Roger Clarke's Web-Site
© Xamax Consultancy Pty Ltd, 1995-2024

Infrastructure
& Privacy
Matilda
Roger Clarke's Web-Site© Xamax Consultancy Pty Ltd, 1995-2024 |

|
|||||
| HOME | eBusiness |
Information Infrastructure |
Dataveillance & Privacy |
Identity Matters | Other Topics | |
| What's New |
Waltzing Matilda | Advanced Site-Search | ||||
Revision of 24 September 2014
First presentation at a
Cyber
Security Law Seminar,
Intercontinental Hotel, Sydney, 13 November 2013
2nd presentation at a
seminar
for the Cyberspace Security and Privacy Laboratory (CySPri)
of the UNSW
School of Computer Science and Engineering,
Sydney, 14 August 2014
© Xamax Consultancy Pty Ltd, 2013-14
Available under an AEShareNet ![]() licence or a Creative
Commons
licence or a Creative
Commons  licence.
licence.
This document is at http://www.rogerclarke.com/EC/SSACS-13.html
The accompanying slide-set is at http://www.rogerclarke.com/EC/SSACS-13.pdf
There are many facets of information and IT security, and threats and vulnerabilities change continually. Safeguards exist that provide at least a reasonable degree of protection. So, with so much accumulated knowledge around, why are SMEs and consumers hung out to dry? Why aren't consumer devices delivered with convenient security facilities?
Nell picked up her new handheld, excited at the prospect of telling her friends about its new features. An avatar appeared on the screen, introduced itself as Secwhiz, and gently explained that a bit of housekeeping needed to be done. It chatted with her about the main things she intended to do with her handheld, and where she wanted to fetch her address-lists from. It offered to set a number of defaults on her device that would balance convenience and security about right for her. It outlined how she could change those settings later, and how she could override them when she wanted to, with the option to drill down for more details.
For Nell, Secwhiz needed to take account of a couple of sensitivities about personal data, particularly health data, and who was to have access to her current location. She also wanted a lot of care taken to keep apart not only her family and social networks, but also to segregate two incompatible groups of friends. The interactions were just interesting enough that her patience hadn't quite run out before Secwhiz completed the configuration process and relinquished control of the device.
[With thanks to Neal Stephenson for the loan of one of his characters in 'The Diamond Age' (Stephenson 1995).]
Many organisations are, or at least should be, capable of undertaking a rational approach to information and IT security. In Australia, for example, there are about 6,000 large business enterprises (LBEs) and 6,000 government agencies that are subject to general legal requirements in relation to risk management and that are subject to frequent cyber-attacks. In addition, perhaps 25,000 medium-sized business enterprises (MBEs), 50,000 small-to-medium enterprises (SMEs), and even some micro-Enterprises (uEs), have reasonable security expertise and safeguards in place.
Many other organisations, however, despite having considerable dependence on information and IT, have at best a hazy understanding of information and IT security. In Australia, these number perhaps 50,000 MBEs, 700,000 SMEs, and of the order of a quarter-million uEs, or close to 1 million organisations.
Meanwhile, millions of individuals use IT artefacts, and many people are highly dependent on them for economic purposes, and greatly attached to them for social purposes. With the explosion in smartphone usage since the launch of the iPhone in 2007, and tablet adoption since the launch of the iPad in mid-2010, a great many of them operate multiple IT devices, conduct transactions on them that have financial implications, and generate, store and disseminate a considerable amount of data, some of it sensitive.
At any given time, some 2-5% of the population are 'persons-at-risk', whose physical safety is dependent on their location not being apparent to one or more other individuals or organisations that bear a serious grudge against them (Clarke 2001b, UKICO 2009 p.19, GFW 2011). A proportion of these individuals are aware of security risks and take at least some steps to address them. But the vast majority of individuals, even those at risk, are ill-informed, ill-prepared, and exposed.
What have IT providers done to assist security-lax organisations, individuals at risk, and consumers generally? A little, but far from enough. This paper asks why not, and investigates ways in which the serious shortfalls might be overcome.
