclarke.com/ID/BiomReg.pdf
The term 'RegTech' emerged in 2016 as a means of adding sex-appeal to the application of technology to compliance responsibilities, in particular those of corporations in the financial services sector. This presentation adopts a broader vision of technology applied to regulation, arguing that RegTech is needed in all sectors, and that it's essential to consider the perspectives not only of the regulatees, but also of the regulators, and of the intended beneficiaries of the regulatory activity.
The question addressed in the session is to what extent can biometrics play a role in RegTech. It's necessary to take a realistic view of the nature of biometric technologies, of the categories of application that they can be put to, and of the array of real-world challenges that confront those applications. There may be scope for biometric applications in RegTech, but far less than enthusiasts would like to believe.
Regulatory arrangements are important wherever natural controls fail to curb excesses. Given the scale of contemporary economies and societies, technologies need to be harnessed in support of activities involved in imposition and supervision by regulators, compliance by regulatees, and utilisation by beneficiaries.
Providers of regulatory technologies (RegTech) naturally 'follow the money' and focus on those large corporations that have substantial obligations imposed on them by formal regulatory instruments, and hence need to perform onerous compliance activities. The financial services industry is accordingly a primary focus. RegTech's scope is far wider than that, however. Other industry sectors are subject to formalised regulatory requirements, and many looser and less stringent business processes can benefit from technological support. In addition to the needs of regulatees, those of regulators can be served, and the intended beneficiaries of regulatory mechanisms also have needs that technology can serve.
This paper begins by reviewing the nature of regulation, and identifying the many forms it takes. That provides a platform for a vision of RegTech with far broader horizons than the financial services sector alone. There has been a longstanding presumption that identity, particularly of people, is central to social control mechanisms. This has resulted in a long, failure-strewn series of initiatives in 'identity provisioning' and 'identity management'. Now the question is being asked whether biometrics can play a role. This paper accordingly summarises the state of play with biometric technologies, conducts a couple of thought-experiments, and draws conclusions for the application of biometrics in the RegTech arena.
The concept of regulation is frequently thought of as a matter of law and policy. Its foundations go far deeper, however. General systems theory grew out of observations of biology, where natural processes are subject to other natural processes whose effect is to limit, control or regulate them, giving rise to homeostatis - the tendency of natural systems to maintain the status quo (von Bertalanffy 1968). During the industrial revolution, a significant breakthrough occurred when Watts invented the steam or 'fly-ball' governor, such that a man-made process exercised control over another man-made process. Together, these threads gave rise to the insights of cybernetics, whereby sensors provide feedback that enables a controller to monitor a process, effectors enable the controller to regulate the process, and succesive levels of nested controllers enable complex systems to be managed (Wiener 1948).
The analysis of RegTech is not concerned with biological phenomena or manufacturing processes, but with economic and social systems. In these contexts, the motivation for active regulatory measures arises when some class of entities behaves in a manner that has materially negative impacts on other entities. Figure 1 provides a graphical representation of the players and their relationships.
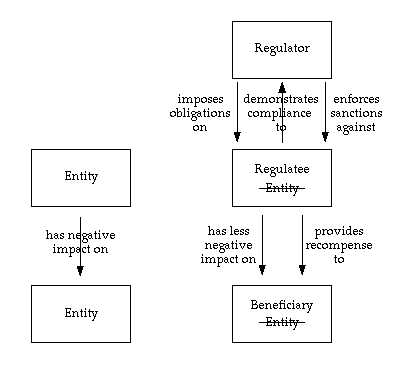
A simple, useful but incomplete definition of regulation is "instruments used ... to influence or control the way people and businesses behave in order to achieve economic, social or environmental policy objectives" (ANAO 2007). A valuable aspect of that interpretation is its generality - formal legal mechanisms are certainly not the only way to influence behaviour. A weakness of the approach, however, is that it is restricted firstly to explicit human actions ("instruments"), and secondly to those instruments whose intention is to achieve influence ("used to").
Theoretical works on regulation refer to an 'enforcement pyramid', with persuasive measures at the bottom and used in high volume, escalating upwards to a (hopefully) smaller volume of aggressive sanctions such as licence revocation (Ayres & Braithwaite 1992). "There is a heavy presumption in favour of starting at the base of the pyramid because dialogue is a low-cost, respectful and time-efficient strategy for obtaining compliance. The responses of the regulatee to interventions drawn from the base of the pyramid are the ones that determine if, how far and when the regulator escalates up the pyramid" (Drahos & Krygier 2017, p.5).
For the present purpose, rather than individual instruments or measures, it is more useful to focus on categories of mechanisms. This paper accordingly proposes the model in Figure 2. This distinguishes layers, based on the degree of formalism and compulsion.
