Roger Clarke's Web-Site
© Xamax Consultancy Pty Ltd, 1995-2024

Infrastructure
& Privacy
Matilda
Roger Clarke's Web-Site© Xamax Consultancy Pty Ltd, 1995-2024 |

|
|||||
| HOME | eBusiness |
Information Infrastructure |
Dataveillance & Privacy |
Identity Matters | Other Topics | |
| What's New |
Waltzing Matilda | Advanced Site-Search | ||||
Principal, Xamax Consultancy Pty Ltd, Canberra
Visiting Fellow, Department of Computer Science, Australian National University
Notes to accompany a presentation to staff of the Australian Intellectual Property Office, 24 March 1999
© Xamax Consultancy Pty Ltd, 1999
The copiously hot-linked canonical version of this document is at http://www.rogerclarke.com/II/Issues99.html
The 'killer app' of the mid-1990s, the World Wide Web, drove the Internet out of the relative obscurity of academic usage. It's become so mainstream that young people are now quite perturbed when someone suggests to them that their research might need to encompass some additional sources.
A few years ago there was much discussion about an abstract notion called 'the information infrastructure'. The Internet is the information infrastructure that we've got; and a theme of this paper is that we should be working very hard to make the most of it. At the turn of the millenium, we should be focusing far less on short-term challenges like the Y2K demonology, and far more on the patterns that will shape our work and play in the decades ahead, and determine the relative and even absolute levels of financial wellbeing we achieve.
This short paper, designed as an accompaniment to a lunchtime talk, identifies some of the many issues that are alive, right now, and which need to be addressed, right now. The tensions can be thought of in the manner depicted in the following diagram. The following sections are structured to reflect, what, at the moment, looks far too much like a vicious circle.
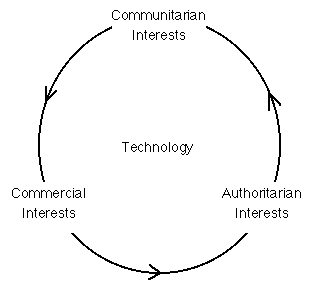
The foundation of the Internet is of course its technology. Newcomers might like to read an introduction-by-analogy. Readers who already have some understanding of how it works might like to use a primer on Internet technology.
The origins of the Internet lie in an experiment. The U.S. defense establishment sought a network architecture that would be robust in the face of nuclear attack. Prior to the emergence of the then ARPANet in 1969, all networks were essentially centralised (using a 'star-topology'). That made them vulnerable to the disablement of a few key components and connections (whether by military action or by accident). ARPANet, and its successors based on TCP/IP protocols (or, more generally, the Internet Protocol Suite), are far less vulnerable, because redundancy is built in, and software in the computers on the network identifies malfunctioning connections and routes traffic around them. As a result, multiple failures would have to occur before the service seriously degraded or ceased to function.
Internet architecture is therefore inherently non-centralised. Reflecting that style, no single authority exists that 'runs' the Internet. Internet governance is in fact quite complex, participative and consensual. Governments, primarily to date the U.S.government, influence it, but do not dominate it. Associated with this has non-centralised nature been a state-of-mind that people commonly refer to as 'anarchic'. This is not used in the sense of 'chaos' or 'disorder', but simply in the political sense of the absence of direct or coercive authority.
The history of the Internet since 1969 is increasingly well-documented, whereas the history of the Internet in Australia, which stretches back to the early 1970s, but commenced in earnest in 1989 for research use, and in 1992 for more general community use, is, as yet, remarkably poorly documented.
The Internet is, however, much more than just a technology.
What has become the Internet has long been used for person-with-computer communications (remote login - telnet, file transfer - ftp, and much later the gopher and the web protocols), and for computer-to-computer communications. In terms of volume of data transferred, telnet was only overtaken in 1994 (by the web).
Communication among people has always been important, however. The earliest applications were email, then emailing lists (e-lists) from the mid-1970s. Bulletin board systems (BBSs) and newsgroups developed independently of the Internet, but newsgroups later came to be disseminated predominantly over the net. MUDs started in 1979, Internet Relay Chat (IRC) in 1988. Web-chat and ICQ came much later.
It was clear even before the explosion of the web that the Internet promised a great deal of assistance to the practice of research. The enormous freedom felt by pioneers has resulted in expectations of specific freedoms being and remaining available to netizens. A particular ethos arose.
One approach to gaining an understanding of the-Internet-in-use is through fiction and aphorisms, and another is through metaphors. John Perry Barlow was responsible for many of the clearest statements of the 'electronic frontier' mentality, such as his 'Declaration of the Independence of Cyberspace' of 1996.
