Roger Clarke's Web-Site
© Xamax Consultancy Pty Ltd, 1995-2024

Infrastructure
& Privacy
Matilda
Roger Clarke's Web-Site© Xamax Consultancy Pty Ltd, 1995-2024 |

|
|||||
| HOME | eBusiness |
Information Infrastructure |
Dataveillance & Privacy |
Identity Matters | Other Topics | |
| What's New |
Waltzing Matilda | Advanced Site-Search | ||||
Version of 13 November 2023
© Xamax Consultancy Pty Ltd, 2021-23
Available under an AEShareNet ![]() licence or a Creative
Commons
licence or a Creative
Commons  licence.
licence.
This document is at http://rogerclarke.com/ID/IDM-O.html
This is the index-page for a set of papers. The author's contention is that the notion of 'Identity Management', which has been central to people-facing systems for a quarter-century is fundamentally flawed. The series explains the reasoning underlying that claim.
The set of papers indexed here presents a theory of what the author terms (Id)Entity Management (IdEM). This is proposed as a replacement for the notion of Identity Management (IdM). IdEM features a number of material differences from its troubled predecessor. Most crucially, it avoids the fundamental flaw in IdM, by carefully distinguishing the notion of 'identity' from that of 'entity'.
IdEM draws heavily on the author's three decades of consultancy work. It is not, however, an ad hoc approach. Many of the ideas have been previously presented by the author not only in consultancies and professional publications and presentations, but also in refereed conference papers and journal articles.
The present series differs from those earlier works in two important ways:
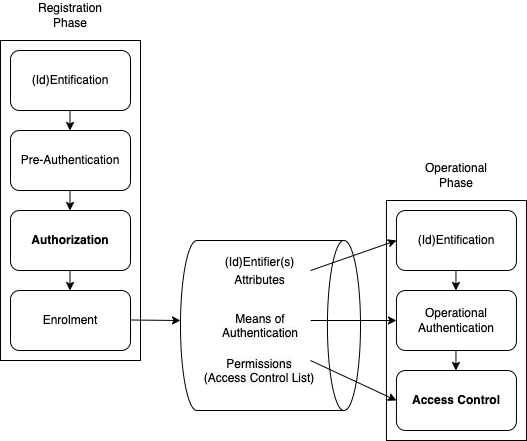
The papers are listed below, with a diagrammatic overview in Figure 1. The theory of (Id)Entity Management is presented in four papers, T1-T4, depicted across the top of the diagram. T1 declares the intellectual framework within which the theory is situated, and defines key terms. T2 has its focus on the notions of identity and entity. T3 presents the theory underlying the authentication of assertions relating to identity and entity. T4 extends the theory to authorization and access control.
The four theoretical papers are underpinned by M1, which declares the philosophical basis underlying the framework. In recent decades, the IS discipline has become increasingly remote from the practice of IS, with its focus rigidly on theory, its demands for rigour in research methods relegating relevance to the world of practice to a very minor role, and its strong preference for intellectualisation and the invention of constructs that are foreign to practitioners. The model used to support the theory of (Id)Entity Management is, on the other hand, committed to IS practice and practice-relevant IS research. It is accordingly pragmatic in nature, seeking to reflect the relevant part of the real world in a manner that is economic, but sufficiently comprehensive and realistic that misunderstandings common during the last few decades are overcome or avoided.
A further metatheoretic paper makes up the set. No adequate abstract theory of the notion of authentication has been located. M2, depicted at an intermediate level, fills that gap by presenting a generic theory of authentication, thereby underpinning the authentication of (id)entity assertions.
The generic theory of authentication is by definition capable of application to matters other then (Id)Entity Management. IS practice and theory have long been preoccupied with the handling of structured data. The last three decades have, however, seen substantial developments in the extent to which, and the sophistication with which, textual content has come to be supported by IT and managed using IS. A further paper, T5, presents an analysis of the authentication of textual statements, and contends that this needs to be brought expressly within the domain of IS practice and research.

Each of the papers is designed to be read standalone. All have been variously presented at or submitted to refereed conferences. A full appreciation of IdEM requires a reading of at least the first four Theory papers, if not of the two Metatheory papers. A comprehensive reading of the entire body of work is best done in the sequence M1, T1, T2; M2, T3, T4, T5. The series is accompanied by a Glossary, containing all definitions presented in the series as a whole.