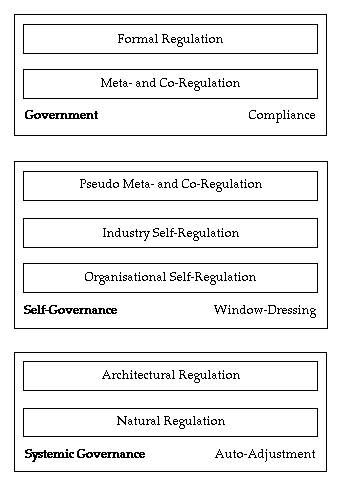
The foundational regulatory layer is a correlate of the natural control processes that occur in biological systems. It comprises natural influences, by which is meant processes that are intrinsic to the relevant socio-economic system (Clarke 1995, 2014). Examples of natural controls include the exercise of countervailing power by those affected by an initiative, activities by competitors, reputational effects, and cost/benefit trade-offs. An appreciation of pre-existing natural controls is a vital precursor to any analysis of regulation, because the starting-point always has to be 'what is there about the natural order of things that is inadequate, and how will intervention improve the situation?'.
All of the other layers represent interventions into natural processes, and comprise 'instruments' and 'measures', generally designed with an intention to achieve some end. That end is desirably to curb undesirable behaviours and excesses, but in some cases the purpose is to give the appearance of doing so, in order to hold off stronger or more effective interventions.
The second-lowest layer in the hierarchy, referred to here as 'architectural regulation', is a correlate of artefacts like the mechanical steam governor. It comprises aspects of the system that are designed into the infrastructure that supports the particular socio-economic system. Information technology provides many opportunities, and even mechanical controls are feasible, through the application of robotics. For example, unusual occurrences can be logged and notified to regulators for investigation, online behaviour indicative of unauthorised access or hacking can be detected and countermeasures deployed, stock exchange operations can be automatically suspended when signs of serious bandwagon effects are detected, and dam sluice-gate settings can be automatically adjusted in response to measures of catchment-area precipitation events or increases in feeder-stream water-flows.
At the other extremity of the hierarchy, formal regulation exercises the power of a parliament through statutes and delegated legislation (such as Regulations), together with case law that clarifies the application of the legislation. Formal regulation demands compliance with requirements that are expressed in more or less specific terms, and is complemented by sanctions and enforcement powers.
Because regulation of the formal kind imposes considerable constraints and costs, regulatees naturally invest a great deal of time, effort and money in order to avoid, minimise and dilute formal regulation. As a result, a substantial flotilla of intermediate forms exists. In the lowest layer of instruments are organisational self-regulatory mechanisms. These include internal codes of conduct and 'customer charters', and self-restraint associated with expressions such as 'business ethics' and 'corporate social responsibility'.
The next higher layer is industry sector self-regulation. In many sectors, schemes exist that express technical or process standards. There are also many codes of conduct, or of practice, or of ethics, and some industries feature agreements or Memoranda of Understanding (MoUs) that are claimed to have, and may even have, some regulatory effect. However, by their nature, and under the influence of trade practices / anti-monopoly / anti-cartel laws, these are in almost all cases non-binding. A further mechanism used in some fields is accreditation schemes, which are better understood as meta-brands (Clarke 2001).
The effectiveness of the two self-regulatory layers, perceived from the viewpoint of the entities that are meant to be beneficiaries of regulatory arrangements, generally falls well short of their promise. Activities conducted under the 'governance' label are primarily motivated by the avoidance of harm to the regulatees rather than the assurance of protections for beneficiaries. Braithwaite (2017) notes that "self-regulation has a formidable history of industry abuse of [the] privilege" (p.124). Writing primarily in the context of environmental regulation, Gunningham & Sinclair (2017) write "Overall, what passes for smart regulation in policy circles is more akin to a regulatory stew from which policymakers have selected particularly juicy morsels that appeal to the political rhetoric of their masters, largely irrespective of their likely effectiveness or efficiency" (p.144), and note that 'voluntarism' is generally an effective regulatory element only when it exists in combination with 'command-and-control' components.
Other intermediate forms have emerged that have greater prospects of achieving the regulatory objective of protecting against inappropriate behaviour and excesses. In a number of areas, convincing arguments can reasonably be made by regulatees to the effect that government is poorly placed to cope with either the detailed workings of complex industry sectors, or the rate of change in industries' structures, practices and technologies. Parliaments should therefore legislate no more than a framework, and enable details of the scheme to be developed within that framework.
During the last four decades, further intermediate forms have emerged, between (often heavy-handed) formal regulation and (mostly ineffective and excusatory) self-regulation. In Grabowsky (2017), the notion of 'enforced self-regulation' is traced to Braithwaite (1982), and the use of the term 'meta-regulation', in its sense of 'government-regulated industry self-regulation', to Gupta & Lad (1983). See also Parker (2007). In parallel, the notion of 'co-regulation' emerged (Ayres & Braithwaite 1992, Clarke 1999). Common features of these approaches are that a legislative framework is enacted, but the details are expressed in a code that is established and maintained through a negotiation process among the relevant parties. These necessarily include at least the regulatory agency, the regulatees and the intended beneficiaries of the regulation, and the process must reflect needs rather than institutional and market power. Further, a scheme of this nature necessarily specifies meaningful sanctions, and enforces them.
