Special Adviser, IT Security Policy, Security Division
Presented at an IBC Conference, November 1995
© Commonwealth of Australia, 1995
Editor's Note: Most of this paper is reasonably general, particularly for the people likely to visit it. The part that will interest a lot of people is about authentication, a proposed framework for public key authentication facilities, and the role of smart cards in the proposed scheme.
At a recent speech to the Security in Government 95 Conference, the Commonwealth Auditor-General said
The ANAO sees the implementation and management of an appropriate security regime as an important element of effective public sector administration. ... Public service managers need to recognise and adequately assess the implications of any disruption to their business or functions from security deficiencies and breaches, their responsibilities to those who provide personal or other confidential data as well as any international obligations that apply.
Security is now an integral part of corporate activity with a positive contribution to corporate outcomes. The modern security professional is now a part of the corporate management structure, needs to be proactive rather than reactive and be an integral part of all aspects of the corporate planning process.
In 1992 the Organisation for Economic Co-operation and Development (OECD) issued Guidelines for the Security of Information Systems prepared by an expert group under the Chairmanship of Justice Michael Kirby. A copy of the Guidelines is attached to this paper.
Australia has adopted the guidelines.
Perhaps the best definition of Information Technology Security (ITS) is contained in the security objective set out in the Guidelines:
The objective of security of information systems is the protection of the interests of those relying on information systems from harm resulting from failures of availability, confidentiality, and integrity
"Availability" means the characteristic of data, information and information systems being accessible and useable on a timely basis in the required manner.
"Confidentiality" means the characteristic of data and information being disclosed only to authorised persons, entities and processes at authorised times and in the authorised manner.
"Integrity" means the characteristic of data and information being accurate and complete and the preservation of accuracy and completeness.
Since the Guidelines were written, a number of people have been adding a fourth element, authentication, to the list. While this is implicit in the other three, we are moving to an era where we need to be assured that the persons, or indeed computers, with whom we are dealing are who they say they are. Considerable work is being carried out in the area of authentication. Some of it will be referred to later in the paper.
These guidelines are useful as they establish not so much the measures which should be taken to secure information systems, but rather the framework within which security should be applied. It addresses such issues as accountability, ethics, democracy, and awareness which are not traditionally seen as security matters. However, they are an integral part of a holistic approach to information security management.
Briefly the principles are:
The responsibility and accountability of owners, providers and users of information systems and other parties concerned with the security of information systems should be explicit.
In order to foster confidence in information systems, owners, providers and users of information systems and other parties should readily be able, consistent with maintaining security, to gain appropriate knowledge of and be informed about the existence and general extent of measures, practices and procedures for the security of information systems.
Information systems and the security of information systems should be provided and used in such a manner that the rights and legitimate interests of others are respected
Measures, practices and procedures for the security of information systems should take account of and address all relevant considerations and viewpoints, including technical, administrative, organisational, operational, commercial, educational, and legal
Security levels, costs, measures, practices and procedures should be appropriate and proportionate to the value of and degree of reliance on the information systems and to the severity, probability and extent of potential harm, as the requirements for security vary depending on the particular information systems.
Measures, practices and procedures for the security of information systems should be co- ordinated and integrated with each other and with other measures, practices and procedures of the organisation so as to create a coherent system of security.
Public and private parties, at both national and international levels, should act in a timely co- ordinated manner to prevent and to respond to breaches of security of information systems.
The security of information systems should be reassessed periodically, as information systems and the requirements for their security vary over time.
The security of information systems should be compatible with the legitimate use and flow of data in a democratic society.
Standards Australia is currently finalising a Standard for Information Security Management (Draft Standard DR95305). The Standard is substantially based on the British Code of Practice which is also being considered as a possible international standard.
The document addresses the following components of IT security management:
Management should set clear direction and demonstrate their support for information security through the issue of a corporate information security policy
A management framework should be established to initiate and control the implementation of information security within the corporation
All major information assets should be accounted for and have a nominated "owner"
Security should be addressed at the recruitment stage and included in job descriptions and contracts. Users must be trained in security and the correct use of IT facilities. Incidents affecting security must be reported through the correct channels as quickly as possible.
IT facilities supporting critical or sensitive business activities should be housed in secure areas. Equipment should be physically protected from security threats and environmental hazards
Responsibilities and procedures for the management and operation of all computers and networks must be established. Advance planning and preparation is required to ensure the availability of adequate capacity and resources. Precautions are required to prevent the introduction of malicious software. Exchanges of data and software between organisations should be controlled
Access to computer services and data should be controlled on the basis of business requirements. There should be formal procedures to control allocation of access rights to IT services. Connections to network services should be controlled. Systems should be monitored to ensure compliance with access policy and standards.
