Roger Clarke's Web-Site
© Xamax Consultancy Pty Ltd, 1995-2024

Infrastructure
& Privacy
Matilda
Roger Clarke's Web-Site© Xamax Consultancy Pty Ltd, 1995-2024 |

|
|||||
| HOME | eBusiness |
Information Infrastructure |
Dataveillance & Privacy |
Identity Matters | Other Topics | |
| What's New |
Waltzing Matilda | Advanced Site-Search | ||||
Revised Version of 29 September 2016
© Xamax Consultancy Pty Ltd, 2015-16
Available under an AEShareNet ![]() licence or a Creative
Commons
licence or a Creative
Commons  licence.
licence.
This document is at http://www.rogerclarke.com/SOS/PDMP.html
The previous version is at http://www.rogerclarke.com/SOS/PDMP-160221.html
Among the many applications of electronic markets is the trading of personal data. A Special Issue of the journal Electronic Markets addressed that topic in June 2015. This paper reports on a review of the papers in that Issue, together with the further c. 25 relevant articles on privacy-related topics in prior Issues of the journal. The assessment utilised as its primary theoretical lens the notion of 'researcher perspective'.
The EM articles were found to be not merely predominantly conducted from the system sponsor's perspective, but almost exclusively so. Consideration of the concept 'market' leads to the conclusion that contributors to EM have not merely ignored the interests of stakeholders other than their corporate client, but have been so myopic that the effectiveness of their research is undermined.
The study was broadened in order to seek out the antecedents of the IS discipline's tight focus on research from the perspective of system sponsors. This gives rise to concern that the narrowness of thinking evident in the Special Issue and the journal as a whole reflects a malaise within the IS discipline.
The motivation for the analysis reported in this paper was the author's negative response to the papers in a Special Issue of the journal Electronic Markets on `Personal Data Markets', in Volume 25, Issue 2 (June 2015). Part of my concern was the apparently heavy bias towards the interests of business enterprises, to the virtual exclusion of the interests of the people whose data is being trafficked. Beyond this public policy issue, however, was discomfort about the conception of the research projects. Surely contemporary information systems demand much more awareness of the broader pictuer than is evident in those papers? And surely electronic markets generally, and particularly those in which the items being traded are personal data, necessarily involve models that encompass all participants, and recognise the existence of all stakeholders?
This paper reports on several studies that were undertaken in order to gather insight into the literature in the research domain of personal data markets.
The first section considers the nature of personal data markets. The notion of 'researcher perspective' is then introduced, to provide a theoretical basis for the studies. The three-phase method used in the research is explained. This involved textual analyses firstly of the papers in the EM Special Issue, and then of the corpus of relevant papers in the 25 volumes of the journal published to date. In order to shed some light on the results, an examination is undertaken of personal data markets and privacy notions in the Information Systems literature more broadly. The final sections of the paper discuss the implications of the findings of the analysis. It is argued that these are very serious for the people whose data is exploited by corporations, but also for the researchers whose work singlemindedly seeks to advantage those corporations over those people. It is concluded that a critical consideration of researcher perspective is a vital element of quality research in the IS area generally, and especially in research domains such as personal data markets.
An electronic market or marketspace is a virtual context in which buyers and sellers discover one another and transact business (Schmidt 1993, Rayport & Sviokla 1994, Bakos 1998, Segev et al. 1999, Weill & Vitale 2001). As with its correlates in physical places, an electronic market comprises tradable items, participants, processes that facilitate trading, and infrastructure that supports the participants and the processes (Benjamin & Wigand 1995, Schmid 1997, Kambil & van Heck 1998, Clarke 2001). Key benefits that any particular instance of a market offers are the ability for buyers and sellers to discover one another, to discover what items are on offer, to develop sufficient confidence to be prepared to conduct the transaction, and to negotiate an agreement. A market may also facilitate the delivery of the goods or performance of the services.
The journal 'Electronic Markets' declares the following working definition of the term 'electronic markets', as guidance not only for its authors, but arguably for the discipline as a whole:
"forms of networked business where multiple suppliers and customers interact for economic purposes within one or among multiple tiers in economic value chains ... In a narrow sense, [electronic markets are] allocation platforms with dynamic price discovery mechanisms involving atomistic relationships [but] in a broader sense, [electronic markets emphasise] longer term relationships and processes for enabling business transactions ... and/or knowledge management" (EM 2016. See also EM 2014).
Markets can adopt multiple forms. One important factor affecting which forms are used in which circumstances is the participants involved. As depicted by Figure 1, the participants include sellers and buyers, sometimes agents for either or both of them, usually service-providers, and possibly an intermediary, usefully referred to as a 'marketspace operator'.
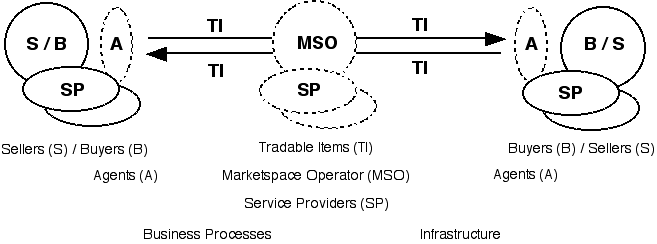
The form of the market also reflects the nature of the tradable items, distinguishing goods from services, physical from digital, and commodities from standard products, customised and customisable items. Other key considerations are the risks that need to be apportioned among the participants, and hence the terms applicable to transactions, and the processes whereby transactions are conducted and settled. Risks are affected by the nature of the exchange. Useful classifications include immediate and direct reciprocity - the mainstream variants being item-for-cash-equivalent and item-for-item (barter) - but also subscription-based, sponsorship-based, deferred reciprocity, indirect reciprocity, and gift (Schmid 1997, Reck 1997, Clarke 2001).
A crucial function that markets perform is to provide a sufficient basis for confidence among the participants, such that lack of trust does not detract from their intrinsic desire to trade (Kollock 1999, Clarke 2002a, Beckert 2005, Clarke 2006, Clarke 2008a). In many markets, a critical factor is assurance about the seller's capacity to pass to the buyer both a quality item and the desired set of rights in relation to it. This frequently includes the provision of information about the tradable item's provenance. In some markets, possession of the item by a seller is a sufficient basis for trust by the buyer. For example, in a bazaar, 'what you see is what you get', and 'no, I'm not sure where it came from'. In many markets, on the other hand, ownership rather than mere possession is important to buyers. For example, trading in shares and derivatives is dependent upon evidence of ownership (since the 1980s, through share registry entries).
Digital data presents particular challenges. For example, trading in shares and derivatives is dependent upon evidence of ownership (since the 1980s, through share registry entries). Characteristics of digital data such as intangibility and reproducability cause participants to other pay particular attention to ways of managing the risks relating to item quality, to the legitimacy of the buyer's possession of the item after it has been traded, and to the legitimacy of the various uses to which the buyer might want to put it.
In applying these concepts to the specific case of 'personal data markets', a distinction first needs to be drawn between primary and secondary markets. One form of primary market is where a consumer consciously trades personal data about themselves to another party, generally a corporation. Because in most cases buyer-corporations have considerably greater market power than seller-consumers, questions arise about the contractual terms and conditions that apply to transactions, the meaningfulness and informedness of consent, and the availability of choice.
In a second form of primary market, an organisation that has created personal data about individuals trades it to another party. Examples of originating parties include informants, paparrazzi and investigators (e.g. private detectives, and insurance and law enforcement agencies). There are many circumstances in which use of the Internet , particularly the Web, gives rise to the collection of personal data about a user by a corporation in a manner that is sufficiently surreptitious that individuals are generally unaware of it and cannot meaningfully be regarded as market participants. An aphorism current since 2010 encapsulates the problem: "If you're not paying for it, you're not the customer; you're the product being sold". Moreover, the range of surveillance mechanisms that generate such data is increasing, as devices that carry people, such as motor vehicles, devices that are carried by people, such as handheld computing equipment, and progressively devices that are worn by people, and are inserted into people, generate streams of personal data.
A secondary market arises where one party trades to a second party data about a third party that is in its possession but that it neither acquired from the individual concerned nor created. The longstanding term `surveillance society' (Lyon 1994) has been joined by `surveillance economy' (Davies 1997, Hirst 2013), as a means of conveying how the `direct marketing' mechanisms of two to five decades ago have developed into heavy reliance by corporations on the acquisition of detailed electronic dossiers of information on large numbers of individuals, through any and all of the three market categories identified above.
In the first of these three kinds of markets, individuals are participants. In the other two, however, individuals are not involved in the trafficking of data that relates to them. The term `usees' is usefully applied to individuals who are not themselves `users' of a system, but who are affected by it, as occurs with indirect primary and secondary personal data markets (Clarke 1992).
In principle, in most civilised countries of the world, data that relates to an identifiable person is subject to considerable constraints. Greenleaf (2014, 2015) documents the 109 countries with laws in place in January 2015, and the 102 without - of which 13 had Bills before their Parliament. The most economically and politically significant country that had no significant data protection law at all in place at the time was the PRC, with the only other large countries on the list being Egypt, Indonesia, Iran, Saudi Arabia and Sri Lanka.
There are many important qualifications to the bland statement about a country having laws in place. Of particular importance is the USA, which is a renegade in these matters in that, rather than having a generic data protection law, it has hundreds of laws in multiple jurisdictions that relate to specific contexts, most of them partial and very weak (Smith 2013). The significance of US law arises from the country's dynamism in the electronic commerce space generally, the dominance of US-based corporations in the practice of personal data collection, expropriation and exchange, and the tendency for other countries to accept the practices of US corporations, even where these breach local law.
Even in the countries with the strongest protections, generally across Europe but also in distant jurisdictions such as Hong Kong, New Zealand and South Korea, there are large numbers of exemptions and exceptions within the data protection statute, and large numbers of separate legal authorisations in other statutes, which are designed to override or create loopholes in the generic law. Moreover, in many countries the provisions relating to consent, given by the person to whom the data relates, permitting trading in their personal data, are highly unclear and as yet unchallenged, or permit token rather than substantive consent. For an analysis of the elements of meaningful consent, see Clarke (2002b).
As a result of the weakness of data protection laws, circumstances arise in which legal protections fall far short of public expectations. This gives rise to personal concerns and unresolved public policy issues, which in turn represent risk factors for corporations and government agencies that handle personal data. Analyses of personal data markets accordingly need to reflect not only the characteristics that they inherit from markets generally, and of the manner in which personal data comes to be available for trading, but also a wide range of legal, social and ethical factors .