Unfortunately, the promise of enforced self-regulation, meta-regulation and co-regulation has seldom been delivered. Commonly, the nominal beneficiaries are effectively excluded from the negotiations, and terms are not meaningfully enforced, and may even be unenforceable. Schemes that lack such fundamentals - typically in the form of 'guidelines' and 'MoUs' but sometimes masquerading under the title of 'Codes' - or that feature capture of the regulatory agency, are referred to in this analysis as 'pseudo' meta- or co-regulatory.
In practice, any regulatory regime normally comprises elements of multiple of the layers in Figure 2: "in the majority of circumstances, the use of multiple rather than single policy instruments, and a broader range of regulatory actors, will produce better regulation [by means of] the implementation of complementary combinations of instruments and participants ..." (Gunningham & Sinclair 2017, p.133). For criteria for the evaluation of regulatory regimes, see Gunningham et al. (1998) and Clarke & Bennett Moses (2014, Table 2).
Within this framework, what contributions does and can technology make to regulatory schemes?
There is scope for technology to be applied to many aspects of regulation, and at all of the layers outlined in the previous section. The term 'RegTech' is a recent coinage (although a small environmental consultancy in Idaho might see that differently, as might the Therapeutic Goods Administration's Consultative Forum). Most early uses of the buzzphrase cite IIF (2016), although earlier mentions exist in Arner et al. (2015) and Treleaven (2015). The current usage arose by reference to the established term 'FinTech', driven by the desire of technology providers to produce offerings attractive to regulatees in the financial services sector. That sector is subject to very substantial formal regulation. This is partly because of the enormous economic and social costs arising from the spectacular failure of softer regulatory forms, resulting in financial crises. Another factor is the serial and substantial intrusions by law enforcement and national security agencies into the sector, demanding copies of transaction flows and then imposing onerous standards on identification and identity authentication for the sector's customers - justified originally by the spectres of organised crime, then drug lords and arms traders, and since 2001 terrorists.
The initial, narrow interpretation of RegTech is 'using technology to reduce compliance costs in financial services'. One aspect is the re-discovery of continuous, automated transaction monitoring as a means of compliance assurance (Winn 2017). Current discussions tend to focus on contemporary buzzwords, particularly Big Data, AI and IoT (e.g. Arner et al. 2016). Conceivably, such technologies may have something to offer, despite the massive and seriously misleading hype associated with them (Clarke 2016). But even without resorting to technologies of the 'vogue but vague' variety, a great many opportunities exist for RegTech initiatives.
Current compliance practices are poorly supported, and hence RegTech needs to assist organisations to catch up with where they should already be in such areas as acccess control, audit trails, and automated monitoring of audit trails. Those techniques were well-known a quarter-century ago (Clarke 1992), but their implementation remains almost as poor as at that time, as evidenced by the continual flow of data breach reports (Lord 2017). In many organisations outside the financial services sector, even the implementation of baseline security measures would greatly improve performance (Clarke 2015). The same applies to incident management (ENISA 2010), complaints-handling (e.g. ISO 2006) and automated statistical reporting.
Beyond the needs of regulatees, regulators also have an interest in applying technology to their own needs. Financial transactions tracking has long been a focus, in Australia by Austrac. Stock market supervisors subject trading to real-time monitoring for patterns indicative of illegal behaviour. Health care claims are monitored for evidence of fraudulent invoicing, over-servicing, and doctor-shopping in order to acquire supplies of controlled drugs. Many further possibilities exist in such areas.
Generally overlooked are the needs of the intended beneficiaries of regulation. Consumers, citizens and small business alike need guidance on how to go about dealing with organisations that are failing to fulfil their obligations or otherwise behaving unreasonably. As a result of the current post-customer-service mode of business and government operations, it is increasingly common for problems to fester rather than being solved. This has increased the need for guidance as to which regulatory agencies exercise what powers over what organisations, and on how to initiate formal complaints processes. Regulatory agencies have failed their responsibilities to assist in these discovery processes, and in the composition of effective complaints. So scope exists for services to be delivered - although viable business models may be difficult to contrive.
Within this rich palette of RegTech opportunities, suggestions have been made that biometric technologies have something to offer. In order to evaluate that proposition, a review of the nature of biometrics is necessary.
What appears to be the earliest formal reference on RegTech envisages biometrics to be part of the technology mix: "When coupled with biometrics technology to enable fingerprint and iris scanning, face recognition, but also remote passport recognition and eIDs, advanced analytics can allow for more efficient ways to verify an individual's identity to access financial services" (IIF 2016). Further, one of the first academic papers to emerge on the topic wrote approvingly of the 'India Stack' for RegTech, whose foundation is "a national system of biometric identification" (Arner et al. 2016). (India has imposed an authoritarian biometrics regime called Aadhar, in defiance of claims before the courts of breach of the constitutional right to privacy - Greenleaf 2016).