Business organisations don't lightly take on a responsibility to help the infirm. Their reason for existing is to make money for their investors. Measures that they invest in need to be perceived as 'a cost of being in the game', or must contribute and be seen to contribute to making money. If an argument is to be mounted for businesses to make security easy for their customers, then it's incumbent on the proponent to explain why they should do so. And that argument needs to be strong, because of the considerable challenges involved. The challenges include:
As a result of these challenges, providers of IT products and services face considerable costs in achieving reasonable degrees of security and of security-friendliness. Moreover, it's far from clear that enough customers will recognise the value of using a security-conscious vendor. If they don't, then they're unlikely to pay a sufficient margin to enable recoupment of the investment needed to deliver safer computing environments.
A gap therefore exists between what's needed and what exists. This is a 'market failure', and it's an important one. Even conservative economists agree that market failures need to be addressed by market interventions. So it's necessary to define the need in greater detail, to devise solutions to the problems, to consider what form or forms of intervention would be most appropriate, and to devise interventions that can be reasonably expected to achieve the desired results.
To provide structure to a large problem domain, the next section states the objective, then discusses approaches to defining a baseline level of security for organisations. Building on this, on several key security resources, and on prior research in the area, definitions are proposed for three levels of security profile for consumers. The final section assesses the prospects for both market-driven initiatives, and for market interventions, to achieve outcomes that can be both effective and Nell-friendly.
This section commences by clarifying the aim of the initiative. It then focuses on small organisations, providing an example of what such a definition might look like, and suggesting ways in which a satisfactory definition could be developed. The attention is then switched to individuals, and the scope expanded from baseline security to a comprehensive model.
Under the conventional security model, outlined in Appendix 1, security can't be an absolute, because there are too many threats and vulnerabilities, and ensuring protection against them costs resources. In order to determine what security measures are appropriate, it is necessary to appreciate the context of the organisation or individual. The objectives are to avoid, prevent or minimise harm arising from Acts of God, accidents and intentional acts, where that harm is judged to be readily avoidable, and to cope with the harm where it is not avoidable; but to balance the reasonably predictable financial costs and other disbenefits of safeguards against the less predictable and contingent financial costs and other disbenefits arising from security incidents.
Many organisations and some individuals have sufficient assets, and are subject to sufficient threats, that considerable care is warranted. Some organisations and some individuals, on the other hand, may judge the risks that they face to be sufficiently limited and/or mainstream that they may take quite limited precautions. Meanwhile, some organisations and most individuals simply don't, and won't, even think about security.
Given the contemporary environment of widespread use of IT for important transactions and communications, and the very limited extent to which security is embedded in IT artefacts and their use, it is simply negligent for any organisation, and for most individuals, to take no precautions at all. Safeguards need to be retro-fitted and grafted onto business processes, applications, systems software, devices and locations of use. This involves actions in relation to IT functionality, configurations, policies, human behaviour, and training.
To achieve these aims, opportunities need to be sought out and exploited. An opportunity arose in Australia during 2012-13 and again in mid-2014, when the Office of the Australian Information Commissioner (OAIC) undertook a revision of the 2001 edition of its 'Guide to Information Security'. This is meant to assist organisations to comply with the security safeguards Principles within the country's data protection law. The relevant Principles are Information Privacy Principle 4 (affecting the public sector 1988-2014) and National Privacy Principle 4 (affecting most of the private sector 2000-14). With effect from March 2014, these were superseded by Australian Privacy Principle 11 (applying to both the public and privacy sectors).
Submissions to the Privacy Commissioner relating to both submissions (APF 2012, Clarke 2013a, APF 2013, APF 2014) proposed that the revised edition of the Guide should:
When the 2013 version was published (OAIC 2013), it contained only quite modest amendments to the 2001 document. A further draft revision of mid-2014 (spurred by changes in the legislation) is not materially different. The document remains highly vague, with many uses of 'appropriate' (34 occurrences) and 'reasonable' (74 occurrences). It provides no indication of mandatory requirements, but merely discusses some 'steps and strategies which may be reasonable to take'. It includes brief mentions of a number of specific measures (such as access control, firewalls and vulnerability scanning), but all are merely factors to consider.
The opportunity for the Privacy Commissioner to have a material impact on the demonstrably low standards of data security in Australia was spurned. A later section considers other avenues through which the aims could be pursued.
This section adopts three different approaches to the problem, in order to provide an indication of the shape that meaningful guidance might take.