Many people and institutions would seriously question the ethicality of research into effective electronic markets for slave-trading or human-trafficking, and the morality of individuals who conduct it. Where do the boundaries lie between ethical and unethical practices in research? This brief review of the notion of electronic markets as applied to personal data suggests that there are also grounds for doubting the legitimacy of personal data markets as they are currently conceived. At the very least, it is essential that discussions about personal data markets take into account the issues arising in relation to the participation or otherwise of the individuals whose data is the subject of trading, trust in the tradeable item, the legitimacy of trading it, trust in the organisations conducting the trading, and the legitimacy of each of the various actions that might be taken with the data once it has been acquired.
This paper's primary purpose is to assess published research in relation to personal data markets. The approach adopted was to examine the perspective adopted by researchers as evidences by their published articles. As researcher perspective is not yet an established element in discussions of research methods, it is necessary to provide an overview of the concept and an indication of its significance.
A key point of difference that was brought to IS research by interpretivism is that "the phenomenon of interest [is] examined ... from the perspective of the participants" (Orlikowski & Baroudi 1991 p.5). However, this is better expressed as 'from the [plural] perspectives of the participants', in order to avoid the implication that all participants share the same view. This has enabled the rigour of what is commonly referred to as 'positivist' research to be complemented by work that achieves greater insights, particularly in contexts that involve multiple participants with conflicting interests.
Very little of discussion has been located of the extent to which the idea of 'the perspectives of the participants' affects the conduct of research. This author has argued in Clarke (2015, 2016) that:
In each research project, at least one 'researcher perspective' is adopted, whether expressly or implicitly, and whether consciously or unconsciously.
The researcher perspective influences the conception of the research and the formulation of the research questions, and hence the research design, the analysis and the results.
Each particular perspective is specific, not universal.
Because the interpretation of phenomena depends on the perspective adopted, the adoption of any single researcher perspective creates a considerable risk of drawing inappropriate conclusions.
The notion of researcher perspective is distinct from the concepts of object of study and unit of study: a researcher observes phenomena (object of study) at a particular level of granularity (unit of study) utilising a body of theory (through a lens), but from a particular viewpoint (researcher perspective).
One way to distinguish alternative researcher perspectives is on the basis of the dimension on which they lie. The economic dimension is concerned with resource allocation. The largest economic players are joint-stock companies / corporations - an artefact conceived for that purpose in the 13th century, developed through the following centuries, and further articulated in the 19th century - together with the executive arm of government, acting through individual government agencies. In addition to such organisations, individuals are also economic actors - as consumers, employees, sub-contractors and unincorporated enterprises.
The social dimension is concerned with the activities of individuals in their other capacities - as citizens and members of unincorporated groups, communities, incorporated associations and societies. The environmental dimension comprises such viewpoints as those of local ecologies, the biosphere and the troposphere.
It is common for IS researchers to adopt the perspective of a participant in an information system - particularly the companies that are connected to it, but sometimes the employees or customers of those companies who use it. However, the concept of researcher perspective also extends to non-participating parties who are affected by the information system, such as the families of employees, people who live in the vicinity of a plant or campus that depends on the system, and the people whose data is stored in it. As discussed earlier, a person in the last of those categories - such as those whose data is in tenancy databases, consumer credit bureaux, mailing lists and criminal intelligence collections - is a 'usee'.
The term 'stakeholder' is often used in relation to information systems. It may be used so as to refer only to those participants in a system that have significant market or institutional power, and whose concerns about, and particularly opposition to, an initiative could be expected to undermine the likelihood of adoption and achievement of the project's aims. The earlier discussion about ethicality in research suggests that limiting stakeholders to only those with such power is problematical. The term `stakeholder' properly encompasses all participant and usee categories. In the case of personal data systems, this includes the individuals to whom the data relates.
A particular participant that features prominently in IS research is referred to by this author as 'the system sponsor'. By that term is meant the organisation that develops, implements or adapts a system, process or intervention, or for whose benefit the initiative is undertaken. In some cases, the system sponsor may be a cluster or category of organisations.
Research conducted to date provides evidence of a strong bias in IS research towards the economic dimension, towards single-perspective research, and towards the system sponsor's perspective (Clarke 2015, 2016).
Single-perspective research is straightforward to undertake. However, better quality results may be achieved in other ways. For example, dual-perspective research (e.g. considering the interests of both an employer and its employees, or of both the seller and buyer sides of a market) may enable each stakeholder to better understand the attitudes and needs of the other. Moreover, some forms of research cannot be undertaken without adopting a multi-perspective approach. For example, highly integrated industries such as automotive manufacturing and international trade depend on complex, multi-participant systems. Effective understanding of, and guidance for the design of, such systems simply cannot be achieved other than by means of multi-perspective research (Wrigley et al. 1994, Cameron & Clarke 1996, Cameron 2007).
The motivation for this paper was the discomfort felt by the author on reading the papers in the Special Issue on Personal Data Markets in EM 25, 2 (June 2015). The purpose of the study that I undertook was to examine the perspectives adopted by researchers in the domain of personal data markets. I felt concern that, in common with findings in various IS venues (Clarke 2015, 2016), researchers may be confined to the economic dimension, to single-perspectiive research, and in particular to the perspective of the system sponsor.
A study of this nature is akin to literary criticism, that is to say the description, analysis and evaluation of published works (DHI 2003). Its function is to document and develop understanding about a genre, in this case the body of refereed papers on personal data markets.
It is common for researchers to recapitulate existing bodies of theory, in order to demonstrate that their own work reflects and builds on prior research. The primary approach adopted in `normal science', however, is to extend the existing body of work, by drawing inferences from it and devising empirical studies in order to investigate the extent to which the inferences hold, or by applying the existing theory in a new context, in order to see what insights it may offer. The purpose here is different. An ad hoc, a priori observation had been made suggesting a high degree of uniformity among papers within a particular genre - a uniformity that, if it exists, would be undesirable.
Analyses undertaken of several samples from the information systems literature have provided confirmation that a high degree of uniformity exists in each of the samples, and probably exists in the sampling frames and in the population. This study applies the same analytical technique, but to the relevant genre. The importance of this study is that, if the a priori observation is confirmed, then serious weaknesses exist in the genre, which need to be addressed. The initial research question was framed as:
What researcher perspectives are evident in the Special Issue 25, 2 (June 2015) on `Personal Data Markets'?
The process used for textual analysis in prior studies was refined and applied to the six papers. This involves, for each paper, the extraction of all passages that are indicative of the researcher perspective, and of whether the perspective is on the economic, social or environmental dimension. Experience to date shows that the perspective is seldom explicit, and that it generally needs to be inferred. The process description is provided in the Supplementary Materials. The results are presented in section 5.
The findings were that the papers were indeed very strongly committed to the economic dimension and to a single perspective, that of the system sponsor. The scope of the analysis was then extended to the full corpus of papers in the journal that are relevant to the topic of personal data markets - about 25 further papers, with the second research question framed as:
What researcher perspectives are evident in other papers relevant to `Personal Data Markets' published in the journal Electronic Markets?
The textual analysis process and coding protocol used in previous studies was applied. The results are presented in section 6. Once again, the system-sponsor perspective was dominant.
It is clearly problematical that a genre that is concerned with the inherently multi-participant context of `markets' comprises studies that treat the interests of one participant as objectives, and the interests of others as merely constraints on the achievement of that participant's aims. This is of even greater concern in the case of markets in personal data, because privacy is an important social value, information systems professional codes recognise the primacy of the public interest, and individuals generally suffer from both information asymmetry and a lack of power in comparison with corporations and government agencies and hence their needs are likely to be inadequately reflected in system designs.
This gave rise to the question as to whether the pathological symptoms evident in the papers in the Special Issue and the journal as a whole are mainstream within the Information Systems literature, and possibly derived from some common source. The scope of the study was accordingly extended to the literature that appears to have shaped the attitudes and approaches of the researchers who have submitted to the Electronic Markets journal. The third research question was framed as:
What sources appear to have been significant influences in the narrow researcher perspectives evident in `Personal Data Markets' research published in the journal Electronic Markets?
This segment of the study adopted a series of search strategies designed to identify key references underlying prevailing attitudes to individuals' privacy interests and the interplay between those interests and the processes of business and government. The search strategies and the findings are reported in section 7.
This section evaluates the papers in the Special Issue on Personal Data Markets in EM 25, 2 (June 2015), on the basis of the preceding discussions of electronic markets, researcher perspective and research method.
The Special Issue comprises four contributed papers and one identified in the heading as an invited paper, complemented by a Position Paper by the Issue Editors. The papers are preceded by a Preface by the Issue Editors. This section first considers, in order, the Preface and the five papers, and then the Issue Editors' Position Paper. A comprehensive list of the relevant passages in each paper is provided in the Supplementary Materials.
The Preface to the Special Issue (Spiekermann et al. 2015a) notes that the Issue "is placed at the intersection of [the] seemingly opposing poles of privacy and personal data markets". The Editors ask about "the legitimacy and ethicality of [relevant] business models". They seek "attempt to provide insights into ... ways to manage and protect privacy within those markets". In terms of the discussion in the previous section, the Issue Editors therefore appear to have at least sought, and perhaps even to have assembled, a group of papers that take into account the social as well as the economic dimension, and that seek to balance the perspectives of the buyers of personal data with the perspectives of the individuals to whom the data relates.
The first paper, Roeber et al. (2015), builds on a stream of research associated with Acquisti & Gross (2006), by applying conjoint analysis as a means of evaluating how much (or, more relevantly, how little) consumers appear to value their data when offered money for it. This paper, in common with its predecessors in the area, is entirely dedicated to producing "insights for private and public institutions" and identifying "implications that are relevant for organizations and policy makers" (p. 105). The individuals whose data is being traded are recognised as an object of study; but their interests are relevant only because of their impact on the interests of the corporations trading in the data, and implications and insights for consumers are not in focus. The manipulative nature of the work is underlined by the authors' motivation, which is to "increase consumers' willingness to share their daa" (p.95). There are potential benefits for consumers in "[data] minimization through anonymization" and in a recommendation to "increase the choices [buyers] offer consumers", but a throwaway comment at the end of the article ("more beneficial for organizations and consumers alike" - p.105) does very little to diminish the strong emphasis on the interests of data-acquirers.
