Roger Clarke's Web-Site
© Xamax Consultancy Pty Ltd, 1995-2024

Infrastructure
& Privacy
Matilda
Roger Clarke's Web-Site© Xamax Consultancy Pty Ltd, 1995-2024 |

|
|||||
| HOME | eBusiness |
Information Infrastructure |
Dataveillance & Privacy |
Identity Matters | Other Topics | |
| What's New |
Waltzing Matilda | Advanced Site-Search | ||||
Version of 30 November 2013
Original draft for the Internet Technical Advisory Committee (ITAC), final version published in the December 2013 Newsletter
© Xamax Consultancy Pty Ltd, 2013
Available under an AEShareNet ![]() licence or a Creative
Commons
licence or a Creative
Commons  licence.
licence.
This document is at http://www.rogerclarke.com/SOS/OECDS-1311.html
The Organisation for Economic Co-operation and Development (OECD) is a vehicle for collaboration among primarily developed countries in order to achieve economic prosperity. It has delivered value in that area, but its interest in the social dimension of humanity has always been much more muted. It's clear that a person who is starving has little concern for higher values. But, in the Maslowian hierarchy of needs, security of family and friendship emerges only a little above security of life. Social interests emerge and rapidly increase in importance as people's economic wellbeing improves. The OECD should have long ago shifted social matters much further up its priority scale.
The continuing dominance of economic over social values inherent within the OECD's structures, values and processes creates challenges when a multi-faceted issue like security is addressed. Economic prosperity is seen to be dependent on stable nations nurturing freedoms for corporations that exploit assets to generate revenue. So the focus of security is naturally on the kinds of assets that corporations value, and that governments consider to underwrite stability.
The OECD is revisiting the Security Guidelines that it first published over a decade ago (OECD 2002). To its credit, it has involved civil society. NGOs are able to review drafts and comment on them. What we find, however, is that the ship is steaming confidently in a direction, and that its direction needs to be adapted; but the vessel is large and slow to turn, and the officers and crew are naturally resistant to change, particularly fundamental changes in values.
The notion of security is much-discussed, but people often talk past one another, because their fields of view are so different. Ambiguities of scope and perspective need to be overcome. To ensure that the conversation is grounded, each participant needs to declare to the others their answer to the two-part question 'Security of what, and for whom?'.
The focus of the OECD Guidelines of 2002 was the 'Security of Information Systems and Networks'. In recent presentations in Copenhagen and Oxford, I used a visual aid to convey a range of alternative scope definitions within this field (Clarke 2013):
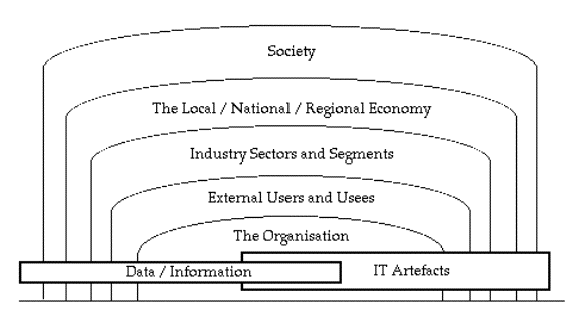
At the deepest level, the assets in focus are data, and information technology artefacts that perform useful functions. (In other contexts, similar models can be constructed with, say, physical artefacts at the centre, e.g. transport and communications infrastructure, or human resources, e.g. key executive, operational or creative staff). At more abstract levels, the asset whose security is to be assured may be an organisation, an industry (particularly those designated as critical infrastructure industries), a geographically-defined economy, or a society. A comprehensive model needs to extend beyond the set in the diagram to the levels of the biosphere (because otherwise climate change cannot be fully assessed) and humanity (to enable discussions about colonies elsewhere in the galaxy, and a Spaceshield to address the planet's vulnerability to asteroid impact).