Especially in the early days of electronic communication tools, there were many instances of what people tend to think of as dysfunctional human behaviour on the net. This resulted in the adoption of the term 'netiquette' (previously used in the context of organisation-internal local area networks) to refer to the community's expectations or moral code of behaviour. A specific example of the care that needs to be taken to balance the interests of the various parties is provided by an analysis of privacy and e-lists.
The clusters of people using the Internet coalesced into a 'virtual community'. The clearest description of this idea was provided in Howard Rheingold's book of that name, published in 1994. I find the term cyberculture more useful, to refer to the means whereby communities in cyberspace can achieve cohesion and maintain relationships, while avoiding unduly dysfunctional behaviour by community-members and outsiders. Cyberculture is worthy of much more careful analysis.
Subsequently, there were successive dilutions of the foundation ethos, as successive waves of 'newbies' arrived. This initially led many longstanding netizens to feel concern about what was happening to the neighbourhood. Some years later, it would seem that the ethos is surviving, with a sufficient proportion of the newcomers undergoing conversion, sometimes becoming more fervent disciples than their predecessors.
By 1994, the technical developments, and the population growth, had attracted the attention of entrepreneurs, who quickly became excited about the opportunities to exploit the new medium.
Unfortunately, they showed then, and continue to show now, an inability to detect that the Internet isn't a broadcast medium, and that net-consumers aren't watching a mind-numbing TV screen. The successive waves of marketer zeal have shown no signs of succeeding, yet no signs of abating either. Fashions that have come and gone have included closed electronic communities, push technology, info-mediaries, and portals.
A particular example of marketer excess that has attracted a great deal of negative comment has been unsolicited emails, or spam. It is abundantly clear that, whether or not direct marketing via the post and the telephone continues in its present, scarcely-constrained 'opt-out' form, email marketing will very quickly be limited to an 'opt-in' scheme. This does not deny the feasibility of marketing on the net, because there are other, more appropriate means of doing so. Recent attempts by direct marketing interests to consolidate their position have been subjected to trenchant criticism by the Australian Computer Society.
Another problem-area has been a technique, introduced originally by Netscape, to assist in the maintenance of 'sessions' between clients and servers. These so-called cookies were introduced without the conventional consultation processes, or even publicity, and were not well-conceived. They have attracted opprobrium, and great care is needed in applying them.
The key to a breakthrough in electronic commerce is recognition by businesses of the importance of trust in general, and Internet privacy in particular. The level of public concern worldwide is sufficient that the few remaining economically advanced nations that have no privacy protections in the private sector (primarily the U.S.A. and Australia) are now recognising the need to act. The Australian Government is in the process of implementing its 1996 commitment to a co-regulatory regime.
The most successful form of electronic commerce to date has brought its own problems. As occurred with the French Teletext service, Minitel, pornography has been a substantial money-earner, offering graphic titillation at the privacy of one's own workstation. This has attracted attention not only from enthusiasts, but also from people disgusted by its mere availability, and by the ease with which it can be discovered.
John Perry Barlow's 'electronic frontier' imagery was borne out: the first wave of settlers were very much 'cowboys', in 'rape-and-pillage' mode. This quickly led to aggressive self-defence, posses, summary justice, and calls for sheriffs.
One of the expectations was that at least the kinds of consumer protections available in the real world would be sustained. To that has been added calls for privacy protections.
A reactionary initiative was the call, particularly by the moral right-wing, for their values to be imposed on everyone else. The primary concerns have been pornography in general, and child pornography in particular; and instruction in violence in general, and bomb-recipes in particular. Meanwhile the moral left-wing has called for suppression of such materials as racist sentiment, and denial of the factual basis for the Nazi persecution of the Jews. The focus often falls on Internet access by children (which gave rise to the 'porn in kiddies' bedrooms' furore).
There is a long history of attempts to impose regulation on content flowing over the Internet. The law is already complex, and some aspects of it are seriously intrusive and, at least in part, seriously dysfunctional. In some jurisdictions, for example, there is a defenceless offence of possession of child pornography.
There have been attempts to establish mechanisms for filtering materials, either on the basis of the transmission's content, or the classification that someone has given it. This has resulted in a web standard (PICS), and a variety of filtering products and services. These commonly block access to large numbers of 'clean' sites, in the process of denying access to a modest proportion of 'dirty' ones. An examination of the experience in Utah is salutary.
In the university sector, analysis was undertaken, and a positive approach adopted. A succession of drafts of an industry association code of practice have attracted serious criticisms from public advocacy groups such as Electronic Frontiers Australia. The industry body stands accused of pandering far too much to the interests of politicians interested in imposing tight constraints on net freedoms, and of paying far too little attention to the needs of its members' customers.