As an Appendix to the submission to the Privacy Commissioner mentioned above, the author provided a 2-page note on Information Security, addressed to small and medium-sized organisations (Clarke 2013b). This proposes that some security safeguards are so fundamental that an organisation is now at serious risk of being found negligent if it does not implement them all. The list proposed in that document is in Exhibit 1. The selection and the expression were somewhat arbitrary, but reflect safeguards that are widely regarded in the IT industry as being fundamental, and on priorities indicated by commercial and governmental sources, e.g. ASD (2013).
Extract from (Clarke 2013b)
Some of these, in particular, items 2-7, require that products and services be delivered with particular technical functionality that has to be installed, configured, and default-on. All involve (reasonably straightforward) organisational policies plus business process descriptions, which explain how to use the technical features to achieve a baseline level of protection against many of the most common accidents and exploitations of vulnerabilities. Item 9 also requires the provision of access to basic training materials.
The flavour of the particular set of safeguards in Exhibit 1 reflects its author's long background in corporate IT, and long use of desktop and portable devices. Organisational norms now reflect the 'untethered' nature of wireless communications. An alternative approach that is more consistent with the era of smartphones and tablets can be developed from an examination of Bring Your Own Device (BYOD) policies, and Mobile Device Management / Mobile Application Management (MDM/MAM) tools. The features implemented by leading, IT-savvy organisations could be studied, in order to extract a suitable list of baseline features.
A third approach that could be adopted is to undertake generic risk assessment and establish generic risk management strategies. Given the diversity of circumstances, some segmentation of the market for security guidance is essential. A possible framework for such a study is provided by Clarke (2008), which addressed the context of mobile payments. It catalogued threats and vulnerabilities relevant in the context of mobile payments, and analysed risk within the following framework:
There are considerably greater difficulties, however, in achieving a similar result for individuals. Consumer devices are massively insecure. The situation was summarised in Clarke & Maurushat (2007) as follows:
The subsequent explosion in smartphones and tablets has given rise to widespread use of 'apps' for functions previously performed using browsers, and hence the expression requires adaptation. The vulnerabilities, on the other hand, are little-reduced and in some cases they have been exacerbated.
As noted in Clarke & Maurushat (2007), "safeguards are available that address some of the threats and vulnerabilities. However, these safeguards:
"In order to take advantage of each particular safeguard, the user must do the following:
"Worse still, after the consumer has gone to all of that trouble, the safeguards are of limited effectiveness, because:
Is it possible to learn from the activities of IT-savvy organisations, in order to adapt the proposals for IT-ignorant organisations in the preceding section above, and to apply the insights to consumer contexts? In addition to being effective at addressing the worst of the vulnerabilities and threats, the solution would need to be scaled and simplified.
A comprehensive list of mainstream safeguards applied in IT-savvy organisations was prepared, reflecting prior research published in Clarke & Maurushat (2007), Clarke (2008) and Clarke (2011), and the primary Australian resources, the Defence/Australian Signals Directorate (DSD/ASD)'s Information Security Manual (ISM 2013), DSD/ASD's Mitigation Strategies (ASD 2013), DBCDE (2013a), DBCDE (2013b), OAIC (2013, pp. 15-23), and RACGP (2013).
Consumers are well-known to prioritise pleasure and convenience well above security. For safeguards to be adopted - or if they are default-on, then left in place - attention needs to be paid to usability. A considerable literature exists, e.g. Nielsen (1993), Whitten & Tygar (1999), Garfinkel & Miller (2005), Clark et al. (2007), Camp (2013). The sheer number of security-relevant features that require configuration is a particularly significant barrier. It is untenable for consumers to have to understand a large number of concepts, and to manually select large numbers of settings. The difficulties are compounded by consumer-hostile designs, such as settings unnecessarily scattered across many locations and levels, and by frequent changes by providers, to settings, and to the implications of settings. It is therefore necessary for devices to be configured automatically, and the number and complexity of user-interactions minimised.