Gkatzelis et al. (2005) aim to "identify the optimal way to bundle demand so as to minimize the expected payment to a risk averse seller" (p. 110). As with the first paper, these authors are also embedded in a stream of research that is entirely manipulative of consumer behaviour, aimed at achieving consent by a person to the use of private data for the cheapest possible price - "so as to minimize the expected payment to a risk averse seller" (p.110). The authors' targets expressly include not only sensitive data about viewing habits, but also highly sensitive data gathered by hospitals for the purpose of medical treatment. No consideration is given to the interests of the consumers whose data the techniques are intended to enveigle out of their control: in the authors' words, "we approach this problem from the market maker's perspective" (p.111). It is particularly noteworthy that the literature on which the authors draw is not from the consumer marketing discipline, which might be expected to exhibit an inherent bias to the interests of marketers. Rather the cited papers are from various parts of the computing literature. The authors mention in passing that they are considering "a scenario where buyers pay for access to raw anonymized data" (p. 110). However, they assume away re-identifiability, and expressly exclude the approach of adding unbiased noise to the data-set. Given the intensity of the health care data that is of central interest to such techniques, the assumption that the data is anonymous is unwarranted.
The paper also implicitly assumes that all consumers have a price, and hence the very notion that some consumers wish to exercise a denial of consent appears to be outside the model. A more committed pro-corporate-purchaser / anti-consumer-seller/usee approach to research would be difficult to devise. This might not be grounds to reject the paper, but if the Editors were to carry through with their declared intention of seeking balance between the perspectives of buyers and sellers, then it was essential that they either required the authors to incorporate consideration of the interests of consumers, or drew attention in the Preface to the paper's one-sidedness.
Heimbach et al. (2015) is addressed to "developers of product recommenders" (p.137). The paper proposes and evaluates the priming of recommender systems using personal data acquired from Facebook profile data. The authors blithely assume that every online merchant's web-site "has access to rather rich, complete and up-to-date data which users provide voluntarily and implicitly" (p. 127). That assumption is not only ethically inappropriate - because the users were merely logging into the shop using their Facebook account, and very few would have contemplated the wholesale use of all of their Facebook data by the merchant - but the assumption is very probably also wrong at law, perhaps even in the highly permissive US context. Again, the large majority of the stream of research on which the work builds is in the computing disciplines, and it is almost entirely devoid of knowledge of or concern about consumer interests, to the extent of ignoring consumer protection laws. The sole indication of any recognition by the authors that consumers' interests may be relevant is their statement that "the [experimental] subjects ... participated voluntarily but may refrain from using the system in a real setting" (p.137) - but once again the interests that drive the discussion are those of the system sponsor in achieving paticipation by consumers. The authors deny consumer privacy, and yet they suppress the name of "the world's largest mail order company (anonymous for confidentiality reasons)" (p.126), without appearing to notice the irony of doing so.
Rayna et al. (2015) presents a mathematical analysis that evaluates the effects of 'first-degree price discrimination' for digital music, by which is meant a different price for each consumer, based on perfect knowledge by the seller of each consumer's willingness to pay. It makes the bold claim that this would be "mutually advantageous and both buyers and sellers gain" (p.139). However, the authors' notion of mutuality is based not on the interests of the consumers themselves, but on the economic concept of `social welfare', and the primary interests that the paper reflects are those of the corporation selling access to music. Moreover, the presumption is made that perfect knowledge by the seller is achievable (by making consumers disclose or provide access to personal data), whereas the consumer-buyer does not need to know anything about the corporation-seller, let alone have perfect knowledge. The purpose of the technique is "to mitigate the effects of consumer piracy and, potentially, to increase revenues in the music industry" (p.140), and "to monetize the 'long tail'" (p.143). As with the previous papers, data disclosure is inherent: "first-degree price discrimination requires consumers to disclose information that would, otherwise, remain hidden" (p.140), and the scheme requires that "exhaustive personal data [are] collected" (Fig.2, p.144). Consumers are untrustworthy: "consumers could ... attempt to manipulate personal data collected" (p.140), and hence measures are needed to overcome such cheating; whereas no consideration is given as to whether controls might be also needed in relation to unfair actions by the monopoly music-provider. As an afterthought, the authors mention that "It could also be worthwhile considering what happens if consumers 'dislike' being monitored" (p.152). Researchers more out-of-touch with the interests (and, to some degree at least, also the sentiments) of consumers, and a market design more biassed to the interests of one side of the market than this notion is difficult to imagine.
The fifth paper in the Special Issue, which is declared in the paper's heading to be invited rather than contributed, is Maguire et al. (2015). This outlines "an interoperable context-aware metadata-based architecture that allows permissions and policies to be bound to data". This bears more than a passing resemblance to the original conception of what became the Platform for Preferences (P3P), a W3C initiative of 1997-2003. P3P failed because it was reduced from a two-sided architecture to a mere channel for publishing policies (Clarke 2001). On the one hand, it might seem ironic that the reduction in scope was a result of interference with the design by a few large corporate members of W3C, including Microsoft - who are the employers of the authors. On the other hand, the neutering of the architecture is sustained by the authors' proposal. Even if their proposal were implemented, it would merely create the capability for "user permissions and policies [to] be permanently associated with data, enabling any entity to handle that data in a way that is consistent with a user's wishes" (p. 155). In other words, it would enable the publishing of consumers' policies, but it would not in any way enforce the consents and denials that the metadata contains. The model embodies no technical protections, but instead flick-passes that aspect to 'principles' and 'trust frameworks'. So it fails just as badly as P3P did.
A further feature is that "policies [would be] set by data controllers, users, third parties, and regulators" (p. 158). The individuals to whom the data relates are a highly significant omission from the list. The text does at one point contemplate individuals setting policies in relation to personal data: "the subjects in the picture may have rights over when and where the picture can be shown" (p.158). But this appears only in "a simple example", and not in the architectural specification. The reasonable inference is that the envisaged" dialog among all major stakeholders in the data ecosystem" (p.155) excludes the categories of individuals whose data is being traded.
The claim is made that the proposal would "provide value to all participants in the ecosystem" (p.155), but unfortunately, it is unclear how consumers would benefit. The benefits that the authors identify are that it would "enable data - including personal data - to flow, be analyzed, and be exchanged freely" (p.155), it would enable "data flows across the trust boundaries of multiple entities" (p.159), it would "drive new business models and innovation" (p.160), and it would "help satisfy the interests of regulators, users, and industry " (p.160). The benefits are all for organisational participants. The individuals to whom the data refers, whether they are sellers or usees, are signally missing from the objective function.
From an academic viewpoint, the paper also fails to reflect important contributions in the area, which at least potentially go well beyond mere policy publication and embody enforcement. For example, Barth et al. (2006) provides a formal model of Nissenbaum's 'contextual integrity' conceptualisation of privacy protection. If this model were to be implemented in such a manner that both an express denial of consent and an implicit failure to provide consent prevent disclosure and use of personal data, then it would go well beyond the weak Maguire / Microsoft approach. Similarly, Riederer at al. (2011) proposed "a mechanism called Transactional Privacy (TP) that enables release of portions of PII by end-users (on a strictly opt-in basis) to information aggregators for adequate monetary compensation" (emphasis added). Their design principles: were "(i) users should have control of their PII and decide what gets released, (ii) aggregators should be able to derive maximum utility of the data they obtain, and (iii) aggregators are best positioned to price the value of users' PII" (emphasis added). The Riederer model remains biassed towards the interests of the (corporate) buyers, but it empowers the consumer, it embodies enforcement, and it enables choice based on an buyer's offer. The designs arising from the EnCoRe project also included a "Privacy-Aware Access Control Policy Enforcement component" whose function was "enforcing security & privacy access control policies on personal data, driven by data subjects' preferences" Whitley 2013, p.172).
The Maguire et al. proposal is yet another pseudo-protection that avoids harming business interests by avoiding any effective empowerment of consumers. The authors have reflected the interests of the corporate side of the market by proposing a trust-inducing measure, but have failed to serve the needs of the consumer side of the market and even to reflect the existing literature. This paper too is emphatically on the economic dimension, it adopts a single perspective , and the perspective is that of the system sponsor.
The narrowness of the five papers in the Special Issue is striking. The journal's focus is 'Electronic Markets'; and the Call for Papers related to 'Personal Data Markets', and the Call was very broad in its scope (EM 2013). The Call mentioned 25 specific topics, but 4 of the 5 papers are exclusively concerned with price discovery, and hence address just 2 of the 25: 'Valuation of personal data' and 'Behavioral studies of trade-offs in personal data disclosure'. The researcher perspective evident in all five of them is that of one side of the market. The would-be buyers of sensitive personal data are actively advantaged, not just to the almost complete exclusion of the interests of the other side - the individuals whose data corporations lust after - but to their significant detriment.
The analysis of the five papers in the Special Issue concludes that the aspirations that were evident in the Preface (Spiekermann et al. 2015a) have not been fulfilled. On the contrary, there are serious doubts about "the legitimacy and ethicality of" the approaches adopted; and, far from offering "ways to manage and protect privacy within those markets", the papers in fact investigate ways to buy off privacy concerns for minimum cost to the buyers.
The final paper in the Special Issue is a Position Paper by the Issue Editors (Spiekermann et al. 2015b). As might be expected from leaders in the field, this paper evidences vastly greater awareness of the issues raised in this paper. The Issue Editors' intention is to outline "some of the economic, technical, social, and ethical issues associated with personal data markets, focusing on the privacy challenges they raise" (p. 161).
However, the Position Paper also embodies some of the key problems that the researcher perspective analysis exposed. The paper is strongly oriented towards the needs of business and government. The paper is framed not in terms of balance between competing interests, but in terms of 'privacy challenges': "We ... highlight the major questions that market players and policy makers will arguably need to face in handling [personal data] markets" (p.162), and "The challenge is how to internalize ... privacy externalities so that the data subject can be fairly compensated" (p.161). The conclusion is that "Our position ... is that companies, which hold customer relationships should go back to more trustworthy relationships with their customers" (p.165, emphases added). The researcher perspective in all of these key quotations is unequivocally that of the organisations that participate in markets, with the interests of individuals - even where they are themselves market-players-relegated to constraints on the interests of corporate players.