The Internet harbours sufficient threat to the status quo that other interest groups have also flexed their muscles, and sought special treatment by legislatures. Important among these have been large publishers, who have accumulated substantial holdings of intellectual property, especially copyright materials. They have successfully lobbied for international and national action to further entrench existing protections, to extend them, and to criminalise acts that they perceive to offend those interests. The application of copyright law to the new context has substantial implications for net-users, and for society and the economy as a whole.
Public interests have been under threat since the emergence of the public Internet, and calls have been made for policy measures to reflect the public's interest. The Internet must be recognised as an 'extra-organisational system' that extends beyond organisations to link individuals, and is quite different from its predecessor inter-organisational and multi-organisational systems.
Incursions by both commerce and government conflict with the communitarian ethos, which seeks to undertake self-regulation. On the other hand, most netizens continue to expect law and order to be sustained within existing geographical jurisdictions (i.e. 'in meatspace').
One of the many important applications of the net is as a means of organisation among citizens and consumers. Application of early lessons, catalogued in places like NetAction, is resulting in what Galbraith referred to as 'countervailing power'. The balance points between large corporations, government agencies and governments, on the one hand, and public interest advocates and community representatives on the other, has changed, and may continue to do so.
Over time, even more fundamental changes may occur in political processes, because the Internet shows representative democracy to have been a measure appropriate for an era of slow transport and limited telecommunications, but out of kilter with the modern world. It has a natural affinity with that dangerous beast: direct democracy.
In the meantime, however, there is considerable concern about whether access to the information infrastructure, and to services and information available over it, will be equitable across all segments of the population. Possible bases for discrimination include:
This in turn brings attention to bear on the question of participation by netizens in the formation of policy relating to the information infrastructure. In addition to the inevitable debates about cross-subsidisation and telco 'universal service obligations', there is also a fear that governments may (directly or indirectly) grant favoured corporations excessive rights to monopoly spaces. The public interest lies in ensuring a contestable market, and diversity of supply to match the diversity of need. This in turn implies the need for open standards, including open source licensing.
Underpinning all of these considerations is the technology of the Internet. Technology can be progressively adapted to reflect needs, but only if the bodies responsible for the various aspects are able to reach consensus. Moreover, new versions of the primary protocols are released only occasionally, because of the challenges involved in migrating the operations of a vast and non-centralised network.
In the meantime, add-on technologies can be devised to address some of the inadequacies. Examples include:
Meanwhile, the threat looms of telcos that release bandwidth too slowly, in order to sustain artificially high prices for communications, that price higher-capacity ISDN and cable beyond the reach of the public and small business, and that continue to apply broadcast and cable TV mentalities in an era whose keynotes are dispersion, interactivity and non-centralised initiative.
There is a risk that we may have been enjoying a brief period in which the open public Internet is king.
The boom in share prices of vapid startups like Yahoo! will be followed by bust. If business doesn't quickly learn about the new medium, there may well be a flight of capital from the Internet, and a resumption of investment by businesses in closed networks whose architecture is less open and more proprietary, and whose inherent patterns are more 'push' and less 'pull', and more' broadcast' and less 'interactive'.
It is in the communitarian interest to help commercial interests apreciate much more quickly the nature of the net, such that they can build effective businesses. Communities and profit-motivated enterprises co-exist in the physical world and they can in the virtual world as well; but not if the knuckle-headed marketing approaches continue. There needs to be a willingness on the part of business enterprises if reconciliation between electronic communities and electronic commerce is to be achieved.
As suggested by the diagram around which this short paper has been built, I believe that the communitarian interests are primary, and that the commercial and authoritarian interests need to appreciate and align themselves with them, rather than trying to continue the rape-and-pillage.
My publications on information infrastructure matters are categorised by theme; and new works are indexed progressively. A foundation work analyses the policy considerations arising in relation to the information infrastructure notion. Materials are also provided on electronic commerce and dataveillance and privacy.
| Personalia |
Photographs Presentations Videos |
Access Statistics |
 |
The content and infrastructure for these community service pages are provided by Roger Clarke through his consultancy company, Xamax. From the site's beginnings in August 1994 until February 2009, the infrastructure was provided by the Australian National University. During that time, the site accumulated close to 30 million hits. It passed 65 million in early 2021. Sponsored by the Gallery, Bunhybee Grasslands, the extended Clarke Family, Knights of the Spatchcock and their drummer |
Xamax Consultancy Pty Ltd ACN: 002 360 456 78 Sidaway St, Chapman ACT 2611 AUSTRALIA Tel: +61 2 6288 6916 |
Created: 23 March 1999 - Last Amended: 24 March 1999 by Roger Clarke - Site Last Verified: 15 February 2009
This document is at www.rogerclarke.com/II/Issues99.html
Mail to Webmaster - © Xamax Consultancy Pty Ltd, 1995-2022 - Privacy Policy