The OECD's 2002 Guidelines addressed only the deepest level of the 'alternative scope definitions' hierarchy depicted in the diagram. The OECD's current work is intended to have broader scope "by realigning their perspective and language with the high-level economic and social objectives pursued by governments, businesses and individuals in the development of cybersecurity policies". Again, the OECD is to be congratulated on moving to encompass more than just the technical aspects that it addressed a decade ago. But is it moving far enough? And will its new approach have sufficient scope to serve the world's needs for the next decade?
A vital corollary arising from alternative scope definitions is that tensions exist between the interests at different levels and between different stakeholders. Sometimes the tensions can be constructively addressed. Ways may be found for all parties to satisfy their needs, or trade-offs may be negotiated that reasonably accommodate the various concerns. In other cases, however, the interests are in direct conflict, the field of play has the nature of a zero-sum game, and the powerful prevail.
One simple example of a tension is the problem of 'botnets'. A bot doesn't harm its host, so the host's owner has no incentive to fix it. (In the language of one particular discipline, this is an `externality'). Tension exists between the owner of the vulnerable device and the owners of other devices whose security is threatened by the botnet. Similarly, data breach notification initiatives have been necessary in order to force organisations to recognise that not only their own perspective on security is at issue, but so is the perspective of their customers. Another example arises in relation to copyright material distributed over peer-to-peer networks. Corporations concern themselves solely with the security of their copyright works, and expect parliaments to grant them the authority to breach what Internet service providers and their customers justifiably perceive to be important security interests that compete against the corporations' interests and that need to be carefully considered, not trampled over.
A currently very topical tension arises from the activities of nation-states that actively undermine the security of information infrastructure, through such means as trapdoors in backbone routers, government-sponsored spyware and denial of service attacks, and contrived weaknesses in cryptographic standards. In this case, the security of all lower layers in the diagram are actively undermined, justified by the vague excuse of 'national security'.
One definition of that term is "The protection of a nation from attack or other danger by holding adequate armed forces and guarding state secrets". In practice, national security has been preoccupied, particularly since 2001, with some fairly specific concerns:
In each of these cases, a meaningful dialogue cannot be achieved if each stakeholder clings to their own perspective, and insists on their security being paramount and everyone else's security being secondary or even illegitimate. A mainstream example of this attitude is the national security mythology of 'you can have security or privacy; but you can't have both'.
A particular concern during discussions about revision of the OECD Security Guidelines has been the need to recognise External Users and Usees as having an important perspective that is commonly lacking from discussion, or is seriously undervalued. The term 'users' is commonly applied to individuals within an organisation who 'use' the organisation's data and IT artefacts in their work. During the last 30 years, systems have become 'extra-organisational', and many people outside an organisation are users of the organisation's systems. The serve-yourself approach that proved successful with ATMs and EFTPOS has been extended to 'external users' in circumstances as diverse as web-commerce, eGovernment and libraries. Meanwhile, many individuals are affected by systems, and hence are stakeholders, even though they are not participants. Prominent examples include law enforcement intelligence databases, consumer profiling databases and financial transaction reporting schemes. Discussions in the socio-technical field apply the term 'usees' to such people. External users and usees always lack institutional and market power, and their interests have suffered greatly during the period of national security extremism that followed 9/11.
If the OECD's revision of its Security Guidelines is to satisfy social as well as economic needs, it must:
The OECD is to be congratulated on ensuring that the Expert Group includes representatives of civil society, and that they have access to documents in advance, and at least some voice - although, as is so often the case, physical participation in meetings is hampered by a lack of budget for the time and travel costs of the professionals who represent the interests of external users and usees. The key test is yet to come, however: will the revised Security Guidelines satisfy the needs of the public, or will governments and corporations ensure that important issues like those discussed in this piece are sidelined, in effect treating them as pleasant intellectual diversions whose real function is to enable NGOs to hear the sounds of their own voices in the corridors of power?