The paper notes that "Thought leaders have proposed whole new market structures and business models that may allow consumers to get into the driver's seat for their personal data (Searls 2012; Hamlin 2013)" (p.162), acknowledges negative effects on society of "the mere existence of personal data markets" (p. 163), mentions "social cohesion, equality of opportunity, freedom, and democracy" (p.163), and includes a 3/4-page segment considering the concerns of individuals (pp.164-165). However, these are presented as 'challenges' to business, not as a means of addressing the needs of individuals, nor as a way of shifting research from a system-sponsor orientation to a dual-or multi-perspective approach.
Even where a statement is made about self-management, it falls short of the care, insight and precision with which the case for organisations is argued. A key passage is that "one can envisage interfaces that empower individuals to manage their personal data ..., ideally on their own trusted devices; this practice would establish a strong base for the user's digital identity" (p.164, emphasis added). This makes the assumption that self-management can be delivered by 'interfaces' rather than by architectures, designs, interoperable infrastructure, and hardware and software features; and it overlooks the critical need for people to have not one but many digital identities (Clarke 2004, 2009).
Further, the paper lacks recognition of the significance of data protection to the physical safety of many segments of society (GFW 2011). This dimension of privacy is becoming far more important than it was in the past because of the substantial recent developments in relation to promiscuity of personal data and location from handsets (Clarke 1999b, Dobson & Fisher 2003, Clarke & Wigan 2011, Michael & Clarke 2013), and the loudly-promised proliferation of eObjects that are intended to continually monitor individuals' behaviour, associations and movements (Weber 2010, Manwaring & Clarke 2015). Moreover, the single mention of 'democracy' fails to convey the impossibility of exercising political freedoms in a context in which surveillance of behaviour and experience are pervasive (Raab 1997, Gross 2004, Clarke 2008b).
The paper notes that "many consider privacy an inalienable right [but] data markets have developed in the opposite direction" (p.162). This fails to confront the crucial facts that the 'inalienable right' is embodied in an international convention that has been ratified by 175 nations, and acceded to by 94 of them, representing the large majority of the world's population (ICCPR 1966), and that scores of countries have embedded these rights at least in legislation, and in many cases in their constitutions. The problem goes even deeper, however, in that the breaches committed by organisations are glossed over, by referring to "legal grey zones", "enforcement gaps" and "regulatory arbitrage", which give the appearance of mere playfulness rather than the corporate misbehaviour and in some cases outright illegality that it actually is.
The paper recognises that "Interpreting personal data as a tradable good raises ethical concerns about whether people's lives, materialized in their data traces, should be property at all" (p. 164). On the other hand, the discussion continually reverts to the paper's dominant theme of 'data as property', and the emphasis on how people's reticence can be overcome, and how people can be made to put a price on access to their data - all to meet the desires of corporations, irrespective of the needs and desires of people. The Position Paper to some degree recovers the gross imbalance of the Special Issue, but it too is strongly committed to the perspective of traders, it evidences too little investment in representing the interests of consumers and usees, and it missed the opportunity to draw to attention and to dispute the one-sidedness of the research reported on in the five papers falls far short of the need.
Note that the evaluation in undertaken in this study has not assessed whether or not the six papers in the Special Issue contain any value for privacy. Of course there are aspects of some of the papers, and especially of the Position Paper, that include recognition of the interests of individuals, and positive implications for individuals. The evaluation, however, has addressed this research question:
What researcher perspectives are evident in the Special Issue of the journal Electronic Markets on 'Personal Data Markets'?
The conclusion is that all of the six papers are on the economic dimension, five are strongly single-perspective and fully committed to the interests of system sponsors, to the almost complete exclusion of the interests of other players in personal data markets. The sixth, the editors' Position Paper, is far more nuanced, and brings a degree of balance by considering the interests of consumers, and arguing that designers should do so as well. On the other hand, the paper is very clearly addressed to organisations, it frames consumers' concerns as 'challenges' to organisations, and it is positively and pleasantly expressed. rather than communicating concerns about, or disputes with, the other five papers.
Given the serious problems that the above analysis detects in the Special Issue, it became important to consider the extent to which the concerns are specific to those papers, or are common to the whole corpus of relevant works in the journal.
The Journal Editor's own Editorial at the beginning of the Special Issue provides an analysis of past articles in EM relevant to personal data markets (Alt et al. 2015). EM has published c. 750 papers to date. The Editorial identified 25 articles published between 2001 and 2014 that dealt with "the relationship between trust and privacy" (p.88). Together with the six in the Special Issue, this provided a pool of 31 papers. One article was discarded from the set because it was not relevant to the topic-area of personal data markets and privacy. That left 30 articles for consideration. These were assessed in order to identify the perspective(s) that they adopted. The articles were coded in accordance with the same protocol as has been applied to articles published in a range of other venues (Clarke 2015, 2016). The process description, the coding protocol and the coded data for the 30 papers are provided in the Supplementary Materials.
Of the 30 papers, 8 were only marginally relevant, in that they related to the very narrow sense of the term 'privacy' used by some authors in the computer science discipline, whereby it is a synonym for 'confidentiality' within the CIA model - a concept that is better described as 'non-disclosure'. The pool was accordingly divided into two sub-pools of 22 and 8 papers.
In 4 of the core 22 articles, and 7 of the 8 fringe articles, organisations were examined. In the remaining 18 and 1 articles, the Object of Study was people.
The perspectives in all 30 articles were on the Economic dimension. This may seem curious, given that a social value, privacy, was central to the field of view. The reason is that, in 20 of the 22 core (and arguably even in the other 2 as well), and in all 8 of the other articles, the Perspective was tightly focussed on the financial interests of corporations.
The 2 exceptions that were coded as being Multi-Perspective declared that the interests being served were respectively "sellers (individuals) and buyers (corporations)" and "music firms and music consumers". Both were concerned with models for pricing data, and inherently assumed that privacy is a merely economic right, that personal data is traded, and that individuals have little or no option in regard to the trading of their data, but that they may have some choice in relation to how much and at what price. Moreover, one of the articles investigated protections for corporations against consumers who cheated, but not protections for consumers against corporations that cheated. Hence the 2 articles were, in effect, strongly oriented towards the interests of corporations, with some acknowledgement of consumers' economic interests, but not at all of their social interests.
The researcher perspective adopted in all 30 articles was that of the system-sponsor, in only 2 was any other perspective considered, and in both cases it was secondary to that of the system-sponsor.
Closer attention was warranted to the majority of the articles (18/22 and 1/8) that studied humans from the system-sponsor's perspective. The following quotations from some of those papers are indicative of their tone (emphases added):
"The objective of this study is to examine the effectiveness of three vendor strategies ... "
"[P]ersonalization can be a successful marketing strategy in some types of website only ... [P]erceived usefulness of personalization is a significant factor in attracting new users. Thus, it is worthwhile for firms to invest in data mining to analyse the transaction patterns among like-minded people"
"[B]y empowering consumers to control their private information, a firm may be able to create a competitive advantage by increasing customer trust"
"Companies need to care for consumer concerns regarding their Privacy and the use of RFID"
"LBS service providers should continue to allay customer's privacy concerns"
"e-[V]endors should give priority to the incorporation of systems on their web sites that guarantee privacy and security in the purchase process because it directly [and indirectly] affects e-trust"
"Privacy implications and information confidentiality issues are threatening the wide diffusion of business networking and online collaboration paradigms"
"Developers of product recommenders based on Facebook profile data need to carefully analyze [specific aspects of the data]"
There are several aspects of the papers that have potential benefits for consumer privacy; but that is only a secondary concern of the analysis conducted in this paper, whose focus is 'researcher perspective'. The texts are, without exception, addressed to system-sponsors. In no case are any implications of the research framed in a manner that addresses the interests of the individuals who were the object of study, despite many opportunities to do so.
For example, the research question "Why do online SNS [social networking services] users continue to use these websites?" could very easily have drawn implications for consumers, as well as for corporations, such as 'the following categories of people may be subject to specific threats rather than mere generalised fears: ...', and 'users who are concerned about the intrusiveness of an SNS need to familiarise themselves with, and take advantage of, the following features: ...'.
Similarly, research on "What are the effects of privacy concerns and personal innovativeness on customers' adoption of LBS [location based services]?" could have communicated to consumers the categories of individual who are rationally concerned about disclosure of location, the measures that are available to address the risks, and examples of products that do and do not match to the needs of the vulnerable.
The fact that the 30 articles in EM that have been relevant to 'personal data markets' were entirely committed to the interests of buyers (corporations) and marketspace operators (corporations), to the almost complete exclusion of sellers (consumers), represents strong evidence that a 20-year-old problem continues to exist. When Web Commerce was unleashed in 1994 (Clarke 2002), it was generally expected that take-up would be very rapid. It was not. The author has argued since the late 1990s that the very notion of 'Business-to-Consumer' (B2C) eCommerce was a major part of the problem (Clarke 1999a, 2006, 2008a). The problem is encapsulated in the '2'. A market supports the conduct of trade between sellers and buyers, and hence Business needs to conceive of itself as conducting eCommerce with Consumers, rather than 'to' or 'at' them. The adoption of '2' has led designers, operators and researchers up a blind alley, and the one-sidedness of papers published in EM is just one result of that intellectual blunder.
The conclusion from the analysis is that not merely the Special Issue, but the entire corpus of papers relevant to personal data markets that has to date appeared in EM, is solely on the economic dimension, is fully committed to the cause of corporations seeking to acquire and use personal data, and is concerned about the interests of other participants and usees only to the extent that they might have sufficient market power to harm the interests of data-exploiting corporations, and might exercise that power. It is not uncommon for authors to mention privacy, and even broader human rights, but the comments are throwaway lines, not central to the work.
Given the extreme narrowness that was fo9und in the two previous studies, the question arises as to whether the problems of a preponderance of single-perspective research, and an overly heavy commitment to the interests of systems sponsors, are generic, rather than specific to the 'personal data markets' genre. Are contributors to EM trapped into a disciplinary Weltanschauung dictated by the bodies of theory that have emerged over the last 50 years?
A third research question was accordingly framed as:
What sources appear to have been significant influences in the narroe researcher perspectives evident in 'personal data markets' research published in the journal Electronic Markets?
The first approach adopted was to extract the history of the 'personal data markets' field by examining the key citations in the papers in the Special Issue. It was expected that this would provide a back-trace to the bodies of theory that have led the authors into the cul de sac. That was unsuccessful, however, because the papers examined only very narrow topics within the personal data markets space.