Security requirements should be identified and agreed prior to the development of IT systems.
Business continuity plans are required to protect critical business processes from major failures or disasters. The plans should be regularly and realistically tested.
The design, operation and use of IT systems must comply with all relevant statutory and contractual security requirements. The security of IT systems should be regularly reviewed.
While much of these are just motherhood statements to security professionals, the fact they are is included in a national standard is extremely useful in convincing management of the need to implement IT security.
Another recent standard has addressed the question of mission or safety critical systems.
AS 4400 Personal privacy protection in health care information systems states:
7.2.1 Certification Systems and software should be certified to the effect that all relevant security features are appropriately incorporated. Systems and software should be certified as suitable for the uses to which they are put, in view of the effect that they may have on the health and wellbeing of the patient, especially when decision support and expert systems are used. Where systems are critical for the health and wellbeing of the patient, such certification should be carried out by an independent body.
As we become more and more dependent on computer systems to perform tasks, the failure of which would have a critical impact on either safety or our business, we are going to need an increasing level of assurance not only that the systems will perform what we want them to do, but also that they will not do something we don't want them to.
There is already a body of expertise being built up in the field of software verification.
In December 1993 the Australian Government established a Broadband Services Expert Group to examine the technical, economic and commercial preconditions for the widespread delivery of broadband services to homes, businesses and schools in Australia. In releasing the Group's Final Report Networking Australia's Future the Prime Minister said being linked to the national information infrastructure is a fundamental right for all Australians.
As the Final Report put it:
"In the next decade, large-scale communications investments in Australia will pave the way for many business, government, information and entertainment services. These services could change forever the way business and government operate and how we communicate with our colleagues, families and friends. Over time, even the significance of international borders and the design of towns and cities will change."
Similarly, the OECD in its 1992 Guidelines for the Security of Information Systems said:
"Recent years have witnessed ... growth of computer use to the point that, in many countries, every individual is an actual or potential user of computer and communication networks."
Over the past twelve months, the OECD has embarked on a round of meetings on Global Information Infrastructures. The outcomes of this round are to be provided in a report to the G7 on job creation and the information society. Security privacy and the protection of intellectual property are some of the issues being addressed as part of this round. Indeed the final meeting will specifically address these issues. In outlining an agenda for this meeting the OECD saw encryption as a pivotal issue in the security of information systems.
The OECD interest in the Global Information Infrastructure relates not only to the direct impact of the infrastructures on national economies, but also on the economic impact of investment failures if the infrastructure is misused or not used to its expected capacity. User confidence is seen as a key factor in infrastructures reaching their full potential. It is from this position that the OECD is examining issues of security, privacy and the protection of intellectual property.
Turning again to the OECD Guidelines, they stated when addressing the question of building confidence:
"Users must have confidence that information systems will operate as intended without unanticipated failures or problems. Otherwise, the systems and their underlying technologies may not be exploited to the extent possible and further growth and innovation may be inhibited."
Adoption of a strategic approach towards the security of Information Infrastructures will be critical to their success. The key strategies are:
The Commonwealth has a specific methodology for risk assessment. The basic elements involve a risk analysis, threat assessment and vulnerability identification. These are used as a basis for assessing risk.
This involves resource identification and consequence analysis. Resource identification is identifying resources that may require protection to ensure proper and continuous functioning of the organisation or facility. Consequence analysis is determining the consequences if certain resources are lost, damaged or destroyed.
A threat assessment is a judgement of the likelihood or probability of an event taking place that could adversely affect an agency's resources. Its purpose is to determine if there is a threat, where it comes from and how it may be realised.
Vulnerability identification is an assessment of whether existing security arrangements can resist threats and/or prevent damage to resources should such threats eventuate.
In carrying out the above steps you should consult with both management and staff in the various elements of your organisation. Other input can be obtained from the police and insurance companies.
This process should be carried out in conjunction with the initial planning for the infrastructure being developed.
Once the risk assessment has been completed, the planning stage should incorporate a strategy for managing the risks identified. This does not mean adopting a risk avoidance approach. Rather, decisions should be reached on what level of risk is acceptable and countermeasures planned to reduce the risk to that level.
Another key strategy is the development of a business continuity strategy at the general planning stage. The strategy should encompass both disaster avoidance and business resumption.
The risk management and business continuity strategies should be developed at this stage to allow equipment specifications to be developed to assist in selecting the most appropriate technology. Formal plans based on these strategies can be developed once the equipment has been selected.
An important point to remember is that most vulnerabilities in systems are discovered more by accident than by structured approaches. Once these vulnerabilities are identified they are readily distributed. The increase in the user base arising from the new infrastructures is likely to result in any vulnerabilities being quickly identified and widely distributed. It is important that the planning stage identify as many vulnerabilities as possible and that contingency plans are in place to handle any problems which might arise.