An appropriate approach to achieve that end is to define a small set of Security Profiles, which comprise software installations, configurations and settings. Three such profiles might be a requisite number, referred to here as:
However, the Security Profiles are insufficient by themselves. The security arrangements need to have two further features:
The list of safeguards was accordingly split into three groups. As was the case with the 'absolute-minimum' set presented in Exhibit 1, the selection and expression are somewhat arbitrary, but reflect industry norms and governmental guidelines:
The consumer needs to be able to establish an initial configuration when they acquire a new device. Structured menus of settings, supported by defaults and explanations, will be suitable for a modest proportion of users, and demanded by some. For most, however, a 'user-friendly wizard', as depicted in the introductory vignette, would be essential. In addition, the user's profile needs to be sustained when updates occur, and the user's adjusted profile needs to be mirrored, and recovered when needed.
Finally, it would be impracticable to fully lock down a consumer device, because consumers would treat the security features as foe rather than as friend, and find ways to subvert them. Hence many settings need to be able to be overridden, both generally, but particularly for specific transactions or communications.
The analysis in this section suggests that practicable baseline-security and enhanced-security are much more challenging in the consumer than in the organisational contexts, but that stratifying safeguards into security profiles offers a way forward.
Can the market provide productised solutions that implement something like the features and services outlined in the preceding sections and the Appendices? And, if so, will they be affordable and accessible by the millions of small organisations and individuals that are the focus of this article?
One analysis (Winterford 2013, pp. 8-13), distinguishes several implementation flavours of 'Enterprise Mobility' solutions which endeavour to balance security and useability for corporate users:
Could such Enterprise Mobility solutions mature into effective solutions for IT-savvy organisations, and then be productised for IT-amateur organisations, and gradually become available and even mainstream for consumers? Unfortunately, the history of computing suggests mixed experiences with dependence on such a 'trickle-down effect'.
Although 'anti-virus software' is available, and has (slowly) expanded its scope to address additional forms of malware, even that sub-set of threats is not fully, conveniently and all-but-automatically addressed on all devices. After well over 30 years of desktop computing, and almost 30 years of portable/laptop computing, broader 'defensive computing' tools haven't arrived even in those segments, let alone in the still rapidly evolving smartphone and tablet environments.
Major challenges arise from the facts of ongoing technological developments, and highly competitive marketplaces, which together ensure that change is very rapid. Moreover, IT providers' business models are predicated on short product-lives of at most 2-3 years, and rapid rec-cycling of customers. In this environment, the technical contexts for which solutions are devised frequently disappear soon after the solutions are deployed.
If and when IT reaches a relatively stable plateau, a market-driven solution may emerge. On the other hand, security issues are already serious. It is untenable for millions of organisations and individuals to await that eventuality.
Market failure is evident, and a significant problem is not being addressed. The necessary conditions therefore exist to justify intervention. This section briefly assesses the several possible forms that intervention can take. The structure of this section reflects the model of regulatory forms outlined in Clarke & Bennett Moses (2014).
Although the IT industry is over 60 years old, it is subject to an immature legal framework. Hardware is subject to laws regarding merchantable goods and services and product liability. Software generally is not subject to those laws, unless it is intrinsic to the hardware. Most computers have in the past been sold as general-purpose devices. Providers have thereby generally escaped liability for even seriously inadequate software, unless it is so severe as to represent negligence, or is in breach of terms of contract.
There has been a rapid shift during the current decade towards the sale of computer-based appliances whose functions are restricted to a very few specific applications. This has the democratically undesirable effect of denying consumers access to general-purpose computing devices. However, it may also have the positive effect of removing the manufacturer's exemption from product liability laws. If so, then class actions against manufacturers relating to device insecurity might force them to take much greater care with their design of features and default settings. Alternatively, manufacturers may continue to escape that responsibility on the basis that the devices have at least some degree of extensibility through the download of 'apps', and/or because they have vastly greater market power than consumers, or avoid having a local footprint in jurisdictions with strong consumer rights laws, strong regulators and active litigants.
Law reform was considered a quarter-century ago (e.g. Clarke 1989), and has been considered from time to time since, with virtually no outcomes. The issue has seldom come before legislatures, and insecurity is not seen as a sufficient priority by public servants to warrant change. In the privacy arena, ample evidence exists that organisations are seriously lax in their handling of personal data, yet data protection oversight agencies have failed to impose specific requirements. Instead, debate revolves around weak data breach notification provisions which, even where they exist, do no more than confirm that organisations are seriously lax in their handling of sensitive data.
There appears to be little prospect in the short term that legislation will drive the emergence of facilities like those described in Appendices 2-4.
