Roger Clarke's Web-Site
© Xamax Consultancy Pty Ltd, 1995-2024

Infrastructure
& Privacy
Matilda
Roger Clarke's Web-Site© Xamax Consultancy Pty Ltd, 1995-2024 |

|
|||||
| HOME | eBusiness |
Information Infrastructure |
Dataveillance & Privacy |
Identity Matters | Other Topics | |
| What's New |
Waltzing Matilda | Advanced Site-Search | ||||
Version of 14 June 2013
Proc. 8th Int'l Conf. on Critical Information Infrastructures Security (CRITIS 2013), Amsterdam, 16-18 September 2013
Rani Yesudas and Roger Clarke **
© Rani Yesudas and Xamax Consultancy Pty Ltd, 2013
Available under an AEShareNet ![]() licence or a Creative
Commons
licence or a Creative
Commons  licence.
licence.
This document is at http://www.rogerclarke.com/EC/SG-FRA.html
Smart Grids have great potential for the management of energy consumption. However, moving from a traditional grid to a smart grid introduces significant new risks to the energy sector that were not present in the power grids that operated in isolation. The data that is generated in the smart metering systems can possibly harm its stakeholders. Hence it is important to protect all the stakeholders by providing effective controls to the vulnerable elements in the smart metering system. This highlights the necessity to conduct a risk analysis to evaluate the harms, threats and vulnerabilities that are introduced into this critical infrastructure by modernization. Currently there are numerous risk analysis methodologies available; there are many differences among them, and hence selecting an appropriate one is challenging. Risks that technical experts perceive to be minor often elicit strong public concerns. Consequently during risk analysis, different perspectives need to be considered. This article reports on an extensive analysis of risk management frameworks, which resulted in a framework specifically targeted at smart metering systems. Perspective of risk analysis is a key element in this framework.
Smart grids, including smart meters, offer great promise for the efficient management of energy. However, concerns remain about the security of smart meter designs, and the potential negative impacts on householder privacy. These could slow adoption of the technologies, and threaten return on the considerable investments involved.
Like any infrastructure, smart grid is also prone to attacks. Moving systems from a manual process to an automated process creates new vulnerabilities. As systems are added, complexities and functionalities increase making it more difficult to address security. Increasing connection to previously isolated systems and networks expands the threat surface. Connection points between different networks become access points for interception and for the infiltration of malware. The dependence on networking technologies introduces new threats to service reliability [1].
Confidentiality, integrity and availability are the commonly used terms in security. In the electrical power system, availability of electricity is considered as the most critical element and a disruption in communications can cause blackout to a vast region. So a secure power grid should have the best control measure to ensure that availability of electricity is protected. Secondly, a smart grid uses data collected by various sensors and agents and this data is used for number of functionalities which include automated billing, peak usage determination, power outage tracking etc. The integrity of this data is very important. Unauthorized modification of the data or insertion of data from unknown sources can cause loss and damage to the system. Next is confidentiality. Customer information, general corporation information, and electric market information are some of the areas that need to be confidential. In smart grid, detailed information of electricity usage is recorded in the smart meter and this information is transmitted at certain intervals to the remote system via different communication method [2].
Having identified availability as the priority in a power system, does not deem integrity and confidentiality as elements of less importance. For a smart grid all the components are equally important. Hence the system should ensure that the customer privacy is not violated and that the consumer is well informed of what could happened to their utility usage and personal data. Ultimately it will be the consumer who will have to bear the cost of running such a system and if the system can't guarantee safety and security they can backlash the system with the help of consumer advocacy groups. Risks that technical experts perceive to be minor, and even non-existent, often elicit strong public concerns and have even resulted in systems being discarded after huge investments have been made [3].