The second approach was to conduct searches on Google and in the AIS eLibrary on <personal data/information markets>. This established that the term has not, or at least not yet, gained much traction, with only a few score papers using the term, none of them with large citation-counts. Novotny & Spiekermann (2013) also notes the paucity of papers on personal data markets that reflect the privacy need, citing only Laudon's 1996 version in CACM, Noam (1997), Schwartz (2004) and Aperjis & Norman (2012). It was therefore necessary to expand the search, using various combinations of terms such as <personal data/information>, <market> and <privacy>.
A review of "information privacy research" in IS is in Belanger & Crossler (2011). It does not mention 'personal data | information markets'. The 142 journal articles and 100 conference articles that it considered appear to be dominated by the MIS tradition. Some doubt exists about the sampling approach used. For example, the set contained a single one of this author's papers in the area, yet omitted half-a-dozen of the author's papers that are within the defined scope of "papers on information privacy in the ABI/Informs database" and that have a combined Google citation-count above 1,500. The papers in the sample are tightly focussed on the economic dimension, predominantly single-perspective in approach, and concerned with the system-sponsor perspective - in most cases with the interests of individuals considered as a constraint, not an objective. A faint hint of balance appears at one point in the paper: "Research could also take the form of an analysis of the dual perspective of the consumer and the web merchant, investigating the impacts of match or mismatch between the privacy preferences of the consumer and the merchant" (p. 1031), but the recognition of consumers' interests as being at the same level as organisations' interests promptly disappears back beneath the waves.
Smith et al. (2011) presents an alternative 'interdisciplinary' "review of [information] privacy-related research ... with a sample of 320 privacy articles and 128 books and book sections" (p. 989). It is also strongly oriented to the MIS sub-set of the IS discipline, and is highly US-centric, with few of the references, particularly in the foundation analysis, from other than North American authors. It considers privacy as a right, but does so without reference to the International Covenant on Civil and Political Rights (ICCPR) or to constitutional or legislative definitions of human rights. The authors write as though their audience comprises solely US academics, and call for more positivist empirical research to be undertaken. There is no discussion of researcher perspective, and no inkling of individuals as stakeholders. The authors appear to implicitly assume that the beneficiary of (M)IS research is system sponsors, not people.
Another article in the same Issue as the Smith review, Pavlou (2015), is quite blatantly biassed towards the economic and system-sponsor perspective: "markets for managing customer information have long been established with the primary purpose of managing personal information in optimal ways, and there is a rich body of research in IS economics that can further extend the literature on information privacy" (p. 985). The paper "directs readers to" Varian (1996) as a source of "fundamental economic principles".
In order to establish an appropriate basis for understanding the narrowness of the (M)IS Weltanschauung , a fresh approach to analysis appears to be necessary. A review of the history of privacy and data protection in relevant literatures was accordingly developed. It was anticipated that this might assist in making judgements about whether particular references or authors appear to be influential in the frame of reference used by researchers who publish in IS venues on topics within and adjacent to the personal data markets genre.
Contemporary theories, laws and practices in the area clearly derive from the work of Columbia University political economist Alan Westin (Westin 1967, 1971, Westin & Baker 1974). In those early years of personal data systems, the dominant school of thought, legitimised by Westin's publications, was that the invisible economic hand of business and government activity would ensure that IT did not result in excessive privacy invasion. Hence privacy regulation was unnecessary, or, to the extent that it was imposed, it was essential that the detrimental effects on business and government be minimised. The term 'Fair Information Practices' (FIP or FIPS) has been widely applied to this approach. Another influential work was the heavily economic interpretation of privacy advocated by Posner (1977).
As European countries moved to establish statutory protections for personal data, the US Administration adopted a countermeasure in international fora, in order to sustain the freedoms of its corporations to handle personal data with minimal constraints. This gave rise to the business-friendly OECD Data Protection Guidelines (OECD 1980). The corporate sector successfully used the FIPs notion to deflect the energy of legislators towards weak privacy regimes which legitimated dataveillance measures in return for some limited procedural protections (Rule 1974, Rule et al. 1980). The USA's light regulatory hand applies a model that is minimalist even by OECD/FIPS norms - commonly referred to as 'Notice, Choice, Access, and Security' - which is published and administered by the Federal Trade Commission (FTC).
The Westin/Posner lines of thought were combined and further articulated. The endeavour was made to reduce privacy from the human right declared in the ICCPR to a mere economic right. Laudon (1993) proposed that "market-based mechanisms based upon individual ownership of personal information and National Information Markets (NIM) where individuals can receive fair compensation for information about themselves" (pp. 2). The enormous scope that Laudon envisaged for the NIM was evident elsewhere in that paper: "MasterCard could use information on your credit history for the purpose of authorization of future MasterCard purchases, but it could not sell your history of credit card purchases directly to other institutions. [MasterCard] could however sell [your history of credit card purchases] on a National Information Market where it could be purchased by a credit bureau like TRW Credit Data who could then use the information for credit histories" (p.18, emphasis added).
Works by Hal Varian, particularly Varian (1996), directly supported the Westin-Posner-Laudon thesis. For the Internet era, the intellectual underpinnings of consumer-manipulative economics was provided by Shapiro & Varian (1999). This book defined 'loyalty' as a one-way relationship from consumer to provider, achieved through lock-in techniques based on deep knowledge of customers. Despite the deep intrusions into personal interests inherent in the proposals, the book does not even include the word 'privacy' in its 1000-entry index. The fourth paper in the EM Special Issue, Rayna et al. (2015), draws directly from Varian's business school economics.
The notion that 'personal data as personal property' in some way represents a solution to privacy problems - certainly for business, although very probably not for consumers - continually re-surfaces, including in influential books like Lessig's 'Code 2.0': "we could imagine an architecture, tied to a market ... It needs the push of law. The law would be a kind of property right in privacy" (Lessig 1999, p. 160). It is significant that the sole instance of a suitable privacy architecture that Lessig mentioned was P3P, which, even as he wrote, was already doomed to failure.
Further contributions in this line are Schwartz (2000, 2004) and Bergelson (2003). Schwartz (2004) "develops a model of propertized personal information". Schwartz argued that "other legal scholars have advocated propertization of personal information, ... generally without sufficient sensitivity to privacy concerns". Schwartz proposed "five critical elements ... that would help fashion a market that would respect individual privacy and help maintain a democratic order ... : limitations on an individual's right to alienate personal information; default rules that force disclosure of the terms of trade; a right of exit for participants in the market; the establishment of damages to deter market abuses; and institutions to police the personal information market and punish privacy violations" (p.2056, emphasis added). Despite its claims of being 'sensitive to privacy concerns', Schwartz's model is merely another avenue towards the objective that corporations desire. The 'right of exit' element is the US notion of 'opt-out', which is the antithesis of consumer empowerment through the necessity of consent - which in US parlance is deprecated as 'opt-in'. A more balanced policy contribution from the sociology discipline, Rule (2007), expresses serious concerns about the facilitation of such pseudo-consensual personal data access.
Even in 1996, when Laudon finally published his paper in Communications of the ACM, his view of propertisation of personal data had already been roundly rejected in Europe. The Data Protection Directive of the European Union (EU 1995) went well beyond the business-friendly / privacy-weak provisions of the OECD Guidelines of 1980. The formal protections it established (Simitis 1995) quickly spread across all EU countries. Meanwhile, Samuelson (2000) provided a polite but firm refutation of the propertisation arguments of Laudon, Varian and Lessig. Kang & Buchner (2004) identified four areas of contention in what they characterised as the economics-dignity debates: (1) what initial entitlements are assigned to which parties, (2) how is informed consent assured, (3) how are reasonable societal overrides to be decided upon, and (4) what legal apparatus is necessary to enforce the norms (pp. 27-28). A further, much-cited work that rejects economics as the lens through which privacy issues should be viewed is Solove (2006).
In a further endeavour to identify relevant influences on IS researchers, a scan was undertaken of the works of highly-cited IS researchers in the area of privacy and information systems. The orientation of the works of one author is summed up by the book-title 'Managing privacy: Information technology and corporate America' (Smith 1994). The most apparently consumer-friendly of another author's works, Culnan & Bies (2003), although it talks throughout about balance, remains constrained within the narrow sub-set of data privacy protections embodied in US FIP formulations such as FTC (2000). Indicative of the work of a third, Tamara Dinev, is this: "A systematic understanding of individuals' privacy concerns is of increasing importance as information technologies increasingly expand the ability for organizations to store, process, and exploit personal data" (Xu et al. 2008). These influential authors consistently treat individuals as objects of study not stakeholders, and individuals' interests as constraints not objectives.
An important genre that adopts the perspective of consumers is that dealing with Privacy-Enhancing Technologies (PETs). However. this is primarily in the adjacent computer science literature, and appears to have had limited impact in the IS literature. In Narayanan et al. (2012) the failure of 'Decentralized Personal Data Architectures' to achieve traction is examined. By that term they means approaches such as personal data stores, intermediation, distributed databases, peer-to-peer overlay networks and mesh/edge networks. The authors identify a range of technical and economic challenges. A similar analysis focussing on social media services is in Clarke (2014). Because decentralised architectures represent a means of giving data subjects a degree of market power in their transactions with corporations, it is unsurprising that they have attracted little in the way of corporate investment, and none have achieved critical mass.
In the AIS eLibrary, a total of 2 (out of 30,000) papers contain <"personal data | information market">. Both were co-authored by one of the co-editors of the EM Special Issue - Spiekermann et al. (2012) and Novotny & Spiekermann (2013). Of the two papers, the second is the more significant for the present discussion. Recognising the need for "an innovative information-rich world while maintaining privacy", the authors propose "a 3-tier information market model ... to empower people as much as companies", which enables personal data to be "used and traded', but lets "[people] control their information and identities. ... In our model, company obligations vis-á-vis consumers are enforced by the law and supported through privacy" (pp.1635-1637, emphasis added). This paper is one of very few found in the AIS eLibrary that adopts he consumer's perspective. The vast majority of relevant papers are strongly US-centric, and wedded to the system-sponsor perspective.