In the RegTech arena, as in so many others, some key questions need to be confronted:
Biometric technologies have a history of failure and industry turnover. The entry-halls in Australian airports are currently in tumult because of the failures of the once-much-vaunted facial 'recognition' system. Even with false-acceptance ratios turned up high, they don't work as claimed. It doesn't help matters that the design of passenger flows within the terminal appears to be remarkably incompetent. Fingerprints represent a less inadequate basis for biometric schemes, but they too have proven in many circumstances to be incapable of being effectively applied. The latest great hope of the industry appears to be iris recognition. In the absence of published, independent testing, impact assessments and public consultations, we have to await the horror-stories that will doubtless emerge in this arena as well.
Biometric technologies are confronted by a fundamental problem: the list of strongly desirable attributes of a biometric is quite long, and the contenders don't satisfy them. Further, a wide range of technical features of biometrics create challenges for designers (Mansfield & Wayman 2002). These include:
Technical inadequacies are exacerbated by further aspects of the socio-technical systems into which biometric technologies are injected:
For a rich selection of problems and sources, see Schneier (1999), Jain et al. (2004), Schneier 2009, Babbage (2010) and Magnet (2011). A succinct summary is: 'biometrics are all about convenience, not security'. [Declaration: I stole that epigram from security consultant Steve Wilson; but Steve was talking specifically about Apple TouchID, and he said "consumer biometrics are all about convenience, not security" (Wilson 2013, my emphasis). The words in my text are an epigram, i.e. a short, pithy statement, not a quotation.]
The Australian Privacy Foundation was and remains astonished at the naiveté of so many of the organisations that have flirted with biometric applications. Its Policy Statement on Biometrics provides a layman's introduction to biometrics, summarises ten problems it perceives, and concludes that "No new biometric schemes should be implemented until and unless comprehensive laws have been brought into effect to regulate them" (APF 2008).
The most common application of biometrics is what is misleadingly referred to as 'verification', but is far more appropriately called 'authentication'. This involves a 1-to-1 comparison between a newly-captured biometric and that or those previously recorded for that person who the newly-presenting person is asserted to be. A second application is what is commonly referred to 'identification', involving a 1-to-n search for a match to a newly-captured biometric within a population, in many cases a large population.
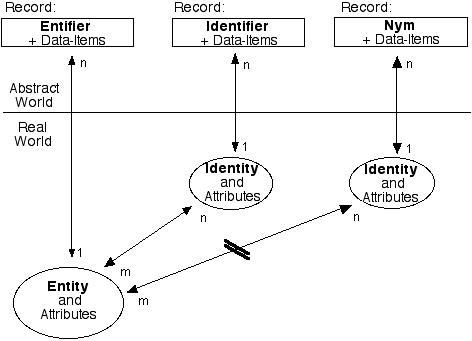
However, designers commonly fail to recognise that biometrics is not about identification or identity authentication, but rather about entification or entity authentication. As depicted by Figure 3, biometrics cut through identities (such as Company Secretary and Clinic Practice Manager) and deal in sensitive personal data relating to the person who is presumed (often incorrectly) to be the user of the identity, and, moreover, to be the sole user of it.
Extract from Clarke (2010)
The assessment of biometric technologies and their applications in this section is almost entirely negative. The reasons for this are the attempt at brevity, and the need to counterbalance the excessive claims made by proponents. The Appendix draws attention to positive contributions I've made in the biometrics area. The following section takes into account biometric technologies' deficiencies and threatening nature, and considers ways in which they might nonetheless have contributions to make to RegTech.
A great deal of effort has been invested into the cases of entity authentication (involving 1-to-1 comparisons) and entification (involving 1-to-n comparisons). Regulatory matters, on the other hand, involve complex and multi-phase business processes. Evaluations of the scope for biometrics to contribute to RegTech accordingly require the adoption of a broader perspective.
Deep case studies of real-world circumstances are vitally needed. Unfortunately, there is a great shortage of them, because of the habitual secrecy with which the biometrics industry has always worked. Even where open technology and process standards exist, analysis is hampered because critical elements are proprietary and closed. Independent evaluations are rarely published. Assertions without supporting evidence are made by provider and user organisations alike. Engagement with affected individuals, their representatives, and public interest advocacy organisations are almost entirely unknown. For example, the 30-year records of the Australian Privacy Foundation include no evidence of any consultation processes being undertaken in relation to any of the many implementations of biometrics in the country.
In the absence of case studies, this section conducts two brief thought-experiments, one in an area in which criminal behaviour in well-known to occur, and another relating to control over access to security-sensitive data.
Many of us are company directors, in my own case since 1974. Not all of the company that we keep, so to speak, behaves as ethically as, of course, we do. A particular concern that is recurrent every few years is the technique currently described as 'phoenix companies', whereby a company goes into liquidation owing a lot of money, and the assets and the going concern are transferred to another company without the liabilities travelling with them.
So what's the problem that biometrics could address? A current proposition is that company directors should be required to register, and to quote their registration-code (a 'Director Identification Number') when they perform particular actions. See generally Anderson et al. (2017).