In various countries, after the initial roll out of smart metering systems there have been protests and demonstrations against them. The main reasons for their protests have been media reports regarding health hazards and privacy breaches that smart meter causes to its consumers. The smart meter has been described as a `spy in the home' [4]. This was based on a report that found that detailed smart meter data at one-minute intervals could provide insights into a household's living patterns to the extent that it could reveal the appliances used and activities conducted by the household [5]. It was completely misleading, as mostly the smart meters were read on half-hourly basis and it was almost impossible to deduce such information. Even if the meter read was done at one minute interval, detailed knowledge of the appliances present in the home and the habits of the consumer would be required to deduce living patterns [4]. Nonetheless, the perceptions of health and privacy threats persist.
If erroneous information sources find ready access to the mass media without effective remedies, then large social impacts, even for minor events, becomes possible [3]. This demonstrates the need to take security and privacy more seriously. In order to avoid any public resistance towards the Smart Grid especially from poorly drawn evidence, risks from the system should not only be analysed and managed but also effectively communicated.
Though over years, experts have stressed the need to have risk analysis embedded into design, it seldom happens. Even if risk analysis is done during design or after deployment; it requires distinct steps or processes that can be followed effectively. A good framework should make its processes transparent and understandable to all its stakeholders. It should also be adaptable and extensible as the system grows or modifies. A great many frameworks are available. They have a lot of commonality, but also differences, some of which are significant in the context of smart meters.
This paper reports on an extensive study of frameworks for the assessment and management of risk, whose purpose was to produce a framework specifically targeted at smart metering systems. Following a brief introductory section on smart grids, a summary and comparison of existing smart grid models are presented, followed by a presentation of a method that is proposed as an effective but efficient approach to smart meter risk assessments.
All around the globe, utilities and government have identified that the traditional energy grid needs to be replaced by Smart Grid. It emerged as a need to effectively manage the electricity requirements from the needs of an increasingly large world population. Though the initial interests were limited to accurately measuring the power usage, the focus has shifted to environmental gains through the reduction of peak demand and hence lower production cost and lower carbon emissions [6] [7].
As smart meters were identified as a primary requirement in a smart grid, many countries have started the smart meter roll-out for residential customers, in some cases mandated.
During and after roll-out, many schemes have been subjected to considerable criticism in relation to security and privacy aspects of the design. In many cases, public concerns have been exacerbated by the discovery that the risk assessments had been performed solely from the perspective of the utility provider [8] [9] [10]. Also by narrowing down the context, most of the documents have failed to consider vulnerabilities of the new system to different kinds of threats.
As a part of the realignment of the utility industry to support a smart grid, various countries and organisations have developed architectural and conceptual models to plan, evaluate and monitor the success of transformation from the traditional to a modern grid. Two popular models are Smart Grid Conceptual Model (SGCM) established by the National Institute of Standards and Technology (NIST) and Smart Grid Architecture Model (SGAM) established by the Working Group Reference Architecture (SG-CG/RA).
SGCM provides a visualized diagram explaining how different components of smart grid can be integrated organised into seven Domains: Bulk Generation, Transmission, Distribution, Customers, Markets, Service Providers and Operations [11].
SGAM has a Smart Grid Plane. Zones are present in additions to the Domains to form a matrix, distinguishing between electrical process and information management viewpoints. The Domains encompass the complete electrical energy conversion chain (Bulk Generation, Transmission, Distribution, Distributed Electrical Resources (DER) and Customers Premises) and the Zones represent the hierarchical levels of power system management (Process, Station, Operation, Enterprise and Market) [12].
SGAM provides a better basis for risk assessment, because its structuring of the area into Domain/Zone cells assists the analyst in identifying the relevant scenarios.
Before entering a discussion on risk analysis it is important to have the terminologies correct. Over years different entities have developed many standards and methods for risk analysis, and the terms and definitions used for risk elements and processes vary.
Most commonly used risk process terms are `Risk Analysis', `Risk Assessment' and `Risk Management'. Some of the descriptions given by few standards and organizations are as follows.
In one definition, `Risk Assessment' encompasses `Risk Analysis' and in another one it is the reverse. Similarly `Risk Management' in one interpretation includes all activities from scope definition to monitoring whereas in another it refers only to the planning and implementation phases.