Links to, and brief outlines of the papers are provided here:
Possible Further Working Paper, not yet drafted:
Historical Working Papers, now superseded:
Many of the ideas in this set of papers have been previously presented, in 6 articles in journals, 5 papers in refereed conferences, a monograph, 6 working papers and 13 presentations in North America, Europe and Australasia. By mid-2023, these previous publications had acquired a total of over 1500 Google citations.
Clarke R. (1990) 'Information Systems: The Scope of the Domain' Xamax Consultancy Pty Ltd, January 1990, at http://rogerclarke.com/SOS/ISDefn.html [4]
Clarke R. (1992) 'Fundamentals of Information Systems' Xamax Consultancy Pty Ltd, September 1992, at http://rogerclarke.com/SOS/ISFundas.html [18]
Clarke R. (1993) 'Computer Matching and Digital Identity' Proc. Computers Freedom & Privacy, Burlingame CA, March 1993, at http://cpsr.org/prevsite/conferences/cfp93/clarke.html/, PrePrint at http://rogerclarke.com/DV/CFP93.html [24]
Clarke R. (1994a) 'The Digital Persona and its Application to Data Surveillance' The Information Society 10,2 (June 1994) 77-92, PrePrint at http://www.rogerclarke.com/DV/DigPersona.html [401]
Clarke R. (1994b) 'Dataveillance by Governments: The Technique of Computer Matching' Information Technology & People 7,2 (June 1994) 46-84, at http://www.rogerclarke.com/DV/MatchIntro.html [38]
Clarke R. (1994c) 'Human Identification in Information Systems: Management Challenges and Public Policy Issues' Information Technology & People 7,4 (December 1994) 6-37, PrePrint at http://www.rogerclarke.com/DV/HumanID.html [581]
Clarke R. (1995) 'When Do They Need to Know 'Whodunnit?' The Justification for Transaction Identification; The Scope for Transaction Anonymity and Pseudonymity' Panel Session Contribution, Computers, Freedom & Privacy Conference, San Francisco, 31 March 1995, at http://www.rogerclarke.com/DV/PaperCFP95.html [11]
Clarke R. (1999) 'Identified, Anonymous and Pseudonymous Transactions: The Spectrum of Choice' Proc. Conf. User Identification & Privacy Protection Conference, Stockholm, June 1999, PrePrint at http://www.rogerclarke.com/DV/UIPP99.html [54]
Clarke R. (2001a) 'The Fundamental Inadequacies of Conventional Public Key Infrastructure' Proc. Conf. ECIS'2001, Bled, Slovenia, 27-29 June 2001, PrePrint at http://www.rogerclarke.com/II/ECIS2001.html [28]
Clarke R. (2001b) 'Certainty of Identity: A Fundamental Misconception, and a Fundamental Threat to Security' Privacy Law & Policy Reporter 8, 3 (September 2001) 63-65, 68, at http://www.rogerclarke.com/DV/IdCertainty.html [3]
Clarke R. (2001c) 'Authentication: A Sufficiently Rich Model to Enable e-Business' Xamax Consultancy Pty Ltd, 19 October 2001, at http://www.rogerclarke.com/EC/AuthModel.html [51]
Clarke R. (2001d) 'The Re-Invention of Public Key Infrastructure' Xamax Consultancy Pty Ltd, December 2001, at http://rogerclarke.com/EC/PKIReinv.html [1]
Clarke R. (2002a) 'Why Do We Need PKI? Authentication Re-visited' Proc. 1st Annual PKI Research Workshop, NIST, Gaithersburg MD, April 2002, PrePrint at http://www.rogerclarke.com/EC/PKIRW02.html [2]
Clarke R. (2002b) 'e-Consent: A Critical Element of Trust in e-Business' Proc. 15th Bled Electronic Commerce Conference, Bled, Slovenia, June 2002, PrePrint at http://www.rogerclarke.com/EC/eConsent.html [57]
Clarke R. (2002c) 'The Mythology of Consumer Identity Authentication', Statement for a Panel Session on 'Understanding e-Business: Can we remain anonymous in the marketplace?' Proc. 24th Int'l Conf. of Data Protection & Privacy Commissioners, Cardiff UK, 9-11 September 2002, at http://www.rogerclarke.com/DV/AnonDPPC02.html [0]