The safeguards that are being sought are that:
The creation of a registration-id for directors, whether name-and-date-of-birth or a number, in itself achieves none of these things; and, even if it were just a small part of a much more substantial scheme, it's not clear whether the existence of such an identifier would contribute much to the objectives.
In principle, it could be attractive to restructure the proposal to include an entifier rather than an identifier, i.e. a biometric. However, there would need to be many elements of such a scheme. In particular:
Such a scheme would in itself do nothing to locate individuals sought for prosecution - unless of course the collection of biometric measures has by then become normalised, and every, say, border-crossing, traffic infringement, random alcohol and drug test, civil ceremony, etc. involves collection and comparison with the wanted list. Where suspects were located, however, the results of comparisons of new biometric measures against that recorded in the register would be likely to be compelling evidence in a trial.
There are about 2.5m Australian corporations (ASIC 2017), and of these 11,500 are in the frame (Anderson et al. 2017), suggesting that needles represent c. 0.5% of the haystack. Corporations are, like cyberspace, merely 'shared hallucinations', so it is impossible to apply biometrics to them (and remarkably challenging even to design effective identification and identity authentication processes). The focus therefore falls on the c. 2,500 of perhaps 250,000-500,000 distinct director identities, or 0.5-1.0% of the particular haystack. (No count or estimate of the number of company directors has been located on ASIC's site or in Anderson's work).
In short, the proposition is to impose a biometric scheme - of a kind achieved in very few of even the most aggressively authoritarian nation-states - on several hundred thousand individuals, in the hope of constraining the activities of a cumulative total of perhaps 2,000 individuals over the last few years who have committed offences, in particular under s.592 of the Corporations Act.
[It would reasonably be expected that these are serious? criminal? (or only civil?) offences. But I can't see what penalties apply in these circumstances. Everything I could quickly locate seems to be about the 'trading while insolvent' offence. On the one hand "Illegal phoenix activity is a serious crime and may result in company officers (directors and secretaries) being imprisoned" (ASIC 2013), but on the other hand no indication of the nature of the offence is provided in that reference, in Anderson (2017) or in media reports, other than vague mentions of 'the directors' duties provisions'. Media searches failed to find any reports of cases. The ATO's Phoenix Task Force, meanwhile, offers only two unidentified cases studies, one of which is claimed to have achieved a prosecution for fraud (implying that it was under the Crimes Act rather than the Corporations Act), and the other of which was said to have resulted in increased assessments and penalties but with no mention of a prosecution, successful or otherwise (ATO 2017). This matters, because the absence of evidence of prosecutions undermines the credibility of a proposition that draconian boimetric measures are necessary and proportionate.]
In summary, all directors, throughout the country, would present themselves, initially and every time thereafter when they want to perform a regulated action, to the regulatory agency (whose footprint is currently almost entirely limited to capital-city offices), or perhaps to a suitable and suitably-managed third party organisation (Australia Post? their own accountant or lawyer???), be subjected to biometric procedures, and perhaps have one or more biometrics stored in a database that is subject to multiple further uses.
At some stage during the development, implementation or operation of the scheme, the challenges and failure modes discussed in the previous section would become publicly visible, and the scope for error and failure would be obvious to all. Directors of small companies have a degree of clout, and the big end of town has a great deal of it. It is difficult to see any government surviving the attempt to implement such a scheme, nor any incoming government failing to close the project down. All of this is completely foreseeable. Application of the well-known but frequently-ignored standards of transparency, justification and proportionality might just save the careers of some budding statespeople.
A great many categories of data need to be subject to reliable safeguards. Some data has intrinsic value (e.g. Bitcoin strings, and debtors' ledgers that prove a debt in court). Some data has personal value (not only for privacy reasons, but also for personal security and family harmony). Other reasons for applying high standards of data protection include data's operational, competitive, reputational and compliance value (Clarke 2013).
An early biometric vignette of relevance was the Mexican Attorney-General's imposition of biometrics on 160 of his staff (although for area access rather than online access - Weissert 2004). Stories like those need to be the subject of deep case studies; but they are in short supply. An issue that's been in the Australian media lately, and that lends itself to a thought-experiment, is the accessibility of Medicare Registry data by well over 200,000 people (Farrell 2017). That's a very substantial threat to personal values. However, because privacy protections are a very low priority among Australian organisations, major investment is unlikely to be forthcoming. On the other hand, this large-scale vulnerability is also a threat to public confidence and trust in the security of payment systems - because the data is a goldmine for identity fraudsters.
Surely biometrics could help in access control? India certainly seems to think so; and it was reported over a decade ago that Centrelink was planning to provide their thousands of employees with a biometric enhancement to their staff identity cards, in order to achieve two-factor authentication on each occasion on which a person logged in, and when they performed sensitive online transactions.
It appears that Medicare registry data is accessible through the Health Professional Online Services (HPOS) system, for which the authentication mechanisms are either a digital signature or a password (possibly including a second factor in the form of a one-time password transmitted over a separate channel). Could a biometric provide far tighter control than the existing arrangements?