Opening the search in the AIS eLibrary out to <market AND ("personal data" OR "personal information")> extends the catch from 2 to 25 papers. However, many of the 23 are of very marginal relevance, or investigate aspects of consumers' trading-off between the privacy value and monetary rewards, or serve the interests of corporations that are seeking to extract pseudo-consents or cheap deals from consumers, and contribute little to market design. The paper of most apparent relevance, van den Broek & van Veenstra (2015), compares personal data markets with other 'governance processes' for inter-organisational data sharing. It is solely concerned with what was described above as secondary personal data markets, and it completely excludes the interests of the individuals/usees whose data is being trafficked. It also assumes an intellectual property basis for both markets and bazaars - despite this being clearly an inappropriate assumption in the case of personal data. The paper does not treat privacy as a requirement. It is merely a business risk and a constraint on achieving the grand promise of the marketing catch-phrase of the moment: "Whereas European data protection legislation requires data minimisation, big data is based on the notion of data maximisation" (p. 10).
There are, of course, many other papers in the AIS eLibrary that include "privacy" and "personal data/information". Most of these, however, are also strongly economic in orientation, and single-mindedly committed to the system-sponsor perspective. However, a recent, valuable contribution that has the capacity to open personal data markets research out into more promising avenues is Hauff et al. (2015).
There are other, related literatures, such as that on the cost to corporations of privacy breaches, e.g. Acquisti et al. (2006), Clarke (2016). There is also a small legal literature that tries to apply the awkward notion of 'markets for information privacy', e.g. Nehf (2005). The primary theoretical frame of reference of the published works to date on personal data markets appears, however, to be the Westin-Posner-Laudon-Varian line of argument, which values corporate freedoms over privacy, and attempts to reduce privacy from a human right to a mere tradable item.
In an extension to the studies of researcher perspective undertaken to date, the author is currently examining a longitudinal sample of papers in the IS `basket of 8' journal s. A further variant of that project is being considered, which would gather a sufficient sample of papers that involve privacy issues, and hence develop a deeper understanding of the orientations that researchers who publish in those venues are bringing to their analyses.
The author's contention is that inadequate diversity in researcher perspectives is a seriously inappropriate characteristic of an academic discipline. Historians who re-write history for dictators are pilloried. Laboratory scientists who falsify data or results in order to serve the needs of a client are dismissed from academe. Conducting research single-mindedly for system sponsors, to the detriment of other participants and of non-participant 'usees' affected by systems, bears an uncomfortable resemblance to such behaviour.
Because markets are an instrument of specifically economic behaviour, it could be seen as only natural that articles published in the Electronic Markets journal are almost all on the economic dimension - and, in the small sub-set that was relevant to this analysis, exclusively so. On the other hand, markets of all kinds have environmental implications, and the discipline needs to give at least some degree of consideration to that dimension. An 'environmental sustainability' literature exists, but in that genre environmental factors are merely constraints, and the objective continues to be the wellbeing of business.
Of even greater significance and importance are markets' social implications. With the last 50 years of decline in the power of governments relative to corporations, and the dominance of neo-classical economic thought, a strong momentum has been achieved towards imposing markets on a great many activities that were previously perceived to be social in nature. The privatisation of national infrastructure such as telecommunications, water, roads, railways and ports has been followed by prisons, hospitals, clinics, education at tertiary, secondary, primary and pre-school levels, aged care, support for the disabled, and even security and private military corporations (PMC) that go beyond support services and training almost to the level of outsourced military operations. The social dimension has arguably become a very significant aspect of electronic as of other markets. Yet, despite the significance of the social dimension, the corpus of works published in EM on personal data markets, shows no recognition of the need to go beyond the economic dimension.
Even within the economic dimension, many perspectives are capable of being adopted. The nature of markets is such that its participants comprise as a minimum one or more sellers and one or more buyers. Intermediated marketspaces have advantages in effectiveness and efficiency and hence many markets feature marketspace operators. A variety of service-providers may be closely associated, in particular for logistics, finance and insurance. Each of these stakeholders needs enough researchers to adopt their particular perspective, enough of the time, not necessarily exclusively, but in a manner that equally weights their interests with those of other stakeholders.
In some electronic markets, regulators have direct roles to play, as occurs for example with embedded monitoring of stock exchange transactions. The Porter model of corporate strategy that has dominated strategy theory for three decades (Clarke 1994) has always lacked, or preferred to ignore, the role of regulators and of law. Unbounded profit-seeking behaviour has very substantial side-effects, far more serious for society and the polity than is conveyed by the anodyne economic concepts of 'externalities' and 'market failure'. As a result, many forms of electronic market also need to be viewed through the eyes of regulators and public policy makers, and none more so than personal data markets.
The application of the researcher perspective notion to electronic markets suggests that:
All of the above categories of research are particularly relevant to personal data markets. In primary markets, in which individuals themselves are sellers, the dual-perspective approach (sellers and buyers) and triple-perspective approach (sellers, marketspace operator and buyers) are especially important, because of the imbalances of information and power. In the other two categories of personal data markets, in which organisations trade data about individuals, it is vital that single-perspective studies also be undertaken from the viewpoint of the people to whom the data relate - non-participant usees. Further, multi-perspective research intended to inform public policy processes must be defined to be within-scope of personal data markets research, of electronic markets research more generally, and of the IS discipline as a whole.
The declared scope of the EM journal is sufficiently broad to encompass all of the approaches discussed above. The Call for Papers for the Special Issue was also very comprehensive. The serious weakness lies in the papers that were submitted, not only to the Special Issue but also to the journal over an extended period. This appears to reflect a malaise within the IS research profession, whereby not only US Business School academics but also most European researchers have been drawn into the vortex, and have come to perceive IS as merely serving the interests of organisations, and particularly business enterprises.
The current genre of personal data markets research is ineffective, even in its own terms. Much better services would be provided to corporations if researchers adopted dual- and multi-perspective approaches to research, and developed genuine understanding of the various stakeholders' interests and needs, rather than playing laboratory games intended to minimise the cost to business of enveigling consumers into trading their privacy off for convenience or a small amount of money.
Beyond that, however, the current genre of personal data markets research is ethically very dubious. The large majority of research actively and wilfully ignores the interests even of participants other than the system sponsor, let alone the interests of people who are non-participants but who are affected by the system. To the extent that researchers are also IS professionals, they are in breach of their obligations under professional bodies' Codes of Ethics. They only escape being in breach of obligations under the Code of Research Conduct of the academic Association for Information Systems (AIS) because that body has yet to grasp the nettle and extend its coverage to the protection of people other than its own members.
The dominance of the system-sponsor perspective in IS research is so great that the argument pursued here might well be regarded as 'beyond the pale', an outlier and even extremist view, and a call in the wilderness. US Business Schools successfully use excusatory movements as a form of camouflage for the consumer-exploitative techniques that they teach and research - in recent decades under such mottos as 'business ethics' and 'corporate social responsibility'.
The IS research community can readily hitch itself more formally to such flags of convenience. Alternatively, it could develop its own. It could overcome its eternal existential angst by replacing 'IS' with the 'MIS' tag and formally excluding interests other than those of business from the discipline's scope.
If, on the other hand, the IS discipline aspires to the mantle of a genuine academic discipline, it needs to carve out a much larger space. The discipline can revert to the original notion of 'everything about systems that handle information', and recognise that the explosion in IT's capabilities and applications have drawn the whole world inside those systems, and that those systems have very substantial impacts and implications for individuals, groups, societies and polities. That approach makes it almost incontrovertible that the perspectives of all affected parties need to be reflected in the corpus of IS research.
Venues that adopt the latter, expansive and positive approach rather than the existing, retractive and negative one, need to do something about how they acquire papers for publication. Calls for papers need to expressly address dimensions additional to the economic, and the perspectives of all stakeholders, broadly defined. Further, Editors need to decline submissions that are mechanistic and narrow - and clearly explain what the authors need to do in order for their submissions to be re-considered. Editors need to develop a culture among their associates, seniors and reviewers that strongly favours dual- and multi-perspective research, and that sets the bar much higher for the routine, single-perspective research that currently takes up so much of journal and conference in-trays.
The focus of this paper has been on personal data markets, within the broader area of electronic markets. The problems that it has found have ramifications well beyond those genres, and raise questions about the future path of the IS discipline as a whole.