In the past, governmental and corporate interests have in a great many cases been able to achieve their desired outcomes without having to publicly explain or justify the rationale for their demands. The particular trade-offs among interests that have been imposed have benefited security technology providers, and have enabled national security and law enforcement agencies to provide the appearance of protection. Many of the technologies and schemes have been highly ineffective, as documented in many critiques provided by analysts such as Bruce Schneier and Ross Anderson.
For the outcomes to be better this time around, the process of public policy formation needs to satisfy a set of criteria. One set of such 'meta-principles' specifies requirements for evaluation, consultation, transparency, justification, proportionality, mitigation, controls, and audit (APF 2013). These criteria need to be applied to the process whereby the revised OECD Security Guidelines are produced. They also need to be embodied within the core concepts, principles and processes that the Guidelines recommend. Typical problems that are readily identified by applying the meta-principles are inadequacies in the scope of stakeholder groups that are engaged, and the tendency of standard formulations to limit consultation to major players rather than specify inclusiveness.
The world is at something of a tipping-point in the emergence of forms of world government. At one extreme is the appallingly anti-democratic, almost feudal, approach adopted by governments in the Trans-Pacific Partnership (TPP) process, which has breached every one of the eight meta-principles. In the field of Internet Governance, the reasonable desire for more effective internationalisation of existing arrangements is seeing a battle between an inclusive, 'multi-stakeholder' approach through the Internet Governance Forum (IGF) process, on the one hand, and a narrow and repressive approach involving tight governmental controls, being pursued through the International Telecommunication Union (ITU).
Where will the new OECD Security Guidelines lie on the scale? Will the OECD seek to sustain the dominance of governments and corporations over policy agendas, or will it point towards a better future in which the eight meta-principles are applied, and security's many scope-definitions and stakeholder perspectives are reflected.
APF (2013) 'Meta-Principles for Privacy Protection' Australian Privacy Foundation, April 2013, at http://www.privacy.org.au/Papers/PS-MetaP.html
Clarke R. (2013) 'Whose Security? The Politics of Alternative Scope Definitions' Xamax Consultancy Pty Ltd, 2013, at http://www.rogerclarke.com/EC/WS-1301.html
OECD (2002) 'OECD Guidelines for the Security of Information Systems and Networks: Towards a Culture of Security' Organisation for Economic Co-operation and Development, at http://www.oecd.org/dataoecd/16/22/15582260.pdf
Roger Clarke is Principal of Xamax Consultancy Pty Ltd, Canberra. He is also a Visiting Professor in the Cyberspace Law & Policy Centre at the University of N.S.W., and a Visiting Professor in the Research School of Computer Science at the Australian National University.
He is also Secretary of the Internet Society of Australia (ISOC-AU), and Chair of the Australian Privacy Foundation (APF). He has also contributed to discussions in the Civil Society Informatoin Society Advisory Council (CSISAC).
He has valued the opportunity to provide input to the OECD Security Expert Group supporting the Working Party on Information Security and Privacy and OECD staff who are developing the Guidelines. But he remains unsure whether his input will have any effect, given the power-imbalance inherent in the process.
| Personalia |
Photographs Presentations Videos |
Access Statistics |
 |
The content and infrastructure for these community service pages are provided by Roger Clarke through his consultancy company, Xamax. From the site's beginnings in August 1994 until February 2009, the infrastructure was provided by the Australian National University. During that time, the site accumulated close to 30 million hits. It passed 65 million in early 2021. Sponsored by the Gallery, Bunhybee Grasslands, the extended Clarke Family, Knights of the Spatchcock and their drummer |
Xamax Consultancy Pty Ltd ACN: 002 360 456 78 Sidaway St, Chapman ACT 2611 AUSTRALIA Tel: +61 2 6288 6916 |
Created: 30 November 2013 - Last Amended: 30 November 2013 by Roger Clarke - Site Last Verified: 15 February 2009
This document is at www.rogerclarke.com/SOS/OECDS-1311.html
Mail to Webmaster - © Xamax Consultancy Pty Ltd, 1995-2022 - Privacy Policy