Key problems that need to be addressed appear to be as follows:
Of this list of apparent problems, only the last would appear capable of being addressed by the use of biometric technology. Requiring the use of biometric authentication would place some constraints on use of accounts by persons other than the person to whom the authenticator was issued. On the other hand:
In return for very substantial costs being imposed on both the agency and every practice throughout the country, the risks arising from people masquerading as a particular employee in the same practice would be somewhat reduced. In return for that, the risks arising from the sheer number of people with authorised (and essentially uncontrolled) access to the data would be multiplied. In addition, none of the other problems identified at the beginning of this section would be addressed.
The net effect of the application of biometrics would appear to be not a decrease, but a moderate increase in the data's vulnerability.
The previous section discussed two potential applications of biometrics to RegTech. They were thought-experiments, not case studies. Their selection was random, not careful, and may reflect unconscious bias on the author's part. The impracticability and negative payback apparent in both instances may or may not be a common feature of biometric applications in RegTech. There is no substitute for deep cases studies of real-world projects.
Subject to those qualifications, a couple of key messages emerge from experience with a range of actual projects combined with the above thought-experiments:
Before starting to think about biometrics as a possible solution, it's crucial to know what the problem is that you're trying to solve.
All biometric schemes face substantial technical challenges, and require pre-planned arrangements for multiple exception-conditions that will arise frequently. This is particularly so in contexts that involve large volumes of transactions, or that are subject to multiple failure-modes, especially where some players are motivated to subvert or attack the scheme.
At some stage, the real nature of the scheme, and its shortfalls, will both become abundantly apparent. A great many people will dislike it intensely. Many of them will be powerful enough to cause the scheme's sponsors a great deal of grief.
As in other areas of biometric technologies, user organisations that consider biometrics as a form of RegTech need to avoid getting caught up in supplier hype, and evaluate the possibilities calmly and realistically.
Cartels of user-and-provider organisations such as the Biometrics Institute need to be broken down, not just for the public's benefit, but also for that of the shareholders in companies that get sucked into spending money on ineffective technologies. (Despite the home-page claim of being "a user group with a majority of user members", as at July 2017, user organisations represented only 42% of the Institute's membership, and supplier members 50%).
From a public policy perspective, propositions for the design and application of privacy-invasive technologies need to be subject to a set of meta-principles (APF2013) - every one of which is conventional and accepted, yet far too often applied.
In summary, it's possible that biometrics may have a role to play somewhere in the RegTech arena; but the path is strewn with risks for developers, regulatees and regulators, and great care is strongly advisable.
Arner D.W., Barberis J. & Buckley R.P. (2015) 'The Evolution of FinTech: A New Post-Crisis Paradigm?' University of Hong Kong Faculty of Law Research Paper No. 2015/047, UNSW Law Research Paper No. 2016-62, October 2015, at https://hub.hku.hk/bitstream/10722/221450/1/Content.pdf?accept=1
Arner D.W., Barberis J. & Buckley R.P. (2016) 'FinTech, RegTech and the Reconceptualization of Financial Regulation' Northwestern Journal of International Law and Business, PrePrint of October 2016 at https://papers.ssrn.com/sol3/papers.cfm?abstract_id=2847806
ANAO (2007) 'Administering Regulation: Better Practice Guide' Australian National Audit Office, March 2007, at http://www.anao.gov.au/~/media/Uploads/Documents/administering_regulation_.pdf
ANAO (2014) 'Better practice guide: Administering Regulation: Achieving the right balance' Australian National Audit Office, June 2014, at https://www.anao.gov.au/work/better-practice-guide/administering-regulation-achieving-right-balance
Anderson H., Ramsay I., Welsh M. & Hedges J. (2017) 'Phoenix Activity: Recommendations on Detection, Disruption And Enforcement' Melbourne Law School and Monash Business School, February 2017, at http://law.unimelb.edu.au/__data/assets/pdf_file/0020/2274131/Phoenix-Activity-Recommendations-on-Detection-Disruption-and-Enforcement.pdf