Alt R., Militzer-Horstmann C. & Zimmerman H.-D. (2015) 'Editorial 25/2: Electronic Markets and privacy' Electronic Markets 25, 2 (June 2015) 87-90
Acquisti A., Friedman A. & Telang R. (2006) 'Is There a Cost to Privacy Breaches? An Event Study' Proc. ICIS 2006, Paper 94
Acquisti A. & Gross R. (2006) 'Imagined communities: awareness, information sharing, privacy on the Facebook' Proc. Privacy Enhancing Technology Workshops (PET), 2006, 1-22, at http://people.cs.pitt.edu/~chang/265/proj10/zim/imaginedcom.pdf
Aperjis C. & Huberman B. (2012) 'A Market for Unbiased Private Data: Paying Individuals According to their Privacy Attitudes' HP Working Paper, 2012
Bakos Y. (1998) 'The emerging role of electronic marketplaces on the Internet' Communications of the ACM 41, 8 (August 1998) 35-42, at http://people.stern.nyu.edu/bakos/emkts-cacm.pdf
Barth A., Datta A., Mitchell J.C. & Nissenbaum H. (2006) 'Privacy and Contextual Integrity: Framework and Applications' Proceedings of the 27th IEEE Symposium on Security and Privacy, IEEE Computer Society, 2006, at http://www.adambarth.org/papers/barth-datta-mitchell-nissenbaum-2006.pdf
Beckert J. (2005) 'Trust and the Performative Construction of Markets ' MPIfG Discussion Paper 05/8, Max-Planck-Institut für Gesellschaftsforschung Köln, September 2005 , at http://edoc.vifapol.de/opus/volltexte/2007/54/pdf/dp05_8.pdf
Bélanger F. & Crossler R.E. (2011) 'Privacy in the Digital Age: A Review of Information Privacy Research in Information Systems' MIS Quarterly 35, 4 (December 2011) 1017-1041
Benjamin R.I. & Wigand R.T. (1995) 'Electronic Markets and Virtual Value Chains on the Information Superhighway' Sloan Management Review 36, 2 (1995) 62-72
Bergelson V. (2003) 'It's personal but is it mine? Toward property rights in personal information' UC Davis Law Review 37 (2003) 379-451, at http://papers.ssrn.com/sol3/papers.cfm?abstract_id=870070
Camerno J. (2007) 'An Integrated Framework for Managing eBusiness Collaborative Projects' PhD Thesis, UNSW, March 2007, at http://unsworks.unsw.edu.au/fapi/datastream/unsworks:2112/SOURCE01?view=true
Cameron J. & Clarke R. (1996) 'Towards a theoretical framework for collaborative electronic commerce projects involving small and medium-sized enterprises' Proc. 9th Int'l Conf. on EDI-IOS, Bled, Slovenia, 1996
Clarke R. (1992) 'Extra-Organisational Systems: A Challenge to the Software Engineering Paradigm' Proc. IFIP World Congress, Madrid, September 1992, PrePrint at http://www.rogerclarke.com/SOS/PaperExtraOrgSys.html
Clarke R. (1994) 'The Path of Development of Strategic Information Systems Theory' Xamax Consultancy Pty Ltd, July 1994, at http://www.rogerclarke.com/SOS/StratISTh.html
Clarke R. (1999a) 'The Willingness of Net-Consumers to Pay: A Lack-of-Progress Report' Proc. 12th International Bled Electronic Commerce Conference, Bled, Slovenia, June 7 - 9, 1999, PrePrint at http://www.rogerclarke.com/EC/WillPay.html
Clarke R. (1999b) 'Person-Location and Person-Tracking: Technologies, Risks and Policy Implications' Proc. 21st Int'l Conf. on Privacy and Personal Data Protection, pp.131-150, Hong Kong, September 1999. Revised version in Information Technology & People 14, 2 (Summer 2001) 206-231, PrePrint at http://www.rogerclarke.com/DV/PLT.html
Clarke R. (2001a) 'P3P Re-visited' Privacy Law & Policy Reporter 7, 10 (April 2001), PrePrint at http://www.rogerclarke.com/DV/P3PRev.html
Clarke R. (2001b) 'Towards a Taxonomy of B2B e-Commerce Schemes' Proc. 14th Int'l eCommerce Conf., Bled, Slovenia, June 2001, pp. 591-615, at http://www.rogerclarke.com/EC/Bled01.html
Clarke R. (2002a) 'Trust in the Context of e-Business' Internet Law Bulletin 4, 5 (February 2002) 56-59, at http://www.rogerclarke.com/EC/Trust.html
Clarke R. (2002b) 'e-Consent: A Critical Element of Trust in e-Business' Proc. 15th Bled Electronic Commerce Conference, Bled, Slovenia, 17-19 June 2002, at http://www.rogerclarke.com/EC/eConsent.html
Clarke R. (2002c) 'The Birth of Web Commerce' Xamax Consultancy Pty Ltd, October 2002, at http://www.rogerclarke.com/II/WCBirth.html
Clarke R. (2004) 'Identity Management: The Technologies, Their Business Value, Their Problems, Their Prospects' Xamax Consultancy Pty Ltd, March 2004, at http://www.xamax.com.au/EC/IdMngt.html
Clarke R. (2006) 'A Major Impediment to B2C Success is ... the Concept 'B2C' Invited Keynote, Proc. ICEC'06, Fredericton NB, Canada, 14-16 August 2006, PrePrint at http://www.rogerclarke.com/EC/ICEC06.html
Clarke R. (2008a) 'B2C Distrust Factors in the Prosumer Era' Invited Keynote, Proc. CollECTeR Iberoamerica, Madrid, 25-28 June 2008, pp. 1-12, PrePrint at http://www.rogerclarke.com/EC/Collecter08.html
Clarke R. (2008b) 'Dissidentity: The Political Dimension of Identity and Privacy' Identity in the Information Society 1, 1 (December, 2008) 221-228, PrePrint at http://www.rogerclarke.com/DV/Dissidentity.html
Clarke R. (2009) 'A Sufficiently Rich Model of (Id)entity, Authentication and Authorisation' Proc. IDIS 2009 - The 2nd Multidisciplinary Workshop on Identity in the Information Society, LSE, London, 5 June 2009, at http://www.rogerclarke.com/ID/IdModel-090605.html
Clarke R. (2014) 'The Prospects for Consumer-Oriented Social Media' Proc. Bled eConference, June 2014, at http://www.rogerclarke.com/II/COSM-1402.html
Clarke R. (2015) 'Not Only Horses Wear Blinkers: The Missing Perspectives in IS Research' Keynote Presentation, Proc. Austral. Conf. in Infor. Syst. (ACIS 2015), Adelaide, December 2015, PrePrint at http://www.rogerclarke.com/SOS/ACIS15.html
Clarke R. (2016a) 'An Empirical Assessment of Researcher Perspectives' Working Paper, Xamax Consultancy Pty Ltd, February 2016, at http://www.rogerclarke.com/SOS/BledP.html
Clarke R. (2016b) 'Vignettes of Corporate Privacy Disasters' Xamax Consultancy Pty Ltd, Versions 2006-16, at http://www.rogerclarke.com/DV/PrivCorp.html
Clarke R. & Wigan M.R. (2011) 'You Are Where You've Been: The Privacy Implications of Location and Tracking Technologies' Journal of Location Based Services 5, 3-4 (December 2011) 138-155, PrePrint at http://www.rogerclarke.com/DV/YAWYB-CWP.html
Culnan M.J. & Bies R.J. (2003) 'Consumer privacy: Balancing economic and justice considerations' Journal of Social Issues 59, 2 (2003) 323-342, at https://www.researchgate.net/profile/Mary_Culnan/publication/227510444_Consumer_Privacy_Balancing_Economic_and_Justice_Considerations/links/0046353c41051a8217000000.pdf
Davies S. (1997) 'Time for a byte of privacy please' Index on Censorship 26, 6 (1997) 44-48 DHI (2003) 'Literary Criticism' Dictionary of the History of Ideas, University of Virginia, 2003, at http://xtf.lib.virginia.edu/xtf/view?docId=DicHist/uvaBook/tei/DicHist1.xml;chunk.id=dv1-71;toc.depth=1;toc.id=dv1-71;brand=default;query=LITERARY%20CRITICISM#1
Dobson J. & Fisher P. (2003) 'Geoslavery' IEEE Technology and Society 22 (2003) 47-52
EM (2013) 'CfP Special Issue on Personal Data Markets', Electronic Markets, 2013, at http://www.electronicmarkets.org/call-for-papers/single-view-for-cfp/datum/2014/04/05/deadline-extension-cfp-special-issue-on-personal-data-markets/
EM (2014) 'Editorial' Electronic Markets 24, 3 (August 2014) 161-164, at http://link.springer.com/article/10.1007/s12525-014-0163-9/fulltext.html
EM (2016) 'Scope' Electronic Markets, at http://www.electronicmarkets.org/about-em/scope/
EU (1995) 'Directive 95/46/EC of the European Parliament and of the Council of 24 October 1995 on the protection of individuals with regard to the processing of personal data and on the free movement of such data', European Union, at http://eur-lex.europa.eu/legal-content/EN/TXT/?uri=CELEX:31995L0046
FTC (2000) 'Privacy Online: Fair Information Practices in the Electronic Marketplace: A Federal Trade Commission Report to Congress' Federal Trade Commission, May 2000, at http://www.ftc.gov/reports/privacy2000/privacy2000.pdf
GFW (2011) 'Who is harmed by a "Real Names" policy?' Geek Feminism Wiki, undated, apparently of 2011, at http://geekfeminism.wikia.com/wiki/Who_is_harmed_by_a_%22Real_Names%22_policy%3F
Greenleaf G. (2014) 'Asian Data Privacy Laws: Trade and Human Rights Perspectives' Oxford University Press, October 2014
Greenleaf G. (2015) 'Global Data Privacy Laws 2015: 109 Countries, with European Laws Now a Minority' Privacy Laws & Business International Report, February 2015, 133, at http://papers.ssrn.com/sol3/Delivery.cfm/SSRN_ID2603529_code57970.pdf?abstractid=2603529&mirid=1
Gross E. (2004) 'The Struggle of a Democracy against Terrorism - Protection of Human Rights: The Right to Privacy versus the National Interest - the Proper Balance' Cornell International Law Journal 37, 1 (2004) Article 2, at http://scholarship.law.cornell.edu/cilj/vol37/iss1/2
Hauff S., Veit D. & Tuunainen V. (2015) 'Towards a Taxonomy of Perceived Consequences of Privacy-invasive Practices' Proc. ECIS 2015, June 2015, Paper 74, at https://www.researchgate.net/publication/277953385_TOWARDS_A_TAXONOMY_OF_PERCEIVED_CONSEQUENCES_OF_PRIVACY-INVASIVE_PRACTICES
Hirst M. (2013) `Someone's looking at you: welcome to the surveillance economy' The Conversation, 26 July 2013, at http://theconversation.com/someones-looking-at-you-welcome-to-the-surveillance-economy-16357
ICCPR (1966) 'International Covenant on Civil and Political Rights' United Nations, 1966, at http://www.ohchr.org/en/professionalinterest/pages/ccpr.aspx, Accession list at https://treaties.un.org/Pages/ViewDetails.aspx?src=IND&mtdsg_no=IV-4&chapter=4&lang=en
Kambil A. & van Heck E. (1998) 'Reengineering the Dutch flower auctions: A framework for analysing exchange operations' Inf. Sys. Research 9, 1 (1998) 1-19, at http://archive.nyu.edu/ bitstream/2451/14208/1/IS-96-24.pdf