Reference [17] drew attention to the problems inherent in defining the key term 'risk'. This article adopts a similar approach to the other key terms in the area; rather than attempting a universal definition, each term needs to be defined within the risk assessment document and used consistently within that document.
It is also important not to confuse one risk element with others. The Expert Group of the European Commission's Smart Grid Task Force prepared a Data Protection Impact Assessment Template for Smart Grid and Smart Metering Systems (`DPIA Template') in 2012. The main flaw that was highlighted by the Working Party against the DPIA template was that it often confused risks and threats [18].
In this section the key elements of risks are defined. They variously adopt and adapt definitions found in the most relevant sources found during the conduct of the research [13] [19] [20] [14] [21] [22]. The terms used for each risk element by different entities have been tabulated in Table 1.

The quality of security and privacy risk assessments conducted on smart meter projects has generally not been sufficient to satisfy the public [23] [9]. A framework is needed that enables efficient conduct of risk assessment, and that produces understandable results that convince all stakeholders, including consumers who are suspicious about the compulsory installation of a smart device on their premises.
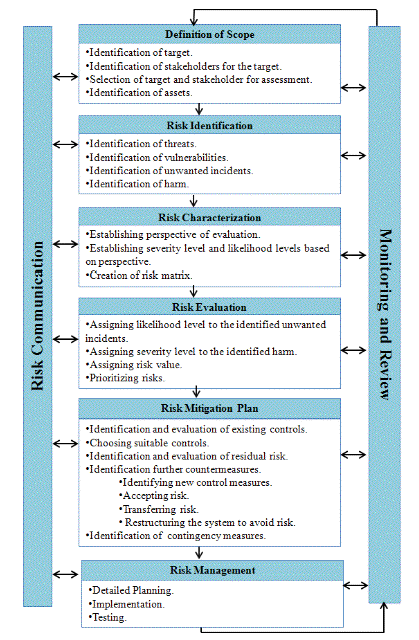
Standards like ISO 2700x, NIST 800-30, BSI 100-x and methods like CORAS and OCTAVE have been exhaustively analysed, with the specific needs of smart meter projects in mind, in order to develop this framework [13] [21] [14] [20] [19]. We choose to use the terminology `Risk Analysis' for this entire decision-making and management process and hence the framework is termed `Risk Analysis Framework'. The proposed framework has a set of optimal steps that can be used to identify, evaluate and control risks to mitigate potential negative effects in Smart Grid. Fig. 1 provides a visual presentation of the framework.
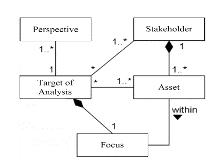
The risk analysis process starts with the definition of scope. To define the scope, the target of evaluations should be identified. Each target will have involvement with one or many stakeholders. To identify the target of evaluation in a smart grid, the Smart Grid Architecture Model (SGAM) is used. There are few ways in which the target can be chosen:
We can identify a number of targets and the stakeholders involved. Then the next step is to choose the target for assessment. We have found that each target may have more than one stakeholder, hence a stakeholder must also be chosen from those identified for the target. Narrowing down the target and stakeholder enables to easily identify the assets involved. At the end of this step we can identify targets, their stakeholders and assets involved.
In this step for each asset identified, all possible threats will be listed. Using the threats identified, all possible vulnerabilities and unwanted incidents can be identified. Using the unwanted incidents list, the harms on the assets can be extracted. Activities should be conducted to ensure stakeholder participation in this phase of risk analysis in particular.
This is vital step in risk analysis. The results from this step will vary based on the perspective of analysis. We have mentioned earlier how risks that have been assessed as minor by technical experts had elicited strong public concerns. For example, an unauthorized party gaining access to the meter data may occur as a minor risk to a utility provider if the access is read-only but from the perspective of the consumer it is still a major risk. So in this step, the perspective of analysis is vital. Based on the perspective, severity levels and likelihood levels need to be identified and tabulated. A risk matrix can be generated using this information.