A regulatory model that has been much-discussed, but seldom effectively implemented, is referred to as 'co-regulation' (Clarke 1999). It involves a 'light touch' legislative framework that creates the scope for enforceable Codes to be established. In practice, however, such schemes as exist have generally been developed by industry sectors rather than negotiated among all stakeholders. Consumers are seldom well-represented in the development of such Codes, due to the lack of funding for analysis, preparation of submissions, and participation in events. Moreover, even when they are present, they have limited market power to achieve their objectives in relation to the Codes' nature, structure and content.
Some data protection oversight agencies have the capacity to approve industry Codes. In most such cases, however, the mechanism has been a failure. In Australia, for example, it appears highly unlikely that the legislative changes that came into effect in March 2014 will make any difference, because there is little incentive for industry associations to initiate Codes, and the Commissioner has no track-record of forcing the issue with industry sectors.
Some government agencies provide useful guidance for user organisations, e.g. DBCDE (2013a) and for consumers, e.g. DBCDE (2013b); but no expectation is created that providers should take any responsibility for even facilitating, let alone automating, the vital security safeguards described in the documents.
A further possibility for intervention to cope with market failure is recognition by industry as a whole, by one or more particular industry associations, or by one or more professional associations, that an initiative along the lines outlined in this paper is essential, followed by action to bring it into being.
To date, standardisation activities have been limited to 'process standards' of the 'quality seal-of-approval' variety, in particular the ISO 31000 series on generic risk management processes, the ISO 27000 series on IT Risk Management processes, and NIST (2011, 2012). One possibility would be for Standards Associations to move beyond process aspects and specify technical requirements. On the other hand, industry keeps other stakeholders well away from the standards formation process, and hence requirements are seldom specified that might intrude into providers' freedom to deliver insecure products.
Similarly, no signs of momentum towards facilities like those discussed in this paper are apparent in professional associations internationally (e.g. ACM, IEEE, ISSA, LOPSA) nor in Australia (e.g. ACS, ISOC-AU, SAGE-AU, AISA).
'Security Isn't Easier for SMEs and Consumers' because of market failure, matched by regulatory failure, and compounded by industry and professional failure.
Devices used by, and depended on, by millions of SMEs and consumers are seriously insecure. Many aspects of that insecurity are capable of being addressed. Action is needed to achieve that aim. Moreover, a large proportion of consumers are also employees, and their personal behaviour and habits are imported into their workplaces. With the growing implementation of BYOD policies, not just eConsumers' behaviour and habits, but also their devices, are being applied in the workplace. So eConsumer insecurity directly translates into eOrganisational insecurity. If no other driver exists, perhaps deleterious consequences for corporations and government agencies may provide the impetus that's needed for progress to be made towards 'easier security'.
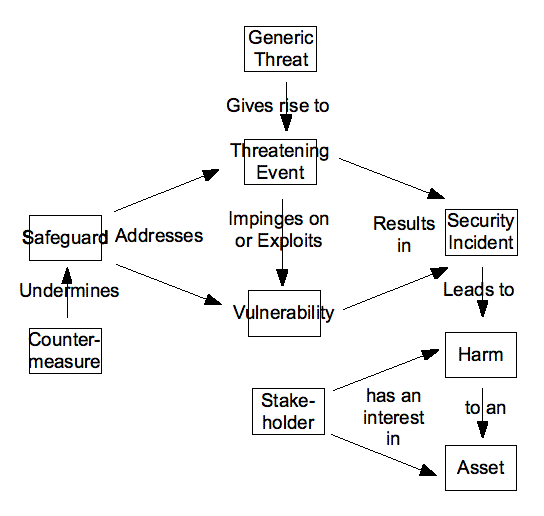
The conventional computer security model is adopted in this paper (e.g. Clarke 2001a, OECD 2002, ISO 2005, Yesudas & Clarke 2013). Under this model:
APF (2012) 'Information Security' Policy Statement, Australian Privacy Foundation, December 2012, at http://www.privacy.org.au/Papers/PS-Secy.html