Clarke R. (2003a) 'Authentication Re-visited: How Public Key Infrastructure Could Yet Prosper' Proc. 16th Bled eCommerce Conf., June 2003, PrePrint at http://www.rogerclarke.com/EC/Bled03.html [5]
Clarke R. (2003b) 'eAuthentication Realities: You want to authenticate what???' Presentation in 11 cities across Australia, July-October 2003, for the Australian Computer Society Professional Development Board, Xamax Consultancy Pty Ltd, August 2003, at http://www.rogerclarke.com/EC/ACSeAuth.html [0]
Clarke R. (2004a) 'Identity Management: The Technologies Their Business Value Their Problems Their Prospects' Xamax Consultancy Pty Ltd, March 2004, 66 pp., at http://www.xamax.com.au/EC/IdMngt-Public.pdf [15]
Clarke R. (2004b) 'Identification and Authentication Fundamentals' Xamax Consultancy Pty Ltd, May 2004, at http://www.rogerclarke.com/DV/IdAuthFundas.html [11]
Clarke R. (2004c) 'Identity and Nymity: Public Policy Issues' Invited Presentation to the Government of Ontario Enterprise Architecture Conf., June 2004, at http://www.rogerclarke.com/EC/IdNymPPI.html [0]
Clarke R. (2004d) 'The Concepts of (Id)entity, Nymity and Authentication' Invited Presentation at the University of Ottawa, June 2004, at http://www.rogerclarke.com/DV/UOttINA.html [0]
Clarke R. (2006) 'National Identity Schemes - The Elements' Xamax Consultancy Pty Ltd, February 2006, at http://www.rogerclarke.com/DV/NatIDSchemeElms.html [3]
Clarke R. (2008) '(Id)Entities (Mis)Management : The Mythologies underlying the Business Failures' Proc. 'Managing Identity in New Zealand', Wellington NZ, 29-30 April 2008, PrePrint at http://www.rogerclarke.com/EC/IdMngt-0804.html [1]
Clarke R. (2009) 'A Sufficiently Rich Model of (Id)entity, Authentication and Authorisation' Proc. IDIS 2009 - The 2nd Multidisciplinary Workshop on Identity in the Information Society, LSE, London, 5 June 2009, at http://www.rogerclarke.com/ID/IdModel-090605.html , revised version at http://www.rogerclarke.com/ID/IdModel-1002.html [30]
Clarke R. (2014) 'Promise Unfulfilled: The Digital Persona Concept, Two Decades Later' Information Technology & People 27, 2 (Jun 2014) 182-207, PrePrint at http://www.rogerclarke.com/ID/DP12.html [45]
Coiera E. & Clarke R. (2014) 'e-Consent: The design and implementation of consumer consent mechanisms in an electronic environment' Journal of the American Medical Informatics Association 11,2 (2014) 129-140 [172]
Roger Clarke is Principal of Xamax Consultancy Pty Ltd, Canberra. He is also a Visiting Professor associated with the Allens Hub for Technology, Law and Innovation in UNSW Law, and a Visiting Professor in the Research School of Computer Science at the Australian National University.
| Personalia |
Photographs Presentations Videos |
Access Statistics |
 |
The content and infrastructure for these community service pages are provided by Roger Clarke through his consultancy company, Xamax. From the site's beginnings in August 1994 until February 2009, the infrastructure was provided by the Australian National University. During that time, the site accumulated close to 30 million hits. It passed 65 million in early 2021. Sponsored by the Gallery, Bunhybee Grasslands, the extended Clarke Family, Knights of the Spatchcock and their drummer |
Xamax Consultancy Pty Ltd ACN: 002 360 456 78 Sidaway St, Chapman ACT 2611 AUSTRALIA Tel: +61 2 6288 6916 |
Created: 3 April 2021 - Last Amended: 13 November 2023 by Roger Clarke - Site Last Verified: 15 February 2009
This document is at www.rogerclarke.com/ID/IDM-O.html
Mail to Webmaster - © Xamax Consultancy Pty Ltd, 1995-2022 - Privacy Policy