In this step the unwanted incidents and the harmful impacts that were identified are evaluated using the established levels for severity and likelihood. A likelihood level is assigned to the unwanted incident listed and a severity level assigned to the harms listed. Based on the values of likelihood and severity given, a risk value can be assigned to each case. This risk value can be used to prioritise the risks identified.
This section specifies the treatment that needs to be provided to the identified risks. It begins with the identification of existing controls. The suitability of the control for the target of evaluation is then evaluated. Common factors affecting suitability are cost and resource limitations. For example, there are strong and complex encryption techniques available to protect data, but it may not be feasible to apply them on a smart meter with a limited processor. Based on the evaluation, a list of applicable controls can be specified, and the residual risk determined. Apart from countermeasure, contingency response also needs to be identified so that those actions can be taken should the risk event actually occur.
With all the risks and countermeasures identified, the next step is to plan and implement the safeguards. The implementation needs be tested to ensure that the risks have been mitigated as expected during the analysis.
A planned communication process is very important to improve the awareness of risk to all its stakeholders. In addition, education of the media is needed, in order to avoid negative impacts caused by erroneous information sources.
All identified unwanted incidents, harm and their controls need to be documented and they to be reviewed regularly in order to adapt to new threats and vulnerabilities, and to improve control measures and find better ways of implementing and maintaining them.
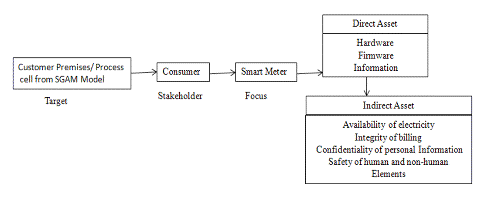
In this section we analyse a scenario using the proposed framework. For this analysis Customer Premises/ Process cell is chosen from the SGAM model. In that cell the target of evaluation is the smart meter. The stakeholder chosen for this analyse is the consumer. The next step is to identify the assets. Assets can be classified as direct assets and indirect assets. For the consumer the direct assets involved with a smart meter are the hardware, firmware and information stored and some of indirect assets are availability of electricity, integrity of billing and other functionalities, confidentiality of personal information and safety of human and non-human elements involved.
The direct assets involved in this scenario can be classified as physical, functional and informational assets. The physical assets comprise of the meter hardware and the communication module. The functional assets entail measuring, conversion, communication and supply-switching functions. The informational assets consist of measurement, configuration, monitoring and consumer's personal information data.
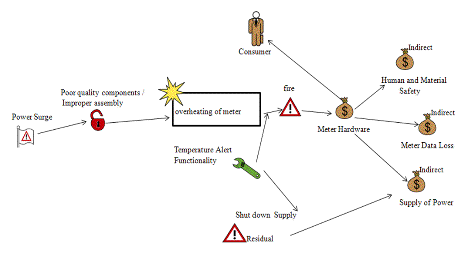
The next step is to identify threats, vulnerabilities and harms. For this analysis we consider the meter hardware. There have been few reports that power surges have caused the smart meter to overheat and start a fire [24]. So in the case, power surge is non-human threat. The vulnerabilities are poor quality components and improper assembly of the meter. Overheating of the meter is the unwanted incident and fire is the harm caused by the threat. It this case, meter hardware is the direct asset and safety, loss of meter data and supply are the indirect asset.
Now this risk can be analyzed from different perspectives. As there were only few incidents reported, regarding fire from overheating of meter, for a provider the risk value related to it will be low. But form a consumer perspective it is very high as there is always a chance of fire that could damage their property and even cause death.
As a control measure to overheating, some smart meters have temperature alert functionality. When the temperature rises above a set threshold, it shuts down the supply and alerts the utility management to take further actions. For a utility provider this control is sufficient as it prevents a fire and there is no harm to their reputation. But from the perspective of a consumer there is still residual risk left. It provides safety by preventing the fire, but the power supply is disrupted. If it is a consumer on life-support machine, it could even cause death.
This scenario clearly shows how the perspective of analysis changes the requirements in control measures for each stakeholder.