APF (2013) 'Revised Guide to Information Security' Submission to the Privacy Commissioner, Australian Privacy Foundation, January 2013, at http://www.privacy.org.au/Papers/OAIC-InfoSecy-1301.pdf
APF (2014) 'Revised Guide to Information Security' Submission to the Privacy Commissioner, Australian Privacy Foundation, August 2014, at http://www.privacy.org.au/Papers/OAIC-InfoSecy-1408.pdf
ASD (2013) 'Strategies to Mitigate Targeted Cyber Intrusions' Australian Signals Directorate, April 2013, at http://www.dsd.gov.au/infosec/top35mitigationstrategies.htm
Camp L.J. (2013) 'Beyond usability: Security Interactions as Risk Perceptions' Proc. Workshop on Risk Perception in IT Security and Privacy, July 24-26, 2013, Newcastle, UK, at http://cups.cs.cmu.edu/soups/2013/risk/RiskWksp_Translucent.pdf
Clark J., van Oorschot P.C. & Adams C. (2007) 'Usability of Anonymous Web Browsing: An Examination of Tor Interfaces and Deployability' Proc. Symposium On Usable Privacy and Security, July 18-20, 2007 Pittsburgh, at http://cups.cs.cmu.edu/soups/2007/proceedings/p41_clark.pdf
Clarke R. (1989) 'Who Is Liable for Software Errors? Proposed New Product Liability Law in Australia' Computer Law & Security Report 5, 1 (May-June 1989) 28-32, at http://www.rogerclarke.com/SOS/PaperLiaby.html
Clarke R. (1999) 'Internet Privacy Concerns Confirm the Case for Intervention' Communications of the ACM 42, 2 (February 1999) 60-67, at http://www.rogerclarke.com/DV/CACM99.html
Clarke R. (2001a) 'Introduction to Information Security' Xamax Consultancy Pty Ltd, February 2001, at http://www.rogerclarke.com/EC/IntroSecy.html
Clarke R. (2001b) 'Research Challenges in Emergent e-Health Technologies' Xamax Consultancy Pty Ltd, July 2001, at http://www.rogerclarke.com/EC/eHlthRes.html#PAR
Clarke R. (2008) 'A Risk Assessment Framework for Mobile Payments' Proc. 21st Bled eCommerce Conf., June 2008, pp. 63-77, at http://www.rogerclarke.com/EC/MP-RAF.html
Clarke R. (2010) 'Re-Conceptualising Malware' Xamax Consultancy Pty Ltd, February 2010, at http://www.rogerclarke.com/II/RCMal.html
Clarke R. (2011) 'What Everyone Ought to Know About Passwords' Xamax Consultancy Pty Ltd, July 2011, at http://www.rogerclarke.com/II/Passwords.html
Clarke R. (2013a) 'Submission re the OAIC Guide to Information Security' Xamax Consultancy Pty Ltd, January 2013, at http://www.rogerclarke.com/DV/OAIC-ISGuide-130104.pdf
Clarke R. (2013b) 'Information Security for Small and Medium-Sized Organisations' Xamax Consultancy Pty Ltd, January 2013, at http://www.xamax.com.au/EC/ISInfo.pdf
Clarke R. (2013c) 'eConsumer Insecurity: Five Sensationalist Headlines, and Why They're True' Presentation to the Wirtschaftsinformatik Forum, University of Koblenz-Landau, Xamax Consultancy Pty Ltd, January 2013, at http://www.rogerclarke.com/EC/eCIS.html
Clarke R. & Bennett Moses L. (2014) 'The Regulation of Civilian Drones' Impacts on Public Safety' Computer Law & Security Review 30, 3 (June 2014) 263-285, PrePrint at http://www.rogerclarke.com/SOS/Drones-PS.html
Clarke R. & Maurushat A. (2007) 'The Feasibility of Consumer Device Security' J. of Law, Information and Science 18 (2007), PrePrint at http://www.rogerclarke.com/II/ConsDevSecy.html
DBCDE (2013a) 'Stay Smart Online - Business' Dept of Broadband Communications and the Digital Economy, 2013, at http://www.staysmartonline.gov.au/business
DBCDE (2013b) 'Stay Smart Online - Home Users' Dept of Broadband Communications and the Digital Economy, 2013, at http://www.staysmartonline.gov.au/home_users
Garfinkel S. & Miller R.C. (2005) 'Johnny 2: A User Test of Key Continuity Management with S/MIME and Outlook Express' Symposium On Usable Privacy and Security, July 6-8, 2005 Pittsburgh, at http://cups.cs.cmu.edu/soups/2005/2005proceedings/p13-garfinkel.pdf