APF (2008) 'Biometrics' Policy Statement, Australian Privacy Foundation, April 2008, at http://www.privacy.org.au/Papers/Biometrics.html
APF (2013) 'Meta-Principles for Privacy Protection' Australian Privacy Foundation, March 2013, at http://www.privacy.org.au/Papers/PS-MetaP.html
ASIC (2013) 'Small business-illegal phoenix activity' Australian Securities and Investment Commission, November 2013, at http://asic.gov.au/for-business/your-business/small-business/compliance-for-small-business/small-business-illegal-phoenix-activity/
ASIC (2017) '2017 Company registration statistics' Australian Securities and Investment Commission, at http://asic.gov.au/regulatory-resources/find-a-document/statistics/company-registration-statistics/2017-company-registration-statistics/, copy extracted 31 July 2017
ATO (2017) 'Phoenix Taskforce' Australian Tax Office, July 2017, at https://www.ato.gov.au/General/The-fight-against-tax-crime/Our-focus/Illegal-phoenix-activity/Phoenix-Taskforce/?=redirected#Newsandresults
Ayres I. & Braithwaite J. (1992) 'Responsive Regulation: Transcending the Deregulation Debate' Oxford Univ. Press
Babbage (2010) 'Biometrics: The Difference Engine: Dubious security' The Economist, October 2010, at http://www.economist.com/blogs/babbage/2010/10/biometrics
von Bertalanffy L. (1968) 'General System Theory: Foundations, Development, Applications' George Braziller, 1968
Braithwaite J. (1982) `Enforced self-regulation: A new strategy for corporate crime control' Michigan Law Review 80, 7 (1982) 1466-507
Braithwaite J. (2017) 'Types of responsiveness' Chapter 7 in Drahos (2017), pp. 117-132, at http://press-files.anu.edu.au/downloads/press/n2304/pdf/ch07.pdf
Clarke R. (1992) 'Practicalities of Keeping Confidential Information on a Database With Multiple Points of Access : Technological and Organisational Measures' Xamax Consultancy Pty Ltd, September 1992, Invited Paper for a Seminar of the Independent Commission Against Corruption of the State of N.S.W. on 'Just Trade? A Seminar on Unauthorised Release of Government Information', Sydney Opera House, 12 October 1992, at http://www.rogerclarke.com.au/DV/PaperICAC.html
Clarke R. (1995) 'A Normative Regulatory Framework for Computer Matching' Journal of Computer & Information Law XIII,4 (Summer 1995) 585-633, PrePrint at http://www.rogerclarke.com/DV/MatchFrame.html#IntrCtls
Clarke R. (1999) 'Internet Privacy Concerns Confirm the Case for Intervention' Commun. ACM 42, 2 (February 1999) 60-67, PrePrint at http://www.rogerclarke.com/DV/CACM99.html
Clarke R. (2001) 'Meta-Brands' Privacy Law & Policy Reporter 7, 11 (May 2001), PrePrint at http://www.rogerclarke.com/DV/MetaBrands.html
Clarke R. (2002) 'The Scope for Privacy-Sensitive Biometric Architecture' Xamax Consultancy Pty Ltd, May 2002, at http://www.rogerclarke.com/DV/BioArch.html
Clarke R. (2010) 'A Sufficiently Rich Model of (Id)entity, Authentication and Authorisation' Proc. IDIS 2009 - The 2nd Multidisciplinary Workshop on Identity in the Information Society, LSE, London, 5 June 2009, PrePrint at http://www.rogerclarke.com/ID/IdModel-1002.html
Clarke R. (2013) 'Data Risks in the Cloud' Journal of Theoretical and Applied Electronic Commerce Research (JTAER) 8, 3 (December 2013) 60-74, PrePrint at http://www.rogerclarke.com/II/DRC.html
Clarke R. (2014) 'The Regulation of of the Impact of Civilian Drones on Behavioural Privacy' Computer Law & Security Review 30, 3 (June 2014) 286-305, PrePrint at http://www.rogerclarke.com/SOS/Drones-BP.html#RN
Clarke R. (2015) 'The Prospects of Easier Security for SMEs and Consumers' Computer Law & Security Review 31, 4 (August 2015) 538-552, PrePrint at http://www.rogerclarke.com/EC/SSACS.html
Clarke R. (2016) 'Big Data, Big Risks' Information Systems Journal 26, 1 (January 2016) 77-90, PrePrint at http://www.rogerclarke.com/EC/BDBR.html
Clarke R. & Bennett Moses L. (2014) 'The Regulation of Civilian Drones' Impacts on Public Safety' Computer Law & Security Review 30, 3 (June 2014) 263-285, PrePrint at http://www.rogerclarke.com/SOS/Drones-PS.html
Drahos P. (ed.) (2017) 'Regulatory Theory: Foundations and Applications' ANU Press, 2017. at http://press.anu.edu.au/publications/regulatory-theory/download
Drahos P. & Krygier M. (2017) 'Regulation, institutions and networks' Ch. 1 in Drahos (2017), at http://press-files.anu.edu.au/downloads/press/n2304/pdf/ch01.pdf
ENISA (2010) 'Good Practice Guide for Incident Management' European Union Agency for Network and Information Security, December 2010, at https://www.enisa.europa.eu/publications/good-practice-guide-for-incident-management
Farrell P. (2017) 'Revealed: more than 200,000 people can access Medicare card details' The Guardian, 6 July 2017, at https://www.theguardian.com/australia-news/2017/jul/06/revealed-more-than-200000-people-access-medicare-card-details