In the previous section we have seen how a scenario has been analysed using the framework. Similarly for each target of evaluation, its key risk elements can be identified. A repository can be created for assets, harms, risks and controls. Both quantitative and qualitative risk analysis can be carried out using this framework. A risk register or risk log can be created using the criteria mentioned in the framework. For qualitative risk register descriptive terms are used where as in a quantitative risk register numerical quantities will be used.
Alternately, tools like CORAS can be modified to satisfy the framework and then used for conducting security analyses. This model-based approach, improves communication and interaction between parties involved in the analysis. It will help in easily identifying the missing links and errors [19]. Diagrammatic representations of some of the elements are shown in the following figures (Fig. 2, Fig. 3 and Fig. 4).
Smart grids, and their critical sub-element smart meters, have great potential, but harbour risks to various stakeholders. The perception by householders that they are subject to significant security and privacy risks has proven to be a significant impediment to progress.
The field of risk assessment suffers from an excess of frameworks and a great deal of terminological ambiguity. The risk evaluation framework proposed in this paper reflects the substantial accumulated literature on risk assessment, and is sculpted to the needs of smart meter projects. It is now being applied to existing AMI systems. Experience gained from its use will result in clarifications and improvements to the framework.
Also there are some of the directions in which we can expand this work. We have mentioned in the definition of scope that the stakeholder needs to be identified. It has been conventional to identify consumers or customers as a large number of homogeneous entities. But can all the consumers be considered the same? Even if residential purpose alone is considered, a free-standing house requirement will vary from those of residential apartments and those of holiday apartments. Hence there will be value for all parties from deepening risk evaluation from a consumer perspective and comparing the results with the current, provider-focused system.
Though this proposed framework is intended for the smart grid, it may have implications for other critical infrastructures as well. The `definition of scope' changes based on the choice of infrastructure and except for that one process all the other processes remains the same. The SGAM model is only used as a plug-in to define the targets in the Smart Grid. So even if the model changes or a new model is used the framework will not be affected.
1. Danahy, Jack and Bochman, Andy. Smart Grid for the CSO. The Smart Grid Security Blog. [Online] 2009.
2. Baumeister, Todd. Literature Review on Smart Grid Cyber Security. Honolulu, Hawaii : Department of Information and Computer Sciences, University of Hawaii, 2010.
3. The Social Amplification of Risk - a Conceptual-Framework. Kasperson, R. E., et al. Jun 1988, Risk Analysis, Vol. vol. 8, pp. 177-187. 2.
4. Roberts, Simon and Redgrove, Zoe. The smart metering programme:a consumer review. Bristol : The Centre for Sustainable Energy, 2011.
5. Quinn, Elias L. Privacy and the new energy infrastructure. s.l. : SSRN eLibrary, 2009. p. 25.
6. Smart Grid - The New and Improved Power Grid. Fang, X. and Misra, S. and Xue, G. and Yang, D. 2011, Communications Surveys Tutorials, IEEE, Vol. PP, pp. 1 -37. 99.
7. The path of the smart grid. Farhangi, H. 1, January-February 2010, Power and Energy Magazine, IEEE, Vol. 8, pp. 18 - 28.
8. Deloitte. Department of Treasury and Finance- Advanced metering infrastructure cost benefit analysis- Final Report. Department of Primary Industries. Victoria : s.n., 2011.
9. Lockstep Consulting. Privacy Impact Assessment Report - Advanced Metering Infrastructure (AMI). Department of Primary Industries Victoria. Vicotria, Australia : s.n., 2011.
10. Rambi, Johan. Lessons learned from the new Smart Meter Risk Analysis Methodology in the Netherlands. [Online] January 16, 2013.
11. NIST, National Institute of Standard and Technology. NIST Framework and Roadmap for Smart Grid Interoperability Standards Release 1.0. by Locke, G. and Gallagher, P.D. Ava. s.l. : Office of the National Coordinator for Smart Grid Interoperability, January 2010.
12. CEN-CENELEC-ETSI. Smart Grid Coordination Group Smart Grid Information Security. CEN-CENELEC-ETSI Smart Grid Coordination Group. 2012.