GFW (2011) 'Who is harmed by a "Real Names" policy?' Geek Feminism Wiki, undated, apparently of 2011, at http://geekfeminism.wikia.com/wiki/Who_is_harmed_by_a_%22Real_Names%22_policy%3F
ISM (2013) 'Information Security Manual' Defence Signals Directorate, August 2013, at http://www.dsd.gov.au/infosec/ism/index.htm
ISO (2005) 'Information Technology - Code of practice for information security management', International Standards Organisation, ISO/IEC 27002:2005
Nielsen J. (1993) 'Usability engineering' Morgan Kaufmann, 1993
NIST (2011) 'Managing Information Security Risk: Organization, Mission, and Information System View' National Institute of Standards and Technology, SP 800-39, March 2011, at http://csrc.nist.gov/publications/nistpubs/800-39/SP800-39-final.pdf
NIST (2012) 'Guide for Conducting Risk Assessments' National Institute of Standards and Technology, SP 800-30 Rev. 1, September 2012, at http://csrc.nist.gov/publications/nistpubs/800-30-rev1/sp800_30_r1.pdf
OAIC (2013) 'Guide to Information Security' Office of the Australian Information Commissioner, April 2013, at http://www.oaic.gov.au/privacy/privacy-resources/privacy-guides/guide-to-information-security
OECD (2002) 'OECD Guidelines for the Security of Information Systems and Networks: Towards A Culture Of Security' Organisation For Economic Co-Operation And Development, July 2002, at http://www.oecd.org/dataoecd/16/22/15582260.pdf
RACGP (2013) 'Computer and Information Security Standards' Royal Australian College of General Practitioners, 2nd Edition, June 2013, at http://www.racgp.org.au/your-practice/standards/ciss/
Stephenson N. (1995) 'The Diamond Age' Bantam, 1995
UKICO (2009) 'Privacy impact assessment (PIA) - handbook' Information Commissioner's Office, United Kingdom, June 2009, at http://www.ico.org.uk/pia_handbook_html_v2/files/PIAhandbookV2.pdf
Whitten A. & Tygar J. (1999) 'Why johnny can't encrypt: A usability evaluation of pgp 5.0' Proc. 8th USENIX Security Symposium, vol. 99, 1999, at http://gaudior.net/alma/johnny.pdf
Winterford B. (2013) 'The True Cost of BYOD' itNews, August 2013, at http://www.itnews.com.au/Resource/358142,the-true-cost-of-byod.aspx
Yesudas R. & Clarke R. (2013) 'Framework for Risk Analysis in Smart Grid: Perspective Based Approach' Proc. 8th Int'l Conf. on Critical Information Infrastructures Security (CRITIS 2013), Amsterdam, 16-18 September 2013, at http://www.rogerclarke.com/EC/SG-FRA.html
Roger Clarke is Principal of Xamax Consultancy Pty Ltd, Canberra. He is also a Visiting Professor in the Cyberspace Law & Policy Centre at the University of N.S.W., and a Visiting Professor in the Research School of Computer Science at the Australian National University.
This work has benefited from collaborative work with Arash Shaghaghi, a PhD candidate in UNSW CSE, in particular in relation to a Working Paper on 'Key Factors in the Limited Adoption of End-User PETs'.
| Personalia |
Photographs Presentations Videos |
Access Statistics |
 |
The content and infrastructure for these community service pages are provided by Roger Clarke through his consultancy company, Xamax. From the site's beginnings in August 1994 until February 2009, the infrastructure was provided by the Australian National University. During that time, the site accumulated close to 30 million hits. It passed 65 million in early 2021. Sponsored by the Gallery, Bunhybee Grasslands, the extended Clarke Family, Knights of the Spatchcock and their drummer |
Xamax Consultancy Pty Ltd ACN: 002 360 456 78 Sidaway St, Chapman ACT 2611 AUSTRALIA Tel: +61 2 6288 6916 |
Created: 19 August 2013 - Last Amended: 24 September 2014 by Roger Clarke - Site Last Verified: 15 February 2009
This document is at www.rogerclarke.com/EC/SSACS-13.html
Mail to Webmaster - © Xamax Consultancy Pty Ltd, 1995-2022 - Privacy Policy