Greenleaf G.W. (2016) 'Your Money or Your Life?: Modi's Deceptive Enactment of India's ID Legislation' Privacy Laws & Business International Report 140 (April 2016) 18-20, at https://papers.ssrn.com/sol3/papers.cfm?abstract_id=2800835
Grabowsky P. (2017) 'Meta-Regulation' Chapter 9 in Drahos (2017), pp. 149-161, at http://press-files.anu.edu.au/downloads/press/n2304/pdf/ch09.pdf
Gunningham N., Grabosky P, & Sinclair D. (1998) 'Smart Regulation: Designing Environmental Policy' Oxford University Press, 1998
Gunningham N. & Sinclair D. (2017) 'Smart Regulation', Chapter 8 in Drahos (2017), pp. 133-148, at http://press-files.anu.edu.au/downloads/press/n2304/pdf/ch08.pdf
Gupta,A. & Lad L. (1983) `Industry self-regulation: An economic, organizational, and political analysis' The Academy of Management Review 8, 3 (1983) 416-25
IIF (2016) 'RegTech in Financial Services: Technology Solutions for Compliance and Reporting' Institite of International Finance', March 2016, at https://perma.cc/VKM6-HP8L
ISO (2006) 'Customer Satisfaction - guidelines for complaints handling' ISO 10002:2006 International Standards Organisation, 2006
Jain A.K., Pankanti S., Prabhakar S., Hong L., Ross A. & Wayman J.L. (2004) 'Biometrics: A Grand Challenge' Proc. Int'l Conf. on Pattern Recognition, Cambridge, UK, Aug. 2004, at http://www.cedar.buffalo.edu/~govind/CSE666/fall2007/Biometrics_GC.pdf
Lord N. (2017) 'The History of Data Breaches' Digital Guardian, 27 July 2017, at https://digitalguardian.com/blog/history-data-breaches
Magnet S.A. (2011) 'When Biometrics Fail: Gender, Race and the Technology of Identity' Duke Uni. Presss, 2011
Mansfield A.J. & Wayman J.L. (2002) 'Best Practices in Testing and Reporting Performance of Biometric Devices' U.K. National Physical Laboratory, August 2002, at http://face-rec.org/databases/mansfield02.pdf
Parker C. (2007) 'Meta-Regulation: Legal Accountability for Corporate Social Responsibility?' in McBarnet D, Voiculescu A & Campbell T (eds), The New Corporate Accountability: Corporate Social Responsibility and the Law, 2007
Schneier B. (1999) 'Biometrics: Uses and Abuses' Commun. ACM 42,8 (August 1999) 135-136, at https://www.schneier.com/essays/archives/1999/08/biometrics_uses_and.html
Schneier B. (2009) 'Tigers use scent, birds use calls - biometrics are just animal instinct' The Guardian, 8 January 2009, at https://www.theguardian.com/technology/2009/jan/08/identity-fraud-security-biometrics-schneier-id
Treleaven P. (2015) 'Financial regulation of FinTech' EY Journal of Financial Perspectives 3, 3 (Winter 2015), at https://fsinsights.ey.com/dam/jcr:f4626c4c-e1b7-4e59-a910-319fd19ab5a8/financial-regulation.pdf
Weissert W. (2004) 'Chip Implanted in Mexico Judicial Workers' myway, 14 July 2004, at http://web.archive.org/web/20040718041250/http://apnews.myway.com/article/20040714/D83QQBP80.html
Wiener N. (1948) 'Cybernetics, or Control and Communication in the Animal and the Machine' MIT Press, Cambridge, Massachusetts, 1948, 1961
Wilson S. (2013) 'How Bart Simpson might defend TouchID' Lockstep, 23 Sep 2013, at http://lockstep.com.au/blog/2013/09/23/bart-simpson-and-touchid
Winn J.K. (2017) 'What Impact Will 'RegTech' Have on the Legal Profession?' Seminar, Soochow University School of Law, Taipei, Taiwan, 7 January 2017
These are declared in order to convey that my conclusions about biometrics, although very strongly sceptical, are not exclusively so:
Roger Clarke is Principal of Xamax Consultancy Pty Ltd, Canberra. He is also a Visiting Professor in Cyberspace Law & Policy at the University of N.S.W., and a Visiting Professor in the Computer Science at the Australian National University. He has been a Board member of the Australian Privacy Foundation since its establishment in 1987, and was its Chair 2006-14.
| Personalia |
Photographs Presentations Videos |
Access Statistics |
 |
The content and infrastructure for these community service pages are provided by Roger Clarke through his consultancy company, Xamax. From the site's beginnings in August 1994 until February 2009, the infrastructure was provided by the Australian National University. During that time, the site accumulated close to 30 million hits. It passed 65 million in early 2021. Sponsored by the Gallery, Bunhybee Grasslands, the extended Clarke Family, Knights of the Spatchcock and their drummer |
Xamax Consultancy Pty Ltd ACN: 002 360 456 78 Sidaway St, Chapman ACT 2611 AUSTRALIA Tel: +61 2 6288 6916 |
Created: 31 July 2017 - Last Amended: 6 August 2017 by Roger Clarke - Site Last Verified: 15 February 2009
This document is at www.rogerclarke.com/ID/BiomReg.html
Mail to Webmaster - © Xamax Consultancy Pty Ltd, 1995-2022 - Privacy Policy