These days hardware and software often do not include security packages. It is therefore important to ensure that security products which meet the functional requirements developed at the planning stage are integrated into the overall package. Too often products are selected on their general functionality and then security is added on. It should be made clear to systems integrators that security requirements are part of the overall package and have been developed in conjunction with other measures such as physical, personnel and administrative security. Any change in the security technology selected could impact on the overall security strategy.
As mentioned earlier, system vulnerabilities will assume new proportions in the new infrastructures. It is therefore even more important to know what the hardware and software you are considering actually does. The implications of not identifying known vulnerabilities in systems hardware or software being offered should be made clear to vendors .
Management support is a key element of any strategy. The support must cover all elements. Specifically there must be support both at the design stage and in the ongoing operation of the infrastructure. This support, especially at the latter stage should be highly visible. I have long argued for simple IT security policies which can be expressed on one page, be signed by the Chief Executive Officer and displayed in prominent places.
Of equal importance is the need for an effective management structure for security. Whether it is centralised or devolved, the structure needs to be documented and all involved need to understand what there responsibilities are. Ultimately, however, security is the responsibility of individual users.
Introduction of the new infrastructures will lead to an explosion of the user base to include both staff and clients. There will be a need to educate the general population in how to use the facilities responsibly. This will involve nation wide education campaigns on such issues as controlling identifiers, the importance to the user of maintaining the confidentiality, integrity and availability of personal data being accessed, and the proper use of systems to ensure they are available for other users.
Ultimately these types of issues will need to be taught to children as early as primary school, where they first start to use information infrastructures.
Standards are important not to achieve interoperability, but also to engender confidence. Unless the public has confidence in both the functionality of systems which it is expected to use and the security and privacy of information which it provides, the systems will not be accepted.
In addition, the process of establishing whether your system meets the applicable standard requires it to be examined in detail. This leads to a greater understanding of the system, which will be invaluable if problems do arise.
Digital signature techniques and public key authentication will play an increasingly significant role as networks expand and the number of users and range of services offered increase.
This is an area where confidence needs to be engendered to ensure acceptance. There is a need for a mechanism to ensure that techniques are appropriate for the purpose for which they will be used. Similarly there is a need for a structure through which keys can be obtained and digital signatures authenticated.
Within Australia a Government Group has been developing a proposal for a Public Key Authentication Framework. The group's work has been primarily focused on the needs of electronic commerce. In an unpublished paper the group stated:
There needs to be a wide scale informed debate about this issue before any decisions are taken as to choice of technology, the appropriate administrative structure, privacy issues, legal effect, method of implementation and the like. After such a debate the system will need to be introduced in a planned way with appropriate public education, legislation and the like in order that the use of the PKAF system will have the same standing and validity in the eyes of the community as a paper based signature
Since the project commenced, it has been recognised that the procedures involved could be applied to electronic documents in records management systems as well as to transactions in electronic commerce.
The proposal calls for a management structure to verify various key generation systems, supervise the issue of key pairs and maintain a directory of the public keys.
This proposal has been referred to the Standards Association of Australia which has established a task force to examine the establishment of an Australian Public Key Authentication Facility. The Task Force is required to report by the end of the year.
Australia has also raised in the OECD the need to establish an international framework to ensure the effective use of public keys as a tool for both international electronic commerce and individual use of the global information infrastructure.
While this proposal is driven, primarily, by commercial needs, there is scope for it to be extended to meet the needs of individuals who will also be using the information infrastructure. Any scheme such as this has to be better than the current process of passing credit card information over the network.
The referral of the PKAF proposal to Standards Australia is in keeping with the Australian Government policy of minimal legislative intervention. When commenting on the implementation of the OECD Guidelines for the Security of Information Systems, in a speech to the Australian Share/Guide Conference in March this year, the Minister for Justice outlined the Government's approach as follows:
In implementing the Guidelines, the Government has decided not to use a general legislative approach because of the problems in reaching agreement with State and Territory Governments on legislation where the Commonwealth has no blanket constitutional power. Furthermore we recognise that legislation is slow to respond to technological advances, so broad definitions have been used in relevant legislation to allow the courts to consider current technology as cases come up.
This policy extends to electronic commerce and the use of cryptography in general. Any legislation required to support the use of cryptography is likely to be written in broad terms rather than endorsing particular technology or algorithms. It would then be left to groups such as Standards Australia to specify the standards which at that particular point in time would meet the legislative requirement.
Public acceptance of the new technology will depend, in part, on confidence that the privacy of personal information provided will be protected and that access will be restricted to the individual or persons entitled to access the information for official purposes.