Kang J. & Buchner B. (2004) 'Privacy in Atlantis' Harvard Journal of Law and Technology 18, 1 (Fall 2004) 229-267, at http://paulohm.com/classes/infopriv13/files/week1/Kang%20and%20Buchner%20Privacy%20in%20Atlantis.pdf
Kollock P. (1999) 'The Production of Trust in Online Markets' in Lawler E.J., Macy M., Thyne S. & Walker H.A. (eds.) 'Advances in Group Processes, Vol. 16' JAI Press. 1999, at http://www.connectedaction.net/wp-content/uploads/2009/05/1999-peter-kollock-the-production-of-trust-in-online-markets.htm
Laudon K.C. (1993) 'Markets and Privacy' Stern School of Business, Workinq Paper Series IS-93-21, July 1993, at http://archive.nyu.edu/bitstream/2451/14257/1/IS-93-21.pdf. Revised version published in Communications of the ACM 39, 9 (September 1996) 92-104
Lessig L. (1999) 'Code, and Other Laws of Cyberspace' Basic Books, 1999
Lyon D. (1994) 'The Electronic Eye: The Rise of Surveillance Society' Polity Press, 1994
Manwaring K. & Clarke R. (2015) ''Surfing the third wave of computing: a framework for research into eObjects' Computer Law & Security Review 31,5 (October 2015) 586-603, at http://www.rogerclarke.com/II/SSRN-id2613198.pdf
Michael K. & Clarke R. (2013) 'Location and Tracking of Mobile Devices: Überveillance Stalks the Streets' Computer Law & Security Review 29, 3 (June 2013) 216-228, PrePrint at http://www.rogerclarke.com/DV/LTMD.html
Narayanan A., Toubiana V., Barocas S., Nissenbaum H. & Boneh D. (2012) 'A Critical Look at Decentralized Personal Data Architectures. CoRR abs/1202.4503 (2012), http://randomwalker.info/publications/critical-look-at-decentralization-v1.pdf
Nehf J.P. (2005) 'Shopping for privacy online: Consumer decision-making strategies and the emerging market for information privacy' U. Ill. JL Tech. & Pol'y 2005, 1, at http://illinoisjltp.com/journal/wp-content/uploads/2013/10/nehf.pdf
Noam E.M. (1997) (ed.) 'Privacy and Self-Regulation: Markets for Electronic Privacy', Chapter in Wellbery B.S. (ed.) 'Privacy and Self-Regulation in the Information Age' NTIA, 1997, pp. 21-33
Novotny A. & Spiekermann S. (2013) 'Personal Information Markets AND Privacy: A New Model to Solve the Controversy' Proc. Wirtschaftsinformatik, 2013
OECD (1980) 'Guidelines on the Protection of Privacy and Transborder Flows of Personal Data', Organisation for Economic Cooperation and Development, Paris, 1980, at http://www.oecd.org/document/18/0,2340,en_2649_201185_1815186_1_1_1_1,00.html
Pavlou P.A. (2011) 'State of the Information Privacy Literature: Where Are We Now and Where Should We Go?' MIS Quarterly 35, 4 (December 2011) 977-988
Posner R.A. (1977) 'The Right of Privacy' 12 Georgia Law Review 393, at http://chicagounbound.uchicago.edu/cgi/viewcontent.cgi?article=2803&context=journal_articles
Raab C.D. (1997) 'Privacy, democracy, information' Ch. 10 in Loader B. (ed.) 'The Governance of Cyberspace: Politics, Technology and Global Restructuring', pp. 155-174
Rayport J. F. & Sviokla J. H. (1994) 'Managing in the Marketspace' Harv. Bus. Rev. (Nov-Dec 1994) 141-150
Reck M. (1997) 'Trading-Process Characteristics of Electronic Auctions' Electronic Markets 7, 4 (1997) 17-23, at http://www.electronicmarkets.org/fileadmin/user_upload/doc/Issues/Volume_07/Issue_04/V07I4_Trading-Process_Characteristics_of_Electronic_Auctions.pdf
Riederer C., Erramilli V., Chaintreau A., Krishnamurthy B. & Rodriguez P. (2011) 'For sale : your data: by : you' Proc. 10th ACM Workshop on Hot Topics in Networks, November 2011, at http://www.cs.columbia.edu/~mani/hotnetsX-final85.pdf
Rule, J.B. (1974) 'Private Lives and Public Surveillance: Social Control in the Computer Age' Schocken Books, 1974
Rule J.B. (2007) 'Privacy in peril: How we are sacrificing a fundamental right in exchange for security and convenience' Oxford University press, 2007, at http://books.google.com.au/books?hl=en&lr=&id=RYg3AwAAQBAJ&oi=fnd&pg=PR7&dq=%22personal+information+markets%22&ots=6PEacUyBHI&sig=1ibOhXUX-pl6Uk6nBeUA3GRHjNg
Rule. J.B. McAdam, D. Stearns, L. and Uglow, D. (1980) 'The Politics of Privacy' New American Library, 1980
Samuelson P. (2000) 'Privacy as intellectual property?' Stanford Law Review, 52, 5 (May 2000) 1125-1173, at http://scholarship.law.berkeley.edu/cgi/viewcontent.cgi?article=3137&context=facpubs
Schmidt B. (1993) 'Electronic Markets' 3, 3 (October 1993), at http://www.electronicmarkets.org/fileadmin/user_upload/doc/Issues/Volume_03/Issue_03/Electronic_Markets.pdf
Schmid B.F. (1997) 'Requirements for Electronic Markets Architectures' Electronic Markets 7,1 (1997) 3-6, at http://www.electronicmarkets.org/fileadmin/user_upload/doc/Issues/Volume_07/Issue_01/V07I1_Requirements_For_Electronic_Markets_Architecture.pdf
Schwartz P.M. (2000) 'Beyond Lessig's Code for Internet Privacy: Cyberspace Filters, Privacy Control, and Fair Information Practices' Wis. L. Rev., 2000, at http://scholarship.law.berkeley.edu/cgi/viewcontent.cgi?article=1422&context=facpubs
Schwartz P.M. (2004) 'Property, privacy, and personal data' Harvard Law Review 117 (2004) 2056-2128, at http://scholarship.law.berkeley.edu/cgi/viewcontent.cgi?article=1068&context=facpubs
Segev A., Gebauer J. & Färber F. (1999) 'Internet-based electronic markets' Electronic Markets 9, 3 (1999) 138-146, at http://aws.iwi.uni-leipzig.de/em/fileadmin/user_upload/doc/Issues/Volume_09/Issue_03/V09I3_Internet-based_Electronic_Markets.pdf
Shapiro C. & Varian H.R. (1999) 'Information Rules: A Strategic Guide to the Network Economy' Harvard Business School Press, 1999
Simitis S. (1995) 'From the Market to the Polis: The EU Directive on the Protection of Personal Data' 80 Iowa L. Rev. 445 (1994-95) 445
Smith H.J. (1994) 'Managing privacy: Information technology and corporate America' UNC Press Books, 1994, at https://books.google.com.au/books?hl=en&lr=&id=BwQBT2Mr1YoC&oi=fnd&pg=PR11&dq=privacy+Jeff+Smith&ots=WI997J3n5E&sig=rGWQOeEyKpILywn0or2vqkA5Y0o#v=onepage&q=privacy%20Jeff%20Smith&f=false
Smith H.J., , Dinev T. & Xu H. (2011) 'Information Privacy Research: An Interdisciplinary Review' MIS Quarterly 35, 4 (December 2011) 989-1015
Smith R.E. (2013) 'Compilation of State and Federal Privacy Laws 2013' Privacy Journal, June 2013, plus the 2015 Supplement, adding 20 more laws
Solove D.J. (2006) 'A Taxonomy of Privacy' 154 U. Pa. L. Rev. 477 (2006), at http://scholarship.law.gwu.edu/cgi/viewcontent.cgi?article=2074&context=faculty_publications
Spiekermann S., Böhme R., Acquisti A. & Hui K.-L. (2015a) 'Personal Data Markets' Preface to the Special Issue, Electronic Markets 25, 2 (June 2015) 91-93
Spiekermann S., Böhme R., Acquisti A. & Hui K.-L. (2015b) 'The challenges of personal data markets and privacy' Position Paper, Special Issue, Electronic Markets 25, 2 (June 2015) 161-167
Spiekermann S., Korunovska K. & Bauer C. (2012) 'Psychology of Ownership and Asset Defense: Why people value their personal information beyond privacy' Proc. ICIS, 2012
van den Broek T. & van Veenstra, A.F. (2015) 'Modes of Governance in Inter-Organizational Data Collaborations' Proc. ECIS, June 2015, Paper 188
Varian H.R. (1996) 'Economic Aspects of Personal Privacy' University of California, Berkeley, December 1996, at http://people.ischool.berkeley.edu/~hal/Papers/privacy/
Weber R.H. (2010) 'Internet of Things - New security and privacy challenges' Computer Law & Security Review 26, 1 (Jan-Feb 2010) 23-30, at https://www.researchgate.net/profile/Rolf_Weber3/publication/222708179_Internet_of_Things_-_New_security_and_privacy_challenges/links/0c96053cab03fee371000000.pdf
Weill P. & Vitale M. (2001) 'Place to Space: Migrating to eBusiness Models' Harvard Business School Press, 2001
Westin A.F. (1967) 'Privacy and Freedom' Atheneum 1967
Westin, A.F., Ed. (1971) 'Information Technology in a Democracy', Harvard University Press, Cambridge, Mass., 1971
Westin A.F. & Baker M.A. (1974) 'Databanks in a Free Society: Computers, Record-Keeping and Privacy' Quadrangle 1974
Whitley E.A. (2013) 'Towards Effective, Consent Based Control of Personal Data' in Hildebrandt M. et al. (Eds.) 'Digital Enlightenment Yearbook 2013' IOS Press, 2013, pp. 165-176, at http://personal.lse.ac.uk/whitley/allpubs/def2013.pdf
Wrigley C.D., Wagenaar R.W. & Clarke R. (1994) 'Electronic data interchange in international trade: frameworks for the strategic analysis of ocean port communities' Journal of Strategic Information Systems 3 (3), 211-234
Xu H., Dinev T., Smith H.J. & Hart P. (2008) 'Examining the Formation of Individual's Privacy Concerns: Toward an Integrative View' Proc. 29th Int'l Conf. on Infor. Syst., Paris, December 2008, at http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.231.2985&rep=rep1&type=pdf
Roger Clarke is Principal of Xamax Consultancy Pty Ltd, Canberra. He is also a Visiting Professor in Cyberspace Law & Policy at the University of N.S.W., and a Visiting Professor in the Computer Science at the Australian National University.
| Personalia |
Photographs Presentations Videos |
Access Statistics |
 |
The content and infrastructure for these community service pages are provided by Roger Clarke through his consultancy company, Xamax. From the site's beginnings in August 1994 until February 2009, the infrastructure was provided by the Australian National University. During that time, the site accumulated close to 30 million hits. It passed 65 million in early 2021. Sponsored by the Gallery, Bunhybee Grasslands, the extended Clarke Family, Knights of the Spatchcock and their drummer |
Xamax Consultancy Pty Ltd ACN: 002 360 456 78 Sidaway St, Chapman ACT 2611 AUSTRALIA Tel: +61 2 6288 6916 |
Created: 25 October 2015 - Last Amended: 29 September 2016 by Roger Clarke - Site Last Verified: 15 February 2009
This document is at www.rogerclarke.com/SOS/PDMP.html
Mail to Webmaster - © Xamax Consultancy Pty Ltd, 1995-2022 - Privacy Policy