13. ISO/IEC 27005. ISO/lEC 27005 Information technology - Security techniques - Information security risk management. s.l. : ISO/IEC 2008, 2008.
14. Stoneburner, Gary, Goguen, Alice and Fering, Alexis. Risk Management Guide for Information Technology Systems. National Institute of Standards and Technology, U.S. DEPARTMENT OF COMMERCE ,TECHNOLOGY ADMINISTRATION. VA 22042 : NIST Special Publication 800-30, 2002.
15. ENISA. Risk Management:Implementation principles and Inventories for Risk Management/Risk Assessment methods and tools. ENISA website. [Online] 2005-2013. http://www.enisa.europa.eu/activities/risk-management.
16. SRA. Society for Risk Analysis (SRA). [Online] 2013. [Cited: June 1, 2013.] http://www.sra.org/.
17. Kaplan, Stan, The words of risk analysis. (1997), Risk analysis, Vol. 17.4, pp. 407-41.
18. WP 29. Opinion 04/2013 on the Data Protection Impact Assessment Template for Smart Grid and Smart Metering Systems (`DPIA Template') prepared by Expert Group 2 of the Commission's Smart Grid Task Force . s.l. : ARTICLE 29 DATA PROTECTION WORKING PARTY, 2013.
19. Dimitrakos, T., et al. Model based Security Risk Analysis for Web Applications: The CORAS approach. Euroweb 2002 -- The Web and the GRID: from e-science to e-business. 2002.
20. The OCTAVE methodology as a risk analysis tool for business resources. Marek, P. and Paulina, J. 2006. International Multiconference on Computer Science and Information Technology. pp. 485-497.
21. BSI. BSI-Standard 100-3: Risk analysis based on IT-Grundschutz. Bundesamt für Sicherheit in der Informationstechnik (BSI). [Online] 2008 b. https://www.bsi.bund.de/SharedDocs/Downloads/EN/BSI/Publications/BSIStandards/stndard_100-3_e_pdf.pdf?__blob=publicationFile.
22. Security Risk Analysis Group. Introduction to Risk Analysis. [Online] 2003. http://www.security-risk-analysis.com/introduction.htm.
23. NRECA. Guide to Developing a Cyber Security and Risk Mitigation Plan. National Rural Electric Cooperative Association. Arlington, VA : National Rural Electric Cooperative Association/Cooperative Research Network, 2011.
24. EMF Safety Network , "Smart Meter Fires and Explosions," EMF Safety Network , 2012. [Online]. Available: http://emfsafetynetwork.org/?page_id=1280. [Accessed June 210
Rani Yesudas is a software engineer with experience in the smart meters industry, and a PhD student in the Research School of Computer Science at the Australian National University.
Roger Clarke is Principal of Xamax Consultancy Pty Ltd, Canberra. He is also a Visiting Professor in the Cyberspace Law & Policy Centre at the University of N.S.W., and a Visiting Professor in the Research School of Computer Science at the Australian National University.
| Personalia |
Photographs Presentations Videos |
Access Statistics |
 |
The content and infrastructure for these community service pages are provided by Roger Clarke through his consultancy company, Xamax. From the site's beginnings in August 1994 until February 2009, the infrastructure was provided by the Australian National University. During that time, the site accumulated close to 30 million hits. It passed 65 million in early 2021. Sponsored by the Gallery, Bunhybee Grasslands, the extended Clarke Family, Knights of the Spatchcock and their drummer |
Xamax Consultancy Pty Ltd ACN: 002 360 456 78 Sidaway St, Chapman ACT 2611 AUSTRALIA Tel: +61 2 6288 6916 |
Created: 14 June 2013 - Last Amended: 19 August 2013 by Roger Clarke - Site Last Verified: 15 February 2009
This document is at www.rogerclarke.com/EC/SG-FRA.html
Mail to Webmaster - © Xamax Consultancy Pty Ltd, 1995-2022 - Privacy Policy