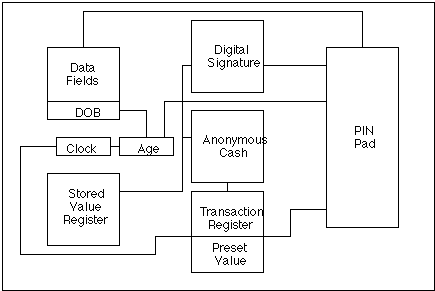
With the advent of public access to information through government and community networks, users will need to be able to establish their entitlement to access information. Similarly the advent of electronic commerce will require the use of digital signatures to conduct the transaction. Electronic documents, for records purposes, will also need to be digitally signed. We are, therefore, moving to the stage where individuals will require a unique electronic authenticator to transact business on the superhighway. Such authenticators are likely to take the form of a digital signature on an individual smart card.
Such cards could be issued within the public key authentication framework referred to earlier. An individual could apply to a certifying authority for a smart card containing their secret key component of their digital signature. The card would be issued upon satisfaction of the one hundred point criteria currently used by banks to open accounts.
Technology also exists for blind signatures and anonymous cash transactions. It may be possible for both digital signature and anonymous cash techniques to be embedded in the one card, which the user could opt to use in either mode. Obtaining a card would, of course, be optional although there would be circumstances where it may be necessary for individuals to identify themselves to obtain access to a particular service. Regulations or Codes Of Practice issued by the Privacy Commissioner could limit the circumstances in which use of the authenticator is mandatory, in much the same way as use of tax file numbers is controlled.
The cards could then perform a number of activities. For example one concern has been access to restricted material over the network. It may be possible to convert date of birth information in the identified section of the smart card into an anonymous age field which could be added when required to demonstrate an entitlement to restricted classification material. Access to restricted information could be limited to those who could demonstrate their age in this way.
As mentioned earlier, obtaining the card would be optional, the user would determine what information other than basic identifying information would be held on the card in addition to the authentication technique. The user would control which of this information would be released through a PIN pad on the card.
The digital signature would be used in much the same way as a written signature is used to authenticate a person signing a document.

The PIN pad would control access to the card and would also control what information is released from the card.
The card holder's secret or private key would be held in this area. Transmission would be controlled by the PIN pad.
An anonymous cash capability such as the David Chaum, Digicash technique would be incorporated to allow transfer of electronic cash in an anonymous mode. For access to restricted classification material the anonymous cash could be combined with the age information to confirm entitlement to access the material.
Use of anonymous cash technology for cash transactions for criminal purposes such as drugs sales or money laundering is of concern to law enforcement authorities. One way of limiting the use of the card for these purposes would be by restricting transactions to a predetermined value per day.
This is where actual cash would be held and could be topped up in the same way as traditional stored value cards.
This field would be computed using the card's clock and date of birth information. It need not necessarily contain actual age but could indicate age range in line with information classification standards. Eg <15, 15 - 18, >18 etc. It is added through the key pad as in most circumstances it will not be required.
This would contain information such as name and date of birth. It would also contain information the card holder opts to have included; eg bank account number, credit card details, access information for network services the user wishes to access and elects to include on the card.
By the turn of the century, the major users of the Global Information Infrastructure will be individuals conducting their day to day activities in electronic form. The main concerns of these users will be to authenticate their identity, to conduct their business with privacy and to have a reasonable level of security for the comparatively low level financial transactions they will be performing. To date the cryptography debate has focussed on the higher needs of government and business. There is a need for the debate to be extended to cover the needs of individual users.
For the information superhighway to reach its full potential in terms of both economic viability and social change, cryptographic systems will need to be developed to meet the needs of individual users. These systems will need to be cheap, user friendly, and above all, have public confidence.
We are entering a new era with new technology, new challenges, new problems which will need new solutions. However, we must not loose sight of our existing social, moral and legal principles which have evolved over millenniums and served us well. An individual's basic right to privacy should still be respected, together with a basic right to live in a safe society. There still needs to be a balance where these two principles conflict. It is the responsibility of governments to attempt to strike this balance between privacy, security and law enforcement.
Go to Roger's Home Page.
Go to the contents-page for this segment.
Last Amended: 21 January 1996
 | These community service pages are a joint offering of the Australian National University (which provides the infrastructure), and Roger Clarke (who provides the content). |  |
| The Australian National University Visiting Fellow, Faculty of Engineering and Information Technology, Information Sciences Building Room 211 | Xamax Consultancy Pty
Ltd, ACN: 002 360 456 78 Sidaway St Chapman ACT 2611 AUSTRALIA Tel: +61 6 288 6916 Fax: +61 6